To help preserve a safe Internet for content creators, we’ve just launched a brand new “easy button” to block all AI bots. It’s available for all customers, including those on our free tier
...moreSummary
Total Articles Found: 25
Top sources:
Top Keywords:
- Security: 3
- Bots: 2
- Vulnerabilities: 2
- Birthday Week: 2
- Bot Management: 1
Top Authors
- Alex Bocharov: 1
- Kenny Johnson: 1
- Oxana Kharitonova: 1
- Evan Johnson: 1
- Bas Westerbaan: 1
Top Articles:
- Announcing AMP Real URL
- Declare your AIndependence: block AI bots, scrapers and crawlers with a single click
- Announcing Turnstile, a user-friendly, privacy-preserving alternative to CAPTCHA
- Speeding up HTTPS and HTTP/3 negotiation with... DNS
- Introducing post-quantum Cloudflare Tunnel
- Cloudflare incident on January 24, 2023
- The Linux Kernel Key Retention Service and why you should use it in your next application
- Cloudflare is not affected by the OpenSSL vulnerabilities CVE-2022-3602 and CVE-2022-3786
- CVE-2022-1096: How Cloudflare Zero Trust provides protection from zero day browser vulnerabilities
- CVE-2022-26143: A Zero-Day vulnerability for launching UDP amplification DDoS attacks
Declare your AIndependence: block AI bots, scrapers and crawlers with a single click

Published: 2024-07-03 13:00:26
Popularity: 206
Author: Alex Bocharov
Keywords:
🤖: ""Click Block""
Cloudflare incident on January 24, 2023
Several Cloudflare services became unavailable for 121 minutes on January 24th, 2023 due to an error releasing code that manages service tokens. The incident degraded a wide range of Cloudflare products
...moreThe Linux Kernel Key Retention Service and why you should use it in your next application

Published: 2022-11-28 14:57:20
Popularity: None
Author: Oxana Kharitonova
Keywords:
Many leaks happen because of software bugs and security vulnerabilities. In this post we will learn how the Linux kernel can help protect cryptographic keys from a whole class of potential security vulnerabilities: memory access violations.
...moreCloudflare is not affected by the OpenSSL vulnerabilities CVE-2022-3602 and CVE-2022-3786
Published: 2022-11-02 09:31:15
Popularity: None
Author: Evan Johnson
Keywords:
Information on CVE-2022-3602 and CVE-2022-3786, and why Cloudflare was not impacted
...moreIntroducing post-quantum Cloudflare Tunnel
Published: 2022-10-03 13:00:00
Popularity: 2
Author: Bas Westerbaan
Keywords:
Every connection we make post-quantum secure, we remove one opportunity for compromise: that's why we are announcing post-quantum Cloudflare Tunnel to help you secure every connection to our network
...moreAnnouncing Turnstile, a user-friendly, privacy-preserving alternative to CAPTCHA
Published: 2022-09-28 13:01:00
Popularity: 105
Author: Reid Tatoris
Keywords:
Any website can use a simple API to replace CAPTCHAs with our invisible alternative, whether they’re on the Cloudflare network or not.
...moreCVE-2022-1096: How Cloudflare Zero Trust provides protection from zero day browser vulnerabilities

Published: 2022-03-29 15:51:37
Popularity: None
Author: Tim Obezuk
Keywords:
CVE-2022-1096 is yet another zero day vulnerability affecting web browsers. Cloudflare zero trust mitigates the risk of zero day attacks in the browser and has been patched
...moreCVE-2022-26143: A Zero-Day vulnerability for launching UDP amplification DDoS attacks
Published: 2022-03-08 15:22:13
Popularity: None
Author: Omer Yoachimik
Keywords:
A zero-day vulnerability in the Mitel MiCollab business phone system has recently been discovered (CVE-2022-26143). This vulnerability, called TP240PhoneHome, which Cloudflare customers are already protected against, can be used to launch UDP amplification attacks
...moreSpeeding up HTTPS and HTTP/3 negotiation with... DNS

Published: 2020-09-30 13:00:00
Popularity: 90
Author: Alessandro Ghedini
Keywords:
A look at a new DNS resource record intended to speed-up negotiation of HTTP security and performance features and how it will help make the web faster.
...moreWARP is here (sorry it took so long)

Published: 2019-09-25 16:39:29
Popularity: None
Author: None
🤖: "Warp speed away!"
Today, after a longer than expected wait, we're opening WARP and WARP Plus to the general public. If you haven’t heard about it yet, WARP is a mobile app designed for everyone which uses our global network to secure all of your phone’s Internet traffic.
...moreHow Verizon and a BGP Optimizer Knocked Large Parts of the Internet Offline Today
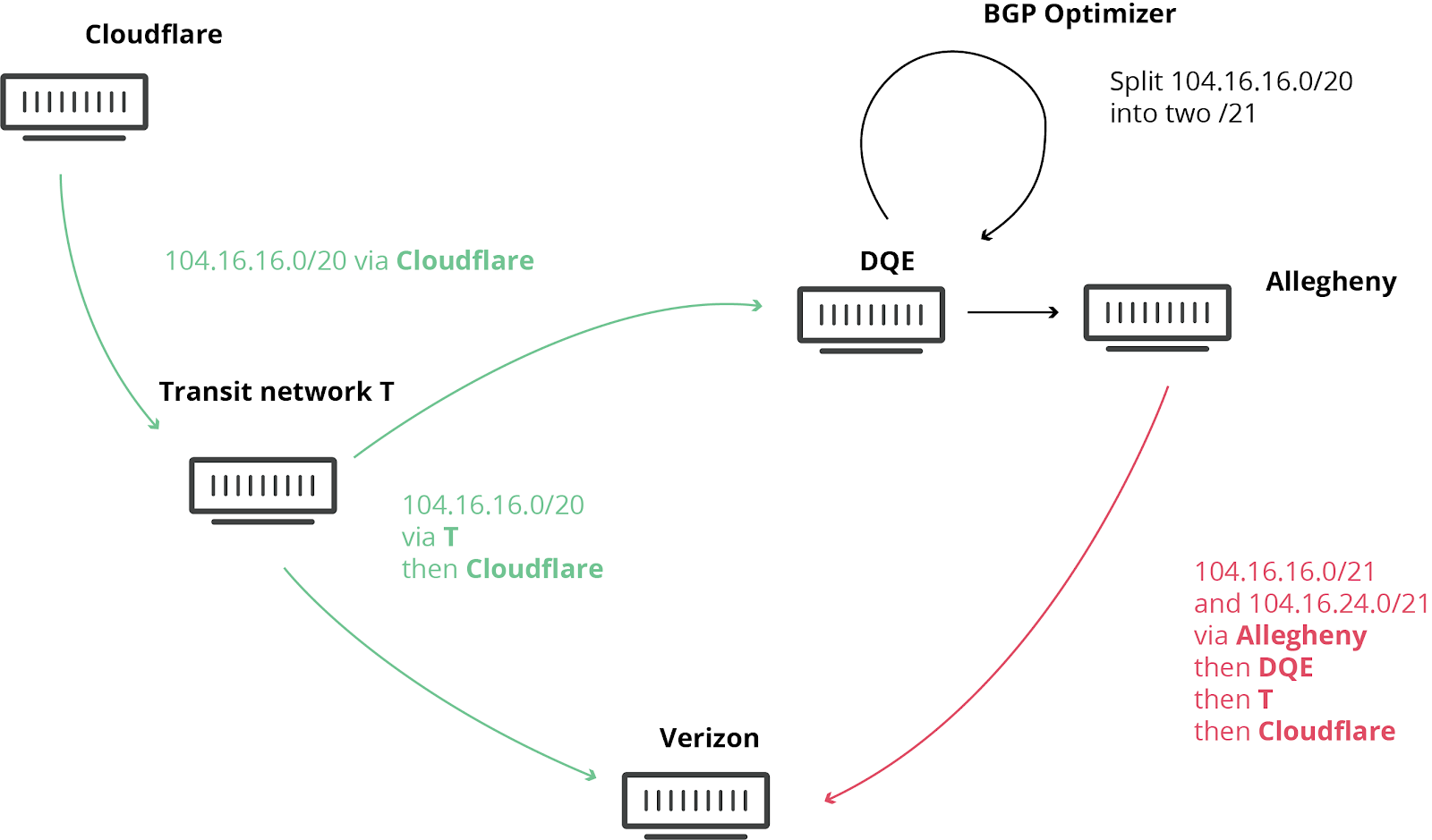
Published: 2019-06-25 04:51:52
Popularity: None
Author: None
Today at 10:30UTC, the Internet had a small heart attack. A small company in Northern Pennsylvania became a preferred path of many Internet routes through Verizon (AS701), a major Internet transit provider.
...moreAnnouncing AMP Real URL

Published: 2019-04-17 00:45:00
Popularity: 630
Author: Zack Bloom
Keywords:
The promise of the AMP (Accelerated Mobile Pages) project was that it would make the web, and, in particular, the mobile web, much more pleasant to surf. The AMP HTML framework was designed to make web pages load quickly.
...moreGo interfaces make test stubbing easy

Published: 2019-03-08 00:40:20
Popularity: None
Author: None
🤖: "Interface ease 🤩💻"
Go's "object-orientation" approach is through interfaces. Interfaces provide a way of specifying the behavior expected of an object, but rather than saying what an object itself can do, they specify what's expected of an object.
...moreKeyless SSL: The Nitty Gritty Technical Details

Published: 2019-03-08 00:33:31
Popularity: None
Author: None
🤖: "HTTPS fail"
We announced Keyless SSL yesterday to an overwhelmingly positive response. We read through the comments on this blog, Reddit, Hacker News, and people seem interested in knowing more and getting deeper into the technical details.
...moreWhy it’s harder to forge a SHA-1 certificate than it is to find a SHA-1 collision
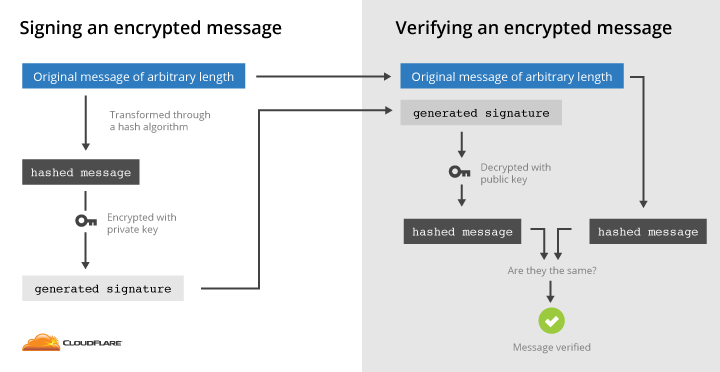
Published: 2019-03-08 00:00:59
Popularity: None
Author: None
It’s well known that SHA-1 is no longer considered a secure cryptographic hash function. Researchers now believe that finding a hash collision (two values that result in the same value when SHA-1 is applied) is inevitable and likely to happen.
...moreIntroducing the p0f BPF compiler

Published: 2019-03-07 23:41:56
Popularity: None
Author: None
Two years ago we blogged about our love of BPF (BSD packet filter) bytecode. Today we are very happy to open source another component of the bpftools: our p0f BPF compiler!
...moreA container identity bootstrapping tool

Published: 2019-03-07 22:58:37
Popularity: None
Author: None
Everybody has secrets. Software developers have many. Often these secrets—API tokens, TLS private keys, database passwords, SSH keys, and other sensitive data—are needed to make a service run properly and interact securely with other services.
...moreSIDH in Go for quantum-resistant TLS 1.3
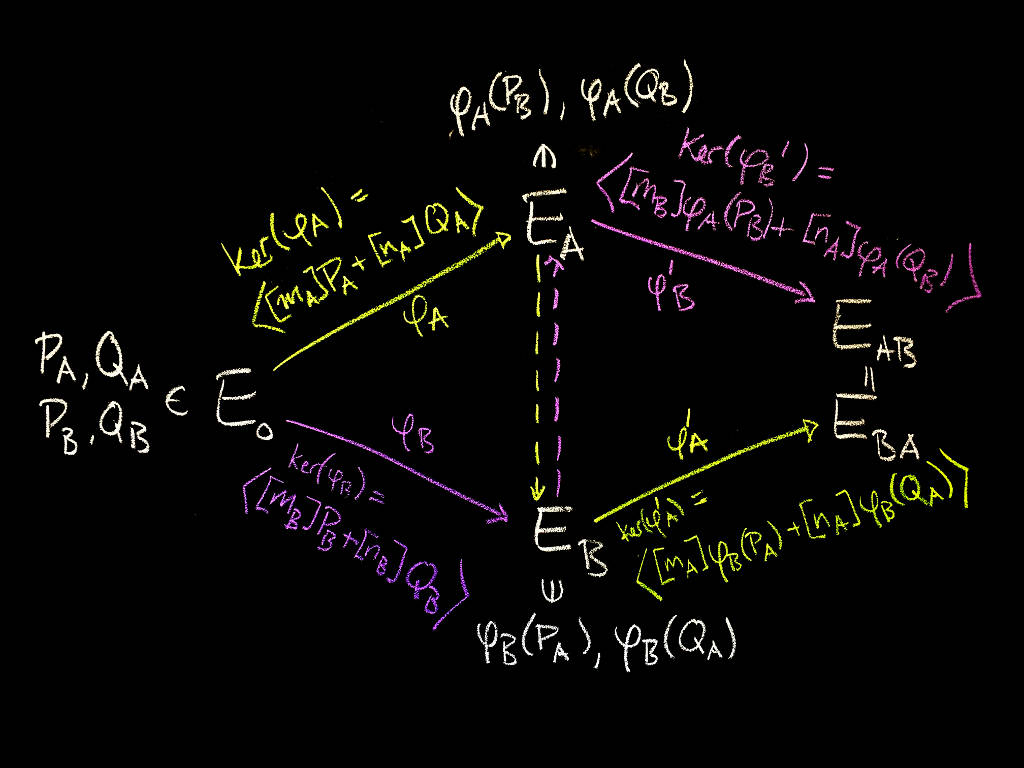
Published: 2019-03-07 22:52:44
Popularity: None
Author: None
Most of today's cryptography is designed to be secure against an adversary with enormous amounts of computational power. This means estimating how much work certain computations require, and choosing cryptographic parameters based on our best estimates.
...moreAnnouncing 1.1.1.1: the fastest, privacy-first consumer DNS service
Published: 2019-03-07 22:26:34
Popularity: None
Author: None
Cloudflare's mission is to help build a better Internet. We're excited today to take another step toward that mission with the launch of 1.1.1.1 — the Internet's fastest, privacy-first consumer DNS service. This post will talk a little about what that is and a lot about why we decided to do it.
...moreBGP leaks and cryptocurrencies

Published: 2019-03-07 22:24:15
Popularity: None
Author: None
Over the few last hours, a dozen news stories have broken about how an attacker attempted (and perhaps managed) to steal cryptocurrencies using a BGP leak.
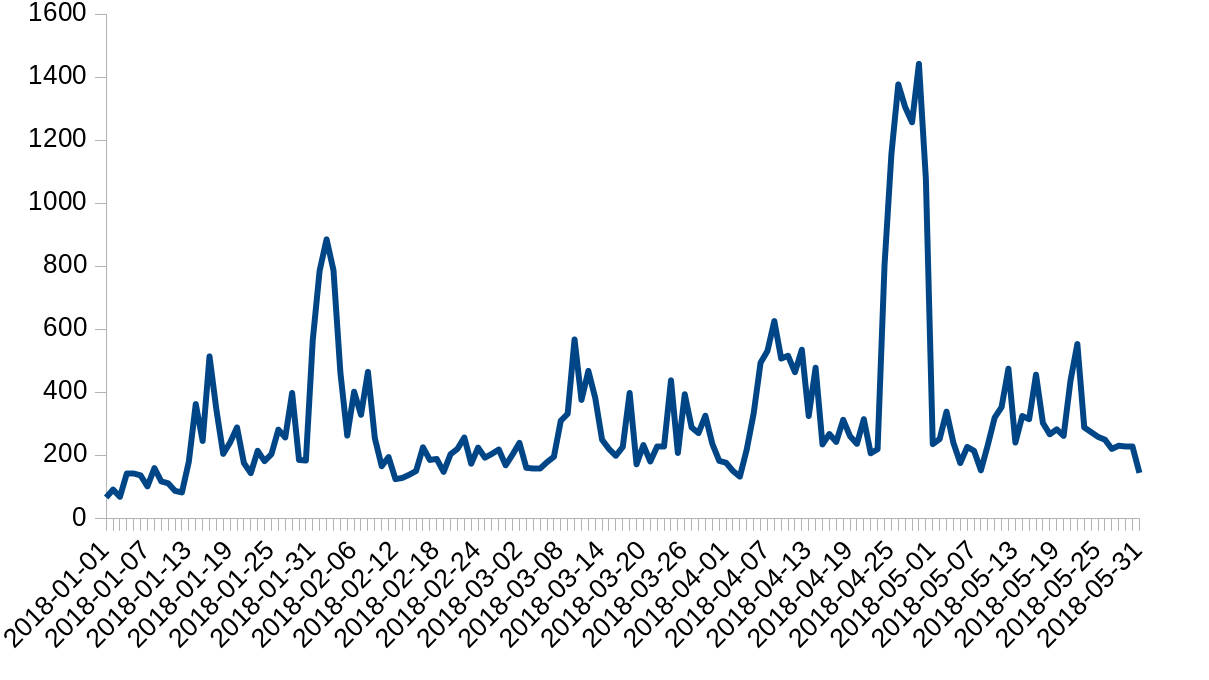
...moreToday we mitigated 1.1.1.1
Published: 2019-03-07 22:19:57
Popularity: None
Author: None
Cloudflare is protected from attacks by the Gatebot DDoS mitigation pipeline. Gatebot performs hundreds of mitigations a day, shielding our infrastructure and our customers from L3 and L7 attacks.
...moreIntroducing DNS Resolver for Tor

Published: 2019-03-07 22:19:19
Popularity: None
Author: None
As was mentioned in the original 1.1.1.1 blog post, our policy is to never write client IP addresses to disk and wipe all logs within 24 hours. Still some folks might not want to reveal their IP address to the resolver at all. This is why we are launching a Tor hidden service for our resolver.
...moreRPKI - The required cryptographic upgrade to BGP routing

Published: 2019-03-07 22:10:42
Popularity: None
Author: None
We have talked about the BGP Internet routing protocol before. We have talked about how we build a more resilient network and how we can see outages at a country-level via BGP. We have even talked about the network community that is vital to the operation of the global Internet.
...moreIntroducing the Cloudflare Onion Service

Published: 2019-03-07 22:10:04
Popularity: None
Author: None
Two years ago this week Cloudflare introduced Opportunistic Encryption, a feature that provided additional security and performance benefits to websites that had not yet moved to HTTPS.
...moreRoughtime: Securing Time with Digital Signatures

Published: 2019-03-07 22:08:39
Popularity: None
Author: None
When you visit a secure website, it offers you a TLS certificate that asserts its identity. Every certificate has an expiration date, and when it’s passed due, it is no longer valid.
...more