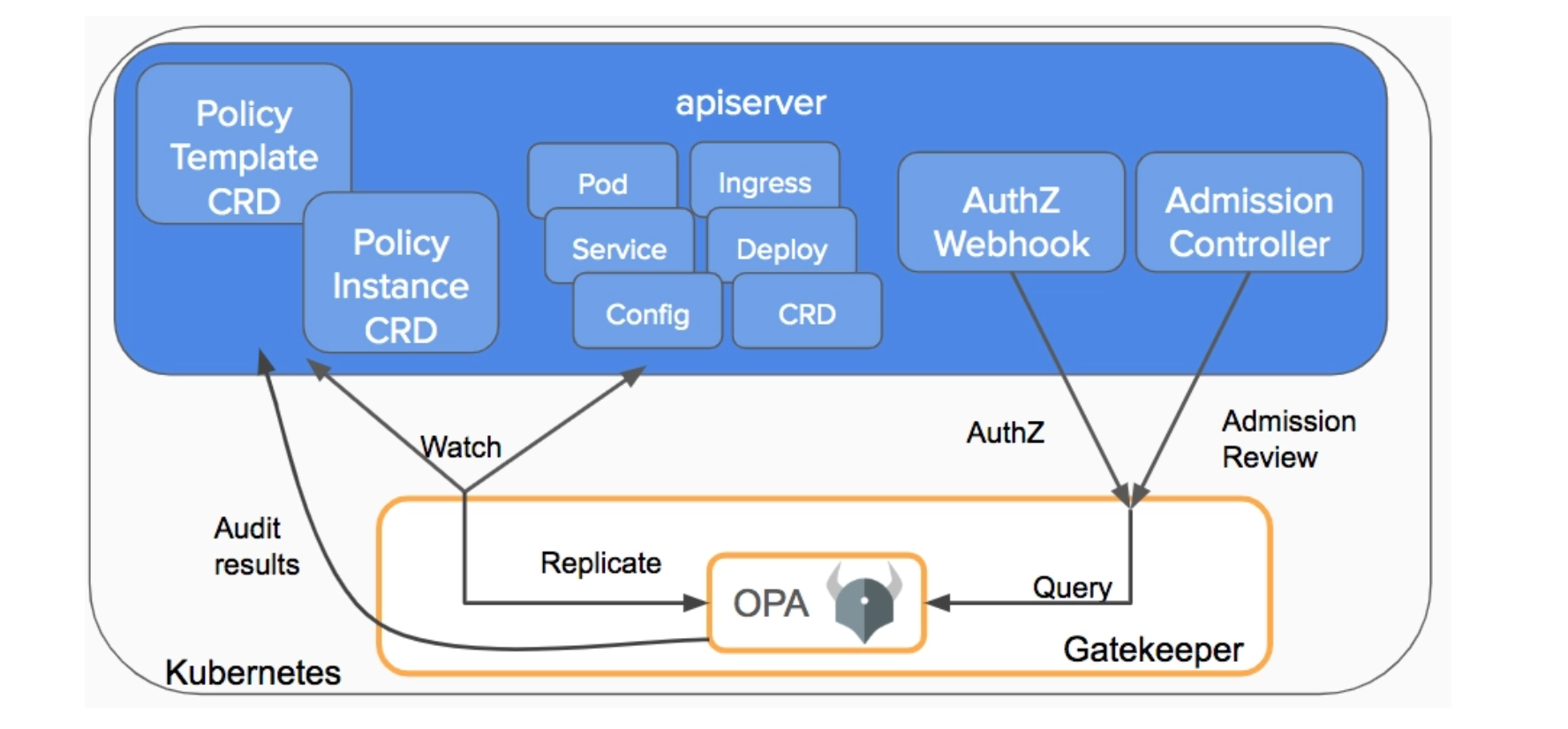
The OpenSSL Project team announced two HIGH severity vulnerabilities (CVE-2022-3602, CVE-2022-3786) on Oct. 25, which affect all OpenSSL v3 versions... The post 5 Steps to Stop the Latest OpenSSL Vulnerabilities: CVE-2022-3602, CVE-2022-3786 appeared first on Sysdig.
...moreSummary
Total Articles Found: 8
Top sources:
- Sysdig 8
Top Keywords:
- CVE: 5
- Kubernetes: 4
- Docker: 2
- Falco: 2
- Sysdig Secure: 2
Top Authors
- Alberto Pellitteri: 2
- Miguel Hernández: 2
- Stefano Chierici: 2
- Michael Clark: 1
- Nicholas Lang: 1
Top Articles:
- Compromising Read-Only Containers with Fileless Malware
- How attackers use exposed Prometheus server to exploit Kubernetes clusters
- Detecting and Mitigating CVE-2022-22963: Spring Cloud RCE Vulnerability
- 5 Steps to Stop the Latest OpenSSL Vulnerabilities: CVE-2022-3602, CVE-2022-3786
- Threat news: TeamTNT targeting misconfigured kubelet
- How to mitigate kubelet’s CVE-2021-25741: Symlink exchange can allow host filesystem access
- CVE-2022-0492: Privilege escalation vulnerability causing container escape
- EMERALDWHALE: 15k Cloud Credentials Stolen in Operation Targeting Exposed Git Config Files
5 Steps to Stop the Latest OpenSSL Vulnerabilities: CVE-2022-3602, CVE-2022-3786
Threat news: TeamTNT targeting misconfigured kubelet
Published: 2022-09-19 17:13:09
Popularity: 1
Author: Alberto Pellitteri
Keywords:
TeamTNT is a prevalent threat actor who has been targeting cloud and virtual environments such as Kubernetes and Docker since... The post Threat news: TeamTNT targeting misconfigured kubelet appeared first on Sysdig.
...moreHow attackers use exposed Prometheus server to exploit Kubernetes clusters
Published: 2022-07-05 14:00:38
Popularity: 24
Author: Miguel Hernández
Keywords:
You might think that your metrics are harmless from a security point of view. Well, that’s not true, and in... The post How attackers use exposed Prometheus server to exploit Kubernetes clusters appeared first on Sysdig.
...moreCompromising Read-Only Containers with Fileless Malware
Containers provide a number of security features that are not simply available on a normal host. One of those is... The post Compromising Read-Only Containers with Fileless Malware appeared first on Sysdig.
...moreDetecting and Mitigating CVE-2022-22963: Spring Cloud RCE Vulnerability
Published: 2022-03-31 02:02:21
Popularity: 7
Author: Stefano Chierici
Keywords:
Today, researchers found a new HIGH vulnerability on the famous Spring Cloud Function leading to remote code execution (RCE). The... The post Detecting and Mitigating CVE-2022-22963: Spring Cloud RCE Vulnerability appeared first on Sysdig.
...moreCVE-2022-0492: Privilege escalation vulnerability causing container escape
Published: 2022-03-09 06:21:16
Popularity: None
Author: Stefano Chierici
Keywords:
Linux maintainers disclosed a privilege escalation vulnerability in the Linux Kernel. The vulnerability has been issued a Common Vulnerability and... The post CVE-2022-0492: Privilege escalation vulnerability causing container escape appeared first on Sysdig.
...moreHow to mitigate kubelet’s CVE-2021-25741: Symlink exchange can allow host filesystem access
CVE-2021-25741 is a new vulnerability discovered in Kubernetes that allows users to create a container with subpath volume mounts to... The post How to mitigate kubelet’s CVE-2021-25741: Symlink exchange can allow host filesystem access appeared first on Sysdig.
...moreEMERALDWHALE: 15k Cloud Credentials Stolen in Operation Targeting Exposed Git Config Files

Published: 2024-10-31 12:31:50
Popularity: None
Author: Miguel Hernández
🤖: "Cloud hack fail"
EMERALDWHALE is an operation targeting exposed Git configurations, resulting in more than 15,000 cloud service credentials stolen.
...more