Widely used forensic software can be exploited to infect investigators' computers.
...moreSummary
Top Articles:
- In epic hack, Signal developer turns the tables on forensics firm Cellebrite
- Multiple “CIA failures” led to theft of agency’s top-secret hacking tools
- The wave of domain hijackings besetting the Internet is worse than we thought
- Telegram feature exposes your precise address to hackers
- A bevy of new features makes iOS 14 the most secure mobile OS ever
- Hackers obtained Twitter DMs for 36 high-profile account holders
- Why big ISPs aren’t happy about Google’s plans for encrypted DNS
In epic hack, Signal developer turns the tables on forensics firm Cellebrite
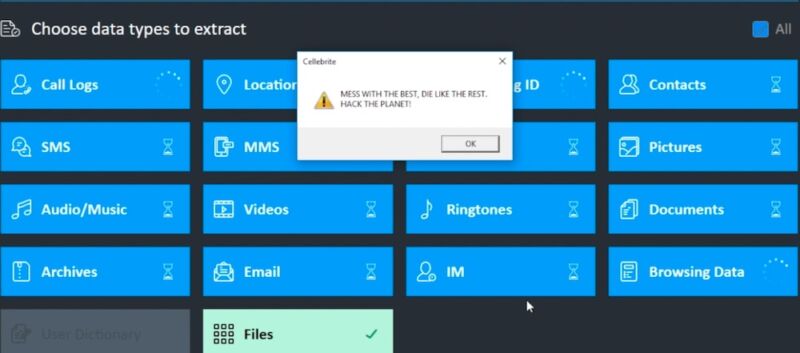
Published: 2021-04-21 19:30:08
Popularity: 3439
Author: Dan Goodin
Keywords:
Telegram feature exposes your precise address to hackers

Published: 2021-01-05 21:40:31
Popularity: 633
Author: Dan Goodin
Keywords:
Messenger maker has expressed no plans to fix location disclosure flaw.
...moreA bevy of new features makes iOS 14 the most secure mobile OS ever

Published: 2020-09-18 11:48:26
Popularity: 265
Author: Dan Goodin
Keywords:
Behold: The useful and not-so-useful privacy features you've been waiting for.
...moreHackers obtained Twitter DMs for 36 high-profile account holders

Published: 2020-07-23 02:27:18
Popularity: 36
Author: Dan Goodin
Keywords:
Hack also exposed phone numbers, email addresses, and other PI for 130 users.
...moreMultiple “CIA failures” led to theft of agency’s top-secret hacking tools

Published: 2020-06-16 21:06:36
Popularity: 976
Author: Dan Goodin
Keywords:
Vault 7, the worst data theft in CIA history, could have been avoided, report finds.
...moreWhy big ISPs aren’t happy about Google’s plans for encrypted DNS

Published: 2019-09-30 22:57:31
Popularity: None
Author: Timothy B. Lee
Keywords:
DNS over HTTPS will make it harder for ISPs to monitor or modify DNS queries.
...moreThe wave of domain hijackings besetting the Internet is worse than we thought

Published: 2019-04-17 15:00:58
Popularity: 822
Author: Dan Goodin
Keywords:
Despite widespread attention since January, DNS campaign shows no signs of abating.
...more