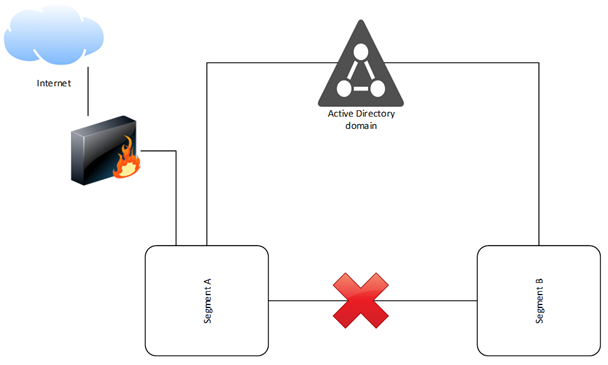
Introduction A while back during a penetration test of an internal network, we encountered physically segmented networks. These networks contained workstations joined to the same Active Directory domain, however only one network segment could connect to the internet. To control workstations in both segments remotely with Cobalt Strike, we built a tool that uses the … Continue reading LDAPFragger: Bypassing network restrictions using LDAP attributes →
...moreSummary
Total Articles Found: 1
Top sources:
Top Keywords:
- Fox-IT: 1
- Research: 1
- LDAP: 1
- Pentesting: 1
- Tool: 1
Top Authors
Top Articles:
- LDAPFragger: Bypassing network restrictions using LDAP attributes
LDAPFragger: Bypassing network restrictions using LDAP attributes
Published: 2020-03-19 10:00:00
Popularity: 4
Author: Rindert Kramer
Keywords: