Over a dozen vulnerabilities discovered in Tor audit, including a high-risk flaw that can be exploited to inject arbitrary bridges. The post Tor Code Audit Finds 17 Vulnerabilities appeared first on SecurityWeek.
...moreSummary
Total Articles Found: 145
Top sources:
Top Keywords:
- Vulnerabilities: 145
- NEWS & INDUSTRY: 88
- Mobile Security: 25
- Endpoint Security: 24
- Malware: 22
Top Authors
- Ionut Arghire: 40
- Eduard Kovacs: 36
- Tara Seals: 17
- Lindsey O'Donnell: 14
- Ryan Naraine: 13
Top Articles:
- MacOS Zero-Day Allows Trusted Apps to Run Malicious Code
- Kerberos Authentication Spoofing: Don’t Bypass the Spec
- Apple Patches Three Actively Exploited Zero-Days, Part of iOS Emergency Update
- Billions of Devices Open to Wi-Fi Eavesdropping Attacks
- BrakTooth Bluetooth Bugs Bite: Exploit Code, PoC Released
- Critical Bug in WordPress Plugins Open Sites to Hacker Takeovers
- Attackers Exploit Critical Adobe Flaw to Target Windows Users
- Citrix Bugs Allow Unauthenticated Code Injection, Data Theft
- Bluetooth Flaws Could Allow Global Tracking of Apple, Windows 10 Devices
- Remote Attackers Can Now Reach Protected Network Devices via NAT Slipstreaming
Tor Code Audit Finds 17 Vulnerabilities

Published: 2024-01-31 12:51:52
Popularity: 20
Author: Eduard Kovacs
Keywords:
Hackers Earn $400k on First Day at Pwn2Own Toronto 2023

Published: 2023-10-25 15:49:59
Popularity: 14
Author: Ionut Arghire
Keywords:
NAS devices, printers, IP cameras, speakers, and mobile phones were hacked on the first day at Pwn2Own Toronto 2023. The post Hackers Earn $400k on First Day at Pwn2Own Toronto 2023 appeared first on SecurityWeek.
...moreAndroid Security Update Patches Kernel Vulnerability Exploited by Spyware Vendor

Published: 2023-05-05 08:33:00
Popularity: 10
Author: Eduard Kovacs
Keywords:
Google’s latest Android security updates patch over 40 vulnerabilities, including CVE-2023-0266, a kernel flaw exploited as a zero-day by a spyware vendor. The post Android Security Update Patches Kernel Vulnerability Exploited by Spyware Vendor appeared first on SecurityWeek.
...moreSolarWinds Announces Upcoming Patches for High-Severity Vulnerabilities

Published: 2023-02-17 12:58:13
Popularity: 15
Author: Ionut Arghire
Keywords:
SolarWinds advisories describe multiple high-severity vulnerabilities that a Platform update will patch by the end of February. The post SolarWinds Announces Upcoming Patches for High-Severity Vulnerabilities appeared first on SecurityWeek.
...moreCritical Vulnerability in Premium Gift Cards WordPress Plugin Exploited in Attacks

Published: 2022-12-27 10:10:33
Popularity: 22
Author: Ionut Arghire
Keywords:
Defiant’s Wordfence team warns of a critical-severity vulnerability in the YITH WooCommerce Gift Cards premium WordPress plugin being exploited in attacks. read more
...moreNearly 300 Vulnerabilities Patched in Huawei's HarmonyOS in 2022

Published: 2023-01-03 11:39:44
Popularity: 11
Author: Eduard Kovacs
Keywords:
Chinese tech giant Huawei patched nearly 300 vulnerabilities in its HarmonyOS operating system in 2022. read more
...moreVulnerability in Acer Laptops Allows Attackers to Disable Secure Boot

Published: 2022-11-29 12:36:28
Popularity: 12
Author: Ionut Arghire
Keywords:
🤖: ""Boot fail""
A vulnerability impacting multiple Acer laptop models could allow an attacker to disable the Secure Boot feature and bypass security protections to install malware. read more
...moreGoogle Patches Eighth Chrome Zero-Day of 2022

Published: 2022-11-28 10:31:25
Popularity: 10
Author: Ionut Arghire
Keywords:
🤖: ""Chrome crashed again""
An emergency Chrome update that Google announced on Thanksgiving Day addresses an actively exploited zero-day in the popular browser. read more
...morePoC Code Published for High-Severity macOS Sandbox Escape Vulnerability

Published: 2022-11-21 12:47:17
Popularity: 12
Author: Ionut Arghire
Keywords:
🤖: "Buggy mac"
A security researcher has published details and proof-of-concept (PoC) code for a macOS vulnerability that could be exploited to escape a sandbox and execute code within Terminal. read more
...moreChrome 106 Update Patches Several High-Severity Vulnerabilities

Published: 2022-10-12 12:45:08
Popularity: 7
Author: Ionut Arghire
Keywords:
🤖: "bug hunt alert"
Google announced on Tuesday that the latest Chrome update patches six high-severity vulnerabilities, including four use-after-free bugs. All the newly resolved vulnerabilities were discovered by external researchers and the internet giant has handed out $38,000 in bug bounty rewards to the reporters. read more
...moreWordPress Security Update 6.0.3 Patches 16 Vulnerabilities

Published: 2022-10-19 11:31:39
Popularity: 16
Author: Eduard Kovacs
Keywords:
WordPress 6.0.3 started rolling out this week. The latest security release patches 16 vulnerabilities. read more
...moreCloudflare is not affected by the OpenSSL vulnerabilities CVE-2022-3602 and CVE-2022-3786
Published: 2022-11-02 09:31:15
Popularity: None
Author: Evan Johnson
Keywords:
Information on CVE-2022-3602 and CVE-2022-3786, and why Cloudflare was not impacted
...moreWordPress Sites Hacked via Zero-Day Vulnerability in WPGateway Plugin

Published: 2022-09-14 13:49:39
Popularity: 7
Author: Ionut Arghire
Keywords:
🤖: "Zero day hack"
Many WordPress sites are at risk of full compromise as attackers are actively exploiting a zero-day vulnerability in the WPGateway plugin, Defiant’s WordFence team warns. A premium plugin for the WPGateway cloud service, the WPGateway plugin provides users with WordPress installation, backup, and cloning capabilities. read more
...moreWordPress 6.0.2 Patches Vulnerability That Could Impact Millions of Legacy Sites

Published: 2022-08-31 11:39:06
Popularity: 13
Author: Ionut Arghire
Keywords:
The WordPress team this week announced the release of version 6.0.2 of the content management system (CMS), with patches for three security bugs, including a high-severity SQL injection vulnerability. read more
...more'DirtyCred' Vulnerability Haunting Linux Kernel for 8 Years

Published: 2022-08-23 12:35:00
Popularity: 9
Author: Ionut Arghire
Keywords:
🤖: "buggy kernel"
Academic researchers from Northwestern University have shared details on ‘DirtyCred’, a previously unknown privilege escalation vulnerability affecting the Linux kernel. read more
...moreSecurity Firm Discloses CrowdStrike Issue After 'Ridiculous Disclosure Process'

Published: 2022-08-23 11:29:19
Popularity: 27
Author: Eduard Kovacs
Keywords:
🤖: "Cyber Oops"
A security firm has disclosed the details of an issue affecting a CrowdStrike product after what it described as a ‘ridiculous vulnerability disclosure process’. CrowdStrike has provided some clarifications following the disclosure. read more
...moreSecure Boot Bypass Flaws Affect Bootloaders of Many Devices Made in Past Decade
Published: 2022-08-15 13:30:49
Popularity: 8
Author: Eduard Kovacs
Keywords:
🤖: "Bootjacked"
Bootloaders present in a majority of computers made in the past 10 years are affected by Secure Boot bypass vulnerabilities, according to firmware security company Eclypsium. read more
...moreGoogle Patches Critical Android Flaw Allowing Remote Code Execution via Bluetooth

Published: 2022-08-02 10:30:19
Popularity: 14
Author: Eduard Kovacs
Keywords:
Google on Monday published a security bulletin describing the latest round of patches for the Android operating system. Three dozen vulnerabilities have been fixed, including a critical issue that can be exploited for remote code execution over Bluetooth. read more
...moreLenovo Patches UEFI Code Execution Vulnerability Affecting Many Laptops

Published: 2022-07-13 20:02:47
Popularity: 19
Author: Eduard Kovacs
Keywords:
🤖: ""UEFI bugger""
Lenovo has released a security advisory to inform customers that more than 70 of its laptops are affected by a UEFI/BIOS vulnerability that can lead to arbitrary code execution. read more
...moreNew Database Catalogs Cloud Vulnerabilities, Security Issues
Published: 2022-06-28 13:01:05
Popularity: 12
Author: Eduard Kovacs
Keywords:
Cloud security company Wiz has announced the launch of a new database whose goal is to keep track of vulnerabilities and other security issues affecting cloud services. read more
...moreGoogle Patches 14 Vulnerabilities With Release of Chrome 103

Published: 2022-06-22 12:10:20
Popularity: 14
Author: Ionut Arghire
Keywords:
Google this week announced the release of Chrome 103 to the stable channel with patches for a total of 14 vulnerabilities, including nine reported by external researchers. The most severe of these bugs is CVE-2022-2156, which is described as a critical-severity use-after-free issue in Base. read more
...moreExploited Vulnerability Patched in WordPress Plugin With Over 1 Million Installations

Published: 2022-06-17 12:00:51
Popularity: 13
Author: Ionut Arghire
Keywords:
More than one million WordPress websites were potentially impacted by a critical Ninja Forms plugin vulnerability that appears to have been exploited in the wild. With over one million installations, the popular Ninja Forms plugin helps administrators add customizable forms to their WordPress sites. read more
...moreChina-linked APT Flew Under Radar for Decade

Published: 2022-06-17 13:34:04
Popularity: 57
Author: Nate Nelson
Keywords:
Evidence suggests that a just-discovered APT has been active since 2013.
...moreReport: L3 Emerges as Suitor for Embattled NSO Group

Published: 2022-06-14 16:18:52
Popularity: 9
Author: Ryan Naraine
Keywords:
🤖: "Spy game 😏"
L3 Technologies, a U.S. government contractor that sells aerospace and defense technology, has emerged as a suitor for Israeli exploit merchant NSO Group. read more
...moreMillions of Budget Smartphones With UNISOC Chips Vulnerable to Remote DoS Attacks

Published: 2022-06-02 15:00:17
Popularity: 10
Author: Eduard Kovacs
Keywords:
🤖: ""bugged phones""
Millions of budget smartphones that use UNISOC chipsets could have their communications remotely disrupted by hackers due to a critical vulnerability discovered recently by researchers at cybersecurity firm Check Point. read more
...moreResearchers Spot Supply Chain Attack Targeting GitLab CI Pipelines

Published: 2022-05-19 17:35:51
Popularity: 13
Author: Ryan Naraine
Keywords:
Security researchers at SentinelLabs are calling attention to a software chain supply attack targeting Rust developers with malware aimed directly at infecting GitLab Continuous Integration (CI) pipelines. read more
...moreGoogle Discloses Details of Zoom Zero-Click Remote Code Execution Exploit

Published: 2022-05-25 10:37:49
Popularity: 12
Author: Eduard Kovacs
Keywords:
Google’s Project Zero has disclosed the details of a zero-click remote code execution exploit targeting the Zoom video conferencing software. read more
...moreCritical Vulnerability in Premium WordPress Themes Allows for Site Takeover

Published: 2022-05-19 13:03:37
Popularity: 238
Author: Elizabeth Montalbano
Keywords:
Privilege escalation flaw discovered in the Jupiter and JupiterX Core Plugin affects more than 90,000 sites.
...moreNVIDIA Patches Code Execution Vulnerabilities in Graphics Driver

Published: 2022-05-18 10:21:17
Popularity: 18
Author: Ionut Arghire
Keywords:
🤖: ""Crashing graphics""
NVIDIA has announced the roll-out of updates for its graphics drivers to address multiple vulnerabilities, including four CVEs rated “high severity.” read more
...moreLarge-Scale Attack Targeting Tatsu Builder WordPress Plugin

Published: 2022-05-18 08:38:10
Popularity: 29
Author: Ionut Arghire
Keywords:
🤖: "Security breach!"
Tens of thousands of WordPress websites are potentially at risk of compromise as part of an ongoing large-scale attack targeting a remote code execution vulnerability in the Tatsu Builder plugin. read more
...moreChrome 101 Update Patches High-Severity Vulnerabilities

Published: 2022-05-11 15:37:18
Popularity: 11
Author: Ionut Arghire
Keywords:
🤖: "Browser crisis!"
Google this week announced the release of a Chrome browser update that resolves a total of 13 vulnerabilities, including nine that were reported by external researchers. Of the externally reported security holes, seven are use-after-free bugs – these types of vulnerabilities could lead to arbitrary code execution. read more
...moreUnpatched DNS Bug Puts Millions of Routers, IoT Devices at Risk

Published: 2022-05-04 10:27:47
Popularity: 97
Author: Elizabeth Montalbano
Keywords:
A flaw in all versions of the popular C standard libraries uClibe and uClibe-ng can allow for DNS poisoning attacks against target devices.
...moreMillions of Java Apps Remain Vulnerable to Log4Shell

Published: 2022-04-27 12:11:25
Popularity: 70
Author: Elizabeth Montalbano
Keywords:
Four months after the critical flaw was discovered, attackers have a massive attack surface from which they can exploit the flaw and take over systems, researchers found.
...moreChrome 101 Patches 30 Vulnerabilities

Published: 2022-04-27 11:15:49
Popularity: 16
Author: Ionut Arghire
Keywords:
Google this week announced that Chrome 101 was released to the stable channel with 30 security fixes inside, including 25 for vulnerabilities identified by external security researchers. read more
...moreOracle Releases 520 New Security Patches With April 2022 CPU

Published: 2022-04-20 09:57:39
Popularity: 14
Author: Ionut Arghire
Keywords:
🤖: "Patching frenzy"
Oracle on Tuesday announced the release of 520 security fixes as part of its April 2022 Critical Patch Update (CPU), including nearly 300 for vulnerabilities that can be exploited remotely without authentication. read more
...moreFirmware Flaws Allow Disabling Secure Boot on Lenovo Laptops

Published: 2022-04-19 18:46:07
Popularity: 14
Author: Ionut Arghire
Keywords:
🤖: "Boot fail"
Computer maker Lenovo has started pushing security patches to address three vulnerabilities impacting the UEFI firmware of more than 110 laptop models. read more
...moreAdobe Patches Gaping Security Holes in Acrobat, Reader, Photoshop

Published: 2022-04-12 17:36:50
Popularity: 21
Author: Ryan Naraine
Keywords:
🤖: "security alert"
Adobe's security update engine revved into overdrive this month with the release of patches for at least 78 documented software vulnerabilities, some serious enough to expose corporate customers to remote code execution attacks. read more
...moreAcademics Devise Side-Channel Attack Targeting Multi-GPU Systems

Published: 2022-04-05 10:22:14
Popularity: 8
Author: Ionut Arghire
Keywords:
A group of academic researchers has devised a side-channel attack targeting architectures that rely on multiple graphics processing units (GPUs) for resource-intensive computational operations. read more
...moreLog4JShell Used to Swarm VMware Servers with Miners, Backdoors

Published: 2022-03-29 20:33:08
Popularity: 52
Author: Lisa Vaas
Keywords:
Researchers have found three backdoors and four miners in attacks exploiting the Log4Shell vulnerability, some of which are still ongoing.
...moreSonicWall Patches Critical Vulnerability in Firewall Appliances

Published: 2022-03-29 10:36:10
Popularity: 16
Author: Ionut Arghire
Keywords:
SonicWall has released patches for a critical-severity vulnerability in the web management interface of multiple firewall appliances. Tracked as CVE-2022-22274 (CVSS score of 9.4), the security flaw is described as a stack-based buffer overflow bug that impacts SonicOS. read more
...moreSoftware Supply Chain Weakness: Snyk Warns of 'Deliberate Sabotage' of NPM Ecosystem

Published: 2022-03-17 15:58:58
Popularity: 20
Author: Ryan Naraine
Keywords:
Software supply chain security fears escalated again this week with the discovery of what’s being described as "deliberate sabotage" of code in the open-source npm package manager ecosystem. read more
...moreGoogle Issues Emergency Fix for Chrome Zero-Day

Published: 2022-03-27 11:58:30
Popularity: 55
Author: Ionut Arghire
Keywords:
Google has issued an emergency security update for Chrome 99 to resolve a vulnerability for which a public exploit already exists. read more
...moreHigh-Severity UEFI Vulnerabilities Patched in Dell Enterprise Laptops

Published: 2022-03-22 11:51:19
Popularity: 7
Author: Ionut Arghire
Keywords:
🤖: "Firmware fail!"
Firmware security company Binarly this week disclosed the details of several vulnerabilities that impact the Unified Extensible Firmware Interface (UEFI) of multiple Dell enterprise laptop models. read more
...moreNew Variant of Spectre Attack Bypasses Intel and Arm Hardware Mitigations

Published: 2022-03-10 11:55:14
Popularity: 18
Author: Eduard Kovacs
Keywords:
🤖: ""Spectre strikes again""
A team of researchers from the Vrije Universiteit Amsterdam in the Netherlands has demonstrated a new Spectre attack variant that can bypass hardware mitigations implemented in recent years by Intel and Arm. read more
...moreCVE-2022-26143: A Zero-Day vulnerability for launching UDP amplification DDoS attacks
Published: 2022-03-08 15:22:13
Popularity: None
Author: Omer Yoachimik
Keywords:
A zero-day vulnerability in the Mitel MiCollab business phone system has recently been discovered (CVE-2022-26143). This vulnerability, called TP240PhoneHome, which Cloudflare customers are already protected against, can be used to launch UDP amplification attacks
...moreGoogle Patches 27 Vulnerabilities With Release of Chrome 98

Published: 2022-02-02 09:50:47
Popularity: 19
Author: Ionut Arghire
Keywords:
🤖: "Chrome patch party 🎉💻"
Google on Tuesday announced the release of Chrome 98 in the stable channel with a total of 27 security fixes inside, including 19 for vulnerabilities reported by external researchers. The most severe of these security defects could be exploited to execute arbitrary code with the same privileges as the Chrome browser has on the target system. read more
...moreXerox Quietly Patched Device-Bricking Flaw Affecting Some Printers

Published: 2022-01-28 11:41:48
Popularity: 20
Author: Ionut Arghire
Keywords:
Xerox patched a device-bricking vulnerability in certain printer models more than a year and a half ago, but said nothing until this week, when information on the bug became public. read more
...more20K WordPress Sites Exposed by Insecure Plugin REST-API

Published: 2022-01-21 18:19:37
Popularity: 34
Author: Becky Bracken
Keywords:
The WordPress WP HTML Mail plugin for personalized emails is vulnerable to code injection and phishing due to XSS.
...moreCritical SAP Vulnerability Allows Supply Chain Attacks

Published: 2022-01-17 13:13:42
Popularity: 15
Author: Ionut Arghire
Keywords:
🤖: ""sap hacked""
A critical vulnerability addressed recently in SAP NetWeaver AS ABAP and ABAP Platform could be abused to set up supply chain attacks, SAP security solutions provider SecurityBridge warns. read more
...moreNew Flaws Expose EVlink Electric Vehicle Charging Stations to Remote Hacking

Published: 2021-12-27 11:33:20
Popularity: 10
Author: Eduard Kovacs
Keywords:
🤖: ""Charging hacked""
Schneider Electric has patched several new vulnerabilities that expose its EVlink electric vehicle charging stations to remote hacker attacks. read more
...moreProject Zero Flags High-Risk Zoom Security Flaw

Published: 2021-11-29 19:03:13
Popularity: 23
Author: Ryan Naraine
Keywords:
Video conferencing software giant Zoom has shipped patches for a pair of security defects that expose Windows, macOS, Linux, iOS and Android users to malicious hacker attacks. read more
...moreGitHub Confirms Another Major NPM Security Defect

Published: 2021-11-16 16:39:16
Popularity: 15
Author: Ryan Naraine
Keywords:
Microsoft-owned GitHub is again flagging major security problems in the npm registry, warning that a pair of newly discovered vulnerabilities continue to expose the soft underbelly of the open-source software supply chain. read more
...moreBlacksmith: Rowhammer Fuzzer Bypasses Existing Protections

Published: 2021-11-16 20:07:55
Popularity: 4
Author: Ionut Arghire
Keywords:
🤖: "Hammer time crashes"
A group of security researchers devised a new attack that completely bypasses the existing mitigations against the Rowhammer vulnerability in dynamic random-access memory (DRAM) chips. read more
...moreBrakTooth Bluetooth Bugs Bite: Exploit Code, PoC Released

Published: 2021-11-05 17:00:57
Popularity: 932
Author: Lisa Vaas
Keywords:
CISA is urging vendors to patch, given the release of public exploit code & a proof of concept tool for bugs that open billions of devices – phones, PCs, toys, etc. – to DoS & code execution.
...moreZoho Password Manager Flaw Torched by Godzilla Webshell

Published: 2021-11-08 16:38:05
Popularity: 36
Author: Lisa Vaas
Keywords:
Researchers have spotted a second, worldwide campaign exploiting the Zoho zero-day: one that’s breached defense, energy and healthcare organizations.
...moreAndroid Patches Actively Exploited Zero-Day Kernel Bug

Published: 2021-11-02 17:20:42
Popularity: 49
Author: Lisa Vaas
Keywords:
Google’s Android November 2021 security updates plug 18 flaws in the framework and system components and 18 more in the kernel and vendor components.
...moreShrootless: macOS Vulnerability Found by Microsoft Allows Rootkit Installation

Published: 2021-10-29 13:28:08
Popularity: 9
Author: Ionut Arghire
Keywords:
🤖: "Rootkit alert!"
Microsoft on Thursday published information on a vulnerability in Apple’s macOS platform that could allow an attacker to bypass System Integrity Protection (SIP) and modify operating system files. read more
...moreTwitter Suspends Accounts Used to Snare Security Researchers

Published: 2021-10-18 16:23:21
Popularity: 88
Author: Lisa Vaas
Keywords:
The accounts were used to catfish security researchers into downloading malware in a long-running cyber-espionage campaign attributed to North Korea.
...moreResearchers Disclose New Side-Channel Attacks Affecting All AMD CPUs
Published: 2021-10-15 11:07:26
Popularity: 18
Author: Eduard Kovacs
Keywords:
Researchers have disclosed the details of new timing and power-based side-channel attacks that affect all CPUs made by AMD, but the chipmaker says no new mitigations are necessary. read more
...moreMFA Glitch Leads to 6K+ Coinbase Customers Getting Robbed

Published: 2021-10-01 20:08:23
Popularity: 191
Author: Lisa Vaas
Keywords:
Coinbase suspects phishing led to attackers getting personal details needed to access wallets but also blamed a flaw in its SMS-based 2FA.
...moreApple AirTag Zero-Day Weaponizes Trackers

Published: 2021-09-29 20:48:33
Popularity: 177
Author: Tara Seals
Keywords:
Apple's personal item-tracker devices can be used to deliver malware, slurp credentials, steal tokens and more thanks to XSS.
...moreAkamai to Acquire Guardicore in $600M Zero Trust Tech Deal
Published: 2021-09-29 17:03:38
Popularity: 5
Author: Ryan Naraine
Keywords:
Edge security and content delivery giant Akamai Technologies on Wednesday announced plans to spend $600 million to acquire Guardicore, an Israeli micro-segmentation technology startup. Akamai said the deal would add new capabilities to help customers thwart ransomware attacks by blocking the spread of malware within an already-compromised enterprise. read more
...moreApple Confirms New Zero-Day Attacks on Older iPhones
Published: 2021-09-23 20:39:09
Popularity: 8
Author: Ryan Naraine
Keywords:
Apple on Thursday confirmed a new zero-day exploit hitting older iPhones and warned that the security vulnerability also affects the macOS Catalina platform. read more
...moreAttacks Targeting OMIGOD Vulnerability Ramping Up
Published: 2021-09-21 03:45:05
Popularity: 13
Author: Ionut Arghire
Keywords:
Attackers are increasingly targeting a remote code execution vulnerability in the Open Management Infrastructure (OMI) framework that Microsoft released patches for earlier this month. read more
...moreAdobe Snuffs Critical Bugs in Acrobat, Experience Manager
Adobe releases security updates for 59 bugs affecting its core products, including Adobe Acrobat Reader, XMP Toolkit SDK and Photoshop.
...moreGoogle Warns of Exploited Zero-Days in Chrome Browser

Published: 2021-09-13 21:51:32
Popularity: 29
Author: Ryan Naraine
Keywords:
🤖: "Zero Day Alert"
Google has joined the list of major software providers scrambling to respond to zero-day exploits in the wild. read more
...moreSideWalk Backdoor Linked to China-Linked Spy Group ‘Grayfly’

Published: 2021-09-09 14:30:56
Popularity: 115
Author: Lisa Vaas
Keywords:
Grayfly campaigns have launched the novel malware against businesses in Taiwan, Vietnam, the US and Mexico and are targeting Exchange and MySQL servers.
...more‘Azurescape’ Kubernetes Attack Allows Cross-Container Cloud Compromise

Published: 2021-09-09 16:39:13
Popularity: 147
Author: Tara Seals
Keywords:
A chain of exploits could allow a malicious Azure user to infiltrate other customers' cloud instances within Microsoft's container-as-a-service offering.
...moreThousands of Fortinet VPN Account Credentials Leaked

Published: 2021-09-09 22:49:27
Popularity: 39
Author: Lisa Vaas
Keywords:
They were posted for free by former Babuk gang members who’ve bickered, squabbled and huffed off to start their own darn ransomware businesses, dagnabbit.
...moreRecently Patched Confluence Vulnerability Exploited in the Wild
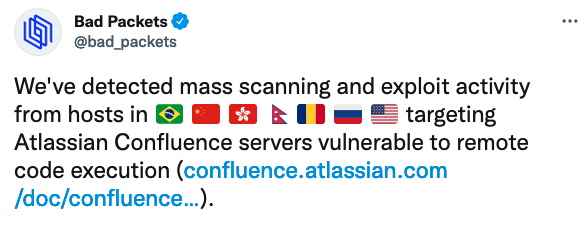
Published: 2021-09-02 10:47:16
Popularity: 7
Author: Eduard Kovacs
Keywords:
Hackers started exploiting a vulnerability in Atlassian’s Confluence enterprise collaboration product just one week after the availability of a patch was announced. read more
...moreKerberos Authentication Spoofing: Don’t Bypass the Spec

Published: 2021-08-18 13:19:15
Popularity: 1210
Author: Yaron Kassner
Keywords:
Yaron Kassner, CTO at Silverfort, discusses authentication-bypass bugs in Cisco ASA, F5 Big-IP, IBM QRadar and Palo Alto Networks PAN-OS.
...moreAdobe Plugs Critical Photoshop Security Flaws

Published: 2021-08-17 23:14:52
Popularity: 12
Author: Ryan Naraine
Keywords:
🤖: "Photoshop fail"
Adobe has issued a warning for a pair of major security vulnerabilities affecting its popular Photoshop image manipulation software. The flaws, rated critical, expose both Windows and MacOS users to code execution attacks, Adobe said in an advisory released Tuesday. read more
...moreNew DNS Attack Enables 'Nation-State Level Spying' via Domain Registration
Published: 2021-08-06 15:08:13
Popularity: 14
Author: Eduard Kovacs
Keywords:
A new domain name system (DNS) attack method that involves registering a domain with a specific name can be leveraged for what researchers described as “nation-state level spying.” read more
...moreAdobe Patches 21 Vulnerabilities Across Seven Products

Published: 2021-07-21 10:03:49
Popularity: 13
Author: Eduard Kovacs
Keywords:
🤖: ""Patch party""
Security updates released by Adobe on Tuesday for seven of its products patch a total of 21 vulnerabilities, including 15 flaws that have been assigned a critical severity rating. read more
...moreAdobe: Critical Flaws in Reader, Acrobat, Illustrator

Published: 2021-07-13 15:08:49
Popularity: 40
Author: Ryan Naraine
Keywords:
🤖: "Crashing software"
Adobe has issued multiple security advisories with patches for critical vulnerabilities in a wide range of software products, including the ever-present Adobe Acrobat and Reader application. read more
...moreCritical VMware Carbon Black Bug Allows Authentication Bypass
The 9.4-rated bug in AppC could give attackers admin rights, no authentication required, letting them attack anything from PoS to industrial control systems.
...moreGitHub Discloses Details of Easy-to-Exploit Linux Vulnerability

Published: 2021-06-11 13:09:45
Popularity: 12
Author: Eduard Kovacs
Keywords:
🤖: ""Linux pwned""
GitHub this week disclosed the details of an easy-to-exploit Linux vulnerability that can be leveraged to escalate privileges to root on the targeted system. The flaw, classified as high severity and tracked as CVE-2021-3560, impacts polkit, an authorization service that is present by default in many Linux distributions. read more
...moreGoogle Patches Critical Android RCE Bug

Published: 2021-06-08 19:02:25
Popularity: 68
Author: Tara Seals
Keywords:
Google's June security bulletin addresses 90+ bugs in Android and Pixel devices.
...moreVMware Urges Customers to Immediately Patch Critical vSphere Vulnerability

Published: 2021-05-26 14:29:30
Popularity: 9
Author: Eduard Kovacs
Keywords:
🤖: "patch party fail"
VMware has urged customers to immediately patch a critical vulnerability affecting vCenter Server, the management interface for vSphere environments. The vulnerability, tracked as CVE-2021-21985, was reported to VMware by Ricter Z of 360 Noah Lab and it has been patched in versions 6.5, 6.7 and 7.0 of vCenter Server. read more
...moreVulnerabilities in Visual Studio Code Extensions Expose Developers to Attacks

Published: 2021-05-27 14:09:48
Popularity: 10
Author: Ionut Arghire
Keywords:
🤖: ""Extension exploited""
Vulnerabilities in Visual Studio Code extensions could be exploited by malicious attackers to steal valuable information from developers and even compromise organizations, researchers with open-source software security firm Snyk say. read more
...moreResearchers Find Exploitable Bugs in Mercedes-Benz Cars

Published: 2021-05-18 20:24:37
Popularity: 93
Author: Ionut Arghire
Keywords:
🤖: "car hack"
Following an eight-month audit of the code in the latest infotainment system in Mercedes-Benz cars, security researchers with Tencent Security Keen Lab identified five vulnerabilities, four of which could be exploited for remote code execution. read more
...more$200,000 Awarded for Zero-Click Zoom Exploit at Pwn2Own

Published: 2021-04-08 11:13:54
Popularity: 47
Author: Eduard Kovacs
Keywords:
Two researchers earned $200,000 on the second day of the Pwn2Own 2021 hacking competition for a Zoom exploit allowing remote code execution without user interaction. read more
...moreNorth Korean .Gov Hackers Back With Fake Pen-Test Company

Published: 2021-03-31 20:57:11
Popularity: 78
Author: Ryan Naraine
Keywords:
A North Korean government-backed APT group has been caught using a fake pen-testing company and a range of sock puppet social media accounts in an escalation of a hacking campaign targeting security research professionals. read more
...moreZoom Screen-Sharing Glitch ‘Briefly’ Leaks Sensitive Data

Published: 2021-03-18 15:52:29
Popularity: 268
Author: Lindsey O'Donnell
Keywords:
A glitch in Zoom's screen-sharing feature shows parts of presenters' screens that they did not intend to share - potentially leaking emails or passwords.
...moreTutor LMS for WordPress Open to Info-Stealing Security Holes

Published: 2021-03-18 11:50:44
Popularity: 113
Author: Tara Seals
Keywords:
The popular learning-management system for teacher-student communication is rife with SQL-injection vulnerabilities.
...moreResearch Shows How Solar Energy Installations Can Be Abused by Hackers

Published: 2021-02-17 15:24:26
Popularity: 28
Author: Eduard Kovacs
Keywords:
Researchers at cybersecurity firm FireEye have analyzed a gateway device used for solar energy installations, and discovered vulnerabilities that could be useful to malicious hackers. read more
...moreCritical WordPress Plugin Flaw Allows Site Takeover

Published: 2021-02-08 21:11:57
Popularity: 124
Author: Lindsey O'Donnell
Keywords:
A patch in the NextGen Gallery WordPress plugin fixes critical and high-severity cross-site request forgery flaws.
...moreAdobe Patches Reader Vulnerability Exploited in the Wild

Published: 2021-02-09 18:29:39
Popularity: 24
Author: Eduard Kovacs
Keywords:
Adobe on Tuesday announced the availability of patches for 50 vulnerabilities across six of its products, including a zero-day vulnerability in Reader that has been exploited in the wild. read more
...moreAttackers Exploit Critical Adobe Flaw to Target Windows Users

Published: 2021-02-09 19:40:47
Popularity: 643
Author: Lindsey O'Donnell
Keywords:
A critical vulnerability in Adobe Reader has been exploited in "limited attacks."
...moreMisconfigured Baby Monitors Allow Unauthorized Viewing

Published: 2021-02-16 16:50:35
Popularity: 302
Author: Tara Seals
Keywords:
Hundreds of thousands of individuals are potentially affected by this vulnerability.
...moreThree New Vulnerabilities Patched in OpenSSL

Published: 2021-02-17 09:31:00
Popularity: 36
Author: Eduard Kovacs
Keywords:
read more
...moreIntel Squashes High-Severity Graphics Driver Flaws
Intel is warning on security bugs across its graphics drivers, server boards, compute modules and modems.
...moreVulnerabilities in Realtek Wi-Fi Module Expose Many Devices to Remote Attacks

Published: 2021-02-04 13:21:18
Popularity: 24
Author: Ionut Arghire
Keywords:
Major vulnerabilities in the Realtek RTL8195A Wi-Fi module expose embedded devices used in a myriad of industries to remote attacks, researchers with automated device security platform provider Vdoo reveal. read more
...moreUnpatched WordPress Plugin Code-Injection Bug Afflicts 50K Sites

Published: 2021-02-05 22:20:20
Popularity: 133
Author: Tara Seals
Keywords:
An CRSF-to-stored-XSS security bug plagues 50,000 'Contact Form 7' Style users.
...moreGoogle Patches Over a Dozen High-Severity Privilege Escalation Flaws in Android

Published: 2021-02-03 04:38:32
Popularity: 36
Author: Ionut Arghire
Keywords:
Google this week published its Android security bulletin for February 2021, which includes information on more than 40 vulnerabilities, most of which could lead to elevation of privilege. read more
...moreSolarWinds Orion Bug Allows Easy Remote-Code Execution and Takeover
The by-now infamous company has issued patches for three security vulnerabilities in total.
...moreWeak ACLs in Adobe ColdFusion Allow Privilege Escalation

Published: 2021-02-03 12:59:51
Popularity: 36
Author: Ionut Arghire
Keywords:
A newly disclosed vulnerability in Adobe ColdFusion could be exploited by unprivileged users for the execution of arbitrary code with SYSTEM privileges. The popular commercial web-application development platform uses the CFML scripting language and is mainly used for the creation of data-driven websites. read more
...moreApple Issues Patches for NAT Slipstreaming 2.0 Attack

Published: 2021-02-02 11:26:42
Popularity: 42
Author: Ionut Arghire
Keywords:
Apple this week released security updates to address multiple vulnerabilities in macOS and Safari, including a flaw that can be exploited for the recently disclosed NAT Slipstreaming 2.0 attack. read more
...moreApple Adds 'BlastDoor' to Secure iPhones From Zero-Click Attacks

Published: 2021-01-28 20:31:16
Popularity: 70
Author: Ryan Naraine
Keywords:
Apple has quietly added several anti-exploit mitigations into its flagship mobile operating system in what appears to be a specific response to zero-click iMessage attacks observed in the wild. read more
...moreRemote Attackers Can Now Reach Protected Network Devices via NAT Slipstreaming

Published: 2021-01-27 20:32:55
Popularity: 440
Author: Tara Seals
Keywords:
A new version of NAT slipstreaming allows cybercriminals an easy path to devices that aren't connected to the internet.
...moreADT Security Camera Flaws Open Homes to Eavesdropping

Published: 2021-01-27 18:05:51
Popularity: 227
Author: Lindsey O'Donnell
Keywords:
Researchers publicly disclosed flaws in ADT's LifeShield DIY HD Video Doorbell, which could have allowed local attackers to access credentials, video feeds and more.
...morePwn2Own 2021: Hackers Offered $200,000 for Zoom, Microsoft Teams Exploits

Published: 2021-01-27 09:49:45
Popularity: 54
Author: Eduard Kovacs
Keywords:
Trend Micro’s Zero Day Initiative (ZDI) on Tuesday announced the targets, prizes and rules for the Pwn2Own Vancouver 2021 hacking competition, a hybrid event scheduled to take place on April 6-8. read more
...moreApple Patches Three Actively Exploited Zero-Days, Part of iOS Emergency Update

Published: 2021-01-27 12:21:28
Popularity: 1153
Author: Elizabeth Montalbano
Keywords:
An anonymous researcher identified bugs in the software’s kernel and WebKit browser engine that are likely part of an exploit chain.
...moreReport: TikTok Harvested MAC Addresses By Exploiting Android Loophole

Published: 2021-01-14 16:21:03
Popularity: 287
Author: SecurityWeek News
Keywords:
The ongoing controversies surrounding TikTok hit a new gear on Thursday with a bombshell report accusing the Chinese company of spying on millions of Android users using a technique banned by Google. read more
...moreGoogle Warns of Critical Android Remote Code Execution Bug

Published: 2021-01-05 20:21:40
Popularity: 394
Author: Lindsey O'Donnell
Keywords:
Google's Android security update addressed 43 bugs overall affecting Android handsets, including Samsung phones.
...moreHardcoded Credentials Expose Zyxel Firewalls and WLAN Controllers to Remote Attacks

Published: 2021-01-04 15:12:42
Popularity: 24
Author: Ionut Arghire
Keywords:
🤖: "passwords out"
Several Zyxel firewall and WLAN controller products contain hardcoded credentials for an undocumented user account that has admin privileges. Identified by EYE security researcher Niels Teusink, the vulnerability exists because the password for the “zyfwp” user account was stored in plaintext and was visible in one of the binaries on the system. read more
...moreApple Loses Copyright Suit Against Security Startup
A federal judge Tuesday dismissed Apple's copyright infringement lawsuit against cybersecurity startup Corellium in a case which could have implications for researchers who find software bugs and vulnerabilities. read more
...moreWidespread Scans Underway for RCE Bugs in WordPress Websites

Published: 2020-11-18 21:53:55
Popularity: 172
Author: Tara Seals
Keywords:
WordPress websites using buggy Epsilon Framework themes are being hunted by hackers.
...moreVulnerabilities Expose Thousands of MobileIron Servers to Remote Attacks

Published: 2020-09-14 12:18:11
Popularity: 44
Author: Eduard Kovacs
Keywords:
Researchers have disclosed the details of several potentially serious vulnerabilities affecting MobileIron’s mobile device management (MDM) solutions, including a flaw that can be exploited by an unauthenticated attacker for remote code execution on affected servers. read more
...moreAdobe Patches Critical Code Execution Flaws in AEM, FrameMaker, InDesign

Published: 2020-09-08 18:07:19
Popularity: 24
Author: Eduard Kovacs
Keywords:
Adobe on Tuesday informed customers that it has patched a total of 18 vulnerabilities across its Experience Manager (AEM), FrameMaker and InDesign products. read more
...moreChinese Researchers Show How They Remotely Hacked a Mercedes-Benz

Published: 2020-08-07 19:11:40
Popularity: 100
Author: Eduard Kovacs
Keywords:
read more
...moreHigh-Severity Android RCE Flaw Fixed in August Security Update

Published: 2020-08-05 16:14:26
Popularity: 124
Author: Lindsey O'Donnell
Keywords:
Google addressed high-severity and critical flaws tied to 54 CVEs in this month's Android security bulletin.
...moreZoom Flaw Could Have Allowed Hackers To Crack Meeting Passcodes

Published: 2020-07-30 21:40:31
Popularity: 146
Author: Lindsey O'Donnell
Keywords:
Zoom has fixed the issue, which stemmed from a lack of checks against incorrect passcode attempts.
...moreCitrix Bugs Allow Unauthenticated Code Injection, Data Theft

Published: 2020-07-07 14:44:30
Popularity: 550
Author: Tara Seals
Keywords:
Admins should patch their Citrix ADC and Gateway installs immediately.
...moreApache Guacamole Opens Door for Total Control of Remote Footprint

Published: 2020-07-02 16:14:46
Popularity: 117
Author: Tara Seals
Keywords:
Several vulnerabilities can be chained together for a full exploit.
...moreAMD Preparing Patches for UEFI SMM Vulnerability

Published: 2020-06-22 10:11:26
Popularity: 40
Author: Ionut Arghire
Keywords:
🤖: ""Firmware fix""
AMD last week said it was preparing patches for a vulnerability affecting the System Management Mode (SMM) of the Unified Extensible Firmware Interface (UEFI) shipped with systems that use certain notebook and embedded processors. read more
...moreAdobe Patches 18 Critical Flaws in Out-Of-Band Update

Published: 2020-06-16 19:29:09
Popularity: 205
Author: Lindsey O'Donnell
Keywords:
Critical vulnerabilities were patched in Adobe After Effects, Illustrator, Premiere Pro, Premiere Rush and Audition.
...moreMicrosoft Patches Critical Code Execution Vulnerabilities in Windows, Browsers

Published: 2020-06-10 03:32:35
Popularity: 29
Author: Eduard Kovacs
Keywords:
Microsoft’s security updates for June 2020 patch 129 vulnerabilities, including 11 critical remote code execution flaws affecting Windows, the Edge and Internet Explorer browsers, and SharePoint. read more
...more'SMBleed' Vulnerability Impacts Windows SMB Protocol

Published: 2020-06-10 17:46:48
Popularity: 36
Author: Ionut Arghire
Keywords:
One of the vulnerabilities that Microsoft addressed on June 2020 Patch Tuesday is a Server Message Block (SMB) protocol bug that could allow an attacker to leak kernel memory remotely, without authentication. read more
...moreCritical Intel Flaws Fixed in Active Management Technology

Published: 2020-06-10 18:37:53
Popularity: 138
Author: Lindsey O'Donnell
Keywords:
Two critical flaws in Intel AMT, which could enable privilege escalation, were patched along with 20 other bugs in its June security update.
...moreCritical Flaw in SEO Plugin Exposed Many WordPress Sites to Attacks

Published: 2020-04-01 12:05:32
Popularity: 33
Author: Ionut Arghire
Keywords:
A critical vulnerability in the Rank Math SEO plugin for WordPress could allow attackers to lock administrators out of their own websites, WordPress security company Defiant reports. read more
...moreNo Patch for VPN Bypass Flaw Discovered in iOS

Published: 2020-03-26 19:55:19
Popularity: 49
Author: Eduard Kovacs
Keywords:
🤖: ""VPN fail""
Proton Technologies, the company behind the privacy-focused ProtonMail and ProtonVPN services, this week disclosed the existence of a vulnerability in Apple’s iOS mobile operating system that prevents VPN applications from encrypting all traffic. read more
...moreCritical Flaw in VMware Workstation, Fusion Allows Code Execution on Host From Guest

Published: 2020-03-13 15:21:36
Popularity: 72
Author: Eduard Kovacs
Keywords:
🤖: ""Vulnerable VMs""
VMware has patched three serious vulnerabilities in its products, including a critical flaw in Workstation and Fusion that can be exploited to execute arbitrary code on the host from the guest operating system. The critical flaw, tracked as CVE-2020-3947, is caused by a use-after-free bug in the vmnetdhcp component. read more
...moreCisco Patches Remote Code Execution Flaws in Webex Player

Published: 2020-03-04 21:06:42
Popularity: 24
Author: Ionut Arghire
Keywords:
🤖: ""Code execution failure""
Cisco has released patches to address more than a dozen vulnerabilities across various products, including two code execution bugs in Webex Player that could be exploited remotely. read more
...moreBillions of Devices Open to Wi-Fi Eavesdropping Attacks

Published: 2020-02-27 04:07:18
Popularity: 990
Author: Tara Seals
Keywords:
The Kr00k bug arises from an all-zero encryption key in Wi-Fi chips that reveals communications from devices from Amazon, Apple, Google, Samsung and others.
...moreFlaw in WordPress Themes Plugin Allowed Hackers to Become Site Admin

Published: 2020-02-17 15:44:34
Popularity: 41
Author: Eduard Kovacs
Keywords:
🤖: ""Security breach""
A serious vulnerability found in a WordPress themes plugin with over 200,000 active installations can be exploited to wipe a website’s database and gain administrator access to the site. read more
...moreGoogle Sets Record High in Bug-Bounty Payouts

Published: 2020-01-29 19:56:14
Popularity: 135
Author: Tara Seals
Keywords:
After a year of big changes, white hats reaped more from Google's programs than ever before.
...moreThai Officials Say Prison Cameras Were Hacked, Broadcast

Published: 2019-12-26 15:07:05
Popularity: 40
Author: Associated Press
Keywords:
Authorities in Thailand say they are investigating an apparent online break-in by a computer hacker that allowed him to broadcast surveillance video from inside a prison in the country's south. read more
...moreCritical Bug in WordPress Plugins Open Sites to Hacker Takeovers

Published: 2019-12-13 18:33:39
Popularity: 743
Author: Tom Spring
Keywords:
One flaw found in WordPress plugins Ultimate Addons for Beaver Builder and Ultimate Addons for Elementor is actively being exploited.
...moreResearchers Disclose Another SIM Card Attack Possibly Impacting Millions
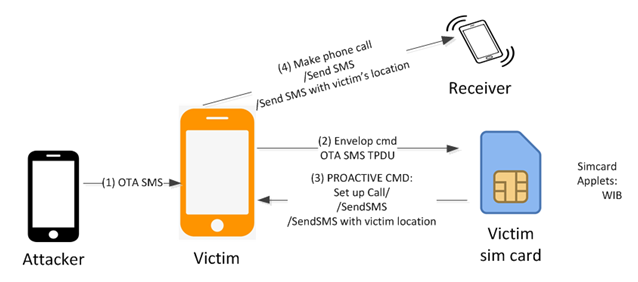
Published: 2019-09-27 11:33:27
Popularity: 76
Author: Eduard Kovacs
Keywords:
A new variant of a recently disclosed SIM card attack method could expose millions of mobile phones to remote hacking, researchers have warned. read more
...moreVulnerability Patched in Firefox Password Manager

Published: 2019-08-15 18:04:13
Popularity: 38
Author: Eduard Kovacs
Keywords:
🤖: "Browser blues"
The latest update released by Mozilla for Firefox patches a vulnerability that can be exploited to bypass the master password of the built-in password manager and obtain stored passwords. read more
...moreBluetooth Flaws Could Allow Global Tracking of Apple, Windows 10 Devices

Published: 2019-07-17 17:29:58
Popularity: 531
Author: Tara Seals
Keywords:
Identifying tokens and random addresses, meant to create anonymity, do not change in sync on some devices -- opening an attack vector.
...moreThreat Actor Poisons OpenPGP Certificates

Published: 2019-07-01 15:30:03
Popularity: 29
Author: Ionut Arghire
Keywords:
🤖: "Crypto chaos"
Poisoned certificates are in the OpenPGP SKS keyserver network after an unknown threat actor targeted the OpenPGP certificates of two high-profile community contributors. read more
...moreFDA Warns of Potentially Fatal Flaws in Medtronic Insulin Pumps

Published: 2019-06-28 15:14:43
Popularity: 259
Author: Lindsey O'Donnell
Keywords:
The FDA sent out an urgent advisory warning of serious flaws in Medtronic's insulin pumps, which are used by thousands across the U.S.
...moreMongoDB Leak Exposed Millions of Medical Insurance Records

Published: 2019-06-28 19:52:31
Popularity: 257
Author: Lindsey O'Donnell
Keywords:
Millions of records containing personal information and medical insurance data were exposed by a database belonging to insurance marketing website MedicareSupplement.com.
...moreVulnerabilities Expose BD Infusion Therapy Devices to Attacks

Published: 2019-06-14 14:16:23
Popularity: 51
Author: Eduard Kovacs
Keywords:
🤖: ""Infusion hack""
CyberMDX, a research and analysis company specializing in medical device security, on Thursday revealed that its employees identified two serious vulnerabilities in infusion therapy products from medical technology firm BD. read more
...moreIntel NUC Firmware Open to Privilege Escalation, DoS and Information Disclosure

Published: 2019-06-12 13:25:43
Popularity: 168
Author: Lindsey O'Donnell
Keywords:
Intel has patched seven high-severity vulnerabilities in its mini PC NUC kit firmware.
...moreMacOS Zero-Day Allows Trusted Apps to Run Malicious Code

Published: 2019-06-03 12:28:42
Popularity: 1233
Author: Tom Spring
Keywords:
Apple 0-Day allows hackers to mimic mouse-clicks to allow malicious behavior on macOS Mojave, despite mitigations.
...moreLinux Kernel Flaw Allows Remote Code-Execution

Published: 2019-05-14 15:21:17
Popularity: 362
Author: Tara Seals
Keywords:
The bug is remotely exploitable without authentication or user interaction.
...moreIntel MDS Vulnerabilities: What You Need to Know

Published: 2019-05-15 14:29:55
Popularity: 64
Author: Eduard Kovacs
Keywords:
read more
...moreGoogle Titan Security Key Recalled After Bluetooth Pairing Bug

Published: 2019-05-15 20:01:32
Popularity: 331
Author: Lindsey O'Donnell
Keywords:
Google is offering free replacements for its Titan Security Key after discovering a misconfiguration in its pairing protocols.
...moreAndroid-Based Sony Smart-TVs Open to Image Pilfering

Published: 2019-04-25 21:13:31
Popularity: 304
Author: Tara Seals
Keywords:
A pair of bugs would allow attackers to compromise the WiFi password of a TV and the multimedia stored inside it.
...moreCisco Finds Serious Flaws in Sierra Wireless AirLink Devices

Published: 2019-04-26 13:55:06
Popularity: 153
Author: Eduard Kovacs
Keywords:
Cisco’s Talos research and intelligence group on Thursday disclosed the details of nearly a dozen vulnerabilities uncovered in Sierra Wireless AirLink devices, including serious flaws that can be exploited to change system settings, execute arbitrary code, and modify passwords. read more
...moreCVE-2019-7238: Insufficient Access Controls in Sonatype Nexus Repository Manager 3 Allows Remote Code Execution

Published: 2019-03-14 12:01:00
Popularity: 65
Author: Trend Micro
Keywords:
A critical remote code execution (RCE) vulnerability (CVE-2019-7238) was found in Sonatype’s Nexus Repository Manager (NXRM) 3, an open source project that allows developers, such as DevOps professionals, to manage software components required for software development, application deployment, and automated hardware provisioning. The post CVE-2019-7238: Insufficient Access Controls in Sonatype Nexus Repository Manager 3 Allows Remote Code Execution appeared first on .
...moreUnpatched Windows Bug Allows Attackers to Spoof Security Dialog Boxes

Published: 2019-03-12 15:09:12
Popularity: 92
Author: Tara Seals
Keywords:
Microsoft won't be patching the bug, but a proof of concept shows the potential for successful malware implantation.
...more



