Comments
...moreSummary
Total Articles Found: 7
Top sources:
Top Keywords:
- mobile: 7
- Breaking News: 5
- Mobile: 5
- hacking news: 5
- information security news: 5
Top Authors
Top Articles:
- Threema Goes Open Source, Welcomes New Partner
- Exploiting 0-click Android Bluetooth vulnerability to inject keystrokes without pairing
- Using WiFi connection probe requests to track users
- Google addresses actively exploited Android flaw in the kernel
- Telegram is becoming the paradise of cyber criminals
- WhatsApp CVE-2020-1910 bug could have led to user data exposure
- Flaws in mobile Internet protocol GTP allow hackers to target 5G users
Exploiting 0-click Android Bluetooth vulnerability to inject keystrokes without pairing
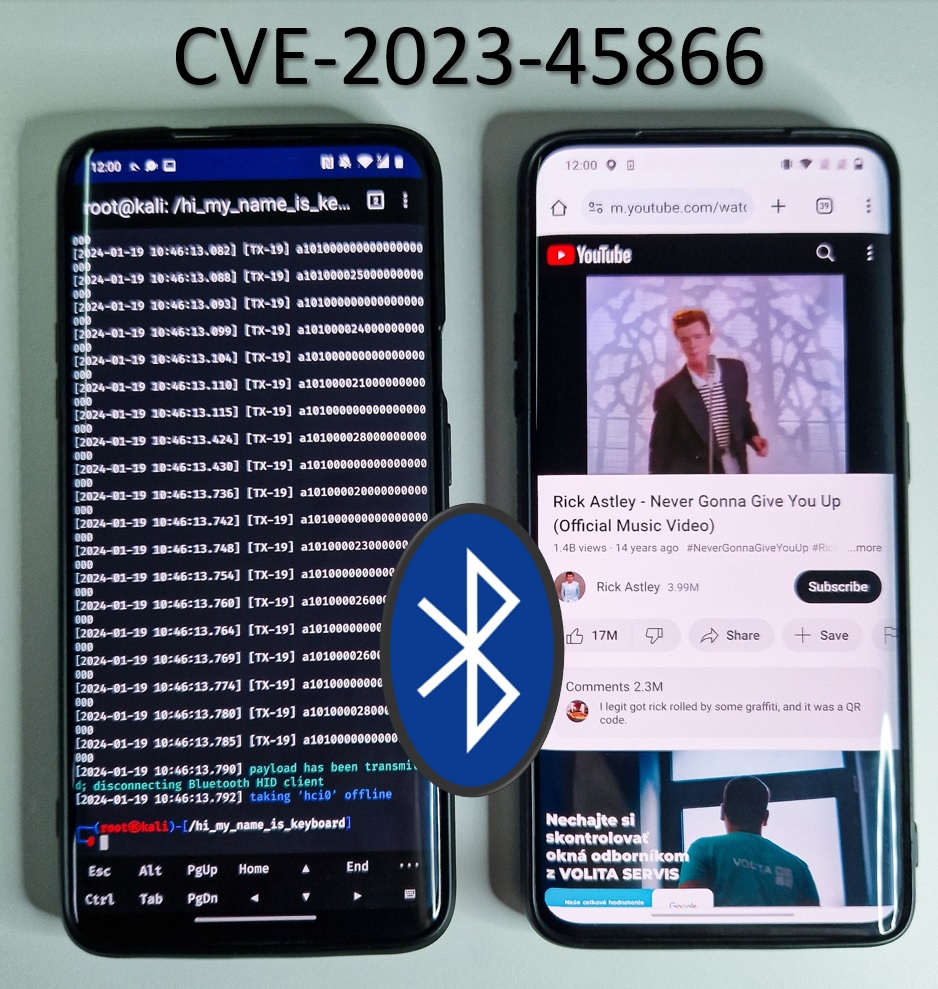
Published: 2024-01-24 10:48:58
Popularity: 162
Author: deejayy@users.lobste.rs (deejayy)
Keywords:
Using WiFi connection probe requests to track users

Published: 2022-06-13 07:52:41
Popularity: 56
Author: Pierluigi Paganini
Keywords:
Researchers at the University of Hamburg demonstrated that WiFi connection probe requests expose users to track. A group of academics at the University of Hamburg (Germany) demonstrated that it is possible to use WiFi connection probe requests to identify and track devices and thereby their users. Mobile devices transmit probe requests to receive information about […] The post Using WiFi connection probe requests to track users appeared first on Security Affairs.
...moreGoogle addresses actively exploited Android flaw in the kernel

Published: 2022-05-05 19:47:00
Popularity: 12
Author: Pierluigi Paganini
Keywords:
Google released the May security bulletin for Android, 2022-05-05 security patch level, which fixed an actively exploited Linux kernel flaw. Google has released the second part of the May Security Bulletin for Android, which includes a fix for an actively exploited Linux kernel vulnerability tracked as CVE-2021-22600. The CVE-2021-22600 is a privilege escalation issue that […] The post Google addresses actively exploited Android flaw in the kernel appeared first on Security Affairs.
...moreTelegram is becoming the paradise of cyber criminals

Published: 2021-09-27 07:56:11
Popularity: None
Author: Pierluigi Paganini
Keywords:
Telegram is becoming an essential platform for cybercriminal activities, crooks use it but and sell any kind of stolen data and hacking tools. Many experts believe that the popular Telegram app is an efficient alternative to dark web marketplaces, its channels are used by hacking communities and cybercriminals to buy and sell stolen data, accesses […] The post Telegram is becoming the paradise of cyber criminals appeared first on Security Affairs.
...moreWhatsApp CVE-2020-1910 bug could have led to user data exposure

Published: 2021-09-02 21:20:19
Popularity: None
Author: Pierluigi Paganini
Keywords:
The now-fixed CVE-2020-1910 vulnerability in WhatApp ‘s image filter feature could have exposed user data to remote attackers. A high-severity security vulnerability in WhatApp’s image filter feature, tracked as CVE-2020-1910, could have been exploited by attackers to read sensitive information from the app’s memory by simply sending a specially crafted image over the messaging app […] The post WhatsApp CVE-2020-1910 bug could have led to user data exposure appeared first on Security Affairs.
...moreThreema Goes Open Source, Welcomes New Partner

Published: 2020-09-04 20:59:39
Popularity: 209
Author: atoponce@users.lobste.rs (atoponce)
Keywords:
Comments
...moreFlaws in mobile Internet protocol GTP allow hackers to target 5G users

Published: 2020-06-15 22:42:36
Popularity: None
Author: Pierluigi Paganini
Keywords:
Security vulnerabilities in modern communication protocol GTP used by mobile network operators can be exploited by attackers to target 4G/5G users. Researchers at cybersecurity firm Positive Technologies Security have discovered several vulnerabilities in communication protocol GPRS Tunnelling Protocol (GTP), that is used by mobile network operators (MNOs). Threat actors could exploit these flaws to conduct several […] The post Flaws in mobile Internet protocol GTP allow hackers to target 5G users appeared first on Security Affairs.
...more