LLMs are trained to block harmful responses. Old-school images can override those rules.
...moreSummary
Total Articles Found: 46
Top sources:
Top Keywords:
- Biz & IT: 46
- vulnerabilities: 10
- exploits: 8
- Tech: 6
- Policy: 6
Top Authors
- Dan Goodin: 46
Top Articles:
- LastPass says employee’s home computer was hacked and corporate vault taken
- In epic hack, Signal developer turns the tables on forensics firm Cellebrite
- Medical device “jailbreak” could help solve the dangerous shortage of ventilators
- Stolen NSA hacking tools were used in the wild 14 months before Shadow Brokers leak
- Multiple “CIA failures” led to theft of agency’s top-secret hacking tools
- Zero-day attackers deliver a double dose of ransomware—no clicking required
- A “serious” Windows 0-day is being actively exploited in the wild
- The wave of domain hijackings besetting the Internet is worse than we thought
- Telegram feature exposes your precise address to hackers
- Marcus Hutchins, slayer of WannaCry worm, pleads guilty to malware charges
ASCII art elicits harmful responses from 5 major AI chatbots

Published: 2024-03-16 00:17:24
Popularity: 118
Author: Dan Goodin
Keywords:
Hackers can force iOS and macOS browsers to divulge passwords and much more
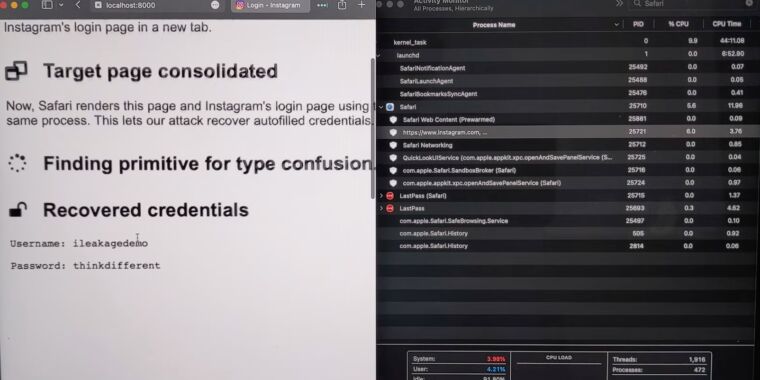
Published: 2023-10-25 17:00:39
Popularity: 157
Author: Dan Goodin
Keywords:
iLeakage is practical and requires minimal resources. A patch isn't (yet) available.
...moreGoogle tells users of some Android phones: Nuke voice calling to avoid infection

Published: 2023-03-17 20:26:26
Popularity: 336
Author: Dan Goodin
Keywords:
If your device runs Exynos chips, be very, very concerned.
...moreLastPass says employee’s home computer was hacked and corporate vault taken

Published: 2023-02-28 01:01:59
Popularity: 3866
Author: Dan Goodin
Keywords:
Already smarting from a breach that stole customer vaults, LastPass has more bad news.
...moreVMware patches vulnerability with 9.8/10 severity rating in Cloud Foundation

Published: 2022-10-28 18:41:57
Popularity: 7
Author: Dan Goodin
Keywords:
NSX-V appliance, which VMware no longer supports, also affected and patched.
...moreSerious vulnerabilities in Matrix’s end-to-end encryption have been patched

Published: 2022-09-28 16:00:27
Popularity: 17
Author: Dan Goodin
Keywords:
Previously overlooked flaws allow malicious homeservers to decrypt and spoof messages.
...more$35M fine for Morgan Stanley after unencrypted, unwiped hard drives are auctioned

Published: 2022-09-20 21:22:34
Popularity: 400
Author: Dan Goodin
Keywords:
"Astonishing failures" over a 5-year span.
...moreNew Linux malware combines unusual stealth with a full suite of capabilities
With polymorphic encoding and a multistage infection chain, Shikitega is hard to detect.
...morePhishers who hit Twilio and Cloudflare stole 10k credentials from 136 others
Already regarded among the most advanced, the attacks were also done at a massive scale.
...moreActors behind PyPI supply chain attack have been active since late 2021
Group that pulled off successful attack on PyPI has humble origins.
...moreCritical flaws in GPS tracker enable “disastrous” and “life-threatening” hacks

Published: 2022-07-19 20:13:27
Popularity: 66
Author: Dan Goodin
Keywords:
China-based Micodus has yet to patch critical vulnerabilities in MV720 GPS tracker.
...moreNew working speculative execution attack sends Intel and AMD scrambling
Published: 2022-07-12 16:00:03
Popularity: 291
Author: Dan Goodin
Keywords:
Both companies are rolling out mitigations, but they add overhead of 12 to 28 percent.
...moreCritical Zoom vulnerabilities fixed last week required no user interaction
Published: 2022-05-26 00:10:27
Popularity: 58
Author: Dan Goodin
Keywords:
If you're machine failed to get them automatically, you're not alone.
...moreMajor cryptography blunder in Java enables “psychic paper” forgeries

Published: 2022-04-20 19:28:17
Popularity: 171
Author: Dan Goodin
Keywords:
A failure to sanity check signatures for division-by-zero flaws makes forgeries easy.
...moreWatchGuard failed to explicitly disclose critical flaw exploited by Russian hackers
Silently fixed authentication bypass remained a secret even after it was under attack.
...moreVMware Horizon servers are under active exploit by Iranian state hackers

Published: 2022-02-17 23:31:35
Popularity: 54
Author: Dan Goodin
Keywords:
TunnelVision group exploit the critical flaw to infect targets with ransomware.
...moreFeds indict “The Bull” for allegedly selling insider stock info on the dark web

Published: 2021-07-09 22:30:14
Popularity: 22
Author: Dan Goodin
Keywords:
Data allegedly sold individually or through weekly or monthly subscriptions.
...moreConnecting to malicious Wi-Fi networks can mess with your iPhone
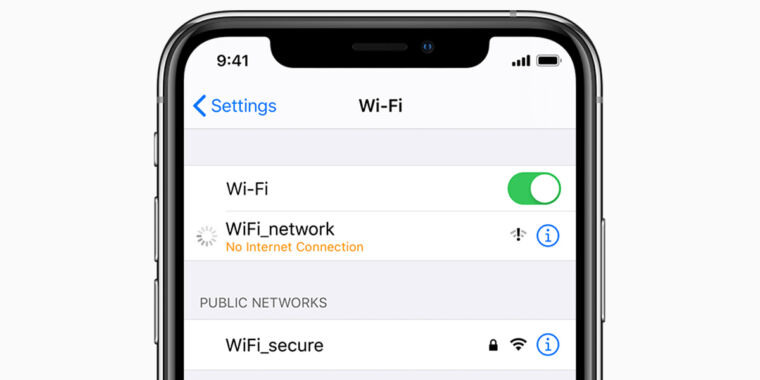
Published: 2021-06-21 21:02:23
Popularity: 37
Author: Dan Goodin
Keywords:
The world's most secure consumer OS is bitten by a garden-variety programming bug.
...moreNew Spectre attack once again sends Intel and AMD scrambling for a fix
Published: 2021-05-04 19:07:56
Popularity: 299
Author: Dan Goodin
Keywords:
A new transient execution variant is the first exploit micro-ops caches.
...moreIn epic hack, Signal developer turns the tables on forensics firm Cellebrite
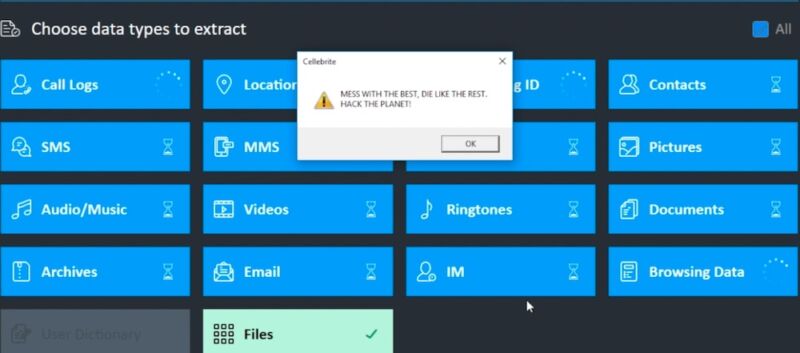
Published: 2021-04-21 19:30:08
Popularity: 3439
Author: Dan Goodin
Keywords:
Widely used forensic software can be exploited to infect investigators' computers.
...moreCritics fume after Github removes exploit code for Exchange vulnerabilities
Microsoft-owned Github pulls down proof-of-concept code posted by researcher.
...moreTelegram feature exposes your precise address to hackers

Published: 2021-01-05 21:40:31
Popularity: 633
Author: Dan Goodin
Keywords:
Messenger maker has expressed no plans to fix location disclosure flaw.
...moreA bevy of new features makes iOS 14 the most secure mobile OS ever

Published: 2020-09-18 11:48:26
Popularity: 265
Author: Dan Goodin
Keywords:
Behold: The useful and not-so-useful privacy features you've been waiting for.
...moreHackers obtained Twitter DMs for 36 high-profile account holders

Published: 2020-07-23 02:27:18
Popularity: 36
Author: Dan Goodin
Keywords:
Hack also exposed phone numbers, email addresses, and other PI for 130 users.
...moreMultiple “CIA failures” led to theft of agency’s top-secret hacking tools

Published: 2020-06-16 21:06:36
Popularity: 976
Author: Dan Goodin
Keywords:
Vault 7, the worst data theft in CIA history, could have been avoided, report finds.
...moreZoom defenders cite legit reasons to not end-to-end encrypt free calls
Critics say everyone deserves it. Others say safety should be factored in, too.
...moreMedical device “jailbreak” could help solve the dangerous shortage of ventilators

Published: 2020-04-14 17:30:20
Popularity: 2326
Author: Dan Goodin
Keywords:
Manufacturer says conversion requires “significant rework.” Airbreak suggests otherwise.
...moreIntel SGX is vulnerable to an unfixable flaw that can steal crypto keys and more
Just when you thought it was secure again, Intel's digital vault falls to a new attack.
...moreMore than 200 browser extensions ejected from Firefox and Chrome stores
Published: 2020-01-30 21:15:49
Popularity: None
Author: Dan Goodin
Keywords:
Firefox ousts almost 200 add-ons while Google detects a significant increase in abuse.
...moreFacebook deletes the accounts of NSO Group workers

Published: 2019-10-30 19:05:04
Popularity: 269
Author: Dan Goodin
Keywords:
Deletions come after allegations NSO exploit targeted 1,400 WhatsApp users.
...moreGoogle confirms that advanced backdoor came preinstalled on Android devices

Published: 2019-06-06 20:47:20
Popularity: None
Author: Dan Goodin
Keywords:
After Google successfully beat back Triada in 2017, its developers found a new way in.
...more238 Google Play apps with >440 million installs made phones nearly unusable

Published: 2019-06-04 19:20:02
Popularity: None
Author: Dan Goodin
Keywords:
Carefully concealed plugin bombarded users with ads during inopportune times.
...moreHackers actively exploit WordPress plugin flaw to send visitors to bad sites
Published: 2019-05-29 23:05:00
Popularity: None
Author: Dan Goodin
Keywords:
If you're seeing more malicious redirects than usual, now you know why.
...moreWebsite for storing digital currencies hosted code with a sneaky backdoor

Published: 2019-05-25 12:45:57
Popularity: None
Author: Dan Goodin
Keywords:
WalletGenerator.net and the mystery of the backdoored random number generator.
...moreSerial publisher of Windows 0-days drops exploits for 2 more unfixed flaws
Published: 2019-05-23 00:41:04
Popularity: None
Author: Dan Goodin
Keywords:
SandboxEscaper has published 7 such exploits to date, 3 in the past 24 hours.
...moreStolen NSA hacking tools were used in the wild 14 months before Shadow Brokers leak

Published: 2019-05-07 06:14:49
Popularity: 1033
Author: Dan Goodin
Keywords:
Already criticized for not protecting its exploit arsenal, the NSA has a new lapse.
...moreZero-day attackers deliver a double dose of ransomware—no clicking required
Published: 2019-04-30 19:50:10
Popularity: 953
Author: Dan Goodin
Keywords:
High-severity hole in Oracle WebLogic under active exploit for 9 days. Patch now.
...moreUnexpected protection added to Microsoft Edge subverts IE security

Published: 2019-04-19 12:20:14
Popularity: 360
Author: Dan Goodin
Keywords:
Permissions that Edge added to downloaded files break important security feature.
...moreMarcus Hutchins, slayer of WannaCry worm, pleads guilty to malware charges

Published: 2019-04-19 22:38:45
Popularity: 512
Author: Dan Goodin
Keywords:
Hutchins once proclaimed his innocence. Now he admits he created the Kronos bank trojan.
...moreThe wave of domain hijackings besetting the Internet is worse than we thought

Published: 2019-04-17 15:00:58
Popularity: 822
Author: Dan Goodin
Keywords:
Despite widespread attention since January, DNS campaign shows no signs of abating.
...moreGoogle Play apps with 150 million installs contain aggressive adware

Published: 2019-03-13 19:51:34
Popularity: 310
Author: Dan Goodin
Keywords:
Google removes 210 apps after outside researchers report them as abusive.
...moreA world of hurt after GoDaddy, Apple, and Google misissue >1 million certificates

Published: 2019-03-12 21:26:24
Popularity: 310
Author: Dan Goodin
Keywords:
Certificates with 63-bit serial numbers touch off mass revocation blitz.
...moreCitrix says its network was breached by international criminals

Published: 2019-03-08 23:30:05
Popularity: 497
Author: Dan Goodin
Keywords:
FBI says hackers gained unauthorized access by exploiting weak passwords.
...moreThree men cop to $21 million vishing and smishing scheme

Published: 2019-03-11 22:40:38
Popularity: 47
Author: Dan Goodin
Keywords:
Phone-based scam may be low-tech, but it netted big bucks, prosecutors say.
...moreA “serious” Windows 0-day is being actively exploited in the wild
Published: 2019-03-08 02:02:29
Popularity: 895
Author: Dan Goodin
Keywords:
Unpatched flaw used in combination with Chrome exploit doesn't work against Win 10.
...moreTwo certificate authorities booted from the good graces of Chrome

Published: 2025-06-04 11:20:37
Popularity: 8
Author: Dan Goodin
Keywords:
🤖: "Certificate Fail"
Chunghwa Telecom and Netlock customers must look elsewhere for new certificates.
...more