OAuth is the widely used standard for access delegation, enabling many of the “Sign in with X” buttons and “Connect your Calendar” features of modern Internet software. OAuth 2.0 is the most common and recent version of this specification, which defines four grant types (as well as various extensions), specifically suited for different use cases. … Continue reading An offensive guide to the Authorization Code grant →
...moreSummary
Total Articles Found: 3
Top sources:
Top Keywords:
- Research: 3
- Pentesting: 3
- access delegation: 1
- authorization: 1
- OAuth: 1
Top Authors
- Rami McCarthy: 1
- Rindert Kramer: 1
- nccmanning: 1
Top Articles:
- An offensive guide to the Authorization Code grant
- Deep Dive into Real-World Kubernetes Threats
- LDAPFragger: Bypassing network restrictions using LDAP attributes
An offensive guide to the Authorization Code grant

Published: 2020-07-07 11:00:01
Popularity: 17
Author: Rami McCarthy
Keywords:
LDAPFragger: Bypassing network restrictions using LDAP attributes
Published: 2020-03-19 10:00:00
Popularity: 4
Author: Rindert Kramer
Keywords:
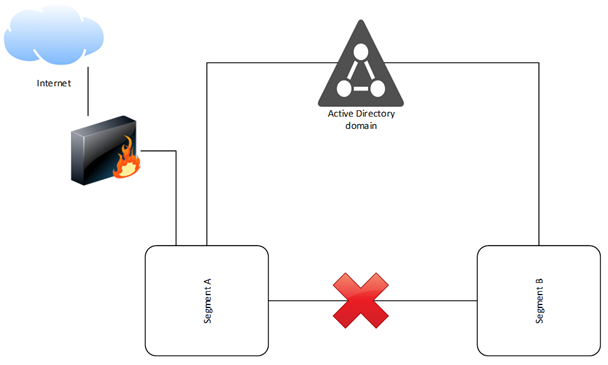
Introduction A while back during a penetration test of an internal network, we encountered physically segmented networks. These networks contained workstations joined to the same Active Directory domain, however only one network segment could connect to the internet. To control workstations in both segments remotely with Cobalt Strike, we built a tool that uses the … Continue reading LDAPFragger: Bypassing network restrictions using LDAP attributes →
...moreDeep Dive into Real-World Kubernetes Threats

Published: 2020-02-12 12:00:00
Popularity: 8
Author: nccmanning
Keywords:
On Saturday, February 1st, I gave my talk titled “Command and KubeCTL: Real-World Kubernetes Security for Pentesters” at Shmoocon 2020. I’m following up with this post that goes into more details than I could cover in 50 minutes. This will re-iterate the points I attempted to make, walk through the demo, and provide resources for … Continue reading Deep Dive into Real-World Kubernetes Threats →
...more