Recent iPhone models have additional hardware-based security protection for sensitive regions of the kernel memory. We discovered that to bypass this hardware-based security protection, the attackers used another hardware feature of Apple-designed SoCs.
...moreSummary
Total Articles Found: 15
Top sources:
Top Keywords:
- Research: 15
- Tool Release: 4
- Cloud & Containerization: 4
- Pentesting: 3
- North American Research: 3
Top Authors
- Jeff Dileo: 4
- Boris Larin: 1
- Bas Westerbaan: 1
- Hunter Stanton: 1
- Jon Szymaniak: 1
Top Articles:
- Operation Triangulation: The last (hardware) mystery
- Bluetooth Flaws Could Allow Global Tracking of Apple, Windows 10 Devices
- Tool Release – Enumerating Docker Registries with go-pillage-registries
- An offensive guide to the Authorization Code grant
- A Survey of Istio's Network Security Features
- Deep Dive into Real-World Kubernetes Threats
- ABSTRACT SHIMMER (CVE-2020-15257): Host Networking is root-Equivalent, Again
- LDAPFragger: Bypassing network restrictions using LDAP attributes
- Introducing post-quantum Cloudflare Tunnel
- Tool Release: Sinking U-Boots with Depthcharge
Operation Triangulation: The last (hardware) mystery

Published: 2023-12-27 14:00:43
Popularity: 2485
Author: Boris Larin
Keywords:
Introducing post-quantum Cloudflare Tunnel
Published: 2022-10-03 13:00:00
Popularity: 2
Author: Bas Westerbaan
Keywords:
Every connection we make post-quantum secure, we remove one opportunity for compromise: that's why we are announcing post-quantum Cloudflare Tunnel to help you secure every connection to our network
...moreCVE-2021-41577: MITM to RCE in EVGA Precision X1
The post CVE-2021-41577: MITM to RCE in EVGA Precision X1 appeared first on Rhino Security Labs.
...moreTool Release – insject: A Linux Namespace Injector

Published: 2022-01-08 05:20:06
Popularity: None
Author: Jeff Dileo
Keywords:
🤖: "Linux namespace party"
tl;dr Grab the release binary from our repo and have fun. Also, happy new year; 2021 couldn’t end soon enough. Background A while back, I was asked by one of my coworkers on the PSC team about ways in which to make their custom credit card data scanner cloud native to assess Kubernetes clusters. While … Continue reading Tool Release – insject: A Linux Namespace Injector →
...moreTool Release – shouganaiyo-loader: A Tool to Force JVM Attaches
🤖: "Java crashes again"
Background Java Virtual Machines (JVMs) provide a number of mechanisms to inspect and modify the Java applications and the runtime they stand on. These include Java agents, JARs that are capable of modifying Java class files at runtime; and JVMTI agents, native libraries that can perform deep hooking into the innards of the JVM itself. … Continue reading Tool Release – shouganaiyo-loader: A Tool to Force JVM Attaches →
...moreSome Musings on Common (eBPF) Linux Tracing Bugs

Published: 2021-08-06 04:54:28
Popularity: None
Author: Jeff Dileo
Keywords:
Having been in the game of auditing kprobe-based tracers for the past couple of years, and in light of this upcoming DEF CON on eBPF tracer race conditions (which you should go watch) being given by a friend of mine from the NYU(-Poly) (OSIR)IS(IS) lab, I figured I would wax poetic on some of the … Continue reading Some Musings on Common (eBPF) Linux Tracing Bugs →
...moreABSTRACT SHIMMER (CVE-2020-15257): Host Networking is root-Equivalent, Again

Published: 2020-12-10 15:00:00
Popularity: 4
Author: Jeff Dileo
Keywords:
This post is a technical discussion of the underlying vulnerability of CVE-2020-15257, and how it can be exploited. Our technical advisory on this issue is available here, but this post goes much further into the process that led to finding the issue, the practicalities of exploiting the vulnerability itself, various complications around fixing the issue, … Continue reading ABSTRACT SHIMMER (CVE-2020-15257): Host Networking is root-Equivalent, Again →
...moreTool Release: Sinking U-Boots with Depthcharge

Published: 2020-07-22 16:00:49
Popularity: 1
Author: Jon Szymaniak
Keywords:
Depthcharge is an extensible Python 3 toolkit designed to aid security researchers when analyzing a customized, product-specific build of the U-Boot bootloader. This blog post details the motivations for Depthcharge’s creation, highlights some key features, and exemplifies its use in a “tethered jailbreak” of a smart speaker that leverages secure boot functionality. I boot, you … Continue reading Tool Release: Sinking U-Boots with Depthcharge →
...moreAn offensive guide to the Authorization Code grant

Published: 2020-07-07 11:00:01
Popularity: 17
Author: Rami McCarthy
Keywords:
OAuth is the widely used standard for access delegation, enabling many of the “Sign in with X” buttons and “Connect your Calendar” features of modern Internet software. OAuth 2.0 is the most common and recent version of this specification, which defines four grant types (as well as various extensions), specifically suited for different use cases. … Continue reading An offensive guide to the Authorization Code grant →
...moreLDAPFragger: Bypassing network restrictions using LDAP attributes
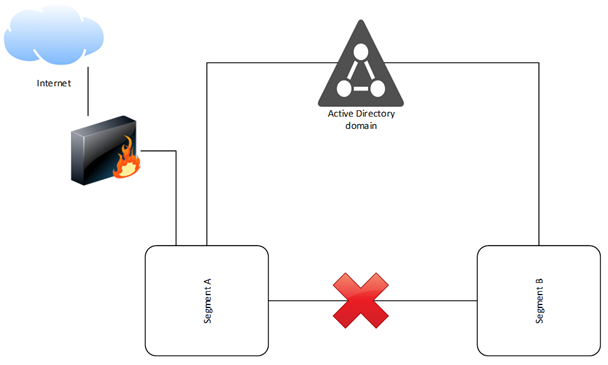
Published: 2020-03-19 10:00:00
Popularity: 4
Author: Rindert Kramer
Keywords:
Introduction A while back during a penetration test of an internal network, we encountered physically segmented networks. These networks contained workstations joined to the same Active Directory domain, however only one network segment could connect to the internet. To control workstations in both segments remotely with Cobalt Strike, we built a tool that uses the … Continue reading LDAPFragger: Bypassing network restrictions using LDAP attributes →
...moreA Survey of Istio's Network Security Features

Published: 2020-03-04 12:00:00
Popularity: 12
Author: jleadfordncc
Keywords:
🤖: "Secure network gates"
Istio is a service mesh, which, in general, exist as a compliment to container orchestrators (e.g. Kubernetes) in order to provide additional, service-centric features surrounding traffic management, security, and observability. Istio is arguably the most popular service mesh (using GitHub stars as a metric). This blog post assumes working familiarity with Kubernetes and microservices, but … Continue reading A Survey of Istio's Network Security Features →
...moreDeep Dive into Real-World Kubernetes Threats

Published: 2020-02-12 12:00:00
Popularity: 8
Author: nccmanning
Keywords:
On Saturday, February 1st, I gave my talk titled “Command and KubeCTL: Real-World Kubernetes Security for Pentesters” at Shmoocon 2020. I’m following up with this post that goes into more details than I could cover in 50 minutes. This will re-iterate the points I attempted to make, walk through the demo, and provide resources for … Continue reading Deep Dive into Real-World Kubernetes Threats →
...moreProperly Signed Certificates on CPE Devices

Published: 2020-02-04 09:04:08
Popularity: None
Author: m4ttlewis
Keywords:
🤖: ""Secure Certs Only""
During late January 2020, a hot topic surfaced between security professionals on an issue that has historically had different proposed solutions. This blog post seeks to explore these solutions and identify pragmatic approaches to risk reduction on this specific issue concerning Customer Premises Equipment (CPE) security. Two security researchers (Tom Pohl and Nick Starke) analysed … Continue reading Properly Signed Certificates on CPE Devices →
...moreTool Release – Enumerating Docker Registries with go-pillage-registries

Published: 2020-01-24 13:15:00
Popularity: 42
Author: jmakinenncc
Keywords:
🤖: "docker hack!"
Introduction Containerization solutions are becoming increasingly common throughout the industry due to their vast applications in logically separating and packaging processes to run consistently across environments. Docker represents these processes as images by packaging a base filesystem and initialization instructions for the runtime environment. Developers can use common base images and instruct Docker to execute … Continue reading Tool Release – Enumerating Docker Registries with go-pillage-registries →
...moreBluetooth Flaws Could Allow Global Tracking of Apple, Windows 10 Devices

Published: 2019-07-17 17:29:58
Popularity: 531
Author: Tara Seals
Keywords:
Identifying tokens and random addresses, meant to create anonymity, do not change in sync on some devices -- opening an attack vector.
...more
