Proton has launched 'Docs in Proton Drive,' a free and open-source end-to-end encrypted web-based document editing and collaboration tool. [...]
...moreSummary
Total Articles Found: 283
Top sources:
- BleepingComputer 283
Top Keywords:
- Security: 156
- Software: 24
- Google: 16
- Technology: 13
- Microsoft: 12
Top Authors
- Sergiu Gatlan: 52
- Bill Toulas: 44
- Lawrence Abrams: 38
- Ionut Ilascu: 23
- Ax Sharma: 21
Top Articles:
- Russia fines Google for spreading ‘unreliable’ info defaming its army
- YouTube-dl GitHub repos taken down by RIAA via DMCA takedown
- ICQ messenger shuts down after almost 28 years
- Hackers exploit bug in Elementor Pro WordPress plugin with 11M installs
- Adobe Flash Player is officially dead tomorrow
- Google outage affecting YouTube, Gmail and more
- Kaspersky releases free tool that scans Linux for known threats
- Firefox Addons Being Disabled Due to an Expired Certificate
- A mishandled GitHub token exposed Mercedes-Benz source code
- New Linux glibc flaw lets attackers get root on major distros
Proton launches free, privacy-focused Google Docs alternative

Published: 2024-07-03 10:00:00
Popularity: 170
Author: Bill Toulas
Keywords:
🤖: "Proton up!"
Google now pays $250,000 for KVM zero-day vulnerabilities
🤖: "Bug bounty boom"
Google has launched kvmCTF, a new vulnerability reward program (VRP) first announced in October 2023 to improve the security of the Kernel-based Virtual Machine (KVM) hypervisor that comes with $250,000 bounties for full VM escape exploits. [...]
...moreMalicious VSCode extensions with 229M installs found on Microsoft marketplace
🤖: ""Extension Nightmare""
A group of Israeli researchers exploring the limits of VSCode security have managed to "infect" over 100 organizations with a typosquatting Dracula extension that was weaponized with risky code. [...]
...moreT-Mobile, Verizon workers get texts offering $300 for SIM swaps

Published: 2024-04-17 14:38:00
Popularity: None
Author: None
Criminals are now texting T-Mobile and Verizon employees on their personal and work phones, trying to tempt them with cash to perform SIM swaps.
...moreHackers abuse QEMU to covertly tunnel network traffic in cyberattacks
Published: 2024-03-05 23:44:51
Popularity: None
Author: None
Malicious actors were detected abusing the open-source hypervisor platform QEMU as a tunneling tool in a cyberattack against a large company.
...moreMalicious AI models on Hugging Face backdoor users’ machines

Published: 2024-03-02 19:33:27
Popularity: None
Author: None
At least 100 instances of malicious AI ML models were found on the Hugging Face platform, some of which can execute code on the victim's machine, giving attackers a persistent backdoor.
...moreCanada to ban the Flipper Zero to stop surge in car thefts

Published: 2024-02-10 15:00:08
Popularity: None
Author: None
The Canadian government plans to ban the Flipper Zero and similar devices after tagging them as tools thieves can use to steal cars.
...moreNew Linux glibc flaw lets attackers get root on major distros
Unprivileged attackers can get root access on multiple major Linux distributions in default configurations by exploiting a newly disclosed local privilege escalation (LPE) vulnerability in the GNU C Library (glibc). [...]
...moreNew Linux glibc flaw lets attackers get root on major distros

Published: 2024-01-31 12:25:34
Popularity: None
Author: None
Unprivileged attackers can get root access on multiple major Linux distributions in default configurations by exploiting a newly disclosed local privilege escalation (LPE) vulnerability in the GNU C Library (glibc).
...moreA mishandled GitHub token exposed Mercedes-Benz source code
A mishandled GitHub token gave unrestricted access to Mercedes-Benz's internal GitHub Enterprise Service, exposing source code to the public. [...]
...moreUK and South Korea: Hackers use zero-day in supply-chain attack

Published: 2023-11-25 21:49:48
Popularity: None
Author: None
A joint advisory by the National Cyber Security Centre (NCSC) and Korea's National Intelligence Service (NIS) discloses a supply-chain attack executed by North Korean hackers involving the MagicLineThe National Cyber Security Centre (NCSC) and Korea's National Intelligence Service (NIS) warn that the North Korean Lazarus hacking grou
...moreMicrosoft: Lazarus hackers breach CyberLink in supply chain attack

Published: 2023-11-22 21:16:27
Popularity: None
Author: None
Microsoft says a North Korean hacking group has breached Taiwanese multimedia software company CyberLink and trojanized one of its installers to push malware in a supply chain attack targeting potential victims worldwide.
...moreCybersecurity firm executive pleads guilty to hacking hospitals

Published: 2023-11-21 17:39:35
Popularity: None
Author: None
The former chief operating officer of a cybersecurity company has pleaded guilty to hacking two hospitals, part of the Gwinnett Medical Center (GMC), in June 2021 to boost his company's business.
...moreHackers exploit Looney Tunables Linux bug, steal cloud creds

Published: 2023-11-07 12:23:40
Popularity: None
Author: None
The operators of the Kinsing malware are targeting cloud environments with systems vulnerable to "Looney Tunables," a Linux security issue identified as CVE-2023-4911 that allows a local attacker to gain root privileges on the system.
...moreHackers earn over $1 million for 58 zero-days at Pwn2Own Toronto
The Pwn2Own Toronto 2023 hacking competition has ended with security researchers earning $1,038,500 for 58 zero-day exploits (and multiple bug collisions) targeting consumer products between October 24 and October 27. [...]
...moreSamsung Galaxy S23 hacked two more times at Pwn2Own Toronto
Security researchers hacked the Samsung Galaxy S23 smartphone two more times on the second day of the Pwn2Own 2023 hacking competition in Toronto, Canada. [...]
...moreCoffee Meets Bagel says recent outage caused by destructive cyberattack

Published: 2023-09-06 23:08:58
Popularity: None
Author: None
The Coffee Meets Bagel dating platform confirms last week's outage was caused by hackers breaching the company's systems and deleting company data.
...moreCritical ColdFusion flaws exploited in attacks to drop webshells

Published: 2023-07-18 10:43:05
Popularity: None
Author: None
Hackers are actively exploiting two ColdFusion vulnerabilities to bypass authentication and remotely execute commands to install webshells on vulnerable servers.
...moreLastPass users furious after being locked out due to MFA resets

Published: 2023-06-25 19:13:46
Popularity: None
Author: None
LastPass password manager users have been experiencing significant login issues starting early May after being prompted to reset their authenticator apps.
...moreMicrosoft finds macOS bug that lets hackers bypass SIP root restrictions

Published: 2023-05-31 19:55:33
Popularity: None
Author: None
Apple has recently addressed a vulnerability that lets attackers with root privileges bypass System Integrity Protection (SIP) to install "undeletable" malware and access the victim's private data by circumventing Transparency, Consent, and Control (TCC) security checks.
...moreWordPress force installs critical Jetpack patch on 5 million sites

Published: 2023-05-31 19:36:36
Popularity: None
Author: None
WordPress.com owner Automat has started force installing a security patch on millions of websites today with the help of the WordPress Security Team to address a critical vulnerability in the Jetpack plug-in.
...moreCybersecurity firm Dragos discloses cybersecurity incident, extortion attempt

Published: 2023-05-11 00:21:49
Popularity: None
Author: None
Industrial cybersecurity company Dragos today disclosed what it describes as a "cybersecurity event" after a known cybercrime gang attempted to breach its defenses and infiltrate the internal network to encrypt devices.
...moreWestern Digital struggles to fix massive My Cloud outage, offers workaround
On Friday, five days into a massive outage impacting its cloud services, Western Digital finally provided customers with a workaround to access their files. [...]
...moreNew sandbox escape PoC exploit available for VM2 library, patch now
Security researchers have released yet another sandbox escape proof of concept (PoC) exploit that makes it possible to execute unsafe code on the host running the VM2 sandbox. [...]
...moreHP to patch critical bug in LaserJet printers within 90 days

Published: 2023-04-05 21:38:30
Popularity: None
Author: None
HP announced in a security bulletin this week that it would take up to 90 days to patch a critical-severity vulnerability that impacts the firmware of certain business-grade printers.
...moreWinRAR SFX archives can run PowerShell without being detected

Published: 2023-04-05 12:13:00
Popularity: None
Author: None
Hackers are adding malicious functionality to WinRAR self-extracting archives that contain harmless decoy files, allowing them to plant backdoors without triggering the security agent on the target system.
...moreExperts call for pause on AI training citing risks to humanity

Published: 2023-04-03 12:25:14
Popularity: None
Author: None
AI professors and developers have co-signed an open letter to artificial intelligence labs, calling them to pause the development and training of AI systems more powerful than GPT-4 for at least six months.
...moreHackers exploit bug in Elementor Pro WordPress plugin with 11M installs
Hackers are actively exploiting a high-severity vulnerability in the popular Elementor Pro WordPress plugin used by over eleven million websites. [...]
...moreGoogle finds 18 zero-day vulnerabilities in Samsung Exynos chipsets

Published: 2023-03-17 12:09:07
Popularity: None
Author: None
Project Zero, Google's zero-day bug-hunting team, discovered and reported 18 zero-day vulnerabilities in Samsung's Exynos chipsets used in mobile devices, wearables, and cars.
...moreBrazil seizing Flipper Zero shipments to prevent use in crime

Published: 2023-03-11 19:02:36
Popularity: None
Author: None
The Brazilian National Telecommunications Agency is seizing incoming Flipper Zero purchases due to its alleged use in criminal activity, with purchasers stating that the government agency has rejected all attempts to certify the equipment.
...moreChick-fil-A confirms accounts hacked in months-long "automated" attack
American fast food chain Chick-fil-A has confirmed that over 71,000 customers' accounts were breached in a months-long credential stuffing attack, allowing threat actors to use stored rewards balances and access personal information. [...]
...moreGoogle will boost Android security through firmware hardening
Google has presented a plan to strengthen the firmware security on secondary Android SoCs (systems on a chip) by introducing mechanisms like control flow integrity, memory safety systems, and compiler-based sanitizers. [...]
...moreLastPass: DevOps engineer hacked to steal password vault data in 2022 breach
LastPass revealed more information on a "coordinated second attack," where a threat actor accessed and stole data from the Amazon AWS cloud storage servers for over two months. [...]
...moreTwitter is down with users seeing "Welcome to Twitter" screen
When attempting to access Twitter's website, users see "Welcome to Twitter!" on the timeline. The alert, typically used for new signups, says, "Twitter is the best place to see what's happening in your world", with a Let's go button that lets you follow some people and topics. [...]
...moreNews Corp says state hackers were on its network for two years

Published: 2023-02-28 13:29:31
Popularity: None
Author: None
Mass media and publishing giant News Corporation (News Corp) says that attackers behind a breach disclosed in 2022 first gained access to its systems two years before, in February 2020.
...moreCritical flaws in WordPress Houzez theme exploited to hijack websites
Hackers are actively exploiting two critical-severity vulnerabilities in the Houzez theme and plugin for WordPress, two premium add-ons used primarily in real estate websites. [...]
...moreCISA: Federal agencies hacked using legitimate remote desktop tools

Published: 2023-01-26 13:48:52
Popularity: None
Author: None
CISA, the NSA, and MS-ISAC warned today in a joint advisory that attackers are increasingly using legitimate remote monitoring and management (RMM) software for malicious purposes.
...moreCircleCI warns of security breach — rotate your secrets!

Published: 2023-01-05 15:34:03
Popularity: None
Author: None
CircleCI, a software development service has disclosed a security incident and is urging users to rotate their secrets. The CI/CD platform touts having a user base comprising more than one million engineers who rely on the service for "speed and reliability" of their builds.
...moreDuckDuckGo now blocks Google sign-in pop-ups on all sites
DuckDuckGo apps and extensions are now blocking Google Sign-in pop-ups on all its apps and browser extensions, removing what it perceives as an annoyance and a privacy risk for its users. [...]
...moreHacker claims to be selling Twitter data of 400 million users
A threat actor claims to be selling public and private data of 400 million Twitter users scraped in 2021 using a now-fixed API vulnerability. They're asking $200,000 for an exclusive sale. [...]
...moreEarSpy attack eavesdrops on Android phones via motion sensors
A team of researchers has developed an eavesdropping attack for Android devices that can, to various degrees, recognize the caller's gender and identity, and even discern private speech. [...]
...moreSamsung Galaxy S22 gets hacked in 55 seconds at Pwn2Own Toronto
On the third day of Pwn2Own, contestants hacked the Samsung Galaxy S22 a fourth time since the start of the competition, and this time they did it in just 55 seconds. [...]
...moreMalicious Android app found powering account creation service
A fake Android SMS application, with 100,000 downloads on the Google Play store, has been discovered to secretly act as an SMS relay for an account creation service for sites like Microsoft, Google, Instagram, Telegram, and Facebook [...]
...moreNew ransomware encrypts files, then steals your Discord account
The new 'AXLocker' ransomware family is not only encrypting victims' files and demanding a ransom payment but also stealing the Discord accounts of infected users. [...]
...moreMassive cryptomining campaign abuses free-tier cloud dev resources
An automated and large-scale 'freejacking' campaign abuses free GitHub, Heroku, and Buddy services to mine cryptocurrency at the provider's expense. [...]
...moreDozens of PyPI packages caught dropping 'W4SP' info-stealing malware
Researchers have discovered over two dozen Python packages on the PyPI registry that are pushing info-stealing malware. [...]
...moreHundreds of U.S. news sites push malware in supply-chain attack

Published: 2022-11-03 11:45:15
Popularity: None
Author: None
🤖: "Malware alert"
The compromised infrastructure of an undisclosed media company is being used by threat actors to deploy the SocGholish JavaScript malware framework (also known as FakeUpdates) on the websites of hundreds of newspapers across the U.S.
...moreFake Microsoft Exchange ProxyNotShell exploits for sale on GitHub
Scammers are impersonating security researchers to sell fake proof-of-concept ProxyNotShell exploits for newly discovered Microsoft Exchange zero-day vulnerabilities. [...]
...moreMicrosoft confirms new Exchange zero-days are used in attacks
Microsoft has confirmed that two recently reported zero-day vulnerabilities in Microsoft Exchange Server 2013, 2016, and 2019 are being exploited in the wild. [...]
...moreCryptominers hijack $53 worth of system resources to earn $1
Security researchers estimate that the financial impact of cryptominers infecting cloud servers costs victims about $53 for every $1 worth of cryptocurrency threat actors mine on hijacked devices. [...]
...moreThis image shows its own MD5 checksum — and it's kind of a big deal
Generating checksums—cryptographic hashes such as MD5 or SHA-256 functions for files is hardly anything new and one of the most efficient means to ascertain the integrity of a file, or to check if two files are identical. But a researcher has generated an image that visibly contains its own MD5 hash. [...]
...moreThis image contains its own MD5 checksum — and it's kind of a big deal
Generating checksums—cryptographic hashes such as MD5 or SHA-256 functions for files is hardly anything new and one of the most efficient means to ascertain the integrity of a file, or to check if two files are identical. But a researcher has generated an image that visibly contains its own MD5 hash. [...]
...moreSignal calls on users to run proxies for bypassing Iran blocks
Signal is urging its global community to help people in Iran stay connected with each other and the rest of the world by volunteering proxies to bypass the aggressive restrictions imposed by the Iranian regime. [...]
...moreMFA Fatigue: Hackers’ new favorite tactic in high-profile breaches
Hackers are more frequently using social engineering attacks to gain access to corporate credentials and breach large networks. One component of these attacks that is becoming more popular with the rise of multi-factor authentication is a technique called MFA Fatigue. [...]
...moreVMware: 70% drop in Linux ESXi VM performance with Retbleed fixes
VMware is warning that ESXi VMs running on Linux kernel 5.19 can have up to a 70% performance drop when Retbleed mitigations are enabled compared to the Linux kernel 5.18 release. [...]
...moreFirmware bugs in many HPE computer models left unfixed for over a year
A set of six high-severity firmware vulnerabilities impacting a broad range of HP Enterprise devices are still waiting to be patched, although some of them were publicly disclosed since July 2021. [...]
...moreAn encrypted ZIP file can have two correct passwords — here's why
Password-protected ZIP archives are common means of compressing and sharing sets of files—from sensitive documents to malware samples to even malware (phishing "invoices" in emails). But, did you know it is possible for an encrypted ZIP file to have two correct passwords, with both producing the same outcome on extraction? [...]
...moreNSA and CISA share tips to secure the software supply chain
The U.S. National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) have released guidance today with tips on how to secure the software supply chain. [...]
...moreGitLab ‘strongly recommends’ patching critical RCE vulnerability
GitLab is urging users to install a security update for branches 15.1, 15.2, and 15.3 of its community and enterprise editions to fix a critical vulnerability that could enable an attacker to perform remote command execution via Github import. [...]
...moreWindows malware delays coinminer install by a month to evade detection
A new malware campaign disguised as Google Translate or MP3 downloader programs was found distributing cryptocurrency mining malware across 11 countries. [...]
...moreOver 80,000 exploitable Hikvision cameras exposed online

Published: 2022-08-23 11:31:48
Popularity: None
Author: None
🤖: ""Hacked cam""
Security researchers have discovered over 80,000 Hikvision cameras vulnerable to a critical command injection flaw that's easily exploitable via specially crafted messages sent to the vulnerable web server.
...more35,000 code repos not hacked—but clones flood GitHub to serve malware
Thousands of GitHub repositories were cloned and altered to include malware, a software engineer discovered. [...]
...moreThousands of Solana wallets drained in attack using unknown exploit
An overnight attack on the Solana blockchain platform drained thousands of software wallets of cryptocurrency worth millions of U.S. dollars. [...]
...moreMalicious npm packages steal Discord users’ payment card info
Multiple npm packages are being used in an ongoing malicious campaign to infect Discord users with malware that steals their payment card information. [...]
...moreCosmicStrand UEFI malware found in Gigabyte, ASUS motherboards
Chinese-speaking hackers have been using since at least 2016 malware that lies virtually undetected in the firmware images for some motherboards, one of the most persistent threats commonly known as a UEFI rootkit. [...]
...moreEx-Coinbase manager charged in first crypto insider-trading case
The U.S. Department of Justice has charged a former Coinbase manager and two co-conspirators with wire fraud conspiracy and scheme to commit insider trading in cryptocurrency assets. [...]
...moreMicrosoft starts blocking Office macros by default, once again
Microsoft announced today that it resumed the rollout of VBA macro auto-blocking in downloaded Office documents after temporarily rolling it back earlier this month following user feedback. [...]
...moreMicrosoft Teams outage also takes down Microsoft 365 services
What initially started like a minor Microsoft Teams outage has also taken down multiple Microsoft 365 services with Teams integration, including Exchange Online, Windows 365, and Office Online. [...]
...moreAtlassian fixes critical Confluence hardcoded credentials flaw
Atlassian has patched a critical hardcoded credentials vulnerability in Confluence Server and Data Center that could let remote, unauthenticated attackers log into vulnerable, unpatched servers. [...]
...moreHoly Ghost ransomware operation linked to North Korean hackers
For more than a year, North Korean hackers have been running a ransomware operation called HolyGhost, attacking small businesses in various countries. [...]
...moreNew Android malware on Google Play installed 3 million times
A new Android malware family on the Google Play Store that secretly subscribes users to premium services was downloaded over 3,000,000 times. [...]
...moreMassive Rogers outage caused by a maintenance update
Over the weekend, Rogers Communications CEO Tony Staffieri revealed the telecom company believes a maintenance update was what caused last week's massive outage. [...]
...moreHackers can unlock Honda cars remotely in Rolling-PWN attacks
A team of security researchers found that several modern Honda car models have a vulnerable rolling code mechanism that allows unlocking the cars or even starting the engine remotely. [...]
...moreNew stealthy OrBit malware steals data from Linux devices
A newly discovered Linux malware is being used to stealthily steal information from backdoored Linux systems and infect all running processes on the machine. [...]
...moreOnline programming IDEs can be used to launch remote cyberattacks
Security researchers are warning that hackers can abuse online programming learning platforms to remotely launch cyberattacks, steal data, and scan for vulnerable devices, simply by using a web browser. [...]
...moreAmazon fixes high-severity vulnerability in Android Photos app
Amazon has confirmed and fixed a vulnerability in its Photos app for Android, which has been downloaded over 50 million times on the Google Play Store. [...]
...moreRussia fines Google for spreading ‘unreliable’ info defaming its army
Roskomnadzor, Russia's telecommunications watchdog, has fined Google 68 million rubles (roughly $1.2 million) for helping spread what it called "unreliable" information on the war in Ukraine and the failure to remove it from its platforms. [...]
...moreAdobe Acrobat may block antivirus tools from monitoring PDF files
Security researchers found that Adobe Acrobat is trying to block security software from having visibility into the PDF files it opens, creating a security risk for the users. [...]
...moreNetSec Goggle shows search results only from cybersecurity sites

Published: 2022-06-27 03:21:43
Popularity: None
Author: None
🤖: "" filtered views""
A new Brave Search Goggle modifies Brave Search results to only show reputable cybersecurity sites, making it easier to search for and find security information.
...moreCritical PHP flaw exposes QNAP NAS devices to RCE attacks
QNAP has warned customers today that many of its Network Attached Storage (NAS) devices are vulnerable to attacks that would exploit a three-year-old critical PHP vulnerability allowing remote code execution. [...]
...moreNew DFSCoerce NTLM Relay attack allows Windows domain takeover
A new Windows NTLM relay attack called DFSCoerce has been discovered that uses MS-DFSNM, Microsoft's Distributed File System, to completely take over a Windows domain. [...]
...moreiCloud hacker gets 9 years in prison for stealing nude photos
A California man who hacked thousands of Apple iCloud accounts was sentenced to 8 years in prison after pleading guilty to conspiracy and computer fraud in October 2021. [...]
...moreThousands of GitHub, AWS, Docker tokens exposed in Travis CI logs
For a second time in less than a year, the Travis CI platform for software development and testing has exposed user data containing authentication tokens that could give access to developers' accounts on GitHub, Amazon Web Services, and Docker Hub. [...]
...morePyPI package 'keep' mistakenly included a password stealer
PyPI packages 'keep,' 'pyanxdns,' 'api-res-py' were found to contain a password-stealer and a backdoor due to the presence of malicious 'request' dependency within some versions. [...]
...moreCritical Atlassian Confluence zero-day actively used in attacks
Hackers are actively exploiting a new Atlassian Confluence zero-day vulnerability tracked as CVE-2022-26134 to install web shells, with no fix available at this time. [...]
...moreResearchers to release exploit for new VMware auth bypass, patch now
Proof-of-concept exploit code is about to be published for a vulnerability that allows administrative access without authentication in several VMware products. [...]
...moreGoogle: Predator spyware infected Android devices using zero-days
Google's Threat Analysis Group (TAG) says that state-backed threat actors used five zero-day vulnerabilities to install Predator spyware developed by commercial surveillance developer Cytrox. [...]
...moreCritical Jupiter WordPress plugin flaws let hackers take over sites
WordPress security analysts have discovered a set of vulnerabilities impacting the Jupiter Theme and JupiterX Core plugins for WordPress, one of which is a critical privilege escalation flaw. [...]
...moreNIST updates guidance for defending against supply-chain attacks
The National Institute of Standards and Technology (NIST) has released updated guidance on securing the supply chain against cyberattacks. [...]
...moreApple emergency update fixes zero-day used to hack Macs, Watches
Apple has released security updates to address a zero-day vulnerability that threat actors can exploit in attacks targeting Macs and Apple Watch devices. [...]
...moreHeroku admits that customer credentials were stolen in cyberattack
Heroku has now revealed that the stolen GitHub integration OAuth tokens from last month further led to the compromise of an internal customer database. The Salesforce-owned cloud platform acknowledged the same compromised token was used by attackers to exfiltrate customers' hashed and salted passwords from "a database." [...]
...moreUnpatched DNS bug affects millions of routers and IoT devices
A vulnerability in the domain name system (DNS) component of a popular C standard library that is present in a wide range of IoT products may put millions of devices at DNS poisoning attack risk. [...]
...moreNew Nimbuspwn Linux vulnerability gives hackers root privileges
A new set of vulnerabilities collectively tracked as Nimbuspwn could let local attackers escalate privileges on Linux systems to deploy malware ranging from backdoors to ransomware. [...]
...moreUbuntu 22.04 LTS released with performance and security improvements
Canonical has announced the general availability of version 22.04 of the Ubuntu Linux distribution, codenamed 'Jammy Jellyfish', which brings better hardware support and an improved security baseline. [...]
...moreCritical flaw in Elementor WordPress plugin may affect 500k sites
The authors of the Elementor Website Builder plugin for WordPress have just released version 3.6.3 to address a critical remote code execution flaw that may impact as many as 500,000 websites. [...]
...moreTrend Micro fixes actively exploited remote code execution bug
Japanese cybersecurity software firm Trend Micro has patched a high severity security flaw in the Apex Central product management console that can let attackers execute arbitrary code remotely. [...]
...moreRussian-linked Android malware records audio, tracks your location
A previously unknown Android malware has been linked to the Turla hacking group after discovering the app used infrastructure previously attributed to the threat actors. [...]
...morePhishing uses Azure Static Web Pages to impersonate Microsoft

Published: 2022-03-31 22:48:44
Popularity: None
Author: None
🤖: "Phish alert"
Phishing attacks are abusing Microsoft Azure's Static Web Apps service to steal Microsoft, Office 365, Outlook, and OneDrive credentials.
...moreNew Spring Java framework zero-day allows remote code execution

Published: 2022-03-30 23:25:30
Popularity: None
Author: None
🤖: ""java exploit""
A new zero-day vulnerability in the Spring Core Java framework called 'Spring4Shell' has been publicly disclosed, allowing unauthenticated remote code execution on applications.
...moreAPC UPS zero-day bugs can remotely burn out devices, disable power
A set of three critical zero-day vulnerabilities now tracked as TLStorm could let hackers take control of uninterruptible power supply (UPS) devices from APC, a subsidiary of Schneider Electric. [...]
...moreNew Linux bug gives root on all major distros, exploit released

Published: 2022-03-08 00:14:34
Popularity: None
Author: None
🤖: ""Linux pwned""
A new Linux vulnerability known as 'Dirty Pipe' allows local users to gain root privileges through publicly available exploits.
...moreNSA-linked Bvp47 Linux backdoor widely undetected for 10 years

Published: 2022-02-24 02:23:26
Popularity: None
Author: None
🤖: ""Sneaky bug""
A report released today dives deep into technical aspects of a Linux backdoor now tracked as Bvp47 that is linked to the Equation Group, the advanced persistent threat actor tied to the U.S. National Security Agency.
...moreHacking group 'ModifiedElephant' evaded discovery for a decade
Threat analysts have linked a decade of activity to an APT (advanced persistent threat) actor called 'ModifiedElephant', who has managed to remain elusive to all threat intelligence firms since 2012. [...]
...moreGoogle sees 50% security boost for 150M users after 2FA enroll
After accelerating its efforts to auto-enroll as many accounts as possible in two-factor authentication (2FA), Google announced that an additional 150 million users now have 2FA enabled. [...]
...moreIt's not just you: Telegram is down for many users
Telegram users are currently experiencing issues around the world, with users unable to use the desktop and mobile apps. [...]
...moreZoho patches new critical authentication bypass in Desktop Central
Zoho has addressed a new critical severity vulnerability found to affect the company's Desktop Central and Desktop Central MSP unified endpoint management (UEM) solutions. [...]
...moreSwiss army bans all chat apps but locally-developed Threema
The Swiss army has banned foreign instant-messaging apps such as Signal, Telegram, and WhatsApp and requires army members to use the locally-developed Threema messaging app instead. [...]
...moreTwitter account of FBI's fake chat app, ANOM seen trolling today
The Twitter account previously associated with the ANOM chat app is posting frivolous tweets this week. ANOM was a fake encrypted messaging platform created as part of a global sting operation led by the U.S. FBI, Australian Federal Police (AFP), and other law enforcement agencies to catch criminals. [...]
...moreLog4j 2.17.1 out now, fixes new remote code execution bug
Apache has released another Log4j version, 2.17.1 fixing a newly discovered remote code execution (RCE) vulnerability in 2.17.0, tracked as CVE-2021-44832. Prior to today, 2.17.0 was the most recent version of Log4j and deemed the safest release to upgrade to, but that advice has now evolved. [...]
...moreMalicious PyPI packages with over 10,000 downloads taken down
The Python Package Index (PyPI) registry has removed three malicious Python packages aimed at exfiltrating environment variables and dropping trojans on the infected machines. These malicious packages are estimated to have generated over 10,000 downloads and mirrors put together, according to the researchers' report. [...]
...moreHackers use in-house Zoho ServiceDesk exploit to drop webshells
An advanced persistent threat (APT) group that had been exploiting a flaw in the Zoho ManageEngine ADSelfService Plus software has pivoted to leveraging a different vulnerability in another Zoho product. [...]
...moreTesla owners unable to unlock cars due to server errors
Some Tesla owners worldwide are unable to unlock their cars or communicate with it using the app due to problems with the company's servers. [...]
...moreFake end-to-end encrypted chat app distributes Android spyware
The GravityRAT remote access trojan is being distributed in the wild again, this time under the guise of an end-to-end encrypted chat application called SoSafe Chat. [...]
...moreZero-day bug in all Windows versions gets free unofficial patch

Published: 2021-11-13 03:44:36
Popularity: None
Author: None
🤖: "Crash imminent"
A free and unofficial patch is now available for a zero-day local privilege escalation vulnerability in the Windows User Profile Service that lets attackers gain SYSTEM privileges under certain conditions.
...moreMozilla Thunderbird 91.3 released to fix high impact flaws
Mozilla released Thunderbird 91.3 to fix several high-impact vulnerabilities that can cause a denial of service, spoof the origin, bypass security policies, and allow arbitrary code execution. [...]
...moreOver 30,000 GitLab servers still unpatched against critical bug
A critical unauthenticated, remote code execution GitLab flaw fixed on April 14, 2021, remains exploitable, with over 50% of deployments remaining unpatched. [...]
...moreWordPress plugin bug impacts 1M sites, allows malicious redirects
The OptinMonster plugin is affected by a high-severity flaw that allows unauthorized API access and sensitive information disclosure on roughly a million WordPress sites. [...]
...moreMedtronic urgently recalls insulin pump controllers over hacking concerns
Medtronic is urgently recalling remote controllers for insulin pumps belonging to its 'MiniMed Paradigm' family of products, due to potential cybersecurity risks. [...]
...moreAtlassian Trello is down — second outage this week
Trello is down for many users around the world, second time this week. Trello is a web-based TODO list-style platform owned by Atlassian, makers of Jira and Confluence. [...]
...moreNew Android malware steals millions after infecting 10M phones
A large-scale malware campaign has infected more than 10 million Android devices from over 70 countries and likely stole hundreds of millions from its victims by tricking them into subscribing to paid services without their knowledge. [...]
...moreGoogle patches 10th Chrome zero-day exploited in the wild this year
Google has released Chrome 93.0.4577.82 for Windows, Mac, and Linux to fix eleven security vulnerabilities, two of them being zero-days exploited in the wild. [...]
...moreJenkins project's Confluence server hacked to mine Monero
Hackers exploiting the recently disclosed Atlassian Confluence remote code execution vulnerability breached an internal server from the Jenkins project. [...]
...moreMalicious WhatsApp mod infects Android devices with malware

Published: 2021-08-25 14:56:44
Popularity: None
Author: None
🤖: ""Warning: Hack Alert!""
A malicious version of the FMWhatsappWhatsApp mod delivers a Triadatrojan payload, a nasty surprise that infects their devices with additional malware, including the very hard-to-remove xHelper trojan.
...moreActively exploited bug bypasses authentication on millions of routers
Threat actors actively exploit a critical authentication bypass vulnerability impacting home routers with Arcadyan firmware to take them over and deploy Mirai botnet malicious payloads. [...]
...moreCritical Microsoft Hyper-V bug could haunt orgs for a long time
Technical details are now available for a vulnerability that affects Hyper-V, Microsoft's native hypervisor for creating virtual machines on Windows systems and in Azure cloud computing environment. [...]
...moreNew PetitPotam attack allows take over of Windows domains
A new NTLM relay attack called PetitPotam has been discovered that allows threat actors to take over a domain controller, and thus an entire Windows domain. [...]
...moreAkamai DNS global outage takes down major websites, online services
Akamai is investigating an ongoing outage affecting many major websites and online services including Steam, the PlayStation Network, Newegg, AWS, Amazon, Google, and Salesforce. [...]
...moreSoftware maker removes "backdoor" giving root access to radio devices
The author of a popular software-defined radio (SDR) project has removed a "backdoor" from radio devices that granted root-level access. The backdoor had been, according to the author, present in all versions of KiwiSDR devices for the purposes of remote administration and debugging. [...]
...moreMozilla Firefox to roll out DNS over HTTPS for Canadian users
Mozilla has decided to roll out the DNS over HTTPS (DoH) feature by default for Canadian Firefox users later this month. The move comes after DoH has already been offered to US-based Firefox users since 2020. [...]
...moreTwitter now lets you use security keys as the only 2FA method
Twitter now lets users use security keys as the only two-factor authentication (2FA) method while having all other methods disabled, as the social network announced three months ago, in March. [...]
...moreNSA: Russian GRU hackers use Kubernetes to run brute force attacks

Published: 2021-07-01 15:00:00
Popularity: 113
Author: Lawrence Abrams
Keywords:
The National Security Agency (NSA) warns that Russian nation-state hackers are conducting brute force attacks to access US networks and steal email and files. [...]
...moreMicrosoft admits to signing rootkit malware in supply-chain fiasco

Published: 2021-06-26 17:24:25
Popularity: None
Author: None
🤖: ""Rootkit alert""
Microsoft has now confirmed signing a malicious driver being distributed within gaming environments. This driver, called "Netfilter," is in fact a rootkit that was observed communicating with Chinese command-and-control IPs.
...moreOnlyFans, Twitter ban users for leaking politician's BDSM video
This week, Twitter and OnlyFans have banned user accounts that illicitly leaked a BSDM video featuring a New York City city council candidate. As reported by Motherboard, the video of 26-year old Zack Weiner began circulating on Twitter and OnlyFans via accounts with identical usernames and profile pictures. [...]
...moreTor Browser fixes vulnerability that tracks you using installed apps
The Tor Project has released Tor Browser 10.0.18 to fix numerous bugs, including a vulnerability that allows sites to track users by fingerprinting the applications installed on their devices. [...]
...moreAdobe issues security updates for 41 vulnerabilities in 10 products
Adobe has released a giant Patch Tuesday security update release that fixes vulnerabilities in ten applications, including Adobe Acrobat, Reader, and Photoshop. [...]
...moreCodecov hackers gained access to Monday.com source code
Monday.com has recently disclosed the impact of the Codecov supply-chain attack that affected multiple companies. As reported by BleepingComputer last month, popular code coverage tool Codecov had been a victim of a supply-chain attack that lasted for two months. [...]
...morePython also impacted by critical IP address validation vulnerability
Python 3.3 standard library 'ipaddress' suffers from a critical IP address vulnerability (CVE-2021-29921) identical to the flaw that was reported in the "netmask" library earlier this year. [...]
...moreHashiCorp is the latest victim of Codecov supply-chain attack
Open-source software tools and Vault maker HashiCorp has disclosed a security incident that occurred due to the recent Codecov attack. HashiCorp, a Codecov customer, has stated that the recent Codecov supply-chain attack aimed at collecting developer credentials led to the exposure of HashiCorp's GPG signing key. [...]
...moreSignal CEO gives mobile-hacking firm a taste of being hacked
Software developed by data extraction company Cellebrite contains vulnerabilities that allow arbitrary code execution on the device, claims Moxie Marlinspike, the creator of the encrypted messaging app Signal. [...]
...moreGitHub Actions being actively abused to mine cryptocurrency on GitHub servers
GitHub Actions has been abused by attackers to mine cryptocurrency using GitHub's servers, automatically.The particular attack adds malicious GitHub Actions code to repositories forked from legitimate ones, and further creates a Pull Request for the original repository maintainers to merge the code back, to alter the original code. [...]
...moreGoogle shares Spectre PoC targeting browser JavaScript engines
Google has published JavaScript proof-of-concept (PoC) code to demonstrate the practicality of using Spectre exploits targeting web browsers to gain access to information from a browser's memory. [...]
...moreQNAP patches critical vulnerability in Surveillance Station NAS app
QNAP has addressed a critical security vulnerability in the Surveillance Station app that allows attackers to execute malicious code remotely on network-attached storage (NAS) devices running the vulnerable software. [...]
...moreBuggy WordPress plugin exposes 100K sites to takeover attacks
Critical and high severity vulnerabilities in the Responsive Menu WordPress plugin exposed over 100,000 sites to takeover attacks as discovered by Wordfence. [...]
...moreTelegram privacy feature failed to delete self-destructing video files
Telegram has fixed a security issue where self-destructing audio and video recording were not being deleted from user's macOS devices as expected. [...]
...moreApple fixes SUDO root privilege escalation flaw in macOS
Apple has fixed a sudo vulnerability in macOS Big Sur, Catalina, and Mojave, allowing any local user to gain root-level privileges. [...]
...moreThe Great Suspender Chrome extension's fall from grace
Google has forcibly uninstalled the immensely popular 'The Great Suspender' extension from Google Chrome and classified it as malware. [...]
...moreFemale escort review site data breach affects 470,000 members

Published: 2021-02-03 20:42:16
Popularity: None
Author: None
🤖: "Data leak"
An online community promoting female escorts and reviews of their services has suffered a data breach after a hacker downloaded the site's database.
...moreMicrosoft: DPRK hackers 'likely' hit researchers with Chrome exploit
Today, Microsoft disclosed that they have also been monitoring the targeted attacks against vulnerability researchers for months and have attributed the attacks to a DPRK group named 'Zinc.' [...]
...moreSkype is down worldwide - Microsoft working on issues
Skype users are currently experiencing issues around the world, with users reporting that they are getting signed out of their Skype account and company accounts automatically. [...]
...moreIt's finally over! Time to uninstall Adobe Flash Player
It's over, kaput, done. Adobe Flash Player is officially non-functional, and it's time to uninstall the program once and for all. [...]
...moreNSA advises companies to avoid third party DNS resolvers
The US National Security Agency (NSA) says that companies should avoid using third party DNS resolvers to block threat actors' DNS traffic eavesdropping and manipulation attempts and to block access to internal network information. [...]
...moreAdobe is telling Windows 10 users to uninstall Flash Player

Published: 2020-12-30 22:35:33
Popularity: 694
Author: Lawrence Abrams
Keywords:
With the Flash Player officially reaching the end of life tomorrow, Adobe has started to display alerts on Windows computers recommending that users uninstall Flash Player. [...]
...moreAdobe Flash Player is officially dead tomorrow
Flash Player will reach its end of life (EOL) on January 1, 2021, after always being a security risk to those who have used it over the years. [...]
...moreHPE discloses critical zero-day in server management software
Hewlett Packard Enterprise (HPE) has disclosed a zero-day bug in the latest versions of its proprietary HPE Systems Insight Manager (SIM) software for Windows and Linux. [...]
...moreGmail hit by a second outage within a single day
Gmail is suffering its second outage in 24 hours, with users able to access their email but unable to send to other Gmail users or are experiencing unexpected behavior. [...]
...moreGoogle outage affecting YouTube, Gmail and more
Google users are currently experiencing issues around the world, with users unable to access Gmail, YouTube, Google Drive, and possibly other Google services. [...]
...moreNew Slipstream NAT bypass attacks to be blocked by browsers
Web browser vendors are planning to block a new attack technique that would allow attackers to bypass a victim's NAT/firewall to gain access to any TCP/UDP service hosted on their devices. [...]
...moreAdobe fixes critical security vulnerabilities in Acrobat, Reader

Published: 2020-11-04 13:32:34
Popularity: None
Author: None
🤖: "Acrobat fixed..."
Adobe has released security updates to address critical severity vulnerabilities affecting Adobe Acrobat and Reader for Windows and macOS that could enable attackers to execute arbitrary code on vulnerable devices.
...moreYouTube-dl GitHub repos taken down by RIAA via DMCA takedown
The Recording Industry Association of America, Inc. (RIAA) has taken down the popular Youtube-dl GitHub repositories using a DMCA takedown notice. [...]
...moreHP Device Manager backdoor lets attackers take over Windows systems
HP released a security advisory detailing three critical and high severity vulnerabilities in the HP Device Manager that could lead to system takeover. [...]
...moreGrindr fixed a bug allowing full takeover of any user account
Grindr has fixed a security flaw that could have allowed attackers to easily hijack any Grindr account if they knew the user's email address. [...]
...moreTutanota encrypted email service suffers DDoS cyberattacks
Encrypted email service, Tutanota has experienced a series of DDoS attacks this week, first targeting the Tutanota website and further its DNS providers. [...]
...moreWindows Zerologon PoC exploits allow domain takeover. Patch Now!
Researchers have released exploits for the Windows Zerologon CVE-2020-1472 vulnerability that allow an attacker to take control of a Windows domain. Install patches now! [...]
...moreCenturyLink routing issue led to outages on Hulu, Steam, Discord, more
A CenturyLink BGP routing mistake has led to a ripple effect across the Internet that led to outages for numerous Internet-connected services such as Cloudflare, Amazon, Garmin, Steam, Discord, Blizzard, and many more. [...]
...moreBusiness technology giant Konica Minolta hit by new ransomware
Business technology giant Konica Minolta was hit with a ransomware attack at the end of July that impacted services for almost a week, BleepingComputer has learned. [...]
...moreKrØØk attack variants impact Qualcomm, MediaTek Wi-Fi chips
Qualcomm and MediaTek Wi-Fi chips were found to have been impacted by new variants of the KrØØk information disclosure vulnerability discovered by ESET researchers Robert Lipovský and Štefan Svorenčík. [...]
...moreCritical Wordpress plugin bug lets hackers take over hosting account
Hackers can exploit a maximum severity vulnerability in the wpDiscuz plugin installed on over 70,000 WordPress sites to execute code remotely after uploading arbitrary files on servers hosting vulnerable sites. (eaf4eb782b57d2f002da312b3ed275fe)[...]
...moreSource code from dozens of companies leaked online
Source code from exposed repositories of dozens of companies across various fields of activity (tech, finance, retail, food, eCommerce, manufacturing) is publicly available as a result of misconfigurations in their infrastructure. [...]
...moreD-Link blunder: Firmware encryption key exposed in unencrypted image

Published: 2020-07-22 16:01:01
Popularity: 41
Author: Ax Sharma
Keywords:
The router manufacturer leaks encryption keys in some firmware versions letting reverse engineers decrypt the latest firmware images. [...]
...moreNew ‘Meow’ attack has deleted almost 4,000 unsecured databases

Published: 2020-07-26 15:17:05
Popularity: None
Author: None
🤖: "purrfectly hacked"
Dozens of unsecured databases exposed on the public web are the target of an automated 'meow' attack that wipes data without any explanation.
...moreMitigating critical F5 BIG-IP RCE flaw not enough, bypass found
F5 BIG-IP customers who only applied recommended mitigations and haven't yet patched their devices against the unauthenticated remote code execution (RCE) CVE-2020-5902 vulnerability are now advised to update them against a recently found bypass. [...]
...moreHundreds arrested after encrypted messaging network takeover
European law enforcement agencies arrested hundreds of suspects in several countries including France, Netherlands, the UK, Norway, and Sweden after infiltrating the EncroChat encrypted mobile communication network used by organized crime groups. [...]
...moreBug in ‘USB for Remote Desktop’ lets hackers add fake devices
An unpatched vulnerability in software that redirects local USB devices to a remote system could help attackers elevate privileges on a target machine by adding fake devices. [...]
...moreuBlock Origin ad blocker now blocks port scans on most sites
A recent update to an ad block filter list now allows the uBlock Origin extension to block most of the known sites that perform port scans of your local Windows computer. [...]
...moreWindows 10 SMBGhost bug gets public proof-of-concept RCE exploit
Working exploit code that achieves remote code execution on Windows 10 machines is now publicly available for CVE-2020-0796, a critical vulnerability in Microsoft Server Message Block (SMB 3.1.1). [...]
...moreGoDaddy notifies users of breached hosting accounts
GoDaddy notified some of its customers that it had to reset their passwords after an unauthorized party used their web hosting account credentials to connect to their hosting account via SSH. [...]
...moreGoogle reenables FTP support in Chrome due to pandemic
After disabling FTP support in Google Chrome 81, Google has decided to reenable it again to prevent outages and difficulties in accessing information during the Coronavirus pandemic. [...]
...moreVMWare Releases Fix for Critical Guest-to-Host Vulnerability

Published: 2020-03-15 03:28:30
Popularity: None
Author: None
🤖: "Virtually pwned"
A security update has been released that fixes a Critical vulnerability in VMware Workstation Pro that could allow an application running in a guest environment to execute a command on the host.
...moreDDR4 Memory Still At Rowhammer Risk, New Method Bypasses Fixes
Academic researchers testing modern memory modules from Samsung, Micron, and Hynix discovered that current protections against Rowhammer attacks are insufficient. [...]
...moreRussian State Hackers Use Britney Spears Instagram Posts to Control Malware

Published: 2020-03-03 19:18:17
Popularity: None
Author: None
🤖: "Spears Hacked"
A cyber-espionage group known as Turla — believed to be the cyber-arm of Russian intelligence — has been playing around with a backdoor trojan disguised as a Firefox extension that uses comments on Britney Spears Instagram photos to store the location of its command and control (C&C) server.
...moreCritical Android Bluetooth Flaw Exploitable without User Interaction
Android users are urged to apply the latest security patches released for the operating system on Monday that address a critical vulnerability in the Bluetooth subsystem. [...]
...moreCritical Remote Code Execution Bug Fixed in OpenBSD SMTP Server
A critical vulnerability in the free OpenSMTPD email server present in many Unix-based systems can be exploited to run shell commands with root privileges. [...]
...more200K WordPress Sites Exposed to Takeoker Attacks by Plugin Bug

Published: 2020-01-29 21:22:39
Popularity: None
Author: None
🤖: ""Plugin Fail""
A high severity cross-site request forgery (CSRF) bug allows attackers to take over WordPress sites running an unpatched version of the Code Snippets plugin because of missing referer checks on the import menu.
...moreKali Linux Adds Single Installer Image, Default Non-Root User
Kali Linux 2020.1 was released today by Kali Linux team at Offensive Security with a new Kali Single Installer image for all desktop environments and a previously announced move to a non-root default user. [...]
...moreMicrosoft's IE Zero-day Fix is Breaking Windows Printing
Published: 2020-01-26 17:35:12
Popularity: 769
Author: Lawrence Abrams
Keywords:
Microsoft's temporary fix for a recently disclosed Internet Explorer zero-day vulnerability is causing numerous problems in Windows, including breaking printing for some users. [...]
...moreGoogle to Kill Chrome Apps Across All Platforms
Google announced that it will slowly phase out support for Chrome apps on all operating systems until they will completely stop working in June 2022 for all users. [...]
...moreMDhex Critical Vulnerabilities Shake the Healthcare Sector
Critical vulnerabilities have been discovered in popular medical devices from GE Healthcare that could allow attackers to alter the way they function or render them unusable. [...]
...more10% of All Macs Shlayered, Malware Cocktail Served
Many people think that malware only targets Windows and that Macs are safe, but a new report shows how a single Apple malware called Shlayer has attacked over 10% of all Apple computers monitored by an antivirus company. [...]
...moreUS Govt Warns of Attacks on Unpatched Pulse VPN Servers
The US Cybersecurity and Infrastructure Security Agency (CISA) today alerted organizations to patch their Pulse Secure VPN servers as a defense against ongoing attacks trying to exploit a known remote code execution (RCE) vulnerability. [...]
...moreGoogle Achieves Its Goal of Erasing the WWW Subdomain From Chrome
With the release of Chrome 79, Google completes its goal of erasing www from browser by no longer allowing Chrome users to automatically show the www trivial subdomain in the address bar. [...]
...moreDisney+ Now Works in Linux After DRM Tweak

Published: 2019-12-05 21:16:59
Popularity: 61
Author: Lawrence Abrams
Keywords:
Linux users can now stream shows and movies from the Disney+ streaming service after Disney lowering the level of their DRM requirements. [...]
...moreWindows, Chrome Zero-Days Chained in Operation WizardOpium Attacks

Published: 2019-12-11 02:00:55
Popularity: None
Author: None
Zero-day vulnerabilities in Google Chrome and Microsoft Windows were used last month to download and install malware onto Windows computers when visiting a Korean-language news portal.
...moreHacker Selling User Info Stolen From Prostitution Forums
Popular prostitution and escort forums in the Netherlands and Italy have suffered data breaches that exposed the usernames, email addresses, and hashed passwords for their registered members. [...]
...moreZendesk Security Breach May Impact Orgs Like Uber, Slack, and FCC

Published: 2019-10-02 19:29:02
Popularity: None
Author: None
🤖: "Data breach alert"
Customer service software company Zendesk is sending users notifications regarding a security incident that might have impacted roughly 10,000 Zendesk Support and Chat accounts activated prior to November 1, 2016.
...moreBulletproof Hosting Service in Former NATO Bunker Goes Down
Authorities in Germany this week shut down the services of a bulletproof hosting provider set up in a former NATO bunker that went five floors underground. [...]
...moreNew Masad Stealer Malware Exfiltrates Crypto Wallets via Telegram
A new and actively distributed malware strain dubbed Masad Stealer steals files, browser information, and cryptocurrency wallet data from infected computers that get sent back to its masters using Telegram as a communication channel. [...]
...moreCritical Exim TLS Flaw Lets Attackers Remotely Execute Commands as Root

Published: 2019-09-06 16:18:27
Popularity: None
Author: None
🤖: "Exploit alert"
The Exim mail transfer agent (MTA) software is impacted by a critical severity vulnerability present in versions 4.80 up to and including 4.92.1.
...moreNew York Passes Law to Update Data Breach Notification Requirements
New York Governor Andrew M. Cuomo signed the Stop Hacks and Improve Electronic Data Security (SHIELD) Act into law, with the new consumer privacy policy being designed to protect New Yorkers' private data and strengthen the state's data breach policies. [...]
...moreRobinhood Brokerage Firm Alerts of Passwords Stored in Clear Text
The Robinhood stock trading site is alerting users that passwords were stored in their system in human readable format, otherwise known as clear text. While no foul play was detected, this could have allowed employees or unauthorized users to view an account's password. [...]
...moreMicrosoft-Owned GitHub Limits Devs in US-Sanctioned Countries
A developer in the Eastern European region of Crimea has found himself at the receiving end of limitations to his GitHub account due to trade control regulations imposed by the US. [...]
...moreUnofficial Telegram App with 100K Installs Pushed Malicious Sites
An app styling itself as a more feature-rich unofficial version of Telegram was installed over 100,000 from Google Play only to provide minimum messaging services and to promote malicious websites. [...]
...moreFake DeepNude Downloads Gives You Malware Instead of Nudes
Cybercriminals are using the notoriety of the DeepNude app to distribute info-stealing malware in campaigns over YouTube that promise a cracked premium version of the program for Windows, Android, and iOS. [...]
...moreCloudflare Worldwide Outage Caused by Bad Software Deployment
Cloudflare experienced a worldwide outage today for about 30 minutes, with network performance issues that brought down a multitude of websites and web services all around the world, and triggered "502 Bad Gateway" errors. [...]
...moreBillions of Records Including Passwords Leaked by Smart Home Vendor
A publicly accessible ElasticSearch cluster owned by Orvibo, a Chinese smart home solutions provider, leaked more than two billion user logs containing sensitive data of customers from countries all over the world. [...]
...moreBotnet Uses SSH and ADB to Create Android Cryptomining Army

Published: 2019-06-20 22:46:16
Popularity: 310
Author: Sergiu Gatlan
Keywords:
Researchers discovered a cryptocurrency mining botnet that uses the Android Debug Bridge (ADB) Wi-Fi interface and SSH connections to hosts stored in the known_hosts list to spread to other devices. [...]
...moreGoogle Chrome Canary Flag Makes The Browser a Colorful Mess
Google is testing a new feature in the Chrome Canary builds that allows you to change the colors used by various user interface elements of the browser. This allows users to make the browser and its New Tab Page a colorful mess that some may find amusing, while others find painful. [...]
...moreMozilla Makes Firefox its Own Brand Name, Releases New Logos
Mozilla has announced that "Firefox" is becoming its own brand name that encompasses the Firefox Browser, Firefox Send, Firefox Lockwise, and Firefox Monitor products. Along with this new umbrella name, Mozilla has released redesigned icons that represent the future of this brand. [...]
...moreMicrosoft NTLM Flaws Expose All Windows Machines to RCE Attacks

Published: 2019-06-12 01:44:26
Popularity: None
Author: None
Two critical vulnerabilities in Microsoft's NTLM authentication protocol consisting of three logical flaws make it possible for attackers to run remote code and authenticate on machines running any Windows version.
...moreVLC 3.0.7 is Biggest Security Release Due to EU Bounty Program

Published: 2019-06-10 02:48:04
Popularity: None
Author: None
VLC Media Player 3.0.7 was released on Friday and contained the most security updates ever in one release of the program. The president of the VideoLan non-profit organization states that this was due to their inclusion in the EU-FOSSA bug bounty program.
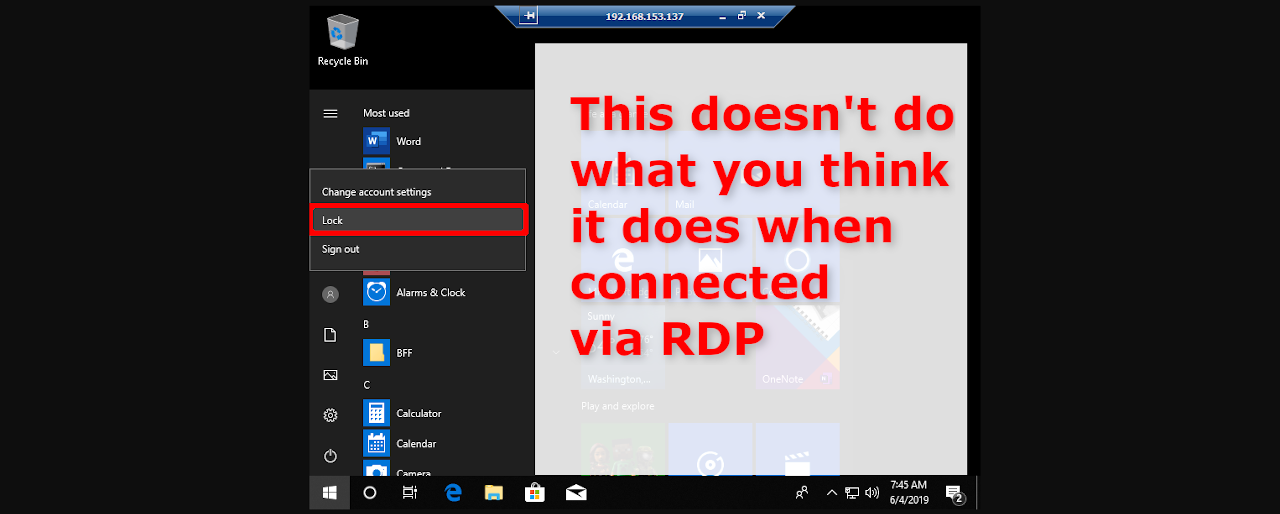
...moreRemote Desktop Zero-Day Bug Allows Attackers to Hijack Sessions
Published: 2019-06-04 23:54:20
Popularity: None
Author: None
A new zero-day vulnerability has been disclosed that could allow attackers to hijack existing Remote Desktop Services sessions in order to gain access to a computer.
...moreBlueKeep Remote Desktop Exploits Are Coming, Patch Now!

Published: 2019-05-21 11:40:42
Popularity: None
Author: None
Security researchers have created exploits for the remote code execution vulnerability in Microsoft's Remote Desktop Services, tracked as CVE-2019-0708 and dubbed BlueKeep, and hackers may not be far behind.
...moreKeyloggers Injected in Web Trust Seal Supply Chain Attack
Published: 2019-05-16 19:54:15
Popularity: None
Author: None
Hackers compromised the script used by Best of the Web to display their trust seal on their customers' websites and to add two key logging scripts designed to sniff keystrokes from visitors.
...moreFirefox Addons Being Disabled Due to an Expired Certificate
Mozilla Firefox users are discovering that all of their addons were suddenly disabled. It turns out that this is being caused by an expired intermediary certificate used to sign Mozilla addons. [...]
...moreSource Code for Carbanak Backdoor Shared with Larger Infosec Community

Published: 2019-04-23 21:58:22
Popularity: None
Author: None
🤖: "Code dump"
For the past two years, the source code for the Carbanak banking malware has been sitting on VirusTotal scanning platform, available for any researcher that recognized it.
...moreUK Announces Introduction of Online Pornography Age Checks in July
UK's government announced today that new age-verification checks will be put into place to prevent Internet users under the age of 18 to access and watch online pornography starting with July 15. [...]
...moreEvernote Fixes Remote Code Execution Vulnerability in macOS App
A local file path traversal vulnerability which allows attackers to run arbitrary code on their targets' Macs remotely was fixed by Evernote after receiving a report from security researcher Dhiraj Mishra. [...]
...moreGoogle Advises Upgrade to Windows 10 to Fix Windows 7 Zero-Day Bug
Google recommends users of Windows 7 to give it up and move to Microsoft's latest operating system if they want to keep systems safe from a zero-day vulnerability exploited in the wild. [...]
...moreRansom32 is the first Ransomware written in Javascript

Published: 2019-03-08 00:00:39
Popularity: None
Author: None
A new ransomware called Ransom32 has been discovered that is created entirely out of Javascript, HTML, and CSS. This ransomware is part of a new Ransomware as a Service that allows anyone with a bitcoin address to create their own ransomware and distribute it.
...moreFirefox 52 Borrows One More Privacy Feature from the Tor Browser

Published: 2019-03-07 23:24:39
Popularity: None
Author: None
Mozilla engineers have added a mechanism to Firefox 52 that prevents websites from fingerprinting users using system fonts.
...moreWindows DRM Files Used to Decloak Tor Browser Users

Published: 2019-03-07 23:20:50
Popularity: None
Author: None
Downloading and trying to open Windows DRM-protected files can deanonymize Tor Browser users and reveal their real IP addresses, security researchers from Hacker House have warned.
...moreJudge: It's OK If Best Buy's Geek Squad Nerds Search Your PC for Illegal Content

Published: 2019-03-07 23:02:44
Popularity: None
Author: None
A judge presiding over a child pornography case that was set in motion in 2012 has ruled that users have no legal expectation of privacy when they hand over their computers to Best Buy's Geek Squad IT technicians.
...moreChrome Bug Allows Sites to Record Audio and Video Without a Visual Indicator
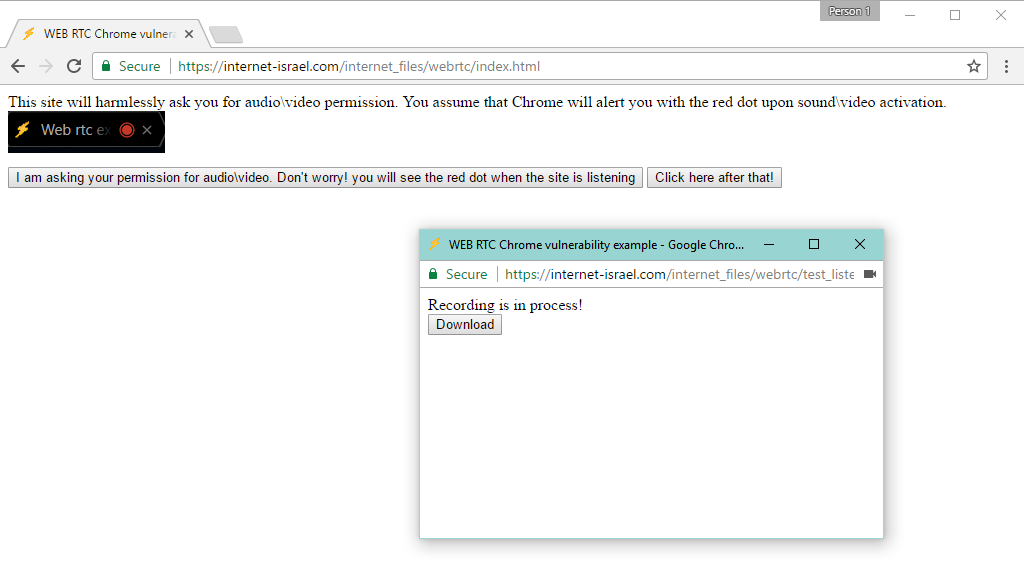
Published: 2019-03-07 23:01:11
Popularity: None
Author: None
Ran Bar-Zik, a web developer at AOL, has discovered and reported a bug in Google Chrome that allows websites to record audio and video without showing a visual indicator.
...moreThree Vendors Decline to Patch Vulnerabilities in Nuclear Radiation Monitors

Published: 2019-03-07 22:56:58
Popularity: None
Author: None
Ruben Santamarta, a security researcher for IOActive, has found various vulnerabilities in nuclear radiation monitoring equipment from three vendors, who when contacted by the researcher, declined to fix the reported flaws, each for various reasons.
...moreSecurity Flaws In "Smart" Car Wash Can Be Exploited to Cause Physical Injuries

Published: 2019-03-07 22:56:57
Popularity: None
Author: None
Two US security researchers have found vulnerabilities in smart car wash solutions sold by PDQ, a US-based vendor of Internet-connected car wash equipment and software.
...moreSymantec Sells SSL Business to DigiCert for $950M in Cash and 30% Shares

Published: 2019-03-07 22:55:36
Popularity: None
Author: None
In the face of devastating penalties prepared by Google, Symantec announced plans to sell its SSL issuance certificate business to rival company DigiCert.
...moreFBI Used Booby-Trapped Video to Catch Suspected Sextortionist Hiding Behind Tor
Published: 2019-03-07 22:54:49
Popularity: None
Author: None
On Monday, US authorities announced the arrest of a suspect who used Tor to disguise his online identity and coerce underage female victims into sending sexually explicit images and videos in a tactic commonly referred to as "sextortion."
...moreMan Who Refused to Decrypt Hard Drives Still in Prison After Two Years

Published: 2019-03-07 22:52:42
Popularity: None
Author: None
Francis Rawls, a former Philadelphia cop, will remain in jail for refusing to decrypt a hard drive federal investigators found in his home two years ago during a child abuse investigation.
...moreDUHK Crypto Attack Recovers Encryption Keys, Exposes VPN Connections, More

Published: 2019-03-07 22:46:15
Popularity: None
Author: None
After last week we had the KRACK and ROCA cryptographic attacks, this week has gotten off to a similarly "great" start with the publication of a new crypto attack known as DUHK (Don't Use Hard-coded Keys)
...moreLogitech Will Intentionally Brick All Harmony Link Devices Next Year

Published: 2019-03-07 22:43:59
Popularity: None
Author: None
Logitech will intentionally brick all Harmony Link universal hubs next year, on March 16, 2018. The company has emailed all Harmony Link customers with the bad news.
...moreKeylogger Found in HP Notebook Keyboard Driver

Published: 2019-03-07 22:40:04
Popularity: None
Author: None
HP has released driver updates for hundreds of notebook models to remove debugging code that an attacker could have abused as a keylogger component.
...moreTor-to-Web Proxy Caught Replacing Bitcoin Addresses on Ransomware Payment Sites
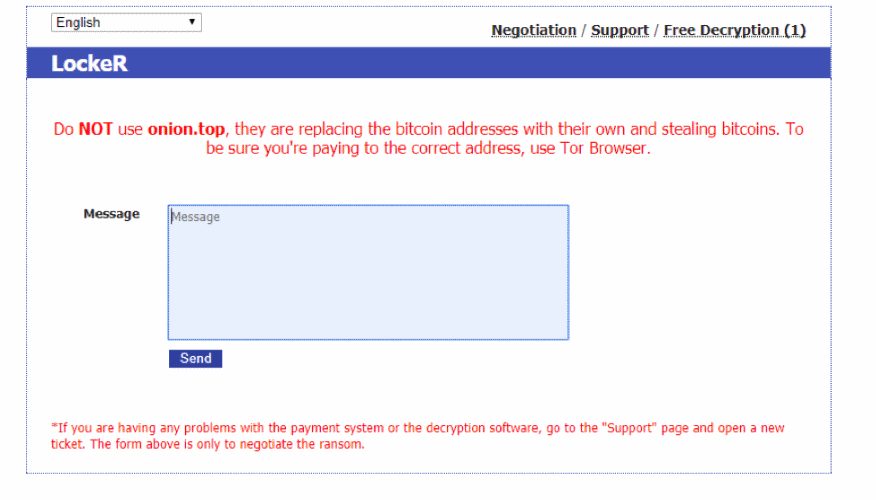
Published: 2019-03-07 22:32:37
Popularity: None
Author: None
The operators of at least one Tor proxy service was recently caught replacing Bitcoin addresses on ransomware ransom payment sites, diverting funds meant to pay for ransomware decrypters to the site's operators.
...moreRansomware Hero to Receive FBI Award

Published: 2019-03-07 22:32:24
Popularity: None
Author: None
The US Federal Bureau of Investigation (FBI) announced on Tuesday that it would be awarding the FBI Director's Community Leadership Award to Michael Gillespie for his efforts in combating ransomware and helping users who fell victims to this threat.
...moreHacker Group Makes $3 Million by Installing Monero Miners on Jenkins Servers

Published: 2019-03-07 22:31:14
Popularity: None
Author: None
A hacker group has made over $3 million by breaking into Jenkins servers and installing malware that mines the Monero cryptocurrency.
...moreUbuntu Gets in the User Data Collection Business

Published: 2019-03-07 22:31:12
Popularity: None
Author: None
Canonical announced plans to roll out a user data and diagnostics collection system with Ubuntu 18.04 LTS (Bionic Beaver). This new system will collect data on the user's OS details, hardware setup, apps and OS settings.
...moreFirefox Master Password System Has Been Poorly Secured for the Past 9 Years

Published: 2019-03-07 22:28:17
Popularity: None
Author: None
For at past nine years, Mozilla has been using an insufficiently strong encryption mechanism for the "master password" feature.
...moreRansomware Hits HPE iLO Remote Management Interfaces
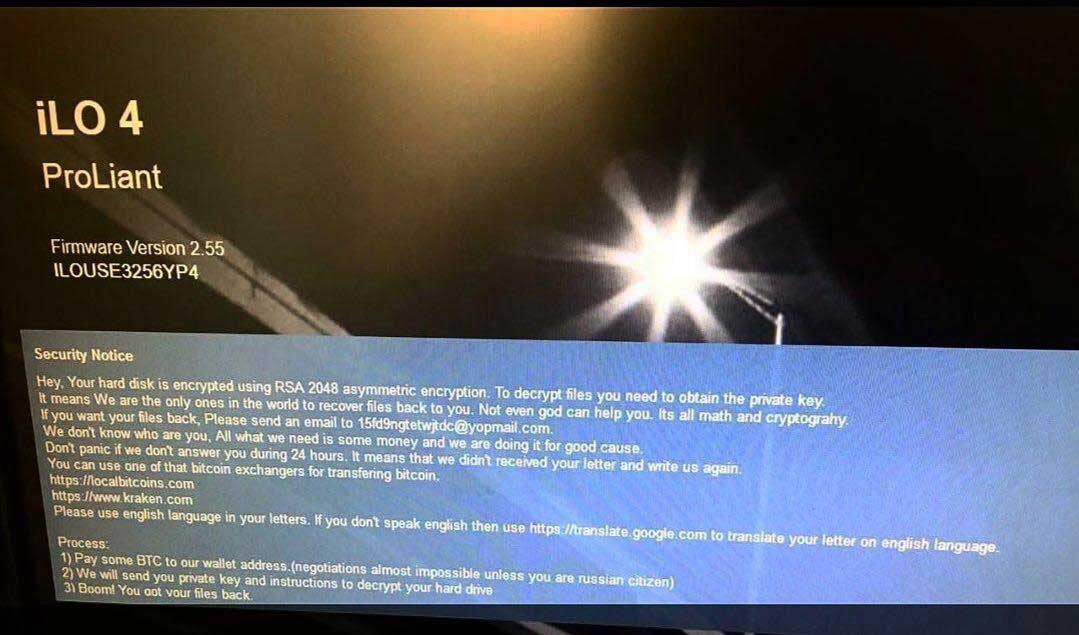
Published: 2019-03-07 22:24:01
Popularity: None
Author: None
Attackers are targeting Internet accessible HPE iLO 4 remote management interfaces, supposedly encrypting the drives, and then demanding Bitcoins to get access to the data again. While it has not been 100% confirmed if the hard drives are actually being encrypted, we do know that multiple victims have been affected by this attack.
...moreStarting Today, Google Chrome Will Show Warnings for Non-Logged SSL Certificates

Published: 2019-03-07 22:23:36
Popularity: None
Author: None
Starting today, the Google Chrome browser will show a full-page warning whenever users are accessing an HTTPS website that's using an SSL certificate that has not been logged in a public Certificate Transparency (CT) log.
...moreMicrosoft Working on a Fix for Windows 10 Meltdown Patch Bypass

Published: 2019-03-07 22:23:31
Popularity: None
Author: None
Microsoft's patches for the Meltdown vulnerability have had a fatal flaw all these past months, according to Alex Ionescu, a security researcher with cyber-security firm Crowdstrike.
...moreMicrosoft Working on a Fix for Windows 10 Meltdown Patch Bypass

Published: 2019-03-07 22:23:29
Popularity: None
Author: None
Microsoft's patches for the Meltdown vulnerability have had a fatal flaw all these past months, according to Alex Ionescu, a security researcher with cyber-security firm Crowdstrike.
...moreMultiple OS Vendors Release Security Patches After Misinterpreting Intel Docs

Published: 2019-03-07 22:22:38
Popularity: None
Author: None
Almost all major OS vendors released security patches yesterday after a researcher discovered that some OS makers have misinterpreted an Intel CPU debug feature and left their systems open to attacks.
...moreBackdoor Account Found in D-Link DIR-620 Routers
Published: 2019-03-07 22:21:13
Popularity: None
Author: None
Security researchers have found a backdoor account in the firmware of D-Link DIR-620 routers that allows hackers to take over any device reachable via the Internet.
...moreMicrosoft Adds Post-Quantum Cryptography to an OpenVPN Fork

Published: 2019-03-07 22:19:46
Popularity: None
Author: None
Microsoft has recently published an interesting open source project called "PQCrypto-VPN" that implements post-quantum cryptography (PQC) with OpenVPN. This project is being developed by the Microsoft Research Security and Cryptography group as part of their research into post-quantum cryptography.
...moreBotnet Authors Don’t Learn Anything From Victims and Secure Databases With Root/Root

Published: 2019-03-07 22:19:17
Popularity: None
Author: None
Botnet operators can be as clueless about security as their victims, according to Ankit Anubhav Principal Researcher at NewSky Security, a cyber-security company specialized in IoT security.
...moreMalware Found in Arch Linux AUR Package Repository

Published: 2019-03-07 22:16:48
Popularity: None
Author: None
Malware has been discovered in at least three Arch Linux packages available on AUR (Arch User Repository), the official Arch Linux repository of user-submitted packages. The malicious code has been removed thanks to the quick intervention of the AUR team.
...moreHacker Steals Military Docs Because Someone Didn’t Change a Default FTP Password

Published: 2019-03-07 22:16:44
Popularity: None
Author: None
A hacker is selling sensitive military documents on online hacking forums, a security firm has discovered.
...moreSenator Asks US Government to Remove Flash From Federal Sites, Computers

Published: 2019-03-07 22:15:49
Popularity: None
Author: None
In a letter sent today, Oregon Senator Ron Wyden asked officials from three government agencies to come up with solutions and procedures that mandate the removal of Adobe Flash content from all US government websites by August 1, 2019.
...moreWhatsApp Vulnerability Allows Attackers to Alter Messages in Chats
Published: 2019-03-07 22:14:48
Popularity: None
Author: None
Researchers from CheckPoint have figured out a way to manipulate conversations in order to modify existing replies that were received, quoting a message so it appears that it came from another user who may not be part of the group, and sending private messages that can be seen by only one person in a group.
...moreVulnerabilities Found in the Firmware of 25 Android Smartphone Models
Published: 2019-03-07 22:14:24
Popularity: None
Author: None
Last week, at the DEF CON security conference held in Las Vegas, security researchers presented details about 47 vulnerabilities in the firmware and default apps of 25 Android smartphone models, 11 of which are also sold in the US.
...moreVulnerabilities in Fax Protocol Let Hackers Infiltrate Networks via Fax Machines

Published: 2019-03-07 22:14:15
Popularity: None
Author: None
Two recently discovered vulnerabilities in the fax protocol can transform fax machines into entry points for hackers into corporate networks, two Check Point researchers revealed last week in a talk given at the DEF CON 26 security conference held in Las Vegas.
...moreTLS Certs Outliving Domain Ownership Open Door to MitM and DoS
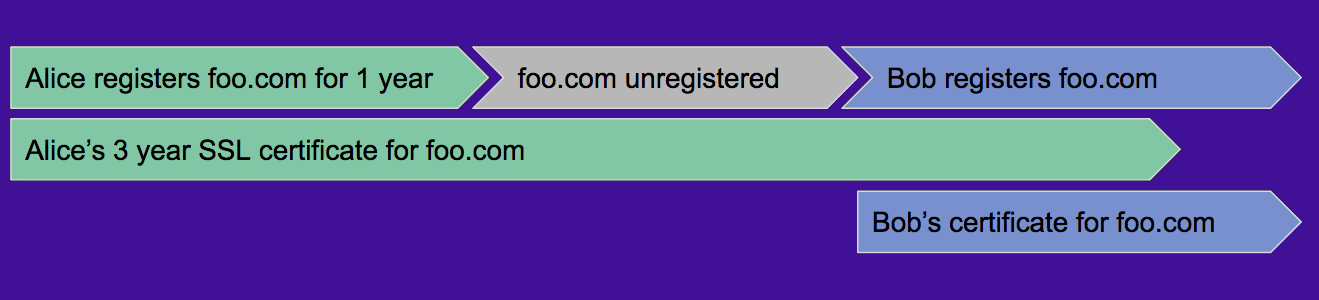
Published: 2019-03-07 22:13:09
Popularity: None
Author: None
Digital certificates that allow secure data exchange over the internet can survive domain ownership transfer and can open the door for malicious actions to the previous holder.
...moreNew Attack Recovers RSA Encryption Keys from EM Waves Within Seconds
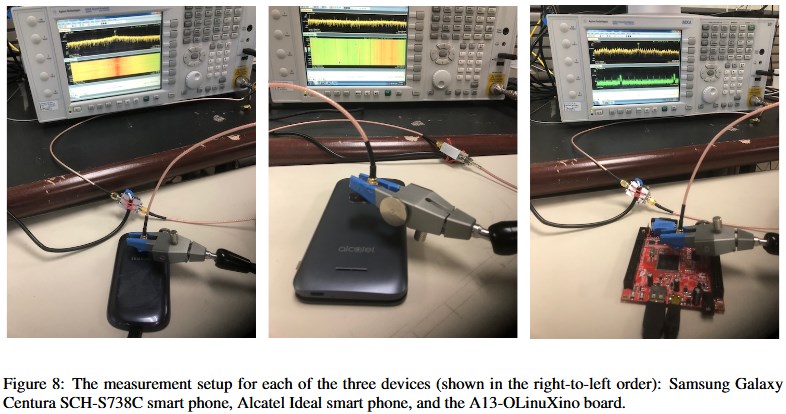
Published: 2019-03-07 22:12:57
Popularity: None
Author: None
A research paper presented at the Usenix security conference last week detailed a new technique for retrieving encryption keys from electronic devices, a method that is much faster than all previously known techniques.
...moreVORACLE Attack Can Recover HTTP Data From VPN Connections
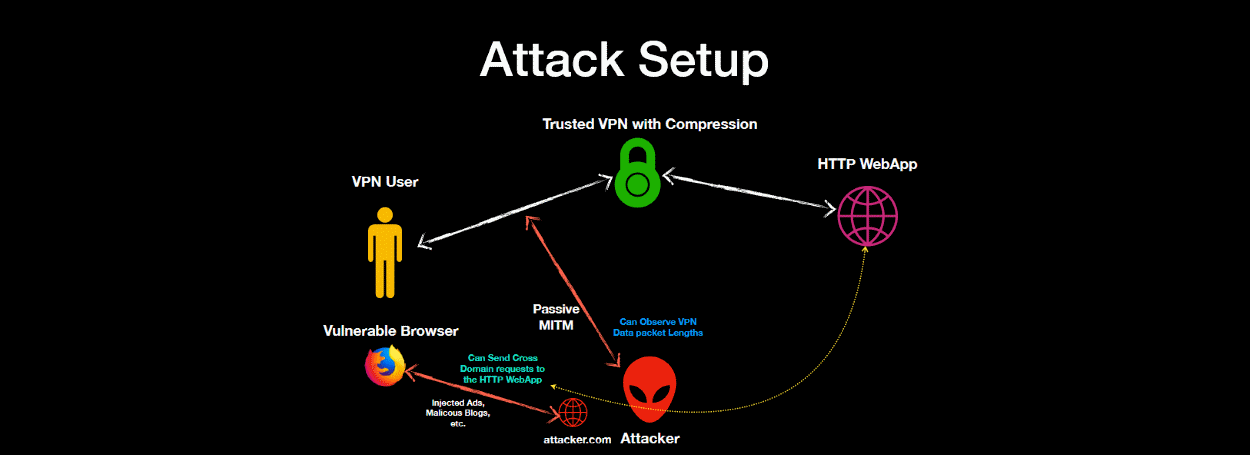
Published: 2019-03-07 22:12:29
Popularity: None
Author: None
A new attack named VORACLE can recover HTTP traffic sent via encrypted VPN connections under certain conditions.
...moreNew Chainshot Malware Found By Cracking 512-Bit RSA Key
Published: 2019-03-07 22:11:04
Popularity: None
Author: None
Security researchers exploited a threat actor's poor choice for encryption and discovered a new piece of malware along with network infrastructure that links to various targeted attacks.
...moreGit Project Patches Remote Code Execution Vulnerability in Git

Published: 2019-03-07 22:08:23
Popularity: None
Author: None
The Git Project announced yesterday a critical arbitrary code execution vulnerability in the Git command line client, Git Desktop, and Atom that could allow malicious repositories to remotely execute commands on a vulnerable machine.
...moreCloudflare Improves Privacy by Encrypting the SNI During TLS Negotiation
Published: 2019-03-07 22:06:55
Popularity: None
Author: None
Cloudflare announces today support for encrypted Server Name Indication, a mechanism that makes it more difficult to track user's browsing.
...moreApple Fixes Creepy FaceTime Vulnerability, Crash Bug in macOS, and More

Published: 2019-03-07 22:06:10
Popularity: None
Author: None
Today Apple released updates for core products that include iOS 12.1, Safari 12.0.1, iCloud for Windows, iTunes, watchOS 5.1, tvOS 12.1, and macOS.
...moreNew BLEEDINGBIT Vulnerabilities Affect Widely-Used Bluetooth Chips
Published: 2019-03-07 22:06:00
Popularity: None
Author: None
Two vulnerabilities in the Bluetooth chips typically found in access points used to provide WiFi service in enterprises allow attackers to take control of the devices without authentication or breach the network.
...moreVirtualBox Zero-Day Vulnerability Details and Exploit Are Publicly Available

Published: 2019-03-07 22:05:54
Popularity: None
Author: None
A Russian vulnerability researcher and exploit developer has published detailed information about a zero-day vulnerability in VirtualBox. His explanations include step-by-step instructions for exploiting the bug.
...moreFirst GDPR Sanction in Germany Fines Flirty Chat Platform EUR 20,000

Published: 2019-03-07 22:03:10
Popularity: None
Author: None
Following a hack that resulted in leaking online about 808,000 email addresses and over 1.8 million usernames and passwords, a social network website in Germany received a fine of EUR 20,000 from the Baden-Württemberg Data Protection Office.
...moreWindows Zero-Day Bug Allows Overwriting Files with Arbitrary Data
Published: 2019-03-07 22:01:42
Popularity: None
Author: None
A security researcher has disclosed exploit code for a fourth zero-day vulnerability in Windows operating system in just as many months. The bug enables overwriting a target file with arbitrary data.
...moreEscaping Containers to Execute Commands on Play with Docker Servers

Published: 2019-03-07 21:59:40
Popularity: None
Author: None
Improperly secured privileged containers on the Play with Docker testing platform offered security researchers a way to escape Linux containers and run arbitrary code on the host system.
...moreVulnerabilities Found in Highly Popular Firmware for WiFi Chips

Published: 2019-03-07 21:59:22
Popularity: None
Author: None
WiFi chip firmware in a variety of devices used mainly for gaming, but also for personal computing, and communication comes with multiple issues. At least some of them could be exploited to run arbitrary code remotely without requiring user interaction.
...moreEthical Hacker Exposes Magyar Telekom Vulnerabilities, Faces 8 Years in Jail

Published: 2019-03-07 21:58:18
Popularity: None
Author: None
An ethical hacker who discovered a security vulnerability in Magyar Telekom's IT systems during April 2018 is currently being investigated by the Hungarian Prosecution Service after the company filed a complaint and faces 8 years in prison, local Hungarian media reports.
...moreCyberSecurity Firm Darkmatter Request to be Trusted Root CA Raises Concerns

Published: 2019-03-07 21:57:03
Popularity: None
Author: None
A United Arab Emirates based cybersecurity company named DarkMatter wants to become a trusted root certificate authority in Firefox and security professionals around the world are concerned.
...moreMalspam Exploits WinRAR ACE Vulnerability to Install a Backdoor

Published: 2019-03-07 21:56:54
Popularity: None
Author: None
Researchers have discovered a malspam campaign that is distributing a a malicious RAR archive that may be the first one to exploit the newly discovered WinRAR ACE vulnerability to install malware on a computer.
...moreHackers use DNS tunneling for network scanning, tracking victims
Threat actors are using Domain Name System (DNS) tunneling to track when their targets open phishing emails and click on malicious links, and to scan networks for potential vulnerabilities. [...]
...moreKaspersky releases free tool that scans Linux for known threats

Published: 2024-06-01 15:17:34
Popularity: 1837
Author: Bill Toulas
Keywords:
🤖: "Linux shield on"
Kaspersky has released a new virus removal tool named KVRT for the Linux platform, allowing users to scan their systems and remove malware and other known threats for free. [...]
...moreMicrosoft Copilot fixed worldwide after 24 hour outage
🤖: ""AI back online""
After over a 24-hour outage, Microsoft's Bing, Copilot, and Copilot in Windows services are back online worldwide, with no information released as to what caused the problem. [...]
...moreICQ messenger shuts down after almost 28 years
🤖: "Goodbye then"
The ICQ messaging app is shutting down on June 26th, marking the end of a much-beloved communication application. [...]
...moreAI-Powered Malware Bypasses All Known Antivirus Solutions, Researchers Warn
🤖: ""AI UhOh""
Researchers have discovered "MalVAI," an AI-powered malware that can bypass all known antivirus solutions by constantly adapting its behavior and code to evade detection. This new threat highlights the obsolescence of traditional cybersecurity methods, prompting an urgent need for AI-driven defense mechanisms. Experts emphasize the necessity for the cybersecurity industry to innovate and develop dynamic solutions capable of evolving alongside sophisticated AI-driven attacks.
...moreCritical ServiceNow RCE flaws actively exploited to steal credentials

Published: 2024-07-27 13:05:54
Popularity: None
Author: None
🤖: "Hackers at work"
Threat actors are chaining together ServiceNow flaws using publicly available exploits to breach government agencies and private firms in data theft attacks.
...morePKfail Secure Boot bypass lets attackers install UEFI malware

Published: 2024-07-26 20:49:52
Popularity: None
Author: None
🤖: ""Malware sneaks in""
Hundreds of UEFI products from 10 vendors are susceptible to compromise due to a critical firmware supply-chain issue known as PKfail, which allows attackers to bypass Secure Boot and install malware.
...moreResearchers find SQL injection to bypass airport TSA security checks
🤖: "Security hole alert"
Security researchers have found a vulnerability in a key air transport security system that allowed unauthorized individuals to potentially bypass airport security screenings and gain access to aircraft cockpits. [...]
...moreWinamp releases source code, asks for help modernizing the player
🤖: "Code out"
The iconic Winamp media player has fulfilled a promise made in May to go open-source and has now published its complete source code on GitHub. [...]
...moreCritical flaw in NVIDIA Container Toolkit allows full host takeover

Published: 2024-09-29 14:23:34
Popularity: 159
Author: Bill Toulas
Keywords:
🤖: ""host taken over""
A critical vulnerability in NVIDIA Container Toolkit impacts all AI applications in a cloud or on-premise environment that rely on it to access GPU resources. [...]
...moreCisco takes DevHub portal offline after hacker publishes stolen data
🤖: "Security breach"
Cisco confirmed today that it took its public DevHub portal offline after a threat actor leaked "non-public" data, but it continues to state that there is no evidence that its systems were breached. [...]
...moreHackers now use ZIP file concatenation to evade detection
🤖: "zip bomb incoming"
Hackers are targeting Windows machines using the ZIP file concatenation technique to deliver malicious payloads in compressed archives without security solutions detecting them. [...]
...moreGitHub projects targeted with malicious commits to frame researcher
🤖: ""Git hacked""
GitHub projects have been targeted with malicious commits and pull requests, in an attempt to inject backdoors into these projects. Most recently, the GitHub repository of Exo Labs, an AI and machine learning startup, was targeted in the attack, which has left many wondering about the attacker's true intentions. [...]
...moreFake Bitwarden ads on Facebook push info-stealing Chrome extension
🤖: "Scam alert!"
Fake Bitwarden password manager advertisements on Facebook are pushing a malicious Google Chrome extension that collects and steals sensitive user data from the browser. [...]
...moreHackers use PoC exploits in attacks 22 minutes after release
🤖: "Exploit train"
Threat actors are quick to weaponize available proof-of-concept (PoC) exploits in actual attacks, sometimes as quickly as 22 minutes after exploits are made publicly available. [...]
...moreNew Blast-RADIUS attack bypasses widely-used RADIUS authentication

Published: 2024-07-11 01:41:48
Popularity: None
Author: None
🤖: "Hacked Radius"
Blast-RADIUS, an authentication bypass in the widely used RADIUS/UDP protocol, enables threat actors to breach networks and devices in man-in-the-middle MD5 collision attacks.
...moreChatGPT is down worldwide with something went wrong error

Published: 2025-04-02 14:48:31
Popularity: 491
Author: Mayank Parmar
Keywords:
🤖: "System Down 🤖👋"
ChatGPT, the famous artificial intelligence chatbot that allows users to converse with various personalities and topics, has connectivity issues worldwide. [...]
...moreCisco warns that Unified CM has hardcoded root SSH credentials
🤖: ""Root access alert!""
Cisco has removed a backdoor account from its Unified Communications Manager (Unified CM), which would have allowed remote attackers to log in to unpatched devices with root privileges. [...]
...more




















































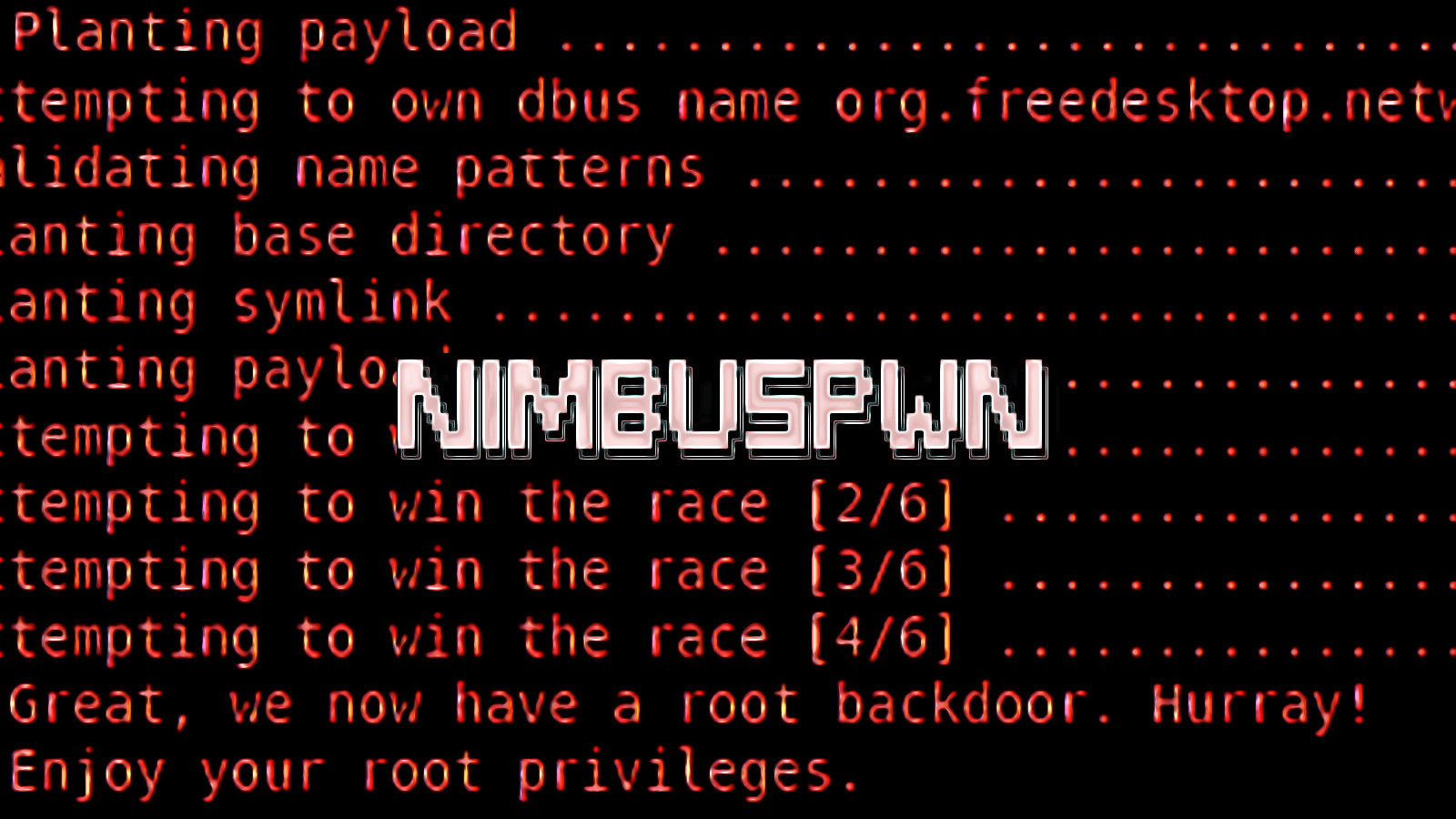


























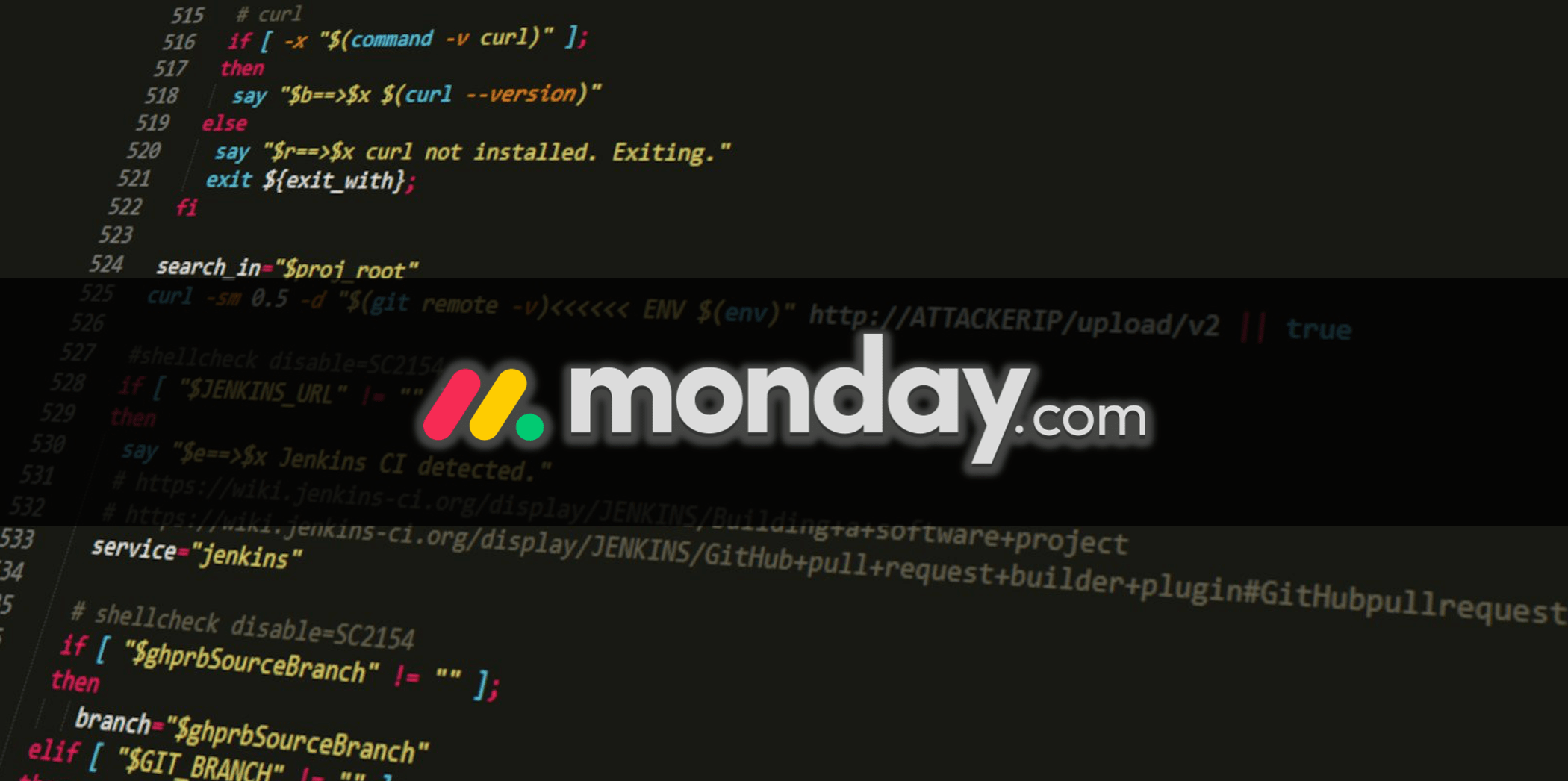

.jpg)