Cybersecurity company Censys has identified over 380,000 hosts that are still referencing the malicious polyfill.io domain. Censys reported that over 380,000 internet-exposed hosts are still referencing the malicious polyfill.io domain. The polyfill.io domain was suspended last week following multiple reports of malicious activity. The domain Polyfill.io was used to host JavaScript code that added modern […]
...moreSummary
Total Articles Found: 41
Top sources:
Top Keywords:
- malware: 41
- Hacking: 33
- Security Affairs: 33
- Breaking News: 31
- information security news: 31
Top Authors
- Pierluigi Paganini: 34
- Dan Goodin: 3
- Bruce Schneier: 2
- Paul Ducklin: 2
Top Articles:
- Zero-day attackers deliver a double dose of ransomware—no clicking required
- Garmin allegedly paid for a decryptor for WastedLocker ransomware
- UScellular data breach: attackers ported customer phone numbers
- LastPass: Keylogger on home PC led to cracked corporate password vault
- Heap-based buffer overflow in Linux Sudo allows local users to gain root privileges
- Thousands of WordPress WooCommerce stores potentially exposed to hack
- Scranos – A Cross Platform, Rootkit-Enabled Spyware rapidly spreading
- New strain of Cerberus Android banking trojan can steal Google Authenticator codes
- Expert discloses details of 3 Tor zero-day flaws … new ones to come
- Cisco Talos discloses technicals details of Chrome, Firefox flaws
Polyfill.io Supply Chain Attack: 384,773 hosts still embedding a polyfill JS script linking to the malicious domain

Published: 2024-07-05 11:32:00
Popularity: 16
Author: Pierluigi Paganini
Keywords:
🤖: ""JS attack detected""
Google fixed critical zero-click RCE in Android

Published: 2023-12-05 08:02:58
Popularity: 19
Author: Pierluigi Paganini
Keywords:
Google fixed a critical zero-click RCE vulnerability (CVE-2023-40088) with the release of the December 2023 Android security updates. Google December 2023 Android security updates addressed 85 vulnerabilities, including a critical zero-click remote code execution (RCE) flaw tracked as CVE-2023-40088. The vulnerability resides in Android’s System component, it doesn’t require additional privileges to be triggered. An […]
...moreSecurity Vulnerability of Switzerland’s E-Voting System
Published: 2023-10-17 11:11:43
Popularity: 46
Author: Bruce Schneier
Keywords:
Online voting is insecure, period. This doesn’t stop organizations and governments from using it. (And for low-stakes elections, it’s probably fine.) Switzerland—not low stakes—uses online voting for national elections. Andrew Appel explains why it’s a bad idea: Last year, I published a 5-part series about Switzerland’s e-voting system. Like any internet voting system, it has inherent security vulnerabilities: if there are malicious insiders, they can corrupt the vote count; and if thousands of voters’ computers are hacked by malware, the malware can change votes as they are transmitted. Switzerland “solves” the problem of malicious insiders in their printing office by officially declaring that they won’t consider that threat model in their cybersecurity assessment...
...moreGoogle researchers found multiple security issues in Intel TDX

Published: 2023-04-25 14:07:21
Popularity: 26
Author: Pierluigi Paganini
Keywords:
Google Cloud Security and Project Zero researchers found multiple vulnerabilities in the Intel Trust Domain Extensions (TDX). Google Cloud Security and Project Zero researchers, working with Intel experts, discovered multiple vulnerabilities in the Intel Trust Domain Extensions (TDX). The Intel Trust Domain Extensions (Intel® TDX) allows to deploy hardware-isolated, virtual machines (VMs) called trust domains […] The post Google researchers found multiple security issues in Intel TDX appeared first on Security Affairs.
...moreLastPass: Keylogger on home PC led to cracked corporate password vault

Published: 2023-02-28 02:23:16
Popularity: 140
Author: Paul Ducklin
Keywords:
Seems the crooks implanted a keylogger via a vulnerable media app (LastPass politely didn't say which one!) on a developer's home computer.
...morePyTorch compromised to demonstrate dependency confusion attack on Python environments

Published: 2023-01-02 18:57:03
Popularity: 19
Author: Pierluigi Paganini
Keywords:
Threat actors compromised the PyTorch Machine Learning Framework by adding a malicious dependency. The maintainers of the PyTorch package warn of a supply chain attack. Users who have installed PyTorch-nightly on Linux via pip between December 25, 2022 and December 30, 2022, to uninstall it and use the latest binaries. “If you installed PyTorch-nightly on […] The post PyTorch compromised to demonstrate dependency confusion attack on Python environments appeared first on Security Affairs.
...moreExperts uncovered novel Malware persistence within VMware ESXi Hypervisors

Published: 2022-09-30 05:17:30
Popularity: 33
Author: Pierluigi Paganini
Keywords:
Researchers from Mandiant have discovered a novel malware persistence technique within VMware ESXi Hypervisors. Mandiant detailed a novel technique used by malware authors to achieve administrative access within VMware ESXi Hypervisors and take over vCenter servers and virtual machines for Windows and Linux to perform the following actions: Send commands to the hypervisor that will […] The post Experts uncovered novel Malware persistence within VMware ESXi Hypervisors appeared first on Security Affairs.
...moreNew Linux malware combines unusual stealth with a full suite of capabilities
With polymorphic encoding and a multistage infection chain, Shikitega is hard to detect.
...moreNew Checkmate ransomware target QNAP NAS devices

Published: 2022-07-08 07:23:07
Popularity: 12
Author: Pierluigi Paganini
Keywords:
Taiwanese vendor QNAP wars of a new strain of ransomware, dubbed Checkmate, that is targeting its NAS devices. The Taiwanese vendor QNAP is warning of a new family of ransomware targeting its NAS devices using weak passwords. Threat actors are targeting devices exposed online with the SMB service enabled, they perform brute-force attacks against accounts […] The post New Checkmate ransomware target QNAP NAS devices appeared first on Security Affairs.
...moreGoogle TAG argues that Italian surveillance firm RCS Labs was helped by ISPs to infect mobile users

Published: 2022-06-24 07:14:03
Popularity: 5
Author: Pierluigi Paganini
Keywords:
Google’s Threat Analysis Group (TAG) revealed that the Italian spyware vendor RCS Labs was supported by ISPs to spy on users. Researchers from Google’s Threat Analysis Group (TAG) revealed that the Italian surveillance firm RCS Labs was helped by some Internet service providers (ISPs) in Italy and Kazakhstan to infect Android and iOS users with […] The post Google TAG argues that Italian surveillance firm RCS Labs was helped by ISPs to infect mobile users appeared first on Security Affairs.
...moreThreat actors target the infoSec community with fake PoC exploits

Published: 2022-05-23 06:56:23
Popularity: 52
Author: Pierluigi Paganini
Keywords:
Researchers uncovered a malware campaign targeting the infoSec community with fake Proof Of Concept to deliver a Cobalt Strike beacon. Researchers from threat intelligence firm Cyble uncovered a malware campaign targeting the infoSec community. The expert discovered a post where a researcher were sharing a fake Proof of Concept (POC) exploit code for an RPC Runtime Library […] The post Threat actors target the infoSec community with fake PoC exploits appeared first on Security Affairs.
...moreOperation GhostShell: MalKamak APT targets aerospace and telco firms

Published: 2021-10-07 07:53:47
Popularity: 4
Author: Pierluigi Paganini
Keywords:
Operation GhostShell: Threat actors used ShellClient malware in cyberespionage campaigns aimed at companies in the aerospace and telecommunications sectors. Hackers use stealthy ShellClient malware on aerospace, telco firms Cybereason Nocturnus and Incident Response Teams discovered a new threat actor that is targeting organizations in the aerospace and telecommunications sectors with the ShellClient malware as part […] The post Operation GhostShell: MalKamak APT targets aerospace and telco firms appeared first on Security Affairs.
...moreTelegram is becoming the paradise of cyber criminals

Published: 2021-09-27 07:56:11
Popularity: None
Author: Pierluigi Paganini
Keywords:
Telegram is becoming an essential platform for cybercriminal activities, crooks use it but and sell any kind of stolen data and hacking tools. Many experts believe that the popular Telegram app is an efficient alternative to dark web marketplaces, its channels are used by hacking communities and cybercriminals to buy and sell stolen data, accesses […] The post Telegram is becoming the paradise of cyber criminals appeared first on Security Affairs.
...moreSiloscape, first known malware that drops a backdoor into Kubernetes clusters

Published: 2021-06-07 19:16:04
Popularity: None
Author: Pierluigi Paganini
Keywords:
Siloscape is a new strain of malware that targets Windows Server containers to execute code on the underlying node and spread in the Kubernetes cluster. Researchers from Palo Alto Networks have spotted a piece of malware that targets Windows Server containers to execute code on the underlying node and then drop a backdoor into Kubernetes […] The post Siloscape, first known malware that drops a backdoor into Kubernetes clusters appeared first on Security Affairs.
...moreGoogle discovered a new variant of Rowhammer attack dubbed Half-Double

Published: 2021-05-26 15:32:57
Popularity: None
Author: Pierluigi Paganini
Keywords:
Google experts discovered a new variant of Rowhammer attack against RAM memory cards that bypasses all current defenses Google researchers discovered a new variant of Rowhammer attacks, dubbed “Half-Double,” that allows bypassing all current defenses. In 2015, security researchers at Google’s Project Zero team demonstrated how to hijack the Intel-compatible PCs running Linux by exploiting the physical […] The post Google discovered a new variant of Rowhammer attack dubbed Half-Double appeared first on Security Affairs.
...moreUNC2447 cybercrime gang exploited SonicWall Zero-Day before it was fixed

Published: 2021-04-30 16:25:58
Popularity: None
Author: Pierluigi Paganini
Keywords:
UNC2447 cybercrime gang exploited a zero-day in the Secure Mobile Access (SMA), addressed by SonicWall earlier this year, before the vendor released a fix. Researchers from FireEye’s Mandiant revealed that a sophisticated cybercrime gang tracked as UNC2447 has exploited a zero-day issue (CVE-2021-20016) in SonicWall Secure Mobile Access (SMA) devices, fixed earlier this year, before […] The post UNC2447 cybercrime gang exploited SonicWall Zero-Day before it was fixed appeared first on Security Affairs.
...moreAttackers are abusing GitHub infrastructure to mine cryptocurrency

Published: 2021-04-03 10:04:30
Popularity: None
Author: Pierluigi Paganini
Keywords:
🤖: "Cryptocurrency mining fail"
The popular code repository hosting service GitHub is investigating a crypto-mining campaign abusing its infrastructure. Code repository hosting service GitHub launched an investigation in a series of attacks aimed at abusing its infrastructure to illicitly mine cryptocurrency. Such kind of attacks was reported at least since the end of 2020, when some software developers reported the malicious activity […] The post Attackers are abusing GitHub infrastructure to mine cryptocurrency appeared first on Security Affairs.
...moreExperts found two flaws in Facebook for WordPress Plugin

Published: 2021-03-28 20:56:24
Popularity: None
Author: Pierluigi Paganini
Keywords:
A critical flaw in the official Facebook for WordPress plugin could be abused exploited for remote code execution attacks. Researchers at Wordfence have discovered two vulnerabilities in the Facebook for WordPress plugin, which has more than 500,000 active installations. The plugin allows administrators to capture the actions people take while interacting with their page, such […] The post Experts found two flaws in Facebook for WordPress Plugin appeared first on Security Affairs.
...moreAdobe addresses a critical vulnerability in ColdFusion product

Published: 2021-03-22 20:42:43
Popularity: None
Author: Pierluigi Paganini
Keywords:
Adobe has released security updates to address a critical vulnerability in the ColdFusion product (versions 2021, 2016, and 2018) that could lead to arbitrary code execution. Adobe has released security patches to address a critical vulnerability in Adobe ColdFusion that could be exploited by attackers to execute arbitrary code on vulnerable systems. The issue, tracked as CVE-2021-21087 is […] The post Adobe addresses a critical vulnerability in ColdFusion product appeared first on Security Affairs.
...moreVMware addresses a critical RCE issue in vCenter Server
Published: 2021-02-23 22:39:22
Popularity: None
Author: Pierluigi Paganini
Keywords:
VMware addressed a critical remote code execution flaw, tracked as CVE-2021-21972, in vCenter Server virtual infrastructure management platform. VMware has addressed a critical remote code execution (RCE) vulnerability in the vCenter Server virtual infrastructure management platform, tracked as CVE-2021-21972, that could be exploited by attackers to potentially take control of affected systems. vCenter Server is the centralized […] The post VMware addresses a critical RCE issue in vCenter Server appeared first on Security Affairs.
...moreExperts found critical flaws in Realtek Wi-Fi Module

Published: 2021-02-06 21:35:47
Popularity: None
Author: Pierluigi Paganini
Keywords:
Critical flaws in the Realtek RTL8195A Wi-Fi module could have been exploited to gain root access and take over devices’ wireless communications. Researchers from Israeli IoT security firm Vdoo found six vulnerabilities in the Realtek RTL8195A Wi-Fi module that could have been exploited to gain root access and take control of a device’s wireless communications. […] The post Experts found critical flaws in Realtek Wi-Fi Module appeared first on Security Affairs.
...moreUScellular data breach: attackers ported customer phone numbers

Published: 2021-01-30 21:37:25
Popularity: 180
Author: Pierluigi Paganini
Keywords:
US wireless carrier UScellular discloses data breach, personal information of customers may have been exposed and their phone numbers ported. US wireless carrier UScellular discloses a data breach that exposed personal information of its customers. United States Cellular Corporation, is the fourth-largest wireless carrier in the United States, with over 4.9 million customers in 426 […] The post UScellular data breach: attackers ported customer phone numbers appeared first on Security Affairs.
...moreExperts addressed flaws in Popup Builder WordPress plugin

Published: 2021-01-29 18:42:00
Popularity: 16
Author: Pierluigi Paganini
Keywords:
Multiple issues in WordPress ‘Popup Builder’ Plugin could be exploited by hackers to perform various malicious actions on affected websites. Developers behind the “Popup Builder – Responsive WordPress Pop up – Subscription & Newsletter” WordPress plugin have recently addressed multiple vulnerabilities that can be exploited to perform various malicious actions on affected websites. The plugin […] The post Experts addressed flaws in Popup Builder WordPress plugin appeared first on Security Affairs.
...moreHeap-based buffer overflow in Linux Sudo allows local users to gain root privileges

Published: 2021-01-27 09:13:03
Popularity: 120
Author: Pierluigi Paganini
Keywords:
CVE-2021-3156 Sudo vulnerability has allowed any local user to gain root privileges on Unix-like operating systems without authentication. Sudo is one of the most important, powerful, and commonly used utilities that comes as a core command pre-installed on macOS and almost every UNIX or Linux-based operating system. sudo is a program for Unix-like computer operating systems that allows […] The post Heap-based buffer overflow in Linux Sudo allows local users to gain root privileges appeared first on Security Affairs.
...moreSecurity firm SonicWall was victim of a coordinated attack

Published: 2021-01-23 10:05:28
Popularity: None
Author: Pierluigi Paganini
Keywords:
The Hacker News reported in exclusive that the security firm SonicWall was hacked as a result of a coordinated attack on its internal systems. TheHackerNews revealed in an exclusive that the security provider SonicWall was hacked on Friday. The company was targeted with a coordinated attack on its internal systems, threat actors exploited zero-day vulnerabilities […] The post Security firm SonicWall was victim of a coordinated attack appeared first on Security Affairs.
...moreTwo kids found a screensaver bypass in Linux Mint

Published: 2021-01-16 22:52:19
Popularity: None
Author: Pierluigi Paganini
Keywords:
The development team behind the Linux Mint distro has fixed a security flaw that could have allowed users to bypass the OS screensaver. The maintainers of the Linux Mint project have addressed a security bug that could have allowed attackers to bypass the OS screensaver. The curious aspect of this vulnerability is related to its […] The post Two kids found a screensaver bypass in Linux Mint appeared first on Security Affairs.
...moreThousands of WordPress WooCommerce stores potentially exposed to hack

Published: 2020-08-22 08:15:04
Popularity: 86
Author: Pierluigi Paganini
Keywords:
Hackers are attempting to exploit multiple vulnerabilities in the Discount Rules for WooCommerce WordPress plugin, which has 30,000+ installations. Researchers from security firm WebArx reported that Hackers are actively attempting to exploit numerous flaws in the Discount Rules for WooCommerce WordPress plugin. The list of vulnerabilities includes SQL injection, authorization flaws, and unauthenticated stored cross-site scripting (XSS) security vulnerabilities. Discount […] The post Thousands of WordPress WooCommerce stores potentially exposed to hack appeared first on Security Affairs.
...morePoC exploit code for two Apache Struts 2 flaws available online

Published: 2020-08-15 15:52:30
Popularity: None
Author: Pierluigi Paganini
Keywords:
Security researchers have discovered a PoC exploit code available online that can be used to trigger unpatched security flaws in Apache Struts 2. Security researchers have discovered a PoC code and exploit available on GitHub that that can be used to trigger the security vulnerabilities in Apache Struts 2. The Proof-of-concept exploit code was released […] The post PoC exploit code for two Apache Struts 2 flaws available online appeared first on Security Affairs.
...moreGarmin allegedly paid for a decryptor for WastedLocker ransomware

Published: 2020-08-02 13:14:51
Popularity: 422
Author: Pierluigi Paganini
Keywords:
BleepingComputer researchers confirmed that Garmin has received the decryption key to recover their files encrypted with the WastedLocker Ransomware. BleepingComputer first revealed that Garmin has received the decryption key to recover the files encrypted with the WastedLocker Ransomware in the recent attack. On July 23, smartwatch and wearables maker Garmin has shut down several of its services […] The post Garmin allegedly paid for a decryptor for WastedLocker ransomware appeared first on Security Affairs.
...moreExpert discloses details of 3 Tor zero-day flaws … new ones to come

Published: 2020-07-30 21:53:32
Popularity: 73
Author: Pierluigi Paganini
Keywords:
A security researcher published the details about two Tor zero-day vulnerabilities and plans to release three more flaws. The security researcher Dr. Neal Krawetz has published technical details about two Tor zero-day vulnerabilities over the past week and promises to release three more. Oppressive regimes could exploit these Tor zero-day flaws to prevent users from […] The post Expert discloses details of 3 Tor zero-day flaws … new ones to come appeared first on Security Affairs.
...moreAdobe fixed critical code execution flaws in Bridge, Photoshop and Prelude products

Published: 2020-07-22 06:07:07
Popularity: None
Author: Pierluigi Paganini
Keywords:
This week, Adobe has addressed several critical code execution vulnerabilities in its Bridge, Photoshop and Prelude products. Adobe has released security updates to address several critical code execution vulnerabilities in its Bridge, Photoshop and Prelude products. “Adobe has published security bulletins for Adobe Bridge (APSB20-44), Adobe Photoshop (APSB20-45), Adobe Prelude (APSB20-46) and Adobe Reader Mobile […] The post Adobe fixed critical code execution flaws in Bridge, Photoshop and Prelude products appeared first on Security Affairs.
...moreZoom is working on a patch for a zero-day in Windows client

Published: 2020-07-09 23:11:06
Popularity: None
Author: Pierluigi Paganini
Keywords:
Researchers from cyber-security firm ACROS Security have disclosed a zero-day vulnerability in the Windows client of the popular Zoom video conferencing platform. Researchers from cyber-security firm ACROS Security have disclosed a zero-day vulnerability in the Windows client of the video conferencing software Zoom. The vulnerability is a remote code execution issue, which could allow the […] The post Zoom is working on a patch for a zero-day in Windows client appeared first on Security Affairs.
...moreCisco Talos discloses technicals details of Chrome, Firefox flaws

Published: 2020-07-05 12:33:56
Popularity: 67
Author: Pierluigi Paganini
Keywords:
Cisco’s Talos experts disclosed the details of recently patched vulnerabilities affecting the popular Chrome and Firefox web browsers. Researchers from Cisco Talos disclosed technical details of recently patched vulnerabilities affecting the popular Chrome and Firefox web browsers. The first issue, tracked as CVE-2020-6463, is a memory corruption vulnerability that affects PDFium, an open source PDF […] The post Cisco Talos discloses technicals details of Chrome, Firefox flaws appeared first on Security Affairs.
...moreFlaws in mobile Internet protocol GTP allow hackers to target 5G users

Published: 2020-06-15 22:42:36
Popularity: None
Author: Pierluigi Paganini
Keywords:
Security vulnerabilities in modern communication protocol GTP used by mobile network operators can be exploited by attackers to target 4G/5G users. Researchers at cybersecurity firm Positive Technologies Security have discovered several vulnerabilities in communication protocol GPRS Tunnelling Protocol (GTP), that is used by mobile network operators (MNOs). Threat actors could exploit these flaws to conduct several […] The post Flaws in mobile Internet protocol GTP allow hackers to target 5G users appeared first on Security Affairs.
...moreNew strain of Cerberus Android banking trojan can steal Google Authenticator codes

Published: 2020-02-27 13:21:26
Popularity: 74
Author: Pierluigi Paganini
Keywords:
🤖: "Trojan alert"
Experts found a new version of the Cerberus Android banking trojan that can steal one-time codes generated by the Google Authenticator app and bypass 2FA. Security researchers from ThreatFabric warn of a new Android malware strain can now steal one-time passcodes (OTP) generated through Google Authenticator that is used as part of 2FA to protect online […] The post New strain of Cerberus Android banking trojan can steal Google Authenticator codes appeared first on Security Affairs.
...moreGoogle confirms that advanced backdoor came preinstalled on Android devices

Published: 2019-06-06 20:47:20
Popularity: None
Author: Dan Goodin
Keywords:
After Google successfully beat back Triada in 2017, its developers found a new way in.
...moreZero-day attackers deliver a double dose of ransomware—no clicking required
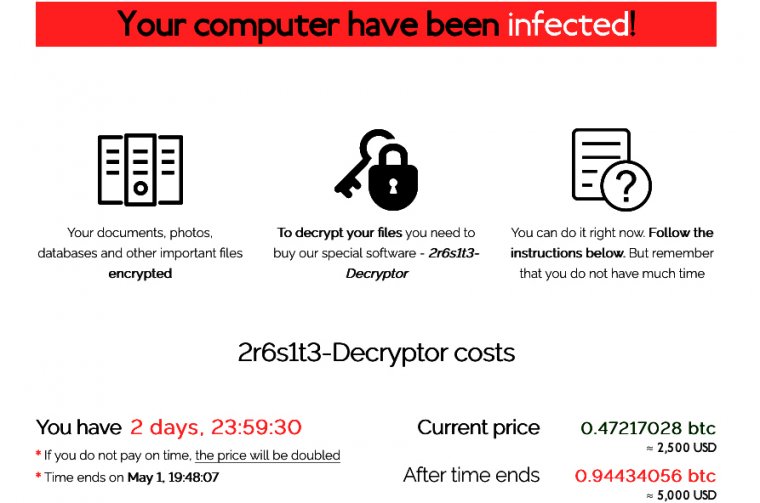
Published: 2019-04-30 19:50:10
Popularity: 953
Author: Dan Goodin
Keywords:
High-severity hole in Oracle WebLogic under active exploit for 9 days. Patch now.
...moreExtraPulsar backdoor based on leaked NSA code – what you need to know

Published: 2019-04-25 14:58:33
Popularity: 0
Author: Paul Ducklin
Keywords:
A US security researcher has come up with an open-source Windows backdoor loosely based on NSA attack code that leaked back in 2017.
...moreScranos – A Cross Platform, Rootkit-Enabled Spyware rapidly spreading

Published: 2019-04-16 11:30:57
Popularity: 79
Author: Pierluigi Paganini
Keywords:
Scranos is a powerful cross-platform rootkit-enabled spyware discovered while investigating malware posing as legitimate software like video players, drivers and even anti-virus products. The Scranos rootkit malware was first discovered late last year when experts at Bitdefender were analyzing a new password- and data-stealing operation leveraging around a rootkit driver digitally signed with a stolen […] The post Scranos – A Cross Platform, Rootkit-Enabled Spyware rapidly spreading appeared first on Security Affairs.
...moreThreat actors exploit Atlassian Confluence bug in cryptomining campaigns

Published: 2024-08-30 08:12:43
Popularity: 21
Author: Pierluigi Paganini
Keywords:
🤖: "Crypto mining chaos"
Threat actors are actively exploiting a critical flaw in the Atlassian Confluence Data Center and Confluence Server in cryptocurrency mining campaigns. The critical vulnerability CVE-2023-22527 (CVSS score 10.0) in the Atlassian Confluence Data Center and Confluence Server is being actively exploited for cryptojacking campaigns. The vulnerability is a template injection vulnerability that can allow remote […]
...morePython Developers Targeted with Malware During Fake Job Interviews

Published: 2024-09-17 11:02:34
Popularity: 10
Author: Bruce Schneier
Keywords:
🤖: "Phishing alert!"
Interesting social engineering attack: luring potential job applicants with fake recruiting pitches, trying to convince them to download malware. From a news article These particular attacks from North Korean state-funded hacking team Lazarus Group are new, but the overall malware campaign against the Python development community has been running since at least August of 2023, when a number of popular open source Python tools were maliciously duplicated with added malware. Now, though, there are also attacks involving “coding tests” that only exist to get the end user to install hidden malware on their system (cleverly hidden with Base64 encoding) that allows remote execution once present. The capacity for exploitation at that point is pretty much unlimited, due to the flexibility of Python and how it interacts with the underlying OS...
...more