If you're machine failed to get them automatically, you're not alone.
...moreSummary
Total Articles Found: 10
Top sources:
Top Keywords:
- exploits: 10
- Biz & IT: 9
- vulnerabilities: 9
- Policy: 3
- Windows: 2
Top Authors
- Dan Goodin: 9
- Bruce Schneier: 1
Top Articles:
- In epic hack, Signal developer turns the tables on forensics firm Cellebrite
- >20,000 Linksys routers leak historic record of every device ever connected
- Stolen NSA hacking tools were used in the wild 14 months before Shadow Brokers leak
- Multiple “CIA failures” led to theft of agency’s top-secret hacking tools
- Zero-day attackers deliver a double dose of ransomware—no clicking required
- The wave of domain hijackings besetting the Internet is worse than we thought
- Unexpected protection added to Microsoft Edge subverts IE security
- Critical Zoom vulnerabilities fixed last week required no user interaction
- Zero-Click iMessage Exploit
- Serial publisher of Windows 0-days drops exploits for 2 more unfixed flaws
Critical Zoom vulnerabilities fixed last week required no user interaction
Published: 2022-05-26 00:10:27
Popularity: 58
Author: Dan Goodin
Keywords:
Zero-Click iMessage Exploit

Published: 2021-09-17 11:09:27
Popularity: 13
Author: Bruce Schneier
Keywords:
🤖: "Sneaky hack"
Citizen Lab released a report on a zero-click iMessage exploit that is used in NSO Group’s Pegasus spyware. Apple patched the vulnerability; everyone needs to update their OS immediately. News articles on the exploit.
...moreIn epic hack, Signal developer turns the tables on forensics firm Cellebrite
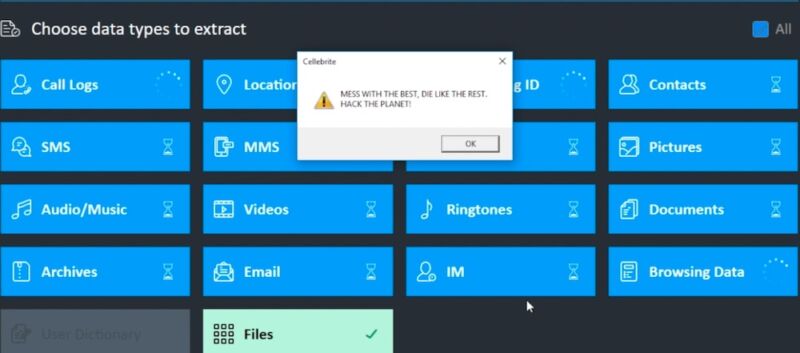
Published: 2021-04-21 19:30:08
Popularity: 3439
Author: Dan Goodin
Keywords:
Widely used forensic software can be exploited to infect investigators' computers.
...moreMultiple “CIA failures” led to theft of agency’s top-secret hacking tools

Published: 2020-06-16 21:06:36
Popularity: 976
Author: Dan Goodin
Keywords:
Vault 7, the worst data theft in CIA history, could have been avoided, report finds.
...more>20,000 Linksys routers leak historic record of every device ever connected

Published: 2019-05-18 11:45:24
Popularity: 1565
Author: Dan Goodin
Keywords:
Linksys said it fixed flaw in 2014. Researcher Troy Mursch disagrees.
...moreSerial publisher of Windows 0-days drops exploits for 2 more unfixed flaws
Published: 2019-05-23 00:41:04
Popularity: None
Author: Dan Goodin
Keywords:
SandboxEscaper has published 7 such exploits to date, 3 in the past 24 hours.
...moreStolen NSA hacking tools were used in the wild 14 months before Shadow Brokers leak

Published: 2019-05-07 06:14:49
Popularity: 1033
Author: Dan Goodin
Keywords:
Already criticized for not protecting its exploit arsenal, the NSA has a new lapse.
...moreZero-day attackers deliver a double dose of ransomware—no clicking required
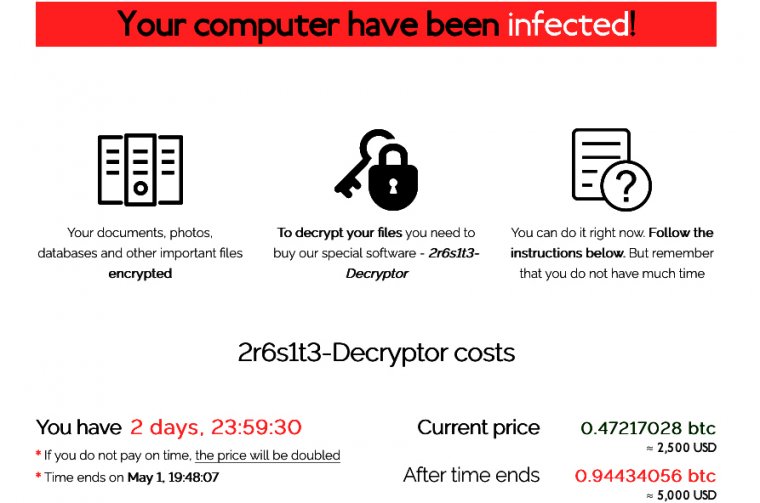
Published: 2019-04-30 19:50:10
Popularity: 953
Author: Dan Goodin
Keywords:
High-severity hole in Oracle WebLogic under active exploit for 9 days. Patch now.
...moreUnexpected protection added to Microsoft Edge subverts IE security

Published: 2019-04-19 12:20:14
Popularity: 360
Author: Dan Goodin
Keywords:
Permissions that Edge added to downloaded files break important security feature.
...moreThe wave of domain hijackings besetting the Internet is worse than we thought

Published: 2019-04-17 15:00:58
Popularity: 822
Author: Dan Goodin
Keywords:
Despite widespread attention since January, DNS campaign shows no signs of abating.
...more