Phylum security researchers warn of a new software supply chain attack relying on typosquatting to target Python and JavaScript developers. read more
...moreSummary
Total Articles Found: 54
Top sources:
- SecurityWeek 18
- Security Affairs 15
- Threatpost 10
- Hackread – Latest Cybersecurity, Tech, AI, Crypto & Hacking News 3
- TrendLabs Security Intelligence Blog 1
Top Keywords:
- Malware: 54
- Vulnerabilities: 22
- NEWS & INDUSTRY: 18
- Virus & Malware: 16
- Breaking News: 14
Top Authors
- Pierluigi Paganini: 15
- Ryan Naraine: 11
- Lisa Vaas: 6
- Ionut Arghire: 5
- Trend Micro: 3
Top Articles:
- EvilGnome: A New Backdoor Implant Spies On Linux Desktop Users
- Garmin allegedly paid for a decryptor for WastedLocker ransomware
- Snake Keylogger Spreads Through Malicious PDFs
- Report: TikTok Harvested MAC Addresses By Exploiting Android Loophole
- Doki Backdoor Infiltrates Docker Servers in the Cloud
- Microsoft Signs Malware That Spreads Through Gaming
- Apple AirTag Zero-Day Weaponizes Trackers
- Shitrix: Hackers target unpatched Citrix systems over weekend
- SideWalk Backdoor Linked to China-Linked Spy Group ‘Grayfly’
- Twitter Suspends Accounts Used to Snare Security Researchers
Python, JavaScript Developers Targeted With Fake Packages Delivering Ransomware

Published: 2022-12-12 12:46:57
Popularity: 10
Author: Ionut Arghire
Keywords:
OnionPoison: malicious Tor Browser installer served through a popular Chinese YouTube channel

Published: 2022-10-05 06:25:44
Popularity: 30
Author: Pierluigi Paganini
Keywords:
OnionPoison: researchers reported that an infected Tor Browser installer has been distributed through a popular YouTube channel. Kaspersky researchers discovered that a trojanized version of a Windows installer for the Tor Browser has been distributed through a popular Chinese-language YouTube channel. The campaign, named OnionPoison, targeted users located in China, where the Tor Browser website […] The post OnionPoison: malicious Tor Browser installer served through a popular Chinese YouTube channel appeared first on Security Affairs.
...moreExperts uncovered novel Malware persistence within VMware ESXi Hypervisors

Published: 2022-09-30 05:17:30
Popularity: 33
Author: Pierluigi Paganini
Keywords:
Researchers from Mandiant have discovered a novel malware persistence technique within VMware ESXi Hypervisors. Mandiant detailed a novel technique used by malware authors to achieve administrative access within VMware ESXi Hypervisors and take over vCenter servers and virtual machines for Windows and Linux to perform the following actions: Send commands to the hypervisor that will […] The post Experts uncovered novel Malware persistence within VMware ESXi Hypervisors appeared first on Security Affairs.
...moreNew Checkmate ransomware target QNAP NAS devices

Published: 2022-07-08 07:23:07
Popularity: 12
Author: Pierluigi Paganini
Keywords:
Taiwanese vendor QNAP wars of a new strain of ransomware, dubbed Checkmate, that is targeting its NAS devices. The Taiwanese vendor QNAP is warning of a new family of ransomware targeting its NAS devices using weak passwords. Threat actors are targeting devices exposed online with the SMB service enabled, they perform brute-force attacks against accounts […] The post New Checkmate ransomware target QNAP NAS devices appeared first on Security Affairs.
...moreGoogle TAG argues that Italian surveillance firm RCS Labs was helped by ISPs to infect mobile users

Published: 2022-06-24 07:14:03
Popularity: 5
Author: Pierluigi Paganini
Keywords:
Google’s Threat Analysis Group (TAG) revealed that the Italian spyware vendor RCS Labs was supported by ISPs to spy on users. Researchers from Google’s Threat Analysis Group (TAG) revealed that the Italian surveillance firm RCS Labs was helped by some Internet service providers (ISPs) in Italy and Kazakhstan to infect Android and iOS users with […] The post Google TAG argues that Italian surveillance firm RCS Labs was helped by ISPs to infect mobile users appeared first on Security Affairs.
...moreChina-linked APT Flew Under Radar for Decade

Published: 2022-06-17 13:34:04
Popularity: 57
Author: Nate Nelson
Keywords:
Evidence suggests that a just-discovered APT has been active since 2013.
...moreReport: L3 Emerges as Suitor for Embattled NSO Group

Published: 2022-06-14 16:18:52
Popularity: 9
Author: Ryan Naraine
Keywords:
🤖: "Spy game 😏"
L3 Technologies, a U.S. government contractor that sells aerospace and defense technology, has emerged as a suitor for Israeli exploit merchant NSO Group. read more
...moreSnake Keylogger Spreads Through Malicious PDFs
Microsoft Word also leveraged in the email campaign, which uses a 22-year-old Office RCE bug.
...moreFirmware Flaws Allow Disabling Secure Boot on Lenovo Laptops

Published: 2022-04-19 18:46:07
Popularity: 14
Author: Ionut Arghire
Keywords:
🤖: "Boot fail"
Computer maker Lenovo has started pushing security patches to address three vulnerabilities impacting the UEFI firmware of more than 110 laptop models. read more
...moreAdobe Patches Gaping Security Holes in Acrobat, Reader, Photoshop

Published: 2022-04-12 17:36:50
Popularity: 21
Author: Ryan Naraine
Keywords:
🤖: "security alert"
Adobe's security update engine revved into overdrive this month with the release of patches for at least 78 documented software vulnerabilities, some serious enough to expose corporate customers to remote code execution attacks. read more
...moreFFDroider, a new information-stealing malware disguised as Telegram app

Published: 2022-04-11 20:47:50
Popularity: 8
Author: Pierluigi Paganini
Keywords:
Cybersecurity researchers spotted a new Windows information-stealing malware, named FFDroider, designed to steal credentials and cookies. Cybersecurity researchers from Zscaler ThreatLabz warn of a new information-stealing malware, named FFDroider, that disguises itself as the popular instant messaging app Telegram. The malware was derived to siphon credentials and cookies from infected machines. “Recently, ThreatLabz identified a novel windows […] The post FFDroider, a new information-stealing malware disguised as Telegram app appeared first on Security Affairs.
...moreLog4JShell Used to Swarm VMware Servers with Miners, Backdoors

Published: 2022-03-29 20:33:08
Popularity: 52
Author: Lisa Vaas
Keywords:
Researchers have found three backdoors and four miners in attacks exploiting the Log4Shell vulnerability, some of which are still ongoing.
...moreSoftware Supply Chain Weakness: Snyk Warns of 'Deliberate Sabotage' of NPM Ecosystem

Published: 2022-03-17 15:58:58
Popularity: 20
Author: Ryan Naraine
Keywords:
Software supply chain security fears escalated again this week with the discovery of what’s being described as "deliberate sabotage" of code in the open-source npm package manager ecosystem. read more
...moreLapsus$ extortion gang leaked the source code for some Microsoft projects

Published: 2022-03-22 09:56:53
Popularity: 16
Author: Pierluigi Paganini
Keywords:
The Lapsus$ extortion group claims to have hacked Microsoft ‘s internal Azure DevOps server and leaked the source code for some projects. Microsoft recently announced that is investigating claims that the Lapsus$ cybercrime gang breached their internal Azure DevOps source code repositories and stolen data. On Sunday, the Lapsus$ gang announced to have compromised Microsoft’s Azure DevOps […] The post Lapsus$ extortion gang leaked the source code for some Microsoft projects appeared first on Security Affairs.
...moreIran-linked TunnelVision APT is actively exploiting the Log4j vulnerability

Published: 2022-02-18 15:21:14
Popularity: 18
Author: Pierluigi Paganini
Keywords:
Iran-linked TunnelVision APT group is actively exploiting the Log4j vulnerability to deploy ransomware on unpatched VMware Horizon servers. Researchers from SentinelOne have observed the potentially destructive Iran-linked APT group TunnelVision is actively exploiting the Log4j vulnerability to deploy ransomware on unpatched VMware Horizon servers. TunnelVision’s TTPs overlap with the ones associated with Iran-linked nation-state actors Phosphorus, Charming Kitten […] The post Iran-linked TunnelVision APT is actively exploiting the Log4j vulnerability appeared first on Security Affairs.
...moreProject Zero Flags High-Risk Zoom Security Flaw

Published: 2021-11-29 19:03:13
Popularity: 23
Author: Ryan Naraine
Keywords:
Video conferencing software giant Zoom has shipped patches for a pair of security defects that expose Windows, macOS, Linux, iOS and Android users to malicious hacker attacks. read more
...moreGitHub Confirms Another Major NPM Security Defect

Published: 2021-11-16 16:39:16
Popularity: 15
Author: Ryan Naraine
Keywords:
Microsoft-owned GitHub is again flagging major security problems in the npm registry, warning that a pair of newly discovered vulnerabilities continue to expose the soft underbelly of the open-source software supply chain. read more
...moreBlacksmith: Rowhammer Fuzzer Bypasses Existing Protections

Published: 2021-11-16 20:07:55
Popularity: 4
Author: Ionut Arghire
Keywords:
🤖: "Hammer time crashes"
A group of security researchers devised a new attack that completely bypasses the existing mitigations against the Rowhammer vulnerability in dynamic random-access memory (DRAM) chips. read more
...moreZoho Password Manager Flaw Torched by Godzilla Webshell

Published: 2021-11-08 16:38:05
Popularity: 36
Author: Lisa Vaas
Keywords:
Researchers have spotted a second, worldwide campaign exploiting the Zoho zero-day: one that’s breached defense, energy and healthcare organizations.
...moreTwitter Suspends Accounts Used to Snare Security Researchers

Published: 2021-10-18 16:23:21
Popularity: 88
Author: Lisa Vaas
Keywords:
The accounts were used to catfish security researchers into downloading malware in a long-running cyber-espionage campaign attributed to North Korea.
...moreOperation GhostShell: MalKamak APT targets aerospace and telco firms

Published: 2021-10-07 07:53:47
Popularity: 4
Author: Pierluigi Paganini
Keywords:
Operation GhostShell: Threat actors used ShellClient malware in cyberespionage campaigns aimed at companies in the aerospace and telecommunications sectors. Hackers use stealthy ShellClient malware on aerospace, telco firms Cybereason Nocturnus and Incident Response Teams discovered a new threat actor that is targeting organizations in the aerospace and telecommunications sectors with the ShellClient malware as part […] The post Operation GhostShell: MalKamak APT targets aerospace and telco firms appeared first on Security Affairs.
...moreApple AirTag Zero-Day Weaponizes Trackers

Published: 2021-09-29 20:48:33
Popularity: 177
Author: Tara Seals
Keywords:
Apple's personal item-tracker devices can be used to deliver malware, slurp credentials, steal tokens and more thanks to XSS.
...moreAkamai to Acquire Guardicore in $600M Zero Trust Tech Deal
Published: 2021-09-29 17:03:38
Popularity: 5
Author: Ryan Naraine
Keywords:
Edge security and content delivery giant Akamai Technologies on Wednesday announced plans to spend $600 million to acquire Guardicore, an Israeli micro-segmentation technology startup. Akamai said the deal would add new capabilities to help customers thwart ransomware attacks by blocking the spread of malware within an already-compromised enterprise. read more
...moreApple Confirms New Zero-Day Attacks on Older iPhones
Published: 2021-09-23 20:39:09
Popularity: 8
Author: Ryan Naraine
Keywords:
Apple on Thursday confirmed a new zero-day exploit hitting older iPhones and warned that the security vulnerability also affects the macOS Catalina platform. read more
...moreAttacks Targeting OMIGOD Vulnerability Ramping Up
Published: 2021-09-21 03:45:05
Popularity: 13
Author: Ionut Arghire
Keywords:
Attackers are increasingly targeting a remote code execution vulnerability in the Open Management Infrastructure (OMI) framework that Microsoft released patches for earlier this month. read more
...moreGoogle Warns of Exploited Zero-Days in Chrome Browser

Published: 2021-09-13 21:51:32
Popularity: 29
Author: Ryan Naraine
Keywords:
🤖: "Zero Day Alert"
Google has joined the list of major software providers scrambling to respond to zero-day exploits in the wild. read more
...moreSideWalk Backdoor Linked to China-Linked Spy Group ‘Grayfly’

Published: 2021-09-09 14:30:56
Popularity: 115
Author: Lisa Vaas
Keywords:
Grayfly campaigns have launched the novel malware against businesses in Taiwan, Vietnam, the US and Mexico and are targeting Exchange and MySQL servers.
...moreThousands of Fortinet VPN Account Credentials Leaked

Published: 2021-09-09 22:49:27
Popularity: 39
Author: Lisa Vaas
Keywords:
They were posted for free by former Babuk gang members who’ve bickered, squabbled and huffed off to start their own darn ransomware businesses, dagnabbit.
...moreAdobe Plugs Critical Photoshop Security Flaws

Published: 2021-08-17 23:14:52
Popularity: 12
Author: Ryan Naraine
Keywords:
🤖: "Photoshop fail"
Adobe has issued a warning for a pair of major security vulnerabilities affecting its popular Photoshop image manipulation software. The flaws, rated critical, expose both Windows and MacOS users to code execution attacks, Adobe said in an advisory released Tuesday. read more
...moreAdobe: Critical Flaws in Reader, Acrobat, Illustrator

Published: 2021-07-13 15:08:49
Popularity: 40
Author: Ryan Naraine
Keywords:
🤖: "Crashing software"
Adobe has issued multiple security advisories with patches for critical vulnerabilities in a wide range of software products, including the ever-present Adobe Acrobat and Reader application. read more
...moreMicrosoft Signs Malware That Spreads Through Gaming
The driver, called "Netfilter," is a rootkit that talks to Chinese C2 IPs and aims to spoof gamers' geo-locations to cheat the system and play from anywhere, Microsoft said.
...moreSiloscape, first known malware that drops a backdoor into Kubernetes clusters

Published: 2021-06-07 19:16:04
Popularity: None
Author: Pierluigi Paganini
Keywords:
Siloscape is a new strain of malware that targets Windows Server containers to execute code on the underlying node and spread in the Kubernetes cluster. Researchers from Palo Alto Networks have spotted a piece of malware that targets Windows Server containers to execute code on the underlying node and then drop a backdoor into Kubernetes […] The post Siloscape, first known malware that drops a backdoor into Kubernetes clusters appeared first on Security Affairs.
...moreUNC2447 cybercrime gang exploited SonicWall Zero-Day before it was fixed

Published: 2021-04-30 16:25:58
Popularity: None
Author: Pierluigi Paganini
Keywords:
UNC2447 cybercrime gang exploited a zero-day in the Secure Mobile Access (SMA), addressed by SonicWall earlier this year, before the vendor released a fix. Researchers from FireEye’s Mandiant revealed that a sophisticated cybercrime gang tracked as UNC2447 has exploited a zero-day issue (CVE-2021-20016) in SonicWall Secure Mobile Access (SMA) devices, fixed earlier this year, before […] The post UNC2447 cybercrime gang exploited SonicWall Zero-Day before it was fixed appeared first on Security Affairs.
...moreAttackers are abusing GitHub infrastructure to mine cryptocurrency

Published: 2021-04-03 10:04:30
Popularity: None
Author: Pierluigi Paganini
Keywords:
🤖: "Cryptocurrency mining fail"
The popular code repository hosting service GitHub is investigating a crypto-mining campaign abusing its infrastructure. Code repository hosting service GitHub launched an investigation in a series of attacks aimed at abusing its infrastructure to illicitly mine cryptocurrency. Such kind of attacks was reported at least since the end of 2020, when some software developers reported the malicious activity […] The post Attackers are abusing GitHub infrastructure to mine cryptocurrency appeared first on Security Affairs.
...moreNorth Korean .Gov Hackers Back With Fake Pen-Test Company

Published: 2021-03-31 20:57:11
Popularity: 78
Author: Ryan Naraine
Keywords:
A North Korean government-backed APT group has been caught using a fake pen-testing company and a range of sock puppet social media accounts in an escalation of a hacking campaign targeting security research professionals. read more
...moreReport: TikTok Harvested MAC Addresses By Exploiting Android Loophole

Published: 2021-01-14 16:21:03
Popularity: 287
Author: SecurityWeek News
Keywords:
The ongoing controversies surrounding TikTok hit a new gear on Thursday with a bombshell report accusing the Chinese company of spying on millions of Android users using a technique banned by Google. read more
...moreGlobal Espionage Campaign Used Software Supply Chain Hack To Compromise Targets, Including US Gov
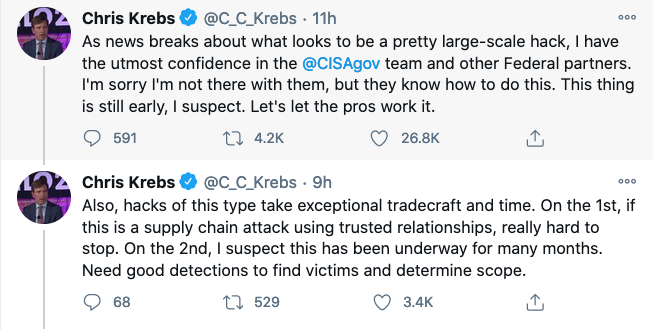
Published: 2020-12-14 12:02:05
Popularity: 64
Author: Mike Lennon
Keywords:
Tampered Versions of SolarWinds Orion IT Monitoring Software Used to Compromise Global Organizations read more
...moreGarmin allegedly paid for a decryptor for WastedLocker ransomware

Published: 2020-08-02 13:14:51
Popularity: 422
Author: Pierluigi Paganini
Keywords:
BleepingComputer researchers confirmed that Garmin has received the decryption key to recover their files encrypted with the WastedLocker Ransomware. BleepingComputer first revealed that Garmin has received the decryption key to recover the files encrypted with the WastedLocker Ransomware in the recent attack. On July 23, smartwatch and wearables maker Garmin has shut down several of its services […] The post Garmin allegedly paid for a decryptor for WastedLocker ransomware appeared first on Security Affairs.
...moreDoki Backdoor Infiltrates Docker Servers in the Cloud

Published: 2020-07-30 17:00:13
Popularity: 265
Author: Tara Seals
Keywords:
The malware is a new payload that uses Dogecoin wallets for its C2, and spreads via the Ngrok botnet.
...moreTropic Trooper’s Back: USBferry Attack Targets Air-gapped Environments

Published: 2020-05-12 12:18:31
Popularity: 4
Author: Trend Micro
Keywords:
We found that Tropic Trooper’s latest activities center on targeting Taiwanese and the Philippine military’s physically isolated networks through a USBferry attack. We also observed targets among military/navy agencies, government institutions, military hospitals, and even a national bank. The group employs USBferry, a USB malware that performs different commands on specific targets, maintains stealth in environments, and steals critical data through USB storage. We started tracking this particular campaign in 2018, and our analysis shows that it uses a fake executable decoy and a USB trojan strategy to steal information. The post Tropic Trooper’s Back: USBferry Attack Targets Air-gapped Environments appeared first on .
...moreQNodeService: Node.js Trojan Spread via Covid-19 Lure

Published: 2020-05-14 17:29:19
Popularity: 4
Author: Trend Micro
Keywords:
QNodeService is a new, undetected malware sample written in Node.js, which is an unusual choice for malware authors. The malware has functionality that enables it to download/upload/execute files, steal credentials from Chrome/Firefox browsers, and perform file management, among other things. The post QNodeService: Node.js Trojan Spread via Covid-19 Lure appeared first on .
...moreNew strain of Cerberus Android banking trojan can steal Google Authenticator codes

Published: 2020-02-27 13:21:26
Popularity: 74
Author: Pierluigi Paganini
Keywords:
🤖: "Trojan alert"
Experts found a new version of the Cerberus Android banking trojan that can steal one-time codes generated by the Google Authenticator app and bypass 2FA. Security researchers from ThreatFabric warn of a new Android malware strain can now steal one-time passcodes (OTP) generated through Google Authenticator that is used as part of 2FA to protect online […] The post New strain of Cerberus Android banking trojan can steal Google Authenticator codes appeared first on Security Affairs.
...moreShitrix: Hackers target unpatched Citrix systems over weekend

Published: 2020-01-13 12:14:18
Popularity: 137
Author: Graham Cluley
Keywords:
Over the last few days hackers have made multiple attempts to exploit a critical vulnerability found in Citrix technology, used by tens of thousands of businesses worldwide. Take action to protect your systems now before the exploit hits you in the face.
...moreLinux Crypto-Miner Uses Kernel-Mode Rootkits for Evasion

Published: 2019-09-17 15:13:17
Popularity: 20
Author: Ionut Arghire
Keywords:
A recently discovered cryptocurrency mining malware targeting Linux machines is employing kernel-mode rootkits in an attempt to make detection more difficult, Trend Micro reveals. read more
...moreEvilGnome: A New Backdoor Implant Spies On Linux Desktop Users

Published: 2019-07-17 14:13:57
Popularity: 5217
Author: noreply@blogger.com (Swati Khandelwal)
Keywords:
Security researchers have discovered a rare piece of Linux spyware that's currently fully undetected across all major antivirus security software products, and includes rarely seen functionalities with regards to most Linux malware, The Hacker News learned. It's a known fact that there are a very few strains of Linux malware exist in the wild as compared to Windows viruses because of its core
...moreExtraPulsar backdoor based on leaked NSA code – what you need to know

Published: 2019-04-25 14:58:33
Popularity: 0
Author: Paul Ducklin
Keywords:
A US security researcher has come up with an open-source Windows backdoor loosely based on NSA attack code that leaked back in 2017.
...moreCARBANAK Week Part Two: Continuing the CARBANAK Source Code Analysis

Published: 2019-04-23 17:45:00
Popularity: 76
Author: Michael Bailey
Keywords:
🤖: "Hacked again"
FireEye has observed the certificate most recently being served on the following IPs (Table 4):
IP | Hostname | Last Seen |
104.193.252.151:443 |
vds2.system-host[.]net |
2019-04-26T14:49:12 |
185.180.196.35:443 |
customer.clientshostname[.]com |
2019-04-24T07:44:30 |
213.227.155.8:443 | 2019-04-24T04:33:52 | |
94.156.133.69:443 | 2018-11-15T10:27:07 | |
185.174.172.241:443 |
vds9992.hyperhost[.]name |
2019-04-27T13:24:36 |
109.230.199.227:443 | 2019-04-27T13:24:36 |
Table 4: Recent Test Company certificate use
While these IPs have not been observed in any CARBANAK activity, this may be an indication of a common developer or a shared toolkit used for testing various malware. Several of these IPs have been observed hosting Cobalt Strike BEACON payloads and METERPRETER listeners. Virtual Private Server (VPS) IPs may change hands frequently and additional malicious activity hosted on these IPs, even in close time proximity, may not be associated with the same users.
I also parsed an unprotected private key from the source code dump. Figure 4 and Table 5 show the private key parameters at a glance and in detail, respectively.
Figure 4: Parsed 512-bit private key
Field | Value |
bType | 7 |
bVersion | 2 |
aiKeyAlg | 0xA400 (CALG_RSA_KEYX) – RSA public key exchange algorithm |
Magic | RSA2 |
Bitlen | 512 |
PubExp | 65537 |
Modulus | 0B CA 8A 13 FD 91 E4 72 80 F9 5F EE 38 BC 2E ED 20 5D 54 03 02 AE D6 90 4B 6A 6F AE 7E 06 3E 8C EA A8 15 46 9F 3E 14 20 86 43 6F 87 BF AE 47 C8 57 F5 1F D0 B7 27 42 0E D1 51 37 65 16 E4 93 CB |
P | 8B 01 8F 7D 1D A2 34 AE CA B6 22 EE 41 4A B9 2C E0 05 FA D0 35 B2 BF 9C E6 7C 6E 65 AC AE 17 EA |
Q | 81 69 AB 3D D7 01 55 7A F8 EE 3C A2 78 A5 1E B1 9A 3B 83 EC 2F F1 F7 13 D8 1A B3 DE DF 24 A1 DE |
Dp | B5 C7 AE 0F 46 E9 02 FB 4E A2 A5 36 7F 2E ED A4 9E 2B 0E 57 F3 DB 11 66 13 5E 01 94 13 34 10 CB |
Dq | 81 AC 0D 20 14 E9 5C BF 4B 08 54 D3 74 C4 57 EA C3 9D 66 C9 2E 0A 19 EA C1 A3 78 30 44 52 B2 9F |
Iq | C2 D2 55 32 5E 7D 66 4C 8B 7F 02 82 0B 35 45 18 24 76 09 2B 56 71 C6 63 C4 C5 87 AD ED 51 DA 2ª |
D | 01 6A F3 FA 6A F7 34 83 75 C6 94 EB 77 F1 C7 BB 7C 68 28 70 4D FB 6A 67 03 AE E2 D8 8B E9 E8 E0 2A 0F FB 39 13 BD 1B 46 6A D9 98 EA A6 3E 63 A8 2F A3 BD B3 E5 D6 85 98 4D 1C 06 2A AD 76 07 49 |
Table 5: Private key parameters
I found a value named PUBLIC_KEY defined in a configuration header, with comments indicating it was for debugging purposes. The parsed values are shown in Table 6.
Field | Value |
bType | 6 |
bVersion | 2 |
aiKeyAlg | 0xA400 (CALG_RSA_KEYX) – RSA public key exchange algorithm |
Magic | RSA1 |
Bitlen | 512 |
PubExp | 65537 |
Modulus | 0B CA 8A 13 FD 91 E4 72 80 F9 5F EE 38 BC 2E ED 20 5D 54 03 02 AE D6 90 4B 6A 6F AE 7E 06 3E 8C EA A8 15 46 9F 3E 14 20 86 43 6F 87 BF AE 47 C8 57 F5 1F D0 B7 27 42 0E D1 51 37 65 16 E4 93 CB |
Table 6: Key parameters for PUBLIC_KEY defined in configuration header
Network Based Indicators
The source code and binaries contained multiple Network-Based Indicators (NBIs) having significant overlap with CARBANAK backdoor activity and FIN7 operations previously observed and documented by FireEye. Table 7 shows these indicators along with the associated FireEye public documentation. This includes the status of each NBI as it was encountered (active in source code, commented out, or compiled into a binary). Domain names are de-fanged to prevent accidental resolution or interaction by browsers, chat clients, etc.
NBI | Status | Threat Group Association |
comixed[.]org | Commented out | |
194.146.180[.]40 | Commented out | |
aaaabbbbccccc[.]org | Active |
|
stats10-google[.]com | Commented out | |
192.168.0[.]100:700 | Active |
|
80.84.49[.]50:443 | Commented out |
|
52.11.125[.]44:443 | Commented out |
|
85.25.84[.]223 | Commented out |
|
qwqreererwere[.]com | Active |
|
akamai-technologies[.]org | Commented out | |
192.168.0[.]100:700 | Active |
|
37.1.212[.]100:700 | Commented out |
|
188.138.98[.]105:710 | Commented out | |
hhklhlkhkjhjkjk[.]org |
Compiled |
|
192.168.0[.]100:700 | Compiled |
|
aaa.stage.4463714.news.meteonovosti[.]info | Compiled | DNS infrastructure overlap with later FIN7 associated POWERSOURCE activity |
193.203.48[.]23:800 | Active |
Table 7: NBIs and prevously observed activity
Four of these TCP endpoints (80.84.49[.]50:443, 52.11.125[.]44:443, 85.25.84[.]223, and 37.1.212[.]100:700) were new to me, although some have been documented elsewhere.
Conclusion
Our analysis of this source code dump confirmed it was CARBANAK and turned up a few new and interesting data points. We were able to notify vendors about disclosures that specifically targeted their security suites. The previously documented NBIs, Windows API function resolution, backdoor command hash values, usage of Windows cabinet file APIs, and other artifacts associated with CARBANAK all match, and as they say, if the shoe fits, wear it. Interestingly though, the project itself isn’t called CARBANAK or even Anunak as the information security community has come to call it based on the string artifacts found within the malware. The authors mainly refer to the malware as “bot” in the Visual Studio project, filenames, source code comments, output binaries, user interfaces, and manuals.
The breadth and depth of this analysis was a departure from the usual requests we receive on the FLARE team. The journey included learning some Russian, searching through a hundred thousand of lines of code for new information, and analyzing a few dozen binaries. In the end, I’m thankful I had the opportunity to take this request.
In the next post, Tom Bennett takes the reins to provide a retrospective on his and Barry Vengerik’s previous analysis in light of the source code. Part Four of CARBANAK Week is available as well.
...moreScranos – A Cross Platform, Rootkit-Enabled Spyware rapidly spreading

Published: 2019-04-16 11:30:57
Popularity: 79
Author: Pierluigi Paganini
Keywords:
Scranos is a powerful cross-platform rootkit-enabled spyware discovered while investigating malware posing as legitimate software like video players, drivers and even anti-virus products. The Scranos rootkit malware was first discovered late last year when experts at Bitdefender were analyzing a new password- and data-stealing operation leveraging around a rootkit driver digitally signed with a stolen […] The post Scranos – A Cross Platform, Rootkit-Enabled Spyware rapidly spreading appeared first on Security Affairs.
...moreFrom Fileless Techniques to Using Steganography: Examining Powload’s Evolution

Published: 2019-03-12 15:31:16
Popularity: 66
Author: Trend Micro
Keywords:
🤖: "Malware evolution"
In some of the recent Powload-related incidents we saw, we noticed significant changes to some of the attachments in the spam emails: the use of steganography and targeting of specific countries. Figure 2 shows the difference. For example, the samples we analyzed in early 2018 had more straightforward infection chains. These updates added another stage to the execution of malicious routines as a way to evade detection. The Powload variants that use these techniques drop and execute the Ursnif and Bebloh data stealers. We did not see any notable differences in the payloads’ routines. The distribution tactics also resemble a spam campaign we uncovered last year, which delivered the same information stealers but distributed via the Cutwail botnet. The post From Fileless Techniques to Using Steganography: Examining Powload’s Evolution appeared first on .
...moreThreat actors exploit Atlassian Confluence bug in cryptomining campaigns

Published: 2024-08-30 08:12:43
Popularity: 21
Author: Pierluigi Paganini
Keywords:
🤖: "Crypto mining chaos"
Threat actors are actively exploiting a critical flaw in the Atlassian Confluence Data Center and Confluence Server in cryptocurrency mining campaigns. The critical vulnerability CVE-2023-22527 (CVSS score 10.0) in the Atlassian Confluence Data Center and Confluence Server is being actively exploited for cryptojacking campaigns. The vulnerability is a template injection vulnerability that can allow remote […]
...moreNew Backdoor Auto-color Linux Targets Systems in US and Asia

Published: 2025-02-27 19:43:42
Popularity: 11
Author: Deeba Ahmed
Keywords:
🤖: "Backdoored systems"
Auto-color: New Linux backdoor malware targeting the US and Asia. Learn about its advanced evasion, persistence, and detection…
...moreMalware Infects Linux and macOS via Typosquatted Go Packages

Published: 2025-03-06 16:11:52
Popularity: 14
Author: Deeba Ahmed
Keywords:
🤖: "Typosquatt hack"
Socket exposes a typosquatting campaign delivering malware to Linux and macOS systems via malicious Go packages. Discover the…
...moreRooted Androids 3,000x More Likely to Be Breached, Even iPhones Not Safe

Published: 2025-03-20 14:53:40
Popularity: 12
Author: Waqas
Keywords:
🤖: ""Rooted phones fail""
A new Zimperium report reveals that rooted Android phones and jailbroken iOS devices face growing threats, with advanced toolkits making detection nearly impossible for cybersecurity researchers.
...moreNew Choicejacking Attack Steals Data from Phones via Public Chargers

Published: 2025-07-29 17:06:49
Popularity: 26
Author: Waqas
Keywords:
🤖: "Charging shock!"
Choicejacking is a new USB attack that tricks phones into sharing data at public charging stations, bypassing security prompts in milliseconds.
...more
