Proton has launched 'Docs in Proton Drive,' a free and open-source end-to-end encrypted web-based document editing and collaboration tool. [...]
...moreSummary
Total Articles Found: 239
Top sources:
- BleepingComputer 156
- Security Affairs 60
- Hackread – Latest Cybersecurity, Tech, AI, Crypto & Hacking News 7
- Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto 5
- Dan Goodin – Ars Technica 3
Top Keywords:
- Security: 239
- Breaking News: 58
- Security Affairs: 58
- information security news: 57
- Hacking: 56
Top Authors
- Pierluigi Paganini: 60
- Sergiu Gatlan: 46
- Bill Toulas: 41
- Lawrence Abrams: 26
- Ionut Ilascu: 23
Top Articles:
- Hackers exploit bug in Elementor Pro WordPress plugin with 11M installs
- Adobe Flash Player is officially dead tomorrow
- Kaspersky releases free tool that scans Linux for known threats
- A mishandled GitHub token exposed Mercedes-Benz source code
- New Linux glibc flaw lets attackers get root on major distros
- Signal CEO gives mobile-hacking firm a taste of being hacked
- CosmicStrand UEFI malware found in Gigabyte, ASUS motherboards
- GoDaddy notifies users of breached hosting accounts
- Google Advises Upgrade to Windows 10 to Fix Windows 7 Zero-Day Bug
- Russian-linked Android malware records audio, tracks your location
Proton launches free, privacy-focused Google Docs alternative

Published: 2024-07-03 10:00:00
Popularity: 170
Author: Bill Toulas
Keywords:
🤖: "Proton up!"
Google now pays $250,000 for KVM zero-day vulnerabilities
🤖: "Bug bounty boom"
Google has launched kvmCTF, a new vulnerability reward program (VRP) first announced in October 2023 to improve the security of the Kernel-based Virtual Machine (KVM) hypervisor that comes with $250,000 bounties for full VM escape exploits. [...]
...moreMalicious VSCode extensions with 229M installs found on Microsoft marketplace
🤖: ""Extension Nightmare""
A group of Israeli researchers exploring the limits of VSCode security have managed to "infect" over 100 organizations with a typosquatting Dracula extension that was weaponized with risky code. [...]
...moreASCII art elicits harmful responses from 5 major AI chatbots

Published: 2024-03-16 00:17:24
Popularity: 118
Author: Dan Goodin
Keywords:
LLMs are trained to block harmful responses. Old-school images can override those rules.
...moreNew Linux glibc flaw lets attackers get root on major distros
Unprivileged attackers can get root access on multiple major Linux distributions in default configurations by exploiting a newly disclosed local privilege escalation (LPE) vulnerability in the GNU C Library (glibc). [...]
...moreA mishandled GitHub token exposed Mercedes-Benz source code
A mishandled GitHub token gave unrestricted access to Mercedes-Benz's internal GitHub Enterprise Service, exposing source code to the public. [...]
...moreMultiple flaws in pfSense firewall can lead to arbitrary code execution

Published: 2023-12-15 12:30:23
Popularity: 21
Author: Pierluigi Paganini
Keywords:
Security flaws in Netgate pfSense firewall solution can potentially lead to arbitrary code execution on vulnerable devices. pfSense is a popular open-source firewall solution maintained by Netgate, researchers discovered multiple security issues affecting it. Researchers from SonarCloud discovered several security issues, Cross-Site Scripting (XSS) vulnerabilities and a Command Injection vulnerability in pfSense CE (CVE-2023-42325, CVE-2023-42327, CVE-2023-42326). The […]
...moreBypassing major EDRs using Pool Party process injection techniques

Published: 2023-12-08 15:02:22
Popularity: 44
Author: Pierluigi Paganini
Keywords:
Researchers devised a novel attack vector for process injection, dubbed Pool Party, that evades EDR solutions. Researchers from cybersecurity firm SafeBreach devised a set of process injection techniques, dubbed Pool Party, that allows bypassing EDR solutions. They presented the technique at Black Hat Europe 2023. The experts relied on the less-explored Windows thread pools to discover […]
...moreGoogle fixed critical zero-click RCE in Android

Published: 2023-12-05 08:02:58
Popularity: 19
Author: Pierluigi Paganini
Keywords:
Google fixed a critical zero-click RCE vulnerability (CVE-2023-40088) with the release of the December 2023 Android security updates. Google December 2023 Android security updates addressed 85 vulnerabilities, including a critical zero-click remote code execution (RCE) flaw tracked as CVE-2023-40088. The vulnerability resides in Android’s System component, it doesn’t require additional privileges to be triggered. An […]
...moreHackers earn over $1 million for 58 zero-days at Pwn2Own Toronto
The Pwn2Own Toronto 2023 hacking competition has ended with security researchers earning $1,038,500 for 58 zero-day exploits (and multiple bug collisions) targeting consumer products between October 24 and October 27. [...]
...moreSamsung Galaxy S23 hacked two more times at Pwn2Own Toronto
Security researchers hacked the Samsung Galaxy S23 smartphone two more times on the second day of the Pwn2Own 2023 hacking competition in Toronto, Canada. [...]
...moreHackers can force iOS and macOS browsers to divulge passwords and much more
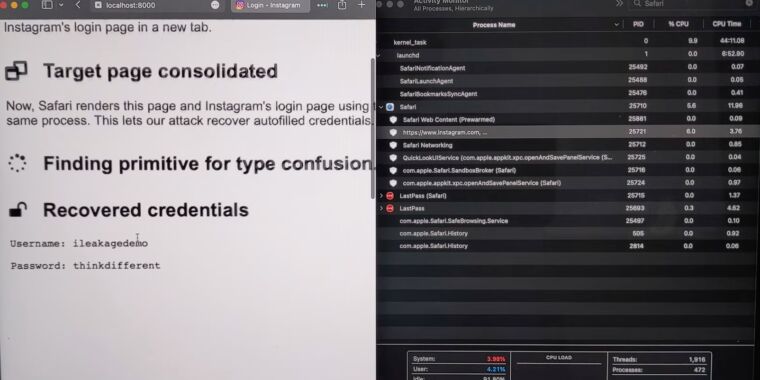
Published: 2023-10-25 17:00:39
Popularity: 157
Author: Dan Goodin
Keywords:
iLeakage is practical and requires minimal resources. A patch isn't (yet) available.
...moreNew sandbox escape PoC exploit available for VM2 library, patch now
Security researchers have released yet another sandbox escape proof of concept (PoC) exploit that makes it possible to execute unsafe code on the host running the VM2 sandbox. [...]
...moreGoogle researchers found multiple security issues in Intel TDX

Published: 2023-04-25 14:07:21
Popularity: 26
Author: Pierluigi Paganini
Keywords:
Google Cloud Security and Project Zero researchers found multiple vulnerabilities in the Intel Trust Domain Extensions (TDX). Google Cloud Security and Project Zero researchers, working with Intel experts, discovered multiple vulnerabilities in the Intel Trust Domain Extensions (TDX). The Intel Trust Domain Extensions (Intel® TDX) allows to deploy hardware-isolated, virtual machines (VMs) called trust domains […] The post Google researchers found multiple security issues in Intel TDX appeared first on Security Affairs.
...moreResearchers found DoS flaws in popular BGP implementation

Published: 2023-05-03 07:17:34
Popularity: 34
Author: Pierluigi Paganini
Keywords:
Vulnerabilities in a software implementation of the Border Gateway Protocol (BGP) that could be weaponized to trigger a DoS condition on BGP peers. Forescout Vedere Labs researchers discovered multiple vulnerabilities in the software implementation of the Border Gateway Protocol (BGP). The issues reside in the BGP message parsing in version 8.4 of FRRouting implementation, a […] The post Researchers found DoS flaws in popular BGP implementation appeared first on Security Affairs.
...moreHackers exploit bug in Elementor Pro WordPress plugin with 11M installs
Hackers are actively exploiting a high-severity vulnerability in the popular Elementor Pro WordPress plugin used by over eleven million websites. [...]
...moreCISA adds Plex Media Server bug, exploited in LastPass attack, to Known Exploited Vulnerabilities Catalog

Published: 2023-03-13 20:43:09
Popularity: 16
Author: Pierluigi Paganini
Keywords:
US CISA added remote code execution vulnerability in Plex Media Server to its Known Exploited Vulnerabilities Catalog. U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a remote code execution (RCE) vulnerability in the Plex Media Server, tracked as CVE-2020-5741 (CVSS score: 7.2), to its Known Exploited Vulnerabilities Catalog. The three-year-old high-severity flaw is a deserialization of […] The post CISA adds Plex Media Server bug, exploited in LastPass attack, to Known Exploited Vulnerabilities Catalog appeared first on Security Affairs.
...moreChick-fil-A confirms accounts hacked in months-long "automated" attack
American fast food chain Chick-fil-A has confirmed that over 71,000 customers' accounts were breached in a months-long credential stuffing attack, allowing threat actors to use stored rewards balances and access personal information. [...]
...moreGoogle will boost Android security through firmware hardening
Google has presented a plan to strengthen the firmware security on secondary Android SoCs (systems on a chip) by introducing mechanisms like control flow integrity, memory safety systems, and compiler-based sanitizers. [...]
...moreLastPass: DevOps engineer hacked to steal password vault data in 2022 breach
LastPass revealed more information on a "coordinated second attack," where a threat actor accessed and stole data from the Amazon AWS cloud storage servers for over two months. [...]
...moreCritical flaws in WordPress Houzez theme exploited to hijack websites
Hackers are actively exploiting two critical-severity vulnerabilities in the Houzez theme and plugin for WordPress, two premium add-ons used primarily in real estate websites. [...]
...moreGoogle Chrome 109 update addresses six security vulnerabilities

Published: 2023-01-25 19:14:36
Popularity: 3
Author: Pierluigi Paganini
Keywords:
Google addressed six security vulnerabilities in its web browser Chrome, none of them actively exploited in the wild. Google released Chrome version 109.0.5414.119 for Mac and Linux and 109.0.5414.119/.120 for Windows to address a total of six vulnerabilities. Four of the addressed flaws were reported by external researchers that were awarded for more than $26,500 for their […] The post Google Chrome 109 update addresses six security vulnerabilities appeared first on Security Affairs.
...more2022 Year in Review

Published: 2022-12-22 16:59:51
Popularity: 24
Author: Cindy Cohn
Keywords:
EFF believes we can create a future where our rights not only follow us online, but are enhanced by new technology. The activists, lawyers, and technologists on EFF’s staff fight for that better future and against the kinds of dystopias best left to speculative fiction. In courts, in legislatures, and in company offices we make sure that the needs of the users are heard. Sometimes we send letters. Sometimes, we send planes. We’ve pushed hard this year and won many hard-fought battles. And in the battles we have not won, we continue on, because it’s important to stand up for what’s right, even if the road is long and rocky. In 2022, we looked into the apps used by daycare centers that collect and share information about the children in their care with their parents. It turned out that not only are the apps dangerously insecure, but the companies that make them were uninterested in making them safer. We responded by giving parents information that they can use to bring their own pressure, including basic recommendations for these applications like implementing two-factor authentication to ensure that this sensitive information about our kids stays in the right hands. We won big in security this year. After years of pressure, Apple has finally implemented one of our longstanding demands: that cloud backups be encrypted. Apple also announced the final death of its dangerous plan to scan your phone. We also continued our fight against police surveillance. Williams v. San Francisco, our lawsuit with the ACLU where the San Francisco Police Department illegally accessed surveillance cameras during the Black Lives Matters protests continues on appeal. Since the lawsuit was filed, the San Francisco Police Department has repeatedly tried to change the law to give the police unwarranted access to third-party cameras. Mayor London Breed introduced and then withdrew a proposal to give the police even more power. The San Francisco Board of Supervisors eventually passed a similar change to the law—but we secured a 15 month sunset. Rest assured, we will be fighting this mass surveillance that sweeps in protests and other First Amendment-protected activity when that sunset date approaches. The camera setback was followed by a dramatic turnaround win, again in San Francisco. In one week the Board of Supervisors reversed its position on giving the SFPD the ability to deploy killer robots. (The SFPD would like you to know that they object to our “killer robots” framing. That’s because the robots do not act on their own or have guns. Instead, they have bombs and explode. We stand by our framing.) Make no mistake: this historic reversal would not have happened without the pushback of the activists. And of course our thanks to the many regular residents of the Bay Area who showed up and made good trouble. Through our representation of the Internet Archive, we also stood up against the four largest publishers who are looking to control how libraries serve their patrons. These publishers want to lock libraries into expensive and restrictive ebook licenses, while claiming, without evidence, that the Internet Archive’s Controlled Digital Lending (CDL) program, is a threat to their business. Libraries give us all knowledge and EFF stands with them. In the European Union, we lobbied hard for a Digital Markets Act that recognized the value of interoperability and meaningfully restrained the power of “gatekeeper” platforms. Finally, sustained pressure from EFF and its allies—and you—kept Congress from mandating filters or link taxes, protecting free expression online. And Congress did some good this year, too, passing the Safe Connections Act, a bill that EFF pushed to make it easier for survivors of domestic violence to keep their phone number while leaving a family plan. This simple protection can be essential to stop abusers from using access to their victims’ cellphone plans to track and harass. It's impossible to cover everything we’ve done this year in a blog post that doesn’t take the whole new year to read. But rest assured, we did a lot and none of it would be possible without our members, supporters, and all of you who stood up and took action to build a better future. EFF has an annual tradition of writing several blog posts on what we’ve accomplished this year, what we’ve learned, and where we have more to do. We will update this page with new stories about digital rights in 2022 every day between now and the new year. A Roller Coaster for Decentralization Daycare and Early Childhood Education Apps Fighting Tech-Enabled Abuse Lifting the Fog Right to Repair Legislation and Advocacy EFF’s Threat Lab Sharpens Its Knives Pivotal Year for the Metaverse and Extended Reality Raising A Glass with EFF Members Hacking Governments and Government Hacking in Latin America The Adoption of the EU's Digital Services Act: A Landmark Year for Platform Regulation Privacy Shouldn't Clock Out When You Clock In The Battle For Online Speech Moved To U.S. Courts Police Drones and Robots The State of Online Free Expression Worldwide Users Worldwide Said "Stop Scanning Us" An Urgent Year for Interoperability Pushing for Strong Digital Rights in the States Surveillance in San Francisco The Year We Got Serious about Tech Monopolies Ending the Scourge of Redlining in Broadband Access Schools and EdTech Need to Study Up On Student Privacy Reproductive Justice and Digital Rights Seeing Patent Trolls Clearly Fighting for the Digital Future of Books Global Cybercrime and Government Access to User Data Across Borders A Year in Internet Surveillance and Resilience Data Sanctuary for Abortion and Trans Health Care
...moreDuckDuckGo now blocks Google sign-in pop-ups on all sites
DuckDuckGo apps and extensions are now blocking Google Sign-in pop-ups on all its apps and browser extensions, removing what it perceives as an annoyance and a privacy risk for its users. [...]
...morePyTorch compromised to demonstrate dependency confusion attack on Python environments

Published: 2023-01-02 18:57:03
Popularity: 19
Author: Pierluigi Paganini
Keywords:
Threat actors compromised the PyTorch Machine Learning Framework by adding a malicious dependency. The maintainers of the PyTorch package warn of a supply chain attack. Users who have installed PyTorch-nightly on Linux via pip between December 25, 2022 and December 30, 2022, to uninstall it and use the latest binaries. “If you installed PyTorch-nightly on […] The post PyTorch compromised to demonstrate dependency confusion attack on Python environments appeared first on Security Affairs.
...moreSamba addressed multiple high-severity vulnerabilities

Published: 2022-12-17 17:29:08
Popularity: 33
Author: Pierluigi Paganini
Keywords:
Samba released updates to address multiple vulnerabilities that can be exploited to take control of impacted systems. Samba released updates to address multiple vulnerabilities, tracked as CVE-2022-38023, CVE-2022-37966, CVE-2022-37967, and CVE-2022-45141, that can be exploited to take control of impacted systems. On December 15, 2022, Samba announced the 4.17.4, 4.16.8 and 4.15.13 security releases to address […] The post Samba addressed multiple high-severity vulnerabilities appeared first on Security Affairs.
...moreHacker claims to be selling Twitter data of 400 million users
A threat actor claims to be selling public and private data of 400 million Twitter users scraped in 2021 using a now-fixed API vulnerability. They're asking $200,000 for an exclusive sale. [...]
...moreEarSpy attack eavesdrops on Android phones via motion sensors
A team of researchers has developed an eavesdropping attack for Android devices that can, to various degrees, recognize the caller's gender and identity, and even discern private speech. [...]
...moreSamsung Galaxy S22 gets hacked in 55 seconds at Pwn2Own Toronto
On the third day of Pwn2Own, contestants hacked the Samsung Galaxy S22 a fourth time since the start of the competition, and this time they did it in just 55 seconds. [...]
...moreMalicious Android app found powering account creation service
A fake Android SMS application, with 100,000 downloads on the Google Play store, has been discovered to secretly act as an SMS relay for an account creation service for sites like Microsoft, Google, Instagram, Telegram, and Facebook [...]
...moreNew ransomware encrypts files, then steals your Discord account
The new 'AXLocker' ransomware family is not only encrypting victims' files and demanding a ransom payment but also stealing the Discord accounts of infected users. [...]
...moreExperts warn of CVE-2022-42889 Text4Shell exploit attempts

Published: 2022-10-21 20:51:28
Popularity: 2
Author: Pierluigi Paganini
Keywords:
Wordfence researchers warn of exploitation attempts targeting the recently disclosed flaw in Apache Commons Text dubbed Text4Shell. Experts at WordPress security firm Wordfence reported exploitation attempts targeting the recently disclosed flaw in Apache Commons Text dubbed Text4Shell. GitHub’s threat analyst Alvaro Munoz this week disclosed a remote code execution vulnerability, tracked as CVE-2022-42889 (CVSS score 9.8), in the open-source Apache Commons […] The post Experts warn of CVE-2022-42889 Text4Shell exploit attempts appeared first on Security Affairs.
...moreMassive cryptomining campaign abuses free-tier cloud dev resources
An automated and large-scale 'freejacking' campaign abuses free GitHub, Heroku, and Buddy services to mine cryptocurrency at the provider's expense. [...]
...moreCloudflare is not affected by the OpenSSL vulnerabilities CVE-2022-3602 and CVE-2022-3786
Published: 2022-11-02 09:31:15
Popularity: None
Author: Evan Johnson
Keywords:
Information on CVE-2022-3602 and CVE-2022-3786, and why Cloudflare was not impacted
...moreDozens of PyPI packages caught dropping 'W4SP' info-stealing malware
Researchers have discovered over two dozen Python packages on the PyPI registry that are pushing info-stealing malware. [...]
...moreGoogle fixes a new actively exploited Chrome zero-day, it is the seventh one this year

Published: 2022-10-28 13:00:33
Popularity: 14
Author: Pierluigi Paganini
Keywords:
Google Thursday released an emergency patch for Chrome 107 to address the actively exploited zero-day vulnerability CVE-2022-3723. Google released an emergency update for the Chrome 107 to address an actively exploited zero-day vulnerability tracked as CVE-2022-3723. The CVE-2022-3723 flaw is a type confusion issue that resides in the Chrome V8 Javascript engine. The flaw has been reported […] The post Google fixes a new actively exploited Chrome zero-day, it is the seventh one this year appeared first on Security Affairs.
...moreFake Microsoft Exchange ProxyNotShell exploits for sale on GitHub
Scammers are impersonating security researchers to sell fake proof-of-concept ProxyNotShell exploits for newly discovered Microsoft Exchange zero-day vulnerabilities. [...]
...moreReflected XSS bugs in Canon Medical ’s Vitrea View could expose patient info

Published: 2022-10-03 06:40:23
Popularity: 15
Author: Pierluigi Paganini
Keywords:
Trustwave researchers discovered two XSS flaws in Canon Medical ’s Vitrea View tool that could expose patient information. During a penetration test, Trustwave Spiderlabs’ researchers discovered two reflected cross-site scripting (XSS) vulnerabilities, collectively as CVE-2022-37461, in third-party software for Canon Medical’s Vitrea View. The Vitrea View tool allows viewing and securely share medical images through […] The post Reflected XSS bugs in Canon Medical ’s Vitrea View could expose patient info appeared first on Security Affairs.
...moreMicrosoft confirms new Exchange zero-days are used in attacks
Microsoft has confirmed that two recently reported zero-day vulnerabilities in Microsoft Exchange Server 2013, 2016, and 2019 are being exploited in the wild. [...]
...moreCryptominers hijack $53 worth of system resources to earn $1
Security researchers estimate that the financial impact of cryptominers infecting cloud servers costs victims about $53 for every $1 worth of cryptocurrency threat actors mine on hijacked devices. [...]
...moreAnnouncing Turnstile, a user-friendly, privacy-preserving alternative to CAPTCHA
Published: 2022-09-28 13:01:00
Popularity: 105
Author: Reid Tatoris
Keywords:
Any website can use a simple API to replace CAPTCHAs with our invisible alternative, whether they’re on the Cloudflare network or not.
...moreThis image shows its own MD5 checksum — and it's kind of a big deal
Generating checksums—cryptographic hashes such as MD5 or SHA-256 functions for files is hardly anything new and one of the most efficient means to ascertain the integrity of a file, or to check if two files are identical. But a researcher has generated an image that visibly contains its own MD5 hash. [...]
...moreAttackers impersonate CircleCI platform to compromise GitHub accounts

Published: 2022-09-25 16:34:04
Popularity: 18
Author: Pierluigi Paganini
Keywords:
Threat actors target GitHub users to steal credentials and two-factor authentication (2FA) codes by impersonating the CircleCI DevOps platform. GitHub is warning of an ongoing phishing campaign targeting its users to steal credentials and two-factor authentication (2FA) codes by impersonating the CircleCI DevOps platform. The company learned of the attacks against its users on September […] The post Attackers impersonate CircleCI platform to compromise GitHub accounts appeared first on Security Affairs.
...moreThis image contains its own MD5 checksum — and it's kind of a big deal
Generating checksums—cryptographic hashes such as MD5 or SHA-256 functions for files is hardly anything new and one of the most efficient means to ascertain the integrity of a file, or to check if two files are identical. But a researcher has generated an image that visibly contains its own MD5 hash. [...]
...moreSignal calls on users to run proxies for bypassing Iran blocks
Signal is urging its global community to help people in Iran stay connected with each other and the rest of the world by volunteering proxies to bypass the aggressive restrictions imposed by the Iranian regime. [...]
...moreMFA Fatigue: Hackers’ new favorite tactic in high-profile breaches
Hackers are more frequently using social engineering attacks to gain access to corporate credentials and breach large networks. One component of these attacks that is becoming more popular with the rise of multi-factor authentication is a technique called MFA Fatigue. [...]
...moreExperts warn of critical flaws in Flexlan devices that provide WiFi on airplanes

Published: 2022-09-19 05:05:15
Popularity: 28
Author: Pierluigi Paganini
Keywords:
Researchers discovered two critical vulnerabilities (CVE–2022–36158 and CVE–2022–36159) in Flexlan devices that provide WiFi on airplanes. Researchers from Necrum Security Labs discovered a couple of critical vulnerabilities, tracked as CVE–2022–36158 and CVE–2022–36159, impacting the Contec Flexlan FXA3000 and FXA2000 series LAN devices. The FXA3000 and FXA2000 Series are access points that are manufactured by Japan-based firm Contec […] The post Experts warn of critical flaws in Flexlan devices that provide WiFi on airplanes appeared first on Security Affairs.
...moreVMware: 70% drop in Linux ESXi VM performance with Retbleed fixes
VMware is warning that ESXi VMs running on Linux kernel 5.19 can have up to a 70% performance drop when Retbleed mitigations are enabled compared to the Linux kernel 5.18 release. [...]
...moreFirmware bugs in many HPE computer models left unfixed for over a year
A set of six high-severity firmware vulnerabilities impacting a broad range of HP Enterprise devices are still waiting to be patched, although some of them were publicly disclosed since July 2021. [...]
...moreGoogle rolled out emergency fixes to address actively exploited Chrome zero-day

Published: 2022-09-03 15:37:55
Popularity: 45
Author: Pierluigi Paganini
Keywords:
Google rolled out emergency fixes to address a vulnerability in the Chrome web browser that is being actively exploited in the wild. Google on Friday released emergency fixes to address a vulnerability, tracked as CVE-2022-3075, in the Chrome web browser that is being actively exploited in the wild. The CVE-2022-3075 flaw is caused by insufficient data […] The post Google rolled out emergency fixes to address actively exploited Chrome zero-day appeared first on Security Affairs.
...moreAn encrypted ZIP file can have two correct passwords — here's why
Password-protected ZIP archives are common means of compressing and sharing sets of files—from sensitive documents to malware samples to even malware (phishing "invoices" in emails). But, did you know it is possible for an encrypted ZIP file to have two correct passwords, with both producing the same outcome on extraction? [...]
...moreNSA and CISA share tips to secure the software supply chain
The U.S. National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) have released guidance today with tips on how to secure the software supply chain. [...]
...moreGitLab ‘strongly recommends’ patching critical RCE vulnerability
GitLab is urging users to install a security update for branches 15.1, 15.2, and 15.3 of its community and enterprise editions to fix a critical vulnerability that could enable an attacker to perform remote command execution via Github import. [...]
...moreWindows malware delays coinminer install by a month to evade detection
A new malware campaign disguised as Google Translate or MP3 downloader programs was found distributing cryptocurrency mining malware across 11 countries. [...]
...more35,000 code repos not hacked—but clones flood GitHub to serve malware
Thousands of GitHub repositories were cloned and altered to include malware, a software engineer discovered. [...]
...moreThousands of Solana wallets drained in attack using unknown exploit
An overnight attack on the Solana blockchain platform drained thousands of software wallets of cryptocurrency worth millions of U.S. dollars. [...]
...moreMalicious npm packages steal Discord users’ payment card info
Multiple npm packages are being used in an ongoing malicious campaign to infect Discord users with malware that steals their payment card information. [...]
...moreCosmicStrand UEFI malware found in Gigabyte, ASUS motherboards
Chinese-speaking hackers have been using since at least 2016 malware that lies virtually undetected in the firmware images for some motherboards, one of the most persistent threats commonly known as a UEFI rootkit. [...]
...moreMicrosoft starts blocking Office macros by default, once again
Microsoft announced today that it resumed the rollout of VBA macro auto-blocking in downloaded Office documents after temporarily rolling it back earlier this month following user feedback. [...]
...moreDrupal developers fixed a code execution flaw in the popular CMS

Published: 2022-07-25 06:21:14
Popularity: 36
Author: Pierluigi Paganini
Keywords:
Drupal development team released security updates to fix multiple issues, including a critical code execution flaw. Drupal developers have released security updates to address multiple vulnerabilities in the popular CMS: Drupal core – Moderately critical – Multiple vulnerabilities – SA-CORE-2022-015 Drupal core – Critical – Arbitrary PHP code execution – SA-CORE-2022-014 Drupal core – Moderately […] The post Drupal developers fixed a code execution flaw in the popular CMS appeared first on Security Affairs.
...moreAtlassian fixes critical Confluence hardcoded credentials flaw
Atlassian has patched a critical hardcoded credentials vulnerability in Confluence Server and Data Center that could let remote, unauthenticated attackers log into vulnerable, unpatched servers. [...]
...moreHoly Ghost ransomware operation linked to North Korean hackers
For more than a year, North Korean hackers have been running a ransomware operation called HolyGhost, attacking small businesses in various countries. [...]
...moreNew Android malware on Google Play installed 3 million times
A new Android malware family on the Google Play Store that secretly subscribes users to premium services was downloaded over 3,000,000 times. [...]
...moreHackers can unlock Honda cars remotely in Rolling-PWN attacks
A team of security researchers found that several modern Honda car models have a vulnerable rolling code mechanism that allows unlocking the cars or even starting the engine remotely. [...]
...moreNew stealthy OrBit malware steals data from Linux devices
A newly discovered Linux malware is being used to stealthily steal information from backdoored Linux systems and infect all running processes on the machine. [...]
...moreOnline programming IDEs can be used to launch remote cyberattacks
Security researchers are warning that hackers can abuse online programming learning platforms to remotely launch cyberattacks, steal data, and scan for vulnerable devices, simply by using a web browser. [...]
...moreAmazon fixes high-severity vulnerability in Android Photos app
Amazon has confirmed and fixed a vulnerability in its Photos app for Android, which has been downloaded over 50 million times on the Google Play Store. [...]
...moreAdobe Acrobat may block antivirus tools from monitoring PDF files
Security researchers found that Adobe Acrobat is trying to block security software from having visibility into the PDF files it opens, creating a security risk for the users. [...]
...moreCritical PHP flaw exposes QNAP NAS devices to RCE attacks
QNAP has warned customers today that many of its Network Attached Storage (NAS) devices are vulnerable to attacks that would exploit a three-year-old critical PHP vulnerability allowing remote code execution. [...]
...moreNew DFSCoerce NTLM Relay attack allows Windows domain takeover
A new Windows NTLM relay attack called DFSCoerce has been discovered that uses MS-DFSNM, Microsoft's Distributed File System, to completely take over a Windows domain. [...]
...moreiCloud hacker gets 9 years in prison for stealing nude photos
A California man who hacked thousands of Apple iCloud accounts was sentenced to 8 years in prison after pleading guilty to conspiracy and computer fraud in October 2021. [...]
...moreThousands of GitHub, AWS, Docker tokens exposed in Travis CI logs
For a second time in less than a year, the Travis CI platform for software development and testing has exposed user data containing authentication tokens that could give access to developers' accounts on GitHub, Amazon Web Services, and Docker Hub. [...]
...morePyPI package 'keep' mistakenly included a password stealer
PyPI packages 'keep,' 'pyanxdns,' 'api-res-py' were found to contain a password-stealer and a backdoor due to the presence of malicious 'request' dependency within some versions. [...]
...morePACMAN, a new attack technique against Apple M1 CPUs

Published: 2022-06-11 13:34:12
Popularity: 48
Author: Pierluigi Paganini
Keywords:
PACMAN is a new attack technique demonstrated against Apple M1 processor chipsets that could be used to hack macOS systems. PACMAN is a novel hardware attack technique that can allow attackers to bypass Pointer Authentication (PAC) on the Apple M1 CPU. The pointer authentication codes (PACs) allow to detect and guard against unexpected changes to pointers in memory. […] The post PACMAN, a new attack technique against Apple M1 CPUs appeared first on Security Affairs.
...moreCritical Atlassian Confluence zero-day actively used in attacks
Hackers are actively exploiting a new Atlassian Confluence zero-day vulnerability tracked as CVE-2022-26134 to install web shells, with no fix available at this time. [...]
...moreResearchers to release exploit for new VMware auth bypass, patch now
Proof-of-concept exploit code is about to be published for a vulnerability that allows administrative access without authentication in several VMware products. [...]
...moreGoogle: Predator spyware infected Android devices using zero-days
Google's Threat Analysis Group (TAG) says that state-backed threat actors used five zero-day vulnerabilities to install Predator spyware developed by commercial surveillance developer Cytrox. [...]
...moreCritical Jupiter WordPress plugin flaws let hackers take over sites
WordPress security analysts have discovered a set of vulnerabilities impacting the Jupiter Theme and JupiterX Core plugins for WordPress, one of which is a critical privilege escalation flaw. [...]
...moreNIST updates guidance for defending against supply-chain attacks
The National Institute of Standards and Technology (NIST) has released updated guidance on securing the supply chain against cyberattacks. [...]
...moreApple emergency update fixes zero-day used to hack Macs, Watches
Apple has released security updates to address a zero-day vulnerability that threat actors can exploit in attacks targeting Macs and Apple Watch devices. [...]
...moreApple fixes the sixth zero-day since the beginning of 2022

Published: 2022-05-16 20:27:49
Popularity: 26
Author: Pierluigi Paganini
Keywords:
Apple released security updates to address a zero-day bug actively exploited in attacks against Macs and Apple Watch devices. Apple has addressed a zero-day vulnerability, tracked as CVE-2022-22675, actively exploited in attacks aimed at Macs and Apple Watch devices. The flaw is an out-of-bounds write issue that resides in the AppleAVD, it can lead to […] The post Apple fixes the sixth zero-day since the beginning of 2022 appeared first on Security Affairs.
...moreHeroku admits that customer credentials were stolen in cyberattack
Heroku has now revealed that the stolen GitHub integration OAuth tokens from last month further led to the compromise of an internal customer database. The Salesforce-owned cloud platform acknowledged the same compromised token was used by attackers to exfiltrate customers' hashed and salted passwords from "a database." [...]
...moreUnpatched DNS bug affects millions of routers and IoT devices
A vulnerability in the domain name system (DNS) component of a popular C standard library that is present in a wide range of IoT products may put millions of devices at DNS poisoning attack risk. [...]
...moreGoogle addresses actively exploited Android flaw in the kernel

Published: 2022-05-05 19:47:00
Popularity: 12
Author: Pierluigi Paganini
Keywords:
Google released the May security bulletin for Android, 2022-05-05 security patch level, which fixed an actively exploited Linux kernel flaw. Google has released the second part of the May Security Bulletin for Android, which includes a fix for an actively exploited Linux kernel vulnerability tracked as CVE-2021-22600. The CVE-2021-22600 is a privilege escalation issue that […] The post Google addresses actively exploited Android flaw in the kernel appeared first on Security Affairs.
...moreA DNS flaw impacts a library used by millions of IoT devices

Published: 2022-05-03 14:44:16
Popularity: 20
Author: Pierluigi Paganini
Keywords:
A vulnerability in the domain name system (DNS) component of the uClibc library impacts millions of IoT products. Nozomi Networks warns of a vulnerability, tracked as CVE-2022-05-02, in the domain name system (DNS) component of the uClibc library which is used by a large number of IoT products. The flaw also affects DNS implementation of all versions of the uClibc-ng […] The post A DNS flaw impacts a library used by millions of IoT devices appeared first on Security Affairs.
...moreNew Nimbuspwn Linux vulnerability gives hackers root privileges
A new set of vulnerabilities collectively tracked as Nimbuspwn could let local attackers escalate privileges on Linux systems to deploy malware ranging from backdoors to ransomware. [...]
...moreCritical flaw in Elementor WordPress plugin may affect 500k sites
The authors of the Elementor Website Builder plugin for WordPress have just released version 3.6.3 to address a critical remote code execution flaw that may impact as many as 500,000 websites. [...]
...moreTrend Micro fixes actively exploited remote code execution bug
Japanese cybersecurity software firm Trend Micro has patched a high severity security flaw in the Apex Central product management console that can let attackers execute arbitrary code remotely. [...]
...moreRussian-linked Android malware records audio, tracks your location
A previously unknown Android malware has been linked to the Turla hacking group after discovering the app used infrastructure previously attributed to the threat actors. [...]
...moreLapsus$ extortion gang leaked the source code for some Microsoft projects

Published: 2022-03-22 09:56:53
Popularity: 16
Author: Pierluigi Paganini
Keywords:
The Lapsus$ extortion group claims to have hacked Microsoft ‘s internal Azure DevOps server and leaked the source code for some projects. Microsoft recently announced that is investigating claims that the Lapsus$ cybercrime gang breached their internal Azure DevOps source code repositories and stolen data. On Sunday, the Lapsus$ gang announced to have compromised Microsoft’s Azure DevOps […] The post Lapsus$ extortion gang leaked the source code for some Microsoft projects appeared first on Security Affairs.
...moreThree critical RCE flaws affect hundreds of HP printer models

Published: 2022-03-22 16:04:19
Popularity: 4
Author: Pierluigi Paganini
Keywords:
Three critical RCE flaws affect hundreds of HP LaserJet Pro, Pagewide Pro, OfficeJet, Enterprise, Large Format, and DeskJet printer models. HP issued a security bulletin warning of a buffer overflow vulnerability, tracked as CVE-2022-3942 (CVSS score 8.4), that could lead to remote code execution on vulnerable devices. “Certain HP Print products and Digital Sending products may […] The post Three critical RCE flaws affect hundreds of HP printer models appeared first on Security Affairs.
...moreAPC UPS zero-day bugs can remotely burn out devices, disable power
A set of three critical zero-day vulnerabilities now tracked as TLStorm could let hackers take control of uninterruptible power supply (UPS) devices from APC, a subsidiary of Schneider Electric. [...]
...morePopular open-source PJSIP library is affected by critical flaws

Published: 2022-03-02 22:41:45
Popularity: 18
Author: Pierluigi Paganini
Keywords:
Researchers from JFrog’s Security Research team discovered five vulnerabilities in the PJSIP open-source multimedia communication library. Researchers from JFrog’s Security Research team discovered five vulnerabilities in the popular PJSIP open-source multimedia communication library. PJSIP is a communication library written in C language implementing standard-based protocols such as SIP, SDP, RTP, STUN, TURN, and ICE. It […] The post Popular open-source PJSIP library is affected by critical flaws appeared first on Security Affairs.
...moreHacking group 'ModifiedElephant' evaded discovery for a decade
Threat analysts have linked a decade of activity to an APT (advanced persistent threat) actor called 'ModifiedElephant', who has managed to remain elusive to all threat intelligence firms since 2012. [...]
...moreCritical RCE flaws in PHP Everywhere WordPress plugin affect thousands of sites

Published: 2022-02-10 10:22:28
Popularity: 15
Author: Pierluigi Paganini
Keywords:
WordPress plugin PHP Everywhere is affected by three critical issues that can be exploited to execute arbitrary code on affected systems. Wordfence experts found three critical remote code execution vulnerabilities in the PHP Everywhere WordPress plugin, all the issues have received a CVSS score of 9.9. The plugin that allows WordPress admins to insert PHP code […] The post Critical RCE flaws in PHP Everywhere WordPress plugin affect thousands of sites appeared first on Security Affairs.
...moreGoogle sees 50% security boost for 150M users after 2FA enroll
After accelerating its efforts to auto-enroll as many accounts as possible in two-factor authentication (2FA), Google announced that an additional 150 million users now have 2FA enabled. [...]
...moreGoogle Project Zero discloses details of two Zoom zero-day flaws

Published: 2022-01-21 14:40:50
Popularity: 7
Author: Pierluigi Paganini
Keywords:
Google Project Zero experts disclosed details of two zero-day flaws impacting Zoom clients and Multimedia Router (MMR) servers. Google Project Zero researchers Natalie Silvanovich disclosed details of two zero-day vulnerabilities in Zoom clients and Multimedia Router (MMR) servers. An attacker could have exploited the now-fixed issues to crash the service, execute malicious code, and even leak the content […] The post Google Project Zero discloses details of two Zoom zero-day flaws appeared first on Security Affairs.
...moreZoho patches new critical authentication bypass in Desktop Central
Zoho has addressed a new critical severity vulnerability found to affect the company's Desktop Central and Desktop Central MSP unified endpoint management (UEM) solutions. [...]
...moreVMware fixed CVE-2021-22045 heap-overflow in Workstation, Fusion and ESXi

Published: 2022-01-06 00:12:35
Popularity: None
Author: Pierluigi Paganini
Keywords:
VMware addressed a heap-overflow issue (CVE-2021-22045) in Workstation, Fusion and CVE-2021-22045 products that can lead to code execution on the hypervisor. VMware released security updates to address a heap-overflow vulnerability, tracked as CVE-2021-22045, in its Workstation, Fusion and ESXi products. VMware has addressed the vulnerability with the release of ESXi670-202111101-SG, ESXi650-202110101-SG, Workstation 16.2.0, and Fusion […] The post VMware fixed CVE-2021-22045 heap-overflow in Workstation, Fusion and ESXi appeared first on Security Affairs.
...moreSwiss army bans all chat apps but locally-developed Threema
The Swiss army has banned foreign instant-messaging apps such as Signal, Telegram, and WhatsApp and requires army members to use the locally-developed Threema messaging app instead. [...]
...moreSEGA Europe left AWS S3 bucket unsecured exposing data and infrastructure to attack

Published: 2022-01-03 14:26:22
Popularity: None
Author: Pierluigi Paganini
Keywords:
SEGA Europe inadvertently left users’ personal information publicly accessible on Amazon Web Services (AWS) S3 bucket. SEGA Europe inadvertently left users’ personal information publicly accessible on Amazon Web Services (AWS) S3 bucket. At the end of the year, gaming giant SEGA Europe inadvertently left users’ personal information publicly accessible on Amazon Web Services (AWS) S3 bucket, cybersecurity firm VPN […] The post SEGA Europe left AWS S3 bucket unsecured exposing data and infrastructure to attack appeared first on Security Affairs.
...moreY2k22 bug in Microsoft Exchange causes failure in email delivery

Published: 2022-01-01 21:44:55
Popularity: None
Author: Pierluigi Paganini
Keywords:
Y2k22 bug is causing Microsoft Exchange on-premise servers to fail in delivering email starting on January 1st, 2022. Microsoft Exchange on-premise servers cannot deliver emails starting on January 1st, 2022, due to a bug in the FIP-FS anti-malware scanning engine dubbed Y2k22 bug. FIP-FS is the anti-malware scanning engine used by Microsoft to protect its […] The post Y2k22 bug in Microsoft Exchange causes failure in email delivery appeared first on Security Affairs.
...moreMultiple flaws in Netgear Nighthawk R6700v3 router are still unpatched

Published: 2021-12-31 14:29:50
Popularity: None
Author: Pierluigi Paganini
Keywords:
Researchers discovered multiple high-risk vulnerabilities affecting the latest firmware version for the Netgear Nighthawk R6700v3 router. Researchers from Tenable have discovered multiple vulnerabilities in the latest firmware version (version 1.0.4.120) of the popular Netgear Nighthawk R6700v3 WiFi router. An attacker can trigger the vulnerabilities to take full control of the vulnerable devices. Below is the […] The post Multiple flaws in Netgear Nighthawk R6700v3 router are still unpatched appeared first on Security Affairs.
...moreTwitter account of FBI's fake chat app, ANOM seen trolling today
The Twitter account previously associated with the ANOM chat app is posting frivolous tweets this week. ANOM was a fake encrypted messaging platform created as part of a global sting operation led by the U.S. FBI, Australian Federal Police (AFP), and other law enforcement agencies to catch criminals. [...]
...moreLog4j 2.17.1 out now, fixes new remote code execution bug
Apache has released another Log4j version, 2.17.1 fixing a newly discovered remote code execution (RCE) vulnerability in 2.17.0, tracked as CVE-2021-44832. Prior to today, 2.17.0 was the most recent version of Log4j and deemed the safest release to upgrade to, but that advice has now evolved. [...]
...moreMalicious PyPI packages with over 10,000 downloads taken down
The Python Package Index (PyPI) registry has removed three malicious Python packages aimed at exfiltrating environment variables and dropping trojans on the infected machines. These malicious packages are estimated to have generated over 10,000 downloads and mirrors put together, according to the researchers' report. [...]
...moreHackers use in-house Zoho ServiceDesk exploit to drop webshells
An advanced persistent threat (APT) group that had been exploiting a flaw in the Zoho ManageEngine ADSelfService Plus software has pivoted to leveraging a different vulnerability in another Zoho product. [...]
...moreExclusive: Resecurity discovered 0-day vulnerability in TP-Link Wi-Fi 6 devices

Published: 2021-11-26 14:39:52
Popularity: None
Author: Pierluigi Paganini
Keywords:
Resecurity researchers found a zero-day vulnerability in the TP-Link enterprise device with model number TL-XVR1800L. Resecurity, a Los Angeles-based cybersecurity company has identified an active a zero-day vulnerability in the TP-Link device with model number TL-XVR1800L (Enterprise AX1800 Dual Band Gigabit Wi-Fi 6 Wireless VPN Router), which is primarily suited to enterprises. The identified vulnerability […] The post Exclusive: Resecurity discovered 0-day vulnerability in TP-Link Wi-Fi 6 devices appeared first on Security Affairs.
...moreFake end-to-end encrypted chat app distributes Android spyware
The GravityRAT remote access trojan is being distributed in the wild again, this time under the guise of an end-to-end encrypted chat application called SoSafe Chat. [...]
...moreMozilla Thunderbird 91.3 released to fix high impact flaws
Mozilla released Thunderbird 91.3 to fix several high-impact vulnerabilities that can cause a denial of service, spoof the origin, bypass security policies, and allow arbitrary code execution. [...]
...moreOver 30,000 GitLab servers still unpatched against critical bug
A critical unauthenticated, remote code execution GitLab flaw fixed on April 14, 2021, remains exploitable, with over 50% of deployments remaining unpatched. [...]
...moreWordPress plugin bug impacts 1M sites, allows malicious redirects
The OptinMonster plugin is affected by a high-severity flaw that allows unauthorized API access and sensitive information disclosure on roughly a million WordPress sites. [...]
...moreBoffins devise a new side-channel attack affecting all AMD CPUs

Published: 2021-10-15 13:50:49
Popularity: None
Author: Pierluigi Paganini
Keywords:
A group of researchers from the Graz University of Technology and CISPA Helmholtz Center for Information Security devised a new side-channel attack that affects AMD CPUs. Researchers Moritz Lipp and Daniel Gruss of the Graz University of Technology and Michael Schwarz of the CISPA Helmholtz Center for Information Security devised a new side-channel attack that […] The post Boffins devise a new side-channel attack affecting all AMD CPUs appeared first on Security Affairs.
...moreMedtronic urgently recalls insulin pump controllers over hacking concerns
Medtronic is urgently recalling remote controllers for insulin pumps belonging to its 'MiniMed Paradigm' family of products, due to potential cybersecurity risks. [...]
...moreThree formers NSA employees fined for providing hacker-for-hire services to UAE firm

Published: 2021-09-15 11:02:17
Popularity: 15
Author: Pierluigi Paganini
Keywords:
Three former NSA employees entered into a deferred prosecution agreement that restricts their future activities and employment and requires the payment of a penalty. Three former NSA employees (Marc Baier, 49, Ryan Adams, 34, and Daniel Gericke, 40) entered into a deferred prosecution agreement that restricts their future activities and employment. The trio has worked as hackers-for-hire […] The post Three formers NSA employees fined for providing hacker-for-hire services to UAE firm appeared first on Security Affairs.
...moreNew Android malware steals millions after infecting 10M phones
A large-scale malware campaign has infected more than 10 million Android devices from over 70 countries and likely stole hundreds of millions from its victims by tricking them into subscribing to paid services without their knowledge. [...]
...moreGoogle patches 10th Chrome zero-day exploited in the wild this year
Google has released Chrome 93.0.4577.82 for Windows, Mac, and Linux to fix eleven security vulnerabilities, two of them being zero-days exploited in the wild. [...]
...moreJenkins project's Confluence server hacked to mine Monero
Hackers exploiting the recently disclosed Atlassian Confluence remote code execution vulnerability breached an internal server from the Jenkins project. [...]
...moreWhatsApp CVE-2020-1910 bug could have led to user data exposure

Published: 2021-09-02 21:20:19
Popularity: None
Author: Pierluigi Paganini
Keywords:
The now-fixed CVE-2020-1910 vulnerability in WhatApp ‘s image filter feature could have exposed user data to remote attackers. A high-severity security vulnerability in WhatApp’s image filter feature, tracked as CVE-2020-1910, could have been exploited by attackers to read sensitive information from the app’s memory by simply sending a specially crafted image over the messaging app […] The post WhatsApp CVE-2020-1910 bug could have led to user data exposure appeared first on Security Affairs.
...moreCVE-2021-3711 in OpenSSL can allow to change an application’s behavior

Published: 2021-08-24 21:43:02
Popularity: 23
Author: Pierluigi Paganini
Keywords:
The OpenSSL Project patched a high-severity vulnerability, tracked as CVE-2021-3711, that can allow an attacker to change an application’s behavior or cause the app to crash. The OpenSSL Project released the OpenSSL 1.1.1l version that addresses a high-severity buffer overflow flaw, tracked as CVE-2021-3711, that could allow an attacker to change an application’s behavior or […] The post CVE-2021-3711 in OpenSSL can allow to change an application’s behavior appeared first on Security Affairs.
...moreAdobe fixes critical flaws in Magento, patch it immediately

Published: 2021-08-11 08:05:34
Popularity: 7
Author: Pierluigi Paganini
Keywords:
Adobe security updates for August 2021 have addressed critical vulnerabilities in Magento and important bugs in Adobe Connect. Adobe security updates for August 2021 address a total of 29 flaws, including critical vulnerabilities in Magento and important issues in Adobe Connect: APSB21-64 Security updates available for Magento APSB21-66 Security update available for Adobe Connect Multiple critical vulnerabilities could be […] The post Adobe fixes critical flaws in Magento, patch it immediately appeared first on Security Affairs.
...moreActively exploited bug bypasses authentication on millions of routers
Threat actors actively exploit a critical authentication bypass vulnerability impacting home routers with Arcadyan firmware to take them over and deploy Mirai botnet malicious payloads. [...]
...moreVMware addresses critical flaws in its products

Published: 2021-08-06 10:29:04
Popularity: None
Author: Pierluigi Paganini
Keywords:
VMware has addressed a critical vulnerability that affects multiple products that could be exploited to gain access to confidential information. VMware has released security updates to address multiple flaws in its products, including a critical issue that could allow an attacker to access confidential information. A couple of vulnerabilities tracked as CVE-2021-22002 and CVE-2021-22003, impact Workspace […] The post VMware addresses critical flaws in its products appeared first on Security Affairs.
...moreCritical Microsoft Hyper-V bug could haunt orgs for a long time
Technical details are now available for a vulnerability that affects Hyper-V, Microsoft's native hypervisor for creating virtual machines on Windows systems and in Azure cloud computing environment. [...]
...moreNew PetitPotam attack allows take over of Windows domains
A new NTLM relay attack called PetitPotam has been discovered that allows threat actors to take over a domain controller, and thus an entire Windows domain. [...]
...moreAkamai DNS global outage takes down major websites, online services
Akamai is investigating an ongoing outage affecting many major websites and online services including Steam, the PlayStation Network, Newegg, AWS, Amazon, Google, and Salesforce. [...]
...moreSoftware maker removes "backdoor" giving root access to radio devices
The author of a popular software-defined radio (SDR) project has removed a "backdoor" from radio devices that granted root-level access. The backdoor had been, according to the author, present in all versions of KiwiSDR devices for the purposes of remote administration and debugging. [...]
...moreMozilla Firefox to roll out DNS over HTTPS for Canadian users
Mozilla has decided to roll out the DNS over HTTPS (DoH) feature by default for Canadian Firefox users later this month. The move comes after DoH has already been offered to US-based Firefox users since 2020. [...]
...moreTwitter now lets you use security keys as the only 2FA method
Twitter now lets users use security keys as the only two-factor authentication (2FA) method while having all other methods disabled, as the social network announced three months ago, in March. [...]
...moreSonicWall addresses critical CVE-2021-20026 flaw in NSM devices

Published: 2021-07-06 17:31:42
Popularity: 7
Author: Pierluigi Paganini
Keywords:
Positive Technologies experts provide details about potential impact of a recently fixes command injection flaw in SonicWall NSM devices. Positive Technologies researcher Nikita Abramov has provided details about the CVE-2021-20026 command injection vulnerability that affects SonicWall’s Network Security Manager (NSM) product. At the end of May, SonicWall urged its customers to ‘immediately’ address a post-authentication vulnerability, tracked […] The post SonicWall addresses critical CVE-2021-20026 flaw in NSM devices appeared first on Security Affairs.
...moreNSA: Russian GRU hackers use Kubernetes to run brute force attacks

Published: 2021-07-01 15:00:00
Popularity: 113
Author: Lawrence Abrams
Keywords:
The National Security Agency (NSA) warns that Russian nation-state hackers are conducting brute force attacks to access US networks and steal email and files. [...]
...moreOnlyFans, Twitter ban users for leaking politician's BDSM video
This week, Twitter and OnlyFans have banned user accounts that illicitly leaked a BSDM video featuring a New York City city council candidate. As reported by Motherboard, the video of 26-year old Zack Weiner began circulating on Twitter and OnlyFans via accounts with identical usernames and profile pictures. [...]
...moreTor Browser fixes vulnerability that tracks you using installed apps
The Tor Project has released Tor Browser 10.0.18 to fix numerous bugs, including a vulnerability that allows sites to track users by fingerprinting the applications installed on their devices. [...]
...moreCVE-2021-3560 flaw in polkit auth system service affects most of Linux distros

Published: 2021-06-12 12:02:50
Popularity: None
Author: Pierluigi Paganini
Keywords:
An authentication bypass flaw in the polkit auth system service used on most Linux distros can allow to get a root shell. An authentication bypass vulnerability in the polkit auth system service, tracked as CVE-2021-3560, which is used on most Linux distros can allow an unprivileged attacker to get a root shell. “A flaw was found […] The post CVE-2021-3560 flaw in polkit auth system service affects most of Linux distros appeared first on Security Affairs.
...moreAdobe issues security updates for 41 vulnerabilities in 10 products
Adobe has released a giant Patch Tuesday security update release that fixes vulnerabilities in ten applications, including Adobe Acrobat, Reader, and Photoshop. [...]
...moreCodecov hackers gained access to Monday.com source code
Monday.com has recently disclosed the impact of the Codecov supply-chain attack that affected multiple companies. As reported by BleepingComputer last month, popular code coverage tool Codecov had been a victim of a supply-chain attack that lasted for two months. [...]
...moreFlaws in Realtek RTL8170C Wi-Fi module allow hijacking wireless communications

Published: 2021-06-03 14:42:15
Popularity: None
Author: Pierluigi Paganini
Keywords:
Researchers found multiple flaws in the Realtek RTL8170C Wi-Fi module that could be exploited to elevate privileges and hijack wireless communications. Researchers from Israeli IoT security firm Vdoo found multiple vulnerabilities in the Realtek RTL8170C Wi-Fi module that could allow to elevate privileges and hijack wireless communications. The Realtek RTL8710C module is based on a […] The post Flaws in Realtek RTL8170C Wi-Fi module allow hijacking wireless communications appeared first on Security Affairs.
...moreGoogle addresses 4 zero-day flaws in Android exploited in the wild

Published: 2021-05-19 18:39:44
Popularity: None
Author: Pierluigi Paganini
Keywords:
Google released Android Security Bulletin for May 2021 security updates that address four zero-day vulnerabilities that were exploited in the wild. Android Security Bulletin for May 2021 security updates address four zero-day vulnerabilities, tracked as CVE-2021-1905, CVE-2021-1906, CVE-2021-28663 and CVE-2021-28664, that were actively exploited in the wild. The four vulnerabilities impact Qualcomm GPU and Arm […] The post Google addresses 4 zero-day flaws in Android exploited in the wild appeared first on Security Affairs.
...moreAnker fixed an issue that caused access to Eufy video camera feeds to random users

Published: 2021-05-24 06:16:06
Popularity: None
Author: Pierluigi Paganini
Keywords:
A misconfiguration issue in the software used by the Eufy video camera exposed private information and video streams of customers. Chinese electronics vendor Anker has recently addressed a bug that mistakenly exposed private information and video streams of customers using its Eufy video cameras. The issue was caused by a misconfiguration, but the vendor told […] The post Anker fixed an issue that caused access to Eufy video camera feeds to random users appeared first on Security Affairs.
...morePython also impacted by critical IP address validation vulnerability
Python 3.3 standard library 'ipaddress' suffers from a critical IP address vulnerability (CVE-2021-29921) identical to the flaw that was reported in the "netmask" library earlier this year. [...]
...moreHashiCorp is the latest victim of Codecov supply-chain attack
Open-source software tools and Vault maker HashiCorp has disclosed a security incident that occurred due to the recent Codecov attack. HashiCorp, a Codecov customer, has stated that the recent Codecov supply-chain attack aimed at collecting developer credentials led to the exposure of HashiCorp's GPG signing key. [...]
...moreSignal CEO gives mobile-hacking firm a taste of being hacked
Software developed by data extraction company Cellebrite contains vulnerabilities that allow arbitrary code execution on the device, claims Moxie Marlinspike, the creator of the encrypted messaging app Signal. [...]
...moreGitHub Actions being actively abused to mine cryptocurrency on GitHub servers
GitHub Actions has been abused by attackers to mine cryptocurrency using GitHub's servers, automatically.The particular attack adds malicious GitHub Actions code to repositories forked from legitimate ones, and further creates a Pull Request for the original repository maintainers to merge the code back, to alter the original code. [...]
...moreExperts found two flaws in Facebook for WordPress Plugin

Published: 2021-03-28 20:56:24
Popularity: None
Author: Pierluigi Paganini
Keywords:
A critical flaw in the official Facebook for WordPress plugin could be abused exploited for remote code execution attacks. Researchers at Wordfence have discovered two vulnerabilities in the Facebook for WordPress plugin, which has more than 500,000 active installations. The plugin allows administrators to capture the actions people take while interacting with their page, such […] The post Experts found two flaws in Facebook for WordPress Plugin appeared first on Security Affairs.
...moreAdobe addresses a critical vulnerability in ColdFusion product

Published: 2021-03-22 20:42:43
Popularity: None
Author: Pierluigi Paganini
Keywords:
Adobe has released security updates to address a critical vulnerability in the ColdFusion product (versions 2021, 2016, and 2018) that could lead to arbitrary code execution. Adobe has released security patches to address a critical vulnerability in Adobe ColdFusion that could be exploited by attackers to execute arbitrary code on vulnerable systems. The issue, tracked as CVE-2021-21087 is […] The post Adobe addresses a critical vulnerability in ColdFusion product appeared first on Security Affairs.
...moreGoogle shares Spectre PoC targeting browser JavaScript engines
Google has published JavaScript proof-of-concept (PoC) code to demonstrate the practicality of using Spectre exploits targeting web browsers to gain access to information from a browser's memory. [...]
...moreVMware addresses a critical RCE issue in vCenter Server
Published: 2021-02-23 22:39:22
Popularity: None
Author: Pierluigi Paganini
Keywords:
VMware addressed a critical remote code execution flaw, tracked as CVE-2021-21972, in vCenter Server virtual infrastructure management platform. VMware has addressed a critical remote code execution (RCE) vulnerability in the vCenter Server virtual infrastructure management platform, tracked as CVE-2021-21972, that could be exploited by attackers to potentially take control of affected systems. vCenter Server is the centralized […] The post VMware addresses a critical RCE issue in vCenter Server appeared first on Security Affairs.
...morePrivacy bug in the Brave browser exposes Tor addresses to user’s DNS provider

Published: 2021-02-19 22:45:28
Popularity: None
Author: Pierluigi Paganini
Keywords:
A privacy bug in the Brave Browser caused the leak of the Tor onion URL addresses visited in the Tor mode by the users. A bug in the Private Window with Tor implemented in the Brave web browser could reveal the onion sites visited by the users. The Tor mode implemented in the Brave web […] The post Privacy bug in the Brave browser exposes Tor addresses to user’s DNS provider appeared first on Security Affairs.
...moreQNAP patches critical vulnerability in Surveillance Station NAS app
QNAP has addressed a critical security vulnerability in the Surveillance Station app that allows attackers to execute malicious code remotely on network-attached storage (NAS) devices running the vulnerable software. [...]
...moreBuggy WordPress plugin exposes 100K sites to takeover attacks
Critical and high severity vulnerabilities in the Responsive Menu WordPress plugin exposed over 100,000 sites to takeover attacks as discovered by Wordfence. [...]
...moreTelegram privacy feature failed to delete self-destructing video files
Telegram has fixed a security issue where self-destructing audio and video recording were not being deleted from user's macOS devices as expected. [...]
...moreApple fixes SUDO root privilege escalation flaw in macOS
Apple has fixed a sudo vulnerability in macOS Big Sur, Catalina, and Mojave, allowing any local user to gain root-level privileges. [...]
...moreThe Great Suspender Chrome extension's fall from grace
Google has forcibly uninstalled the immensely popular 'The Great Suspender' extension from Google Chrome and classified it as malware. [...]
...moreExperts found critical flaws in Realtek Wi-Fi Module

Published: 2021-02-06 21:35:47
Popularity: None
Author: Pierluigi Paganini
Keywords:
Critical flaws in the Realtek RTL8195A Wi-Fi module could have been exploited to gain root access and take over devices’ wireless communications. Researchers from Israeli IoT security firm Vdoo found six vulnerabilities in the Realtek RTL8195A Wi-Fi module that could have been exploited to gain root access and take control of a device’s wireless communications. […] The post Experts found critical flaws in Realtek Wi-Fi Module appeared first on Security Affairs.
...moreMicrosoft: DPRK hackers 'likely' hit researchers with Chrome exploit
Today, Microsoft disclosed that they have also been monitoring the targeted attacks against vulnerability researchers for months and have attributed the attacks to a DPRK group named 'Zinc.' [...]
...moreNSA advises companies to avoid third party DNS resolvers
The US National Security Agency (NSA) says that companies should avoid using third party DNS resolvers to block threat actors' DNS traffic eavesdropping and manipulation attempts and to block access to internal network information. [...]
...moreAdobe is telling Windows 10 users to uninstall Flash Player

Published: 2020-12-30 22:35:33
Popularity: 694
Author: Lawrence Abrams
Keywords:
With the Flash Player officially reaching the end of life tomorrow, Adobe has started to display alerts on Windows computers recommending that users uninstall Flash Player. [...]
...moreAdobe Flash Player is officially dead tomorrow
Flash Player will reach its end of life (EOL) on January 1, 2021, after always being a security risk to those who have used it over the years. [...]
...moreHPE discloses critical zero-day in server management software
Hewlett Packard Enterprise (HPE) has disclosed a zero-day bug in the latest versions of its proprietary HPE Systems Insight Manager (SIM) software for Windows and Linux. [...]
...moreNew Slipstream NAT bypass attacks to be blocked by browsers
Web browser vendors are planning to block a new attack technique that would allow attackers to bypass a victim's NAT/firewall to gain access to any TCP/UDP service hosted on their devices. [...]
...moreHP Device Manager backdoor lets attackers take over Windows systems
HP released a security advisory detailing three critical and high severity vulnerabilities in the HP Device Manager that could lead to system takeover. [...]
...moreGrindr fixed a bug allowing full takeover of any user account
Grindr has fixed a security flaw that could have allowed attackers to easily hijack any Grindr account if they knew the user's email address. [...]
...moreSpeeding up HTTPS and HTTP/3 negotiation with... DNS

Published: 2020-09-30 13:00:00
Popularity: 90
Author: Alessandro Ghedini
Keywords:
A look at a new DNS resource record intended to speed-up negotiation of HTTP security and performance features and how it will help make the web faster.
...moreTutanota encrypted email service suffers DDoS cyberattacks
Encrypted email service, Tutanota has experienced a series of DDoS attacks this week, first targeting the Tutanota website and further its DNS providers. [...]
...moreWindows Zerologon PoC exploits allow domain takeover. Patch Now!
Researchers have released exploits for the Windows Zerologon CVE-2020-1472 vulnerability that allow an attacker to take control of a Windows domain. Install patches now! [...]
...moreOut-of-band security update fixes Adobe Media Encoder issu

Published: 2020-09-15 21:14:42
Popularity: None
Author: Pierluigi Paganini
Keywords:
Adobe has released an out-of-band security update to address three ‘Important’ security vulnerabilities in the Adobe Media Encoder. Adobe has released an out-of-band security update for Adobe Media Encoder that addresses three ‘Important’ Information Disclosure flaws. The three vulnerabilities could be exploited by an attacker to access sensitive information that is leaked in the security […] The post Out-of-band security update fixes Adobe Media Encoder issu appeared first on Security Affairs.
...moreThousands of WordPress WooCommerce stores potentially exposed to hack

Published: 2020-08-22 08:15:04
Popularity: 86
Author: Pierluigi Paganini
Keywords:
Hackers are attempting to exploit multiple vulnerabilities in the Discount Rules for WooCommerce WordPress plugin, which has 30,000+ installations. Researchers from security firm WebArx reported that Hackers are actively attempting to exploit numerous flaws in the Discount Rules for WooCommerce WordPress plugin. The list of vulnerabilities includes SQL injection, authorization flaws, and unauthenticated stored cross-site scripting (XSS) security vulnerabilities. Discount […] The post Thousands of WordPress WooCommerce stores potentially exposed to hack appeared first on Security Affairs.
...moreBusiness technology giant Konica Minolta hit by new ransomware
Business technology giant Konica Minolta was hit with a ransomware attack at the end of July that impacted services for almost a week, BleepingComputer has learned. [...]
...moreKrØØk attack variants impact Qualcomm, MediaTek Wi-Fi chips
Qualcomm and MediaTek Wi-Fi chips were found to have been impacted by new variants of the KrØØk information disclosure vulnerability discovered by ESET researchers Robert Lipovský and Štefan Svorenčík. [...]
...moreCritical Wordpress plugin bug lets hackers take over hosting account
Hackers can exploit a maximum severity vulnerability in the wpDiscuz plugin installed on over 70,000 WordPress sites to execute code remotely after uploading arbitrary files on servers hosting vulnerable sites. (eaf4eb782b57d2f002da312b3ed275fe)[...]
...moreSource code from dozens of companies leaked online
Source code from exposed repositories of dozens of companies across various fields of activity (tech, finance, retail, food, eCommerce, manufacturing) is publicly available as a result of misconfigurations in their infrastructure. [...]
...moreAdobe fixed critical code execution flaws in Bridge, Photoshop and Prelude products

Published: 2020-07-22 06:07:07
Popularity: None
Author: Pierluigi Paganini
Keywords:
This week, Adobe has addressed several critical code execution vulnerabilities in its Bridge, Photoshop and Prelude products. Adobe has released security updates to address several critical code execution vulnerabilities in its Bridge, Photoshop and Prelude products. “Adobe has published security bulletins for Adobe Bridge (APSB20-44), Adobe Photoshop (APSB20-45), Adobe Prelude (APSB20-46) and Adobe Reader Mobile […] The post Adobe fixed critical code execution flaws in Bridge, Photoshop and Prelude products appeared first on Security Affairs.
...moreD-Link blunder: Firmware encryption key exposed in unencrypted image

Published: 2020-07-22 16:01:01
Popularity: 41
Author: Ax Sharma
Keywords:
The router manufacturer leaks encryption keys in some firmware versions letting reverse engineers decrypt the latest firmware images. [...]
...moreMitigating critical F5 BIG-IP RCE flaw not enough, bypass found
F5 BIG-IP customers who only applied recommended mitigations and haven't yet patched their devices against the unauthenticated remote code execution (RCE) CVE-2020-5902 vulnerability are now advised to update them against a recently found bypass. [...]
...moreCisco Talos discloses technicals details of Chrome, Firefox flaws

Published: 2020-07-05 12:33:56
Popularity: 67
Author: Pierluigi Paganini
Keywords:
Cisco’s Talos experts disclosed the details of recently patched vulnerabilities affecting the popular Chrome and Firefox web browsers. Researchers from Cisco Talos disclosed technical details of recently patched vulnerabilities affecting the popular Chrome and Firefox web browsers. The first issue, tracked as CVE-2020-6463, is a memory corruption vulnerability that affects PDFium, an open source PDF […] The post Cisco Talos discloses technicals details of Chrome, Firefox flaws appeared first on Security Affairs.
...moreHundreds arrested after encrypted messaging network takeover
European law enforcement agencies arrested hundreds of suspects in several countries including France, Netherlands, the UK, Norway, and Sweden after infiltrating the EncroChat encrypted mobile communication network used by organized crime groups. [...]
...moreBug in ‘USB for Remote Desktop’ lets hackers add fake devices
An unpatched vulnerability in software that redirects local USB devices to a remote system could help attackers elevate privileges on a target machine by adding fake devices. [...]
...moreCritical Intel Flaws Fixed in Active Management Technology

Published: 2020-06-10 18:37:53
Popularity: 138
Author: Lindsey O'Donnell
Keywords:
Two critical flaws in Intel AMT, which could enable privilege escalation, were patched along with 20 other bugs in its June security update.
...moreA high-severity flaw affects VMware Workstation, Fusion and vSphere products.
Published: 2020-06-10 23:41:49
Popularity: None
Author: Pierluigi Paganini
Keywords:
VMware has addressed a high-severity information disclosure vulnerability affecting its Workstation, Fusion and vSphere virtualization products. VMware has addressed a high-severity information disclosure vulnerability, tracked as CVE-2020-3960, that affects its Workstation, Fusion and vSphere virtualization products. The CVE-2020-3960 flaw was discovered by Cfir Cohen, a researcher from Google’s cloud security team. ESXi, Workstation and Fusion […] The post A high-severity flaw affects VMware Workstation, Fusion and vSphere products. appeared first on Security Affairs.
...moreuBlock Origin ad blocker now blocks port scans on most sites
A recent update to an ad block filter list now allows the uBlock Origin extension to block most of the known sites that perform port scans of your local Windows computer. [...]
...moreWindows 10 SMBGhost bug gets public proof-of-concept RCE exploit
Working exploit code that achieves remote code execution on Windows 10 machines is now publicly available for CVE-2020-0796, a critical vulnerability in Microsoft Server Message Block (SMB 3.1.1). [...]
...moreGoDaddy notifies users of breached hosting accounts
GoDaddy notified some of its customers that it had to reset their passwords after an unauthorized party used their web hosting account credentials to connect to their hosting account via SSH. [...]
...moreDDR4 Memory Still At Rowhammer Risk, New Method Bypasses Fixes
Academic researchers testing modern memory modules from Samsung, Micron, and Hynix discovered that current protections against Rowhammer attacks are insufficient. [...]
...moreCritical Android Bluetooth Flaw Exploitable without User Interaction
Android users are urged to apply the latest security patches released for the operating system on Monday that address a critical vulnerability in the Bluetooth subsystem. [...]
...moreMicrosoft announces the launch of a bug bounty program for Xbox

Published: 2020-02-02 13:00:11
Popularity: 38
Author: Pierluigi Paganini
Keywords:
Microsoft announced the launch of an Xbox bug bounty program with rewards of up to $20,000 for critical remote code execution flaws. Microsoft is going to launch an Xbox bug bounty program that will pay rewards of up to $20,000 for critical remote code execution vulnerabilities. “The Xbox Bounty Program invites gamers, security researchers, and […] The post Microsoft announces the launch of a bug bounty program for Xbox appeared first on Security Affairs.
...moreLeaked confidential report states United Nations has been hacked

Published: 2020-01-30 08:35:24
Popularity: 113
Author: Pierluigi Paganini
Keywords:
A leaked confidential report from the United Nations revealed that dozens of servers belonging to United Nations were “compromised” at offices in Geneva and Vienna. An internal confidential report from the United Nations that was leaked to The New Humanitarian revealed that dozens of servers of the organization were “compromised” at offices in Geneva and […] The post Leaked confidential report states United Nations has been hacked appeared first on Security Affairs.
...moreCritical Remote Code Execution Bug Fixed in OpenBSD SMTP Server
A critical vulnerability in the free OpenSMTPD email server present in many Unix-based systems can be exploited to run shell commands with root privileges. [...]
...moreKali Linux Adds Single Installer Image, Default Non-Root User
Kali Linux 2020.1 was released today by Kali Linux team at Offensive Security with a new Kali Single Installer image for all desktop environments and a previously announced move to a non-root default user. [...]
...moreMicrosoft's IE Zero-day Fix is Breaking Windows Printing
Published: 2020-01-26 17:35:12
Popularity: 769
Author: Lawrence Abrams
Keywords:
Microsoft's temporary fix for a recently disclosed Internet Explorer zero-day vulnerability is causing numerous problems in Windows, including breaking printing for some users. [...]
...moreMDhex Critical Vulnerabilities Shake the Healthcare Sector
Critical vulnerabilities have been discovered in popular medical devices from GE Healthcare that could allow attackers to alter the way they function or render them unusable. [...]
...more10% of All Macs Shlayered, Malware Cocktail Served
Many people think that malware only targets Windows and that Macs are safe, but a new report shows how a single Apple malware called Shlayer has attacked over 10% of all Apple computers monitored by an antivirus company. [...]
...moreHacker Leaks More Than 500K Telnet Credentials for IoT Devices

Published: 2020-01-21 11:57:20
Popularity: 568
Author: Elizabeth Montalbano
Keywords:
Bad actor obtained passwords for servers, home routers, and smart devices by scanning internet for devices open to the Telnet port.
...moreUS Govt Warns of Attacks on Unpatched Pulse VPN Servers
The US Cybersecurity and Infrastructure Security Agency (CISA) today alerted organizations to patch their Pulse Secure VPN servers as a defense against ongoing attacks trying to exploit a known remote code execution (RCE) vulnerability. [...]
...moreThe ProtonCalendar security model
This article documents ProtonCalendar’s security model and illustrates how our product protects calendar-related sensitive data. We examine the advantages and limitations of our approach. This document is somewhat technical, discussing how encryption protects the different layers of data. Still, it is meant to be accessible to a general audience and attempts to explain how ProtonCalendar … The post The ProtonCalendar security model appeared first on ProtonMail Blog.
...moreTor Project is going to remove End-Of-Life relays from the network

Published: 2019-10-10 11:14:28
Popularity: 29
Author: Pierluigi Paganini
Keywords:
🤖: "Tor dropouts"
Maintainers at the Tor Project have removed from its network more than 800 relay servers running outdated and EOL versions of the Tor software. Currently, the Tor network is composed of more than 6000 relays, some of them running outdated Tor software versions (in some cases back to the 0.2.4.x versions). Other relays are running […] The post Tor Project is going to remove End-Of-Life relays from the network appeared first on Security Affairs.
...moreHacker Selling User Info Stolen From Prostitution Forums
Popular prostitution and escort forums in the Netherlands and Italy have suffered data breaches that exposed the usernames, email addresses, and hashed passwords for their registered members. [...]
...moreBulletproof Hosting Service in Former NATO Bunker Goes Down
Authorities in Germany this week shut down the services of a bulletproof hosting provider set up in a former NATO bunker that went five floors underground. [...]
...moreNew Masad Stealer Malware Exfiltrates Crypto Wallets via Telegram
A new and actively distributed malware strain dubbed Masad Stealer steals files, browser information, and cryptocurrency wallet data from infected computers that get sent back to its masters using Telegram as a communication channel. [...]
...moreDoorDash Data Breach Impacts Personal Data of Almost 5M Users

Published: 2019-09-26 21:34:14
Popularity: 436
Author: Lindsey O'Donnell
Keywords:
Accessed information includes delivery addresses, license numbers, names, phone numbers and more.
...moreNew York Passes Law to Update Data Breach Notification Requirements
New York Governor Andrew M. Cuomo signed the Stop Hacks and Improve Electronic Data Security (SHIELD) Act into law, with the new consumer privacy policy being designed to protect New Yorkers' private data and strengthen the state's data breach policies. [...]
...moreRobinhood Brokerage Firm Alerts of Passwords Stored in Clear Text
The Robinhood stock trading site is alerting users that passwords were stored in their system in human readable format, otherwise known as clear text. While no foul play was detected, this could have allowed employees or unauthorized users to view an account's password. [...]
...moreMicrosoft-Owned GitHub Limits Devs in US-Sanctioned Countries
A developer in the Eastern European region of Crimea has found himself at the receiving end of limitations to his GitHub account due to trade control regulations imposed by the US. [...]
...moreUnofficial Telegram App with 100K Installs Pushed Malicious Sites
An app styling itself as a more feature-rich unofficial version of Telegram was installed over 100,000 from Google Play only to provide minimum messaging services and to promote malicious websites. [...]
...moreFake DeepNude Downloads Gives You Malware Instead of Nudes
Cybercriminals are using the notoriety of the DeepNude app to distribute info-stealing malware in campaigns over YouTube that promise a cracked premium version of the program for Windows, Android, and iOS. [...]
...moreBillions of Records Including Passwords Leaked by Smart Home Vendor
A publicly accessible ElasticSearch cluster owned by Orvibo, a Chinese smart home solutions provider, leaked more than two billion user logs containing sensitive data of customers from countries all over the world. [...]
...moreBotnet Uses SSH and ADB to Create Android Cryptomining Army

Published: 2019-06-20 22:46:16
Popularity: 310
Author: Sergiu Gatlan
Keywords:
Researchers discovered a cryptocurrency mining botnet that uses the Android Debug Bridge (ADB) Wi-Fi interface and SSH connections to hosts stored in the known_hosts list to spread to other devices. [...]
...moreRussian military plans to replace Windows with Astra Linux

Published: 2019-06-01 06:55:22
Popularity: 417
Author: Pierluigi Paganini
Keywords:
The Russian army seems to be in the process of replacing the Windows system with the Debian-based Linux distribution Astra Linux. Cyber security seems to subvert the globalization concept, governments are working to develop their own technology fearing possible espionage and sabotage activities of foreign states. The Russian military is in the process of replacing […] The post Russian military plans to replace Windows with Astra Linux appeared first on Security Affairs.
...moreMozilla plans to ban Firefox Extensions containing obfuscated code

Published: 2019-05-04 10:57:46
Popularity: 111
Author: Pierluigi Paganini
Keywords:
Mozilla is going to update the Add-on Policy for Firefox to ban Firefox extensions containing obfuscated code starting from June 10, 2019. Mozilla announced a change to the Add-on Policy for Firefox to ban Firefox extensions containing obfuscated code starting from June 10, 2019. The move aims to prevent malicious extensions to threaten Firefox users. […] The post Mozilla plans to ban Firefox Extensions containing obfuscated code appeared first on Security Affairs.
...moreUK Announces Introduction of Online Pornography Age Checks in July
UK's government announced today that new age-verification checks will be put into place to prevent Internet users under the age of 18 to access and watch online pornography starting with July 15. [...]
...moreEvernote Fixes Remote Code Execution Vulnerability in macOS App
A local file path traversal vulnerability which allows attackers to run arbitrary code on their targets' Macs remotely was fixed by Evernote after receiving a report from security researcher Dhiraj Mishra. [...]
...moreGoogle Advises Upgrade to Windows 10 to Fix Windows 7 Zero-Day Bug
Google recommends users of Windows 7 to give it up and move to Microsoft's latest operating system if they want to keep systems safe from a zero-day vulnerability exploited in the wild. [...]
...moreHackers use DNS tunneling for network scanning, tracking victims
Threat actors are using Domain Name System (DNS) tunneling to track when their targets open phishing emails and click on malicious links, and to scan networks for potential vulnerabilities. [...]
...moreCISA adds GitLab flaw to its Known Exploited Vulnerabilities catalog

Published: 2024-05-02 10:39:40
Popularity: 104
Author: Pierluigi Paganini
Keywords:
CISA adds GitLab Community and Enterprise Editions improper access control vulnerability to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a GitLab Community and Enterprise Editions improper access control vulnerability to its Known Exploited Vulnerabilities (KEV) catalog. The issue, tracked as CVE-2023-7028 (CVSS score: 10.0), is an account takeover via Password Reset. The […]
...moreKaspersky releases free tool that scans Linux for known threats

Published: 2024-06-01 15:17:34
Popularity: 1837
Author: Bill Toulas
Keywords:
🤖: "Linux shield on"
Kaspersky has released a new virus removal tool named KVRT for the Linux platform, allowing users to scan their systems and remove malware and other known threats for free. [...]
...moreAn XSS flaw in GitLab allows attackers to take over accounts

Published: 2024-05-24 20:39:22
Popularity: 16
Author: Pierluigi Paganini
Keywords:
🤖: "Hack alert!"
GitLab addressed a high-severity cross-site scripting (XSS) vulnerability that allows unauthenticated attackers to take over user accounts. GitLab fixed a high-severity XSS vulnerability, tracked as CVE-2024-4835, that allows attackers to take over user accounts. An attacker can exploit this issue by using a specially crafted page to exfiltrate sensitive user information. The vulnerability impacts versions 15.11 before […]
...moreAI-Powered Malware Bypasses All Known Antivirus Solutions, Researchers Warn
🤖: ""AI UhOh""
Researchers have discovered "MalVAI," an AI-powered malware that can bypass all known antivirus solutions by constantly adapting its behavior and code to evade detection. This new threat highlights the obsolescence of traditional cybersecurity methods, prompting an urgent need for AI-driven defense mechanisms. Experts emphasize the necessity for the cybersecurity industry to innovate and develop dynamic solutions capable of evolving alongside sophisticated AI-driven attacks.
...moreResearchers find SQL injection to bypass airport TSA security checks
🤖: "Security hole alert"
Security researchers have found a vulnerability in a key air transport security system that allowed unauthorized individuals to potentially bypass airport security screenings and gain access to aircraft cockpits. [...]
...moreGitLab fixed a critical flaw in GitLab CE and GitLab EE

Published: 2024-09-14 05:02:04
Popularity: 5
Author: Pierluigi Paganini
Keywords:
🤖: ""Git bug squashed""
GitLab addressed multiple vulnerabilities impacting GitLab CE/EE, including a critical pipeline execution issue. GitLab released security patches for 17 vulnerabilities in GitLab CE (Community Edition) and EE (Enterprise Edition). One of these vulnerabilities is a critical pipeline execution flaw, tracked as CVE-2024-6678 (CVSS score of 9.9), that could allow an attacker to trigger a pipeline […]
...moreCritical flaw in NVIDIA Container Toolkit allows full host takeover

Published: 2024-09-29 14:23:34
Popularity: 159
Author: Bill Toulas
Keywords:
🤖: ""host taken over""
A critical vulnerability in NVIDIA Container Toolkit impacts all AI applications in a cloud or on-premise environment that rely on it to access GPU resources. [...]
...moreCisco takes DevHub portal offline after hacker publishes stolen data
🤖: "Security breach"
Cisco confirmed today that it took its public DevHub portal offline after a threat actor leaked "non-public" data, but it continues to state that there is no evidence that its systems were breached. [...]
...moreU.S. CISA adds Veeam Backup and Replication flaw to its Known Exploited Vulnerabilities catalog

Published: 2024-10-19 15:22:13
Popularity: 12
Author: Pierluigi Paganini
Keywords:
🤖: ""Exploit alert!""
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Veeam Backup and Replication vulnerability to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the Veeam Backup and Replication flaw CVE-2024-40711 (CVSS score of 9.8) to its Known Exploited Vulnerabilities (KEV) catalog. This week, Sophos researchers warned that ransomware operators are exploiting the […]
...moreHackers now use ZIP file concatenation to evade detection
🤖: "zip bomb incoming"
Hackers are targeting Windows machines using the ZIP file concatenation technique to deliver malicious payloads in compressed archives without security solutions detecting them. [...]
...moreGitHub projects targeted with malicious commits to frame researcher
🤖: ""Git hacked""
GitHub projects have been targeted with malicious commits and pull requests, in an attempt to inject backdoors into these projects. Most recently, the GitHub repository of Exo Labs, an AI and machine learning startup, was targeted in the attack, which has left many wondering about the attacker's true intentions. [...]
...moreFake Bitwarden ads on Facebook push info-stealing Chrome extension
🤖: "Scam alert!"
Fake Bitwarden password manager advertisements on Facebook are pushing a malicious Google Chrome extension that collects and steals sensitive user data from the browser. [...]
...moreHackers use PoC exploits in attacks 22 minutes after release
🤖: "Exploit train"
Threat actors are quick to weaponize available proof-of-concept (PoC) exploits in actual attacks, sometimes as quickly as 22 minutes after exploits are made publicly available. [...]
...moreNew Backdoor Auto-color Linux Targets Systems in US and Asia

Published: 2025-02-27 19:43:42
Popularity: 11
Author: Deeba Ahmed
Keywords:
🤖: "Backdoored systems"
Auto-color: New Linux backdoor malware targeting the US and Asia. Learn about its advanced evasion, persistence, and detection…
...moreMalware Infects Linux and macOS via Typosquatted Go Packages

Published: 2025-03-06 16:11:52
Popularity: 14
Author: Deeba Ahmed
Keywords:
🤖: "Typosquatt hack"
Socket exposes a typosquatting campaign delivering malware to Linux and macOS systems via malicious Go packages. Discover the…
...moreOracle Denies Breach Amid Hacker’s Claim of Access to 6 Million Records

Published: 2025-03-22 13:29:00
Popularity: 17
Author: Deeba Ahmed
Keywords:
🤖: ""Hacked again""
Oracle denies breach claims as hacker alleges access to 6 million cloud records. CloudSEK reports a potential zero-day exploit affecting 140,000 tenants.
...moreRooted Androids 3,000x More Likely to Be Breached, Even iPhones Not Safe

Published: 2025-03-20 14:53:40
Popularity: 12
Author: Waqas
Keywords:
🤖: ""Rooted phones fail""
A new Zimperium report reveals that rooted Android phones and jailbroken iOS devices face growing threats, with advanced toolkits making detection nearly impossible for cybersecurity researchers.
...moreTwitter (X) Hit by 2.8 Billion Profile Data Leak in Alleged Insider Job

Published: 2025-03-29 15:02:45
Popularity: 223
Author: Waqas
Keywords:
🤖: "Data dump"
Note: Title edited to maintain clarity and accurately reflect the nature of the breach, emphasizing the leak of profile data rather than implying access to private information.
...moreCanon Printer Drivers Flaw Could Let Hackers Run Malicious Code

Published: 2025-04-02 14:11:12
Popularity: 10
Author: Deeba Ahmed
Keywords:
🤖: "Printer hack alert"
A critical vulnerability (CVE-2025-1268) in Canon printer drivers allows remote code execution. See which drivers are affected, how to patch them.
...moreMalicious Code Hits ‘tj-actions/changed-files’ in 23,000 GitHub Repos

Published: 2025-03-17 14:10:44
Popularity: 8
Author: Deeba Ahmed
Keywords:
🤖: "Code injected"
GitHub security alert: Malicious code found in ‘tj-actions/changed-files,’ impacting 23K+ repos. Learn how to check, remove, and protect…
...moreTwo certificate authorities booted from the good graces of Chrome

Published: 2025-06-04 11:20:37
Popularity: 8
Author: Dan Goodin
Keywords:
🤖: "Certificate Fail"
Chunghwa Telecom and Netlock customers must look elsewhere for new certificates.
...moreLinux Crash Reporting Flaws (CVE-2025-5054, 4598) Expose Password Hashes

Published: 2025-06-02 18:21:10
Popularity: 11
Author: Deeba Ahmed
Keywords:
🤖: "Crashing passwords"
Qualys details CVE-2025-5054 and CVE-2025-4598, critical vulnerabilities affecting Linux crash reporting tools like Apport and systemd-coredump. Learn how…
...moreExclusive: Hackers Leak 86 Million AT&T Records with Decrypted SSNs

Published: 2025-06-04 18:31:37
Popularity: 151
Author: Waqas
Keywords:
🤖: ""Data breach alert""
Hackers leak data of 88 million AT&T customers with decrypted SSNs; latest breach raises questions about links to earlier Snowflake-related attack.
...moreCisco warns that Unified CM has hardcoded root SSH credentials
🤖: ""Root access alert!""
Cisco has removed a backdoor account from its Unified Communications Manager (Unified CM), which would have allowed remote attackers to log in to unpatched devices with root privileges. [...]
...moreVerizon and T-Mobile Deny Data Breaches as Millions of User Records Sold Online

Published: 2025-07-02 11:03:12
Popularity: 11
Author: Waqas
Keywords:
🤖: ""Data Leak""
User claims to sell stolen Verizon and T-Mobile data for millions of users (online Verizon says data is old T-Mobile denies any breach and links to it.
...moreNorwegian Dam Valve Forced Open for Hours in Cyberattack
Published: 2025-06-30 09:42:46
Popularity: 33
Author: Deeba Ahmed
Keywords:
🤖: ""Valve blowout""
Unidentified hackers breached a Norwegian dam's control system in April, opening its valve for hours due to a weak password. Learn how simple vulnerabilities threaten critical infrastructure.
...moreNew Choicejacking Attack Steals Data from Phones via Public Chargers

Published: 2025-07-29 17:06:49
Popularity: 26
Author: Waqas
Keywords:
🤖: "Charging shock!"
Choicejacking is a new USB attack that tricks phones into sharing data at public charging stations, bypassing security prompts in milliseconds.
...more










































































.jpg)