TeamTNT is a prevalent threat actor who has been targeting cloud and virtual environments such as Kubernetes and Docker since... The post Threat news: TeamTNT targeting misconfigured kubelet appeared first on Sysdig.
...moreSummary
Total Articles Found: 8
Top sources:
Top Keywords:
- Kubernetes: 8
- CVE: 2
- Docker: 2
- Cloud & Containerization: 2
- North American Research: 2
Top Authors
Top Articles:
- Compromising Read-Only Containers with Fileless Malware
- How attackers use exposed Prometheus server to exploit Kubernetes clusters
- A Survey of Istio's Network Security Features
- Deep Dive into Real-World Kubernetes Threats
- Autonomous Ops Ahoy! Captain Kubernetes Steers Through Blustery Clusters
- Threat news: TeamTNT targeting misconfigured kubelet
- How to mitigate kubelet’s CVE-2021-25741: Symlink exchange can allow host filesystem access
- Siloscape, first known malware that drops a backdoor into Kubernetes clusters
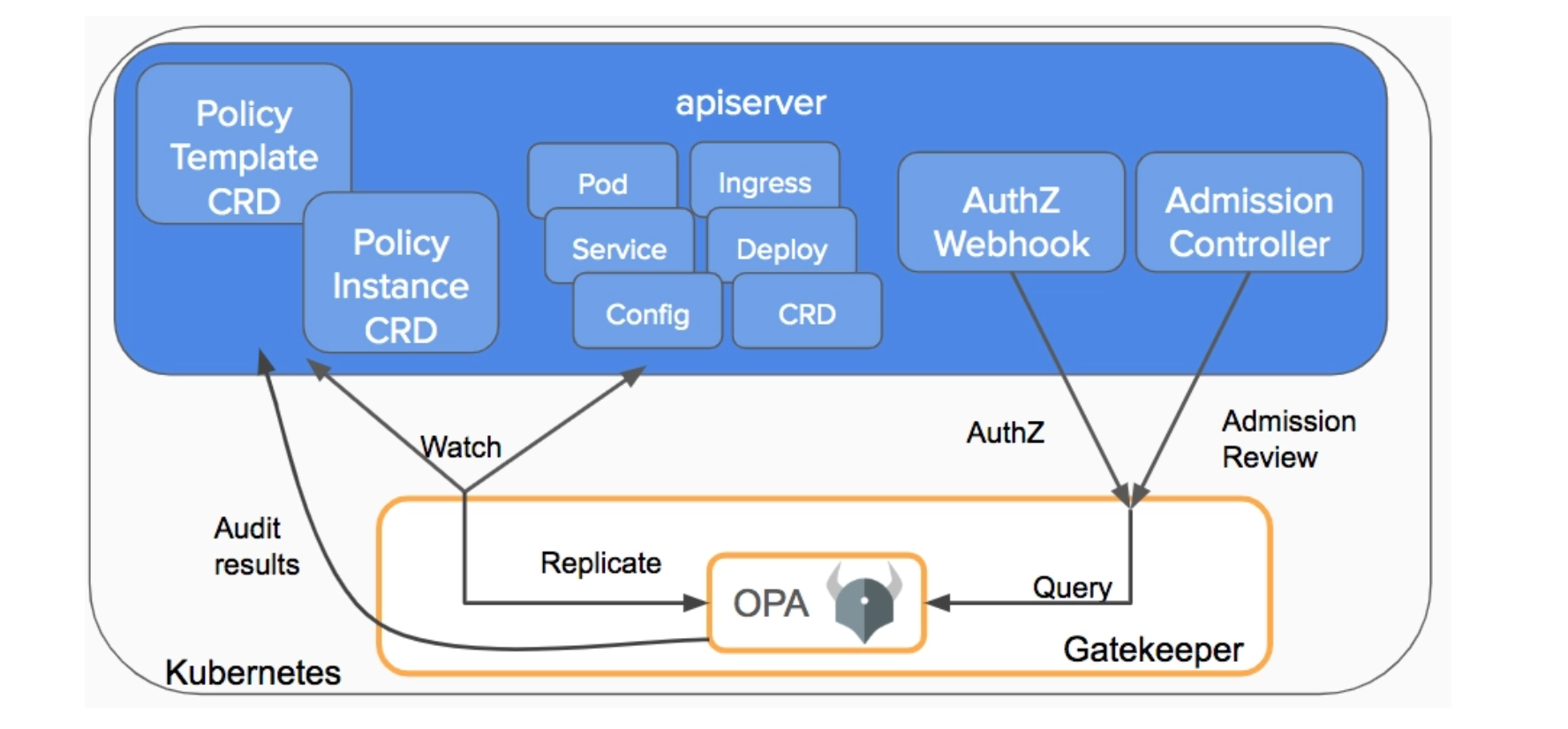
Threat news: TeamTNT targeting misconfigured kubelet
Published: 2022-09-19 17:13:09
Popularity: 1
Author: Alberto Pellitteri
Keywords:
How attackers use exposed Prometheus server to exploit Kubernetes clusters
Published: 2022-07-05 14:00:38
Popularity: 24
Author: Miguel Hernández
Keywords:
You might think that your metrics are harmless from a security point of view. Well, that’s not true, and in... The post How attackers use exposed Prometheus server to exploit Kubernetes clusters appeared first on Sysdig.
...moreCompromising Read-Only Containers with Fileless Malware
Containers provide a number of security features that are not simply available on a normal host. One of those is... The post Compromising Read-Only Containers with Fileless Malware appeared first on Sysdig.
...moreHow to mitigate kubelet’s CVE-2021-25741: Symlink exchange can allow host filesystem access
CVE-2021-25741 is a new vulnerability discovered in Kubernetes that allows users to create a container with subpath volume mounts to... The post How to mitigate kubelet’s CVE-2021-25741: Symlink exchange can allow host filesystem access appeared first on Sysdig.
...moreSiloscape, first known malware that drops a backdoor into Kubernetes clusters

Published: 2021-06-07 19:16:04
Popularity: None
Author: Pierluigi Paganini
Keywords:
Siloscape is a new strain of malware that targets Windows Server containers to execute code on the underlying node and spread in the Kubernetes cluster. Researchers from Palo Alto Networks have spotted a piece of malware that targets Windows Server containers to execute code on the underlying node and then drop a backdoor into Kubernetes […] The post Siloscape, first known malware that drops a backdoor into Kubernetes clusters appeared first on Security Affairs.
...moreA Survey of Istio's Network Security Features

Published: 2020-03-04 12:00:00
Popularity: 12
Author: jleadfordncc
Keywords:
🤖: "Secure network gates"
Istio is a service mesh, which, in general, exist as a compliment to container orchestrators (e.g. Kubernetes) in order to provide additional, service-centric features surrounding traffic management, security, and observability. Istio is arguably the most popular service mesh (using GitHub stars as a metric). This blog post assumes working familiarity with Kubernetes and microservices, but … Continue reading A Survey of Istio's Network Security Features →
...moreDeep Dive into Real-World Kubernetes Threats

Published: 2020-02-12 12:00:00
Popularity: 8
Author: nccmanning
Keywords:
On Saturday, February 1st, I gave my talk titled “Command and KubeCTL: Real-World Kubernetes Security for Pentesters” at Shmoocon 2020. I’m following up with this post that goes into more details than I could cover in 50 minutes. This will re-iterate the points I attempted to make, walk through the demo, and provide resources for … Continue reading Deep Dive into Real-World Kubernetes Threats →
...moreAutonomous Ops Ahoy! Captain Kubernetes Steers Through Blustery Clusters

Published: 2024-11-14 18:07:27
Popularity: 3
Author: Adrian Bridgwater
Keywords:
🤖: "Captain at helm"
AI-driven DevOps solutions company Kubiya has released Captain Kubernetes, an AI teammate for autonomous Kubernetes operations that simplifies Kubernetes management with natural language interaction and autonomous, self-healing capabilities. The post Autonomous Ops Ahoy! Captain Kubernetes Steers Through Blustery Clusters appeared first on Cloud Native Now.
...more