A group of cryptographers have analyzed the eiDAS 2.0 regulation (electronic identification and trust services) that defines the new EU Digital Identity Wallet.
...moreSummary
Total Articles Found: 37
Top sources:
Top Keywords:
- Uncategorized: 37
- vulnerabilities: 8
- cybersecurity: 6
- hacking: 5
- backdoors: 4
Top Authors
- Bruce Schneier: 33
- Dan Goodin: 2
- Paul Ducklin: 1
- Ollie Whitehouse: 1
Top Articles:
- Google Play apps with 150 million installs contain aggressive adware
- Hackers can force iOS and macOS browsers to divulge passwords and much more
- Tesla Remotely Hacked from a Drone
- Apple Adds a Backdoor to iMesssage and iCloud Storage
- Another SolarWinds Orion Hack
- Security Vulnerability of Switzerland’s E-Voting System
- Finding the Location of Telegram Users
- Big bad decryption bug in OpenSSL – but no cause for alarm
- US Space Cybersecurity Directive
- Remotely Exploding Pagers
Security Analysis of the EU’s Digital Wallet

Published: 2024-06-27 11:06:32
Popularity: 16
Author: Bruce Schneier
Keywords:
🤖: "Digital wallet hack"
New Open SSH Vulnerability

Published: 2024-07-03 15:27:11
Popularity: 19
Author: Bruce Schneier
Keywords:
🤖: ""Security Alert!""
It’s a serious one: The vulnerability, which is a signal handler race condition in OpenSSH’s server (sshd), allows unauthenticated remote code execution (RCE) as root on glibc-based Linux systems; that presents a significant security risk. This race condition affects sshd in its default configuration. […] This vulnerability, if exploited, could lead to full system compromise where an attacker can execute arbitrary code with the highest privileges, resulting in a complete system takeover, installation of malware, data manipulation, and the creation of backdoors for persistent access. It could facilitate network propagation, allowing attackers to use a compromised system as a foothold to traverse and exploit other vulnerable systems within the organization...
...moreMicrosoft Executives Hacked
Published: 2024-01-29 12:03:42
Popularity: 12
Author: Bruce Schneier
Keywords:
Microsoft is reporting that a Russian intelligence agency—the same one responsible for SolarWinds—accessed the email system of the company’s executives. Beginning in late November 2023, the threat actor used a password spray attack to compromise a legacy non-production test tenant account and gain a foothold, and then used the account’s permissions to access a very small percentage of Microsoft corporate email accounts, including members of our senior leadership team and employees in our cybersecurity, legal, and other functions, and exfiltrated some emails and attached documents. The investigation indicates they were initially targeting email accounts for information related to Midnight Blizzard itself. ...
...moreNSA Buying Bulk Surveillance Data on Americans without a Warrant
Published: 2024-01-30 12:12:30
Popularity: 6
Author: Bruce Schneier
Keywords:
It finally admitted to buying bulk data on Americans from data brokers, in response to a query by Senator Weyden. This is almost certainly illegal, although the NSA maintains that it is legal until it’s told otherwise. Some news articles.
...moreData Exfiltration Using Indirect Prompt Injection
Published: 2023-12-22 12:05:29
Popularity: 9
Author: Bruce Schneier
Keywords:
Interesting attack on a LLM: In Writer, users can enter a ChatGPT-like session to edit or create their documents. In this chat session, the LLM can retrieve information from sources on the web to assist users in creation of their documents. We show that attackers can prepare websites that, when a user adds them as a source, manipulate the LLM into sending private information to the attacker or perform other malicious activities. The data theft can include documents the user has uploaded, their chat history or potentially specific private information the chat model can convince the user to divulge at the attacker’s behest...
...moreNew Bluetooth Attack
Published: 2023-12-08 12:05:19
Popularity: 20
Author: Bruce Schneier
Keywords:
New attack breaks forward secrecy in Bluetooth. Three news articles: BLUFFS is a series of exploits targeting Bluetooth, aiming to break Bluetooth sessions’ forward and future secrecy, compromising the confidentiality of past and future communications between devices. This is achieved by exploiting four flaws in the session key derivation process, two of which are new, to force the derivation of a short, thus weak and predictable session key (SKC). Next, the attacker brute-forces the key, enabling them to decrypt past communication and decrypt or manipulate future communications...
...moreSecurity Vulnerability of Switzerland’s E-Voting System
Published: 2023-10-17 11:11:43
Popularity: 46
Author: Bruce Schneier
Keywords:
Online voting is insecure, period. This doesn’t stop organizations and governments from using it. (And for low-stakes elections, it’s probably fine.) Switzerland—not low stakes—uses online voting for national elections. Andrew Appel explains why it’s a bad idea: Last year, I published a 5-part series about Switzerland’s e-voting system. Like any internet voting system, it has inherent security vulnerabilities: if there are malicious insiders, they can corrupt the vote count; and if thousands of voters’ computers are hacked by malware, the malware can change votes as they are transmitted. Switzerland “solves” the problem of malicious insiders in their printing office by officially declaring that they won’t consider that threat model in their cybersecurity assessment...
...moreEPA Won’t Force Water Utilities to Audit Their Cybersecurity
Published: 2023-10-24 11:02:03
Popularity: 1
Author: Bruce Schneier
Keywords:
The industry pushed back: Despite the EPA’s willingness to provide training and technical support to help states and public water system organizations implement cybersecurity surveys, the move garnered opposition from both GOP state attorneys and trade groups. Republican state attorneys that were against the new proposed policies said that the call for new inspections could overwhelm state regulators. The attorney generals of Arkansas, Iowa and Missouri all sued the EPA—claiming the agency had no authority to set these requirements. This led to the EPA’s proposal being ...
...moreHackers can force iOS and macOS browsers to divulge passwords and much more
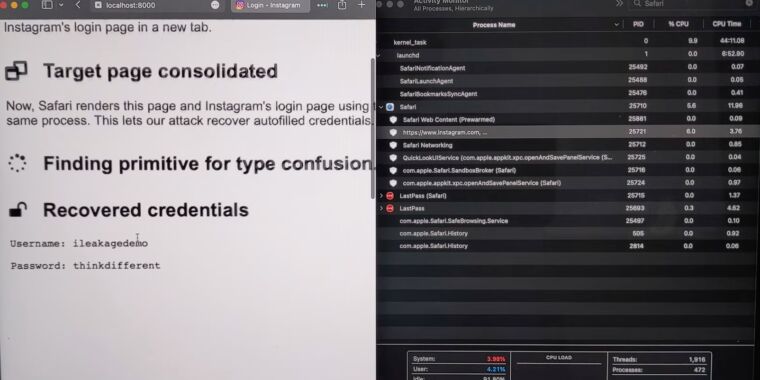
Published: 2023-10-25 17:00:39
Popularity: 157
Author: Dan Goodin
Keywords:
iLeakage is practical and requires minimal resources. A patch isn't (yet) available.
...moreNew Revelations from the Snowden Documents
Published: 2023-09-21 11:03:43
Popularity: 10
Author: Bruce Schneier
Keywords:
Jake Appelbaum’s PhD thesis contains several new revelations from the classified NSA documents provided to journalists by Edward Snowden. Nothing major, but a few more tidbits. Kind of amazing that that all happened ten years ago. At this point, those documents are more historical than anything else. And it’s unclear who has those archives anymore. According to Appelbaum, The Intercept destroyed their copy. I recently published an essay about my experiences ten years ago.
...moreSecurity Risks of New .zip and .mov Domains
Published: 2023-05-19 11:11:52
Popularity: 24
Author: Bruce Schneier
Keywords:
Researchers are worried about Google’s .zip and .mov domains, because they are confusing. Mistaking a URL for a filename could be a security vulnerability.
...moreSignal Phone Numbers Exposed in Twilio Hack

Published: 2022-08-23 11:30:40
Popularity: 9
Author: Bruce Schneier
Keywords:
🤖: ""oops, security breach""
Twilio was hacked earlier this month, and the phone numbers of 1,900 Signal users were exposed: Here’s what our users need to know: All users can rest assured that their message history, contact lists, profile information, whom they’d blocked, and other personal data remain private and secure and were not affected. For about 1,900 users, an attacker could have attempted to re-register their number to another device or learned that their number was registered to Signal. This attack has since been shut down by Twilio. 1,900 users is a very small percentage of Signal’s total users, meaning that most were not affected...
...moreLinux Improves Its Random Number Generator

Published: 2022-03-24 11:38:47
Popularity: 11
Author: Bruce Schneier
Keywords:
🤖: "Randomly good"
In kernel version 5.17, both /dev/random and /dev/urandom have been replaced with a new — identical — algorithm based on the BLAKE2 hash function, which is an excellent security improvement.
...moreZero-Click iMessage Exploit

Published: 2021-09-17 11:09:27
Popularity: 13
Author: Bruce Schneier
Keywords:
🤖: "Sneaky hack"
Citizen Lab released a report on a zero-click iMessage exploit that is used in NSO Group’s Pegasus spyware. Apple patched the vulnerability; everyone needs to update their OS immediately. News articles on the exploit.
...moreBig bad decryption bug in OpenSSL – but no cause for alarm

Published: 2021-08-27 01:03:21
Popularity: 44
Author: Paul Ducklin
Keywords:
The buggy code's in there, alright. Fortunately, it's hard to get OpenSSL to use it even if you want to, which mitigates the risk.
...moreCobalt Strike Vulnerability Affects Botnet Servers

Published: 2021-08-11 11:42:27
Popularity: None
Author: Bruce Schneier
Keywords:
🤖: ""Server hack alert""
Cobalt Strike is a security tool, used by penetration testers to simulate network attackers. But it’s also used by attackers — from criminals to governments — to automate their own attacks. Researchers have found a vulnerability in the product. The main components of the security tool are the Cobalt Strike client — also known as a Beacon — and the Cobalt Strike team server, which sends commands to infected computers and receives the data they exfiltrate. An attacker starts by spinning up a machine running Team Server that has been configured to use specific “malleability” customizations, such as how often the client is to report to the server or specific data to periodically send...
...moreApple Adds a Backdoor to iMesssage and iCloud Storage

Published: 2021-08-10 11:37:30
Popularity: 56
Author: Bruce Schneier
Keywords:
🤖: ""Surveillance mode activated""
Apple’s announcement that it’s going to start scanning photos for child abuse material is a big deal. (Here are five news stories.) I have been following the details, and discussing it in several different email lists. I don’t have time right now to delve into the details, but wanted to post something. EFF writes: There are two main features that the company is planning to install in every Apple device. One is a scanning feature that will scan all photos as they get uploaded into iCloud Photos to see if they match a photo in the database of known child sexual abuse material (CSAM) maintained by the National Center for Missing & Exploited Children (NCMEC). The other feature scans all iMessage images sent or received by child accounts — that is, accounts designated as owned by a minor — for sexually explicit material, and if the child is young enough, notifies the parent when these images are sent or received. This feature can be turned on or off by parents...
...moreChina Taking Control of Zero-Day Exploits

Published: 2021-07-14 11:04:46
Popularity: 5
Author: Bruce Schneier
Keywords:
🤖: "Red flag waving"
China is making sure that all newly discovered zero-day exploits are disclosed to the government. Under the new rules, anyone in China who finds a vulnerability must tell the government, which will decide what repairs to make. No information can be given to “overseas organizations or individuals” other than the product’s manufacturer. No one may “collect, sell or publish information on network product security vulnerabilities,” say the rules issued by the Cyberspace Administration of China and the police and industry ministries. This just blocks the cyber-arms trade. It doesn’t prevent researchers from telling the products’ companies, even if they are outside of China...
...moreApple Will Offer Onion Routing for iCloud/Safari Users

Published: 2021-06-22 11:54:09
Popularity: 9
Author: Bruce Schneier
Keywords:
🤖: "Torified Safari"
At this year’s Apple Worldwide Developer Conference, Apple announced something called “iCloud Private Relay.” That’s basically its private version of onion routing, which is what Tor does. Privacy Relay is built into both the forthcoming iOS and MacOS versions, but it will only work if you’re an iCloud Plus subscriber and you have it enabled from within your iCloud settings. Once it’s enabled and you open Safari to browse, Private Relay splits up two pieces of information that — when delivered to websites together as normal — could quickly identify you. Those are your IP address (who and exactly where you are) and your DNS request (the address of the website you want, in numeric form)...
...moreSecurity Vulnerability in Apple’s Silicon “M1” Chip
🤖: "Chip failure"
The website for the M1racles security vulnerability is an excellent demonstration that not all vulnerabilities are exploitable. Be sure to read the FAQ through to the end. EDITED TO ADD: Wired article.
...moreTesla Remotely Hacked from a Drone

Published: 2021-05-04 14:41:45
Popularity: 65
Author: Bruce Schneier
Keywords:
🤖: "Drone hack attack"
This is an impressive hack: Security researchers Ralf-Philipp Weinmann of Kunnamon, Inc. and Benedikt Schmotzle of Comsecuris GmbH have found remote zero-click security vulnerabilities in an open-source software component (ConnMan) used in Tesla automobiles that allowed them to compromise parked cars and control their infotainment systems over WiFi. It would be possible for an attacker to unlock the doors and trunk, change seat positions, both steering and acceleration modes — in short, pretty much what a driver pressing various buttons on the console can do. This attack does not yield drive control of the car though...
...moreGoogle’s Project Zero Finds a Nation-State Zero-Day Operation

Published: 2021-04-08 11:06:53
Popularity: 12
Author: Bruce Schneier
Keywords:
🤖: "hacked again"
Google’s Project Zero discovered, and caused to be patched, eleven zero-day exploits against Chrome, Safari, Microsoft Windows, and iOS. This seems to have been exploited by “Western government operatives actively conducting a counterterrorism operation”: The exploits, which went back to early 2020 and used never-before-seen techniques, were “watering hole” attacks that used infected websites to deliver malware to visitors. They caught the attention of cybersecurity experts thanks to their scale, sophistication, and speed. […] It’s true that Project Zero does not formally attribute hacking to specific groups. But the Threat Analysis Group, which also worked on the project, does perform attribution. Google omitted many more details than just the name of the government behind the hacks, and through that information, the teams knew internally who the hacker and targets were. It is not clear whether Google gave advance notice to government officials that they would be publicizing and shutting down the method of attack...
...moreAnother SolarWinds Orion Hack

Published: 2021-02-04 12:11:53
Popularity: 48
Author: Bruce Schneier
Keywords:
🤖: ""Network Nightmare""
At the same time the Russians were using a backdoored SolarWinds update to attack networks worldwide, another threat actor — believed to be Chinese in origin — was using an already existing vulnerability in Orion to penetrate networks: Two people briefed on the case said FBI investigators recently found that the National Finance Center, a federal payroll agency inside the U.S. Department of Agriculture, was among the affected organizations, raising fears that data on thousands of government employees may have been compromised. […] Reuters was not able to establish how many organizations were compromised by the suspected Chinese operation. The sources, who spoke on condition of anonymity to discuss ongoing investigations, said the attackers used computer infrastructure and hacking tools previously deployed by state-backed Chinese cyberspies...
...moreFinding the Location of Telegram Users

Published: 2021-01-14 12:08:27
Popularity: 46
Author: Bruce Schneier
Keywords:
🤖: ""Tracking down""
Security researcher Ahmed Hassan has shown that spoofing the Android’s “People Nearby” feature allows him to pinpoint the physical location of Telegram users: Using readily available software and a rooted Android device, he’s able to spoof the location his device reports to Telegram servers. By using just three different locations and measuring the corresponding distance reported by People Nearby, he is able to pinpoint a user’s precise location. […] A proof-of-concept video the researcher sent to Telegram showed how he could discern the address of a People Nearby user when he used a free GPS spoofing app to make his phone report just three different locations. He then drew a circle around each of the three locations with a radius of the distance reported by Telegram. The user’s precise location was where all three intersected...
...moreOblivious DNS-over-HTTPS

Published: 2020-12-08 21:02:08
Popularity: 32
Author: Bruce Schneier
Keywords:
🤖: "DNS fail"
This new protocol, called Oblivious DNS-over-HTTPS (ODoH), hides the websites you visit from your ISP. Here’s how it works: ODoH wraps a layer of encryption around the DNS query and passes it through a proxy server, which acts as a go-between the internet user and the website they want to visit. Because the DNS query is encrypted, the proxy can’t see what’s inside, but acts as a shield to prevent the DNS resolver from seeing who sent the query to begin with. IETF memo. The paper: Abstract: The Domain Name System (DNS) is the foundation of a human-usable Internet, responding to client queries for host-names with corresponding IP addresses and records. Traditional DNS is also unencrypted, and leaks user information to network operators. Recent efforts to secure DNS using DNS over TLS (DoT) and DNS over HTTPS (DoH) havebeen gaining traction, ostensibly protecting traffic and hiding content from on-lookers. However, one of the criticisms ofDoT and DoH is brought to bear by the small number of large-scale deployments (e.g., Comcast, Google, Cloudflare): DNS resolvers can associate query contents with client identities in the form of IP addresses. Oblivious DNS over HTTPS (ODoH) safeguards against this problem. In this paper we ask what it would take to make ODoH practical? We describe ODoH, a practical DNS protocol aimed at resolving this issue by both protecting the client’s content and identity. We implement and deploy the protocol, and perform measurements to show that ODoH has comparable performance to protocols like DoH and DoT which are gaining widespread adoption,while improving client privacy, making ODoH a practical privacy enhancing replacement for the usage of DNS...
...moreUS Space Cybersecurity Directive

Published: 2020-09-09 11:37:47
Popularity: 40
Author: Bruce Schneier
Keywords:
🤖: "Space Alert"
The Trump Administration just published “Space Policy Directive – 5“: “Cybersecurity Principles for Space Systems.” It’s pretty general: Principles. (a) Space systems and their supporting infrastructure, including software, should be developed and operated using risk-based, cybersecurity-informed engineering. Space systems should be developed to continuously monitor, anticipate,and adapt to mitigate evolving malicious cyber activities that could manipulate, deny, degrade, disrupt,destroy, surveil, or eavesdrop on space system operations....
...moreScoutSuite 5.8.0 Released
🤖: "Cyber tools ahead"
Quick note to say we’ve released ScoutSuite 5.8.0 on Github: Improved support for AWS Added support for KMS Added basic support for Secrets Manager Simplified evaluation of IAM policies in multiple rules Improved support for Azure Added support for App Service Web Apps Added support for Security Center Compliance Results Added support for Security Center … Continue reading ScoutSuite 5.8.0 Released →
...moreGoogle Play apps with 150 million installs contain aggressive adware

Published: 2019-03-13 19:51:34
Popularity: 310
Author: Dan Goodin
Keywords:
Google removes 210 apps after outside researchers report them as abusive.
...moreSupply Chain Attack against Courtroom Software

Published: 2024-05-30 11:04:43
Popularity: 3
Author: Bruce Schneier
Keywords:
🤖: "Hacked courtroom"
No word on how this backdoor was installed: A software maker serving more than 10,000 courtrooms throughout the world hosted an application update containing a hidden backdoor that maintained persistent communication with a malicious website, researchers reported Thursday, in the latest episode of a supply-chain attack. The software, known as the JAVS Viewer 8, is a component of the JAVS Suite 8, an application package courtrooms use to record, play back, and manage audio and video from proceedings. Its maker, Louisville, Kentucky-based Justice AV Solutions, says its products are used in more than 10,000 courtrooms throughout the US and 11 other countries. The company has been in business for 35 years...
...moreCloudflare Reports that Almost 7% of All Internet Traffic Is Malicious

Published: 2024-07-17 16:03:20
Popularity: 12
Author: Bruce Schneier
Keywords:
🤖: "Malware alert"
6.8%, to be precise. From ZDNet: However, Distributed Denial of Service (DDoS) attacks continue to be cybercriminals’ weapon of choice, making up over 37% of all mitigated traffic. The scale of these attacks is staggering. In the first quarter of 2024 alone, Cloudflare blocked 4.5 million unique DDoS attacks. That total is nearly a third of all the DDoS attacks they mitigated the previous year. But it’s not just about the sheer volume of DDoS attacks. The sophistication of these attacks is increasing, too. Last August, Cloudflare mitigated a massive HTTP/2 Rapid Reset DDoS attack that peaked at 201 million requests per second (RPS)...
...moreYubiKey Side-Channel Attack

Published: 2024-09-06 15:16:21
Popularity: 3
Author: Bruce Schneier
Keywords:
🤖: ""Leaky key""
There is a side-channel attack against YubiKey access tokens that allows someone to clone a device. It’s a complicated attack, requiring the victim’s username and password, and physical access to their YubiKey—as well as some technical expertise and equipment. Still, nice piece of security analysis.
...morePython Developers Targeted with Malware During Fake Job Interviews

Published: 2024-09-17 11:02:34
Popularity: 10
Author: Bruce Schneier
Keywords:
🤖: "Phishing alert!"
Interesting social engineering attack: luring potential job applicants with fake recruiting pitches, trying to convince them to download malware. From a news article These particular attacks from North Korean state-funded hacking team Lazarus Group are new, but the overall malware campaign against the Python development community has been running since at least August of 2023, when a number of popular open source Python tools were maliciously duplicated with added malware. Now, though, there are also attacks involving “coding tests” that only exist to get the end user to install hidden malware on their system (cleverly hidden with Base64 encoding) that allows remote execution once present. The capacity for exploitation at that point is pretty much unlimited, due to the flexibility of Python and how it interacts with the underlying OS...
...moreRemotely Exploding Pagers

Published: 2024-09-17 15:54:36
Popularity: 34
Author: Bruce Schneier
Keywords:
🤖: "boom!"
Wow. It seems they all exploded simultaneously, which means they were triggered. Were they each tampered with physically, or did someone figure out how to trigger a thermal runaway remotely? Supply chain attack? Malicious code update, or natural vulnerability? I have no idea, but I expect we will all learn over the next few days. EDITED TO ADD: I’m reading nine killed and 2,800 injured. That’s a lot of collateral damage. (I haven’t seen a good number as to the number of pagers yet.) EDITED TO ADD: Reuters writes: “The pagers that detonated were the latest model brought in by Hezbollah in recent months, three security sources said.” That implies supply chain attack. And it seems to be a large detonation for an overloaded battery...
...moreLaw Enforcement Deanonymizes Tor Users

Published: 2024-10-29 11:02:15
Popularity: 24
Author: Bruce Schneier
Keywords:
🤖: "Tor nope"
The German police have successfully deanonymized at least four Tor users. It appears they watch known Tor relays and known suspects, and use timing analysis to figure out who is using what relay. Tor has written about this. Hacker News thread.
...moreSophos Versus the Chinese Hackers

Published: 2024-11-04 12:02:25
Popularity: 10
Author: Bruce Schneier
Keywords:
🤖: "Cyber battle royal"
Really interesting story of Sophos’s five-year war against Chinese hackers.
...moreShredOS

Published: 2025-01-03 14:46:03
Popularity: None
Author: Bruce Schneier
Keywords:
🤖: "Shredded files"
ShredOS is a stripped-down operating system designed to destroy data. GitHub page here.
...moreTroy Hunt Gets Phished

Published: 2025-04-04 11:02:25
Popularity: None
Author: Bruce Schneier
Keywords:
🤖: "phish fail!"
In case you need proof that anyone, even people who do cybersecurity for a living, Troy Hunt has a long, iterative story on his webpage about how he got phished. Worth reading.
...more
