Researchers detail GoFetch, a new side-channel attack impacting Apple CPUs that could allow an attacker to obtain secret keys. The post New ‘GoFetch’ Apple CPU Attack Exposes Crypto Keys appeared first on SecurityWeek.
...moreSummary
Total Articles Found: 131
Top sources:
- SecurityWeek 131
Top Keywords:
- NEWS & INDUSTRY: 117
- Vulnerabilities: 92
- Endpoint Security: 27
- Application Security: 21
- Cloud Security: 21
Top Authors
- Ionut Arghire: 54
- Eduard Kovacs: 46
- Ryan Naraine: 14
- Associated Press: 5
- AFP: 4
Top Articles:
- Report: TikTok Harvested MAC Addresses By Exploiting Android Loophole
- Cisco Finds Serious Flaws in Sierra Wireless AirLink Devices
- Chinese Researchers Show How They Remotely Hacked a Mercedes-Benz
- Researchers Find Exploitable Bugs in Mercedes-Benz Cars
- North Korean .Gov Hackers Back With Fake Pen-Test Company
- Researchers Disclose Another SIM Card Attack Possibly Impacting Millions
- Critical Flaw in VMware Workstation, Fusion Allows Code Execution on Host From Guest
- Apple Adds 'BlastDoor' to Secure iPhones From Zero-Click Attacks
- Facebook to Cut off Huawei to Comply With U.S. Sanctions
- Global Espionage Campaign Used Software Supply Chain Hack To Compromise Targets, Including US Gov
New ‘GoFetch’ Apple CPU Attack Exposes Crypto Keys

Published: 2024-03-22 10:42:36
Popularity: 16
Author: Eduard Kovacs
Keywords:
Tor Code Audit Finds 17 Vulnerabilities

Published: 2024-01-31 12:51:52
Popularity: 20
Author: Eduard Kovacs
Keywords:
Over a dozen vulnerabilities discovered in Tor audit, including a high-risk flaw that can be exploited to inject arbitrary bridges. The post Tor Code Audit Finds 17 Vulnerabilities appeared first on SecurityWeek.
...moreNew ‘SpectralBlur’ macOS Backdoor Linked to North Korea

Published: 2024-01-05 13:14:01
Popularity: 15
Author: Ionut Arghire
Keywords:
SpectralBlur is a new macOS backdoor that shows similarities with North Korean hacking group’s KandyKorn malware. The post New ‘SpectralBlur’ macOS Backdoor Linked to North Korea appeared first on SecurityWeek.
...moreSEC Charges SolarWinds and Its CISO With Fraud and Cybersecurity Failures

Published: 2023-10-31 14:51:41
Popularity: None
Author: Mike Lennon
The SEC filed charges against SolarWinds and its CISO over misleading investors about its cybersecurity practices and known risks.
...moreHackers Earn $400k on First Day at Pwn2Own Toronto 2023

Published: 2023-10-25 15:49:59
Popularity: 14
Author: Ionut Arghire
Keywords:
NAS devices, printers, IP cameras, speakers, and mobile phones were hacked on the first day at Pwn2Own Toronto 2023. The post Hackers Earn $400k on First Day at Pwn2Own Toronto 2023 appeared first on SecurityWeek.
...moreMicrosoft Shares Resources for BlackLotus UEFI Bootkit Hunting

Published: 2023-04-13 10:21:34
Popularity: 9
Author: Ionut Arghire
Keywords:
Microsoft has shared details on how threat hunters can check their systems for BlackLotus UEFI bootkit infections. The post Microsoft Shares Resources for BlackLotus UEFI Bootkit Hunting appeared first on SecurityWeek.
...moreAndroid Security Update Patches Kernel Vulnerability Exploited by Spyware Vendor

Published: 2023-05-05 08:33:00
Popularity: 10
Author: Eduard Kovacs
Keywords:
Google’s latest Android security updates patch over 40 vulnerabilities, including CVE-2023-0266, a kernel flaw exploited as a zero-day by a spyware vendor. The post Android Security Update Patches Kernel Vulnerability Exploited by Spyware Vendor appeared first on SecurityWeek.
...moreSolarWinds Announces Upcoming Patches for High-Severity Vulnerabilities

Published: 2023-02-17 12:58:13
Popularity: 15
Author: Ionut Arghire
Keywords:
SolarWinds advisories describe multiple high-severity vulnerabilities that a Platform update will patch by the end of February. The post SolarWinds Announces Upcoming Patches for High-Severity Vulnerabilities appeared first on SecurityWeek.
...moreMalware Delivered to PyTorch Users in Supply Chain Attack

Published: 2023-01-03 12:50:38
Popularity: 14
Author: Ionut Arghire
Keywords:
Last week’s nightly builds of the open source machine learning framework PyTorch were injected with malware following a supply chain attack. Now part of the Linux Foundation umbrella, PyTorch is based on the Torch library and is used for applications in computer vision and natural language processing fields. read more
...moreNIST to Retire 27-Year-Old SHA-1 Cryptographic Algorithm

Published: 2022-12-16 15:19:08
Popularity: 14
Author: Ionut Arghire
Keywords:
The US National Institute of Standards and Technology (NIST) this week recommended that IT professionals replace the SHA-1 cryptographic algorithm with newer, more secure ones. read more
...moreEarSpy: Spying on Phone Calls via Ear Speaker Vibrations Captured by Accelerometer
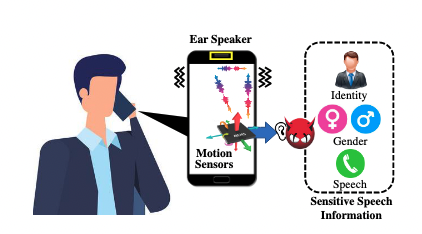
Published: 2022-12-28 11:09:56
Popularity: 47
Author: Eduard Kovacs
Keywords:
As smartphone manufacturers are improving the ear speakers in their devices, it can become easier for malicious actors to leverage a particular side-channel for eavesdropping on a targeted user’s conversations, according to a team of researchers from several universities in the United States. read more
...moreCritical Vulnerability in Premium Gift Cards WordPress Plugin Exploited in Attacks

Published: 2022-12-27 10:10:33
Popularity: 22
Author: Ionut Arghire
Keywords:
Defiant’s Wordfence team warns of a critical-severity vulnerability in the YITH WooCommerce Gift Cards premium WordPress plugin being exploited in attacks. read more
...moreNearly 300 Vulnerabilities Patched in Huawei's HarmonyOS in 2022

Published: 2023-01-03 11:39:44
Popularity: 11
Author: Eduard Kovacs
Keywords:
Chinese tech giant Huawei patched nearly 300 vulnerabilities in its HarmonyOS operating system in 2022. read more
...moreRackspace Hit With Lawsuits Over Ransomware Attack

Published: 2022-12-12 12:21:29
Popularity: 12
Author: Eduard Kovacs
Keywords:
At least two lawsuits have been filed against Texas-based cloud company Rackspace over the recently disclosed ransomware attack. read more
...morePython, JavaScript Developers Targeted With Fake Packages Delivering Ransomware

Published: 2022-12-12 12:46:57
Popularity: 10
Author: Ionut Arghire
Keywords:
Phylum security researchers warn of a new software supply chain attack relying on typosquatting to target Python and JavaScript developers. read more
...moreVulnerability in Acer Laptops Allows Attackers to Disable Secure Boot

Published: 2022-11-29 12:36:28
Popularity: 12
Author: Ionut Arghire
Keywords:
🤖: ""Boot fail""
A vulnerability impacting multiple Acer laptop models could allow an attacker to disable the Secure Boot feature and bypass security protections to install malware. read more
...moreGoogle Patches Eighth Chrome Zero-Day of 2022

Published: 2022-11-28 10:31:25
Popularity: 10
Author: Ionut Arghire
Keywords:
🤖: ""Chrome crashed again""
An emergency Chrome update that Google announced on Thanksgiving Day addresses an actively exploited zero-day in the popular browser. read more
...morePoC Code Published for High-Severity macOS Sandbox Escape Vulnerability

Published: 2022-11-21 12:47:17
Popularity: 12
Author: Ionut Arghire
Keywords:
🤖: "Buggy mac"
A security researcher has published details and proof-of-concept (PoC) code for a macOS vulnerability that could be exploited to escape a sandbox and execute code within Terminal. read more
...moreChrome 106 Update Patches Several High-Severity Vulnerabilities

Published: 2022-10-12 12:45:08
Popularity: 7
Author: Ionut Arghire
Keywords:
🤖: "bug hunt alert"
Google announced on Tuesday that the latest Chrome update patches six high-severity vulnerabilities, including four use-after-free bugs. All the newly resolved vulnerabilities were discovered by external researchers and the internet giant has handed out $38,000 in bug bounty rewards to the reporters. read more
...moreGoogle Unveils KataOS 'Verifiably-Secure' Operating System for Embedded Devices

Published: 2022-10-19 10:18:02
Popularity: 14
Author: Eduard Kovacs
Keywords:
Google last week unveiled a new project focused on building a secure embedded platform for machine learning (ML) applications. The project’s goal is designing intelligent ambient ML systems that are secure and trustworthy. read more
...moreWordPress Security Update 6.0.3 Patches 16 Vulnerabilities

Published: 2022-10-19 11:31:39
Popularity: 16
Author: Eduard Kovacs
Keywords:
WordPress 6.0.3 started rolling out this week. The latest security release patches 16 vulnerabilities. read more
...moreUS Gov Issues Supply Chain Security Guidance for Software Suppliers

Published: 2022-11-01 11:47:41
Popularity: 13
Author: Ionut Arghire
Keywords:
The Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Office of the Director of National Intelligence (ODNI) this week released the second part of a three-part joint guidance on securing the software supply chain. read more
...moreNew 'Wolfi' Linux Distro Focuses on Software Supply Chain Security

Published: 2022-09-23 14:11:20
Popularity: 7
Author: Ionut Arghire
Keywords:
🤖: ""Linux lockdown""
Chainguard this week announced Wolfi, a stripped-down Linux OS distribution designed to improve the security of the software supply chain. read more
...moreWordPress Sites Hacked via Zero-Day Vulnerability in WPGateway Plugin

Published: 2022-09-14 13:49:39
Popularity: 7
Author: Ionut Arghire
Keywords:
🤖: "Zero day hack"
Many WordPress sites are at risk of full compromise as attackers are actively exploiting a zero-day vulnerability in the WPGateway plugin, Defiant’s WordFence team warns. A premium plugin for the WPGateway cloud service, the WPGateway plugin provides users with WordPress installation, backup, and cloning capabilities. read more
...moreWordPress 6.0.2 Patches Vulnerability That Could Impact Millions of Legacy Sites

Published: 2022-08-31 11:39:06
Popularity: 13
Author: Ionut Arghire
Keywords:
The WordPress team this week announced the release of version 6.0.2 of the content management system (CMS), with patches for three security bugs, including a high-severity SQL injection vulnerability. read more
...more'DirtyCred' Vulnerability Haunting Linux Kernel for 8 Years

Published: 2022-08-23 12:35:00
Popularity: 9
Author: Ionut Arghire
Keywords:
🤖: "buggy kernel"
Academic researchers from Northwestern University have shared details on ‘DirtyCred’, a previously unknown privilege escalation vulnerability affecting the Linux kernel. read more
...moreSecurity Firm Discloses CrowdStrike Issue After 'Ridiculous Disclosure Process'

Published: 2022-08-23 11:29:19
Popularity: 27
Author: Eduard Kovacs
Keywords:
🤖: "Cyber Oops"
A security firm has disclosed the details of an issue affecting a CrowdStrike product after what it described as a ‘ridiculous vulnerability disclosure process’. CrowdStrike has provided some clarifications following the disclosure. read more
...moreGoogle Open Sources 'Paranoid' Crypto Testing Library

Published: 2022-08-25 13:45:51
Popularity: 8
Author: Ionut Arghire
Keywords:
🤖: "Crypto fails"
Google has officially announced the open sourcing of ‘Paranoid’, a project for identifying well-known weaknesses in cryptographic artifacts. read more
...moreSecure Boot Bypass Flaws Affect Bootloaders of Many Devices Made in Past Decade
Published: 2022-08-15 13:30:49
Popularity: 8
Author: Eduard Kovacs
Keywords:
🤖: "Bootjacked"
Bootloaders present in a majority of computers made in the past 10 years are affected by Secure Boot bypass vulnerabilities, according to firmware security company Eclypsium. read more
...moreBlack Hat USA 2022 - Announcements Summary

Published: 2022-08-12 10:23:58
Popularity: 11
Author: Eduard Kovacs
Keywords:
Hundreds of companies and organizations showcased their products and services this week at the 2022 edition of the Black Hat conference in Las Vegas. read more
...moreGoogle Patches Critical Android Flaw Allowing Remote Code Execution via Bluetooth

Published: 2022-08-02 10:30:19
Popularity: 14
Author: Eduard Kovacs
Keywords:
Google on Monday published a security bulletin describing the latest round of patches for the Android operating system. Three dozen vulnerabilities have been fixed, including a critical issue that can be exploited for remote code execution over Bluetooth. read more
...moreLenovo Patches UEFI Code Execution Vulnerability Affecting Many Laptops

Published: 2022-07-13 20:02:47
Popularity: 19
Author: Eduard Kovacs
Keywords:
🤖: ""UEFI bugger""
Lenovo has released a security advisory to inform customers that more than 70 of its laptops are affected by a UEFI/BIOS vulnerability that can lead to arbitrary code execution. read more
...moreMicrosoft Confirms Temporary Rollback of Macro Blocking Feature

Published: 2022-07-11 17:50:26
Popularity: 10
Author: Ionut Arghire
Keywords:
Microsoft has confirmed that the recent rollback of a feature related to the blocking of internet macros in its Office suite is only temporary. read more
...moreActing as Own Lawyer, Accused CIA Coder Argues for Acquittal

Published: 2022-07-08 06:26:58
Popularity: 4
Author: Associated Press
Keywords:
A former CIA software engineer accused of causing the biggest theft of classified information in CIA history told a jury Thursday that there’s not enough evidence to convict him of espionage and other federal charges. read more
...moreNew Database Catalogs Cloud Vulnerabilities, Security Issues
Published: 2022-06-28 13:01:05
Popularity: 12
Author: Eduard Kovacs
Keywords:
Cloud security company Wiz has announced the launch of a new database whose goal is to keep track of vulnerabilities and other security issues affecting cloud services. read more
...moreA Year After Death, McAfee's Corpse Still in Spanish Morgue

Published: 2022-06-23 18:22:23
Popularity: 18
Author: AFP
Keywords:
The body of software entrepreneur John McAfee remained at a morgue in Spain Thursday a year after his death as a legal case filed by his family, who do not believe he committed suicide, is yet to be resolved. read more
...moreGoogle Patches 14 Vulnerabilities With Release of Chrome 103

Published: 2022-06-22 12:10:20
Popularity: 14
Author: Ionut Arghire
Keywords:
Google this week announced the release of Chrome 103 to the stable channel with patches for a total of 14 vulnerabilities, including nine reported by external researchers. The most severe of these bugs is CVE-2022-2156, which is described as a critical-severity use-after-free issue in Base. read more
...moreExploited Vulnerability Patched in WordPress Plugin With Over 1 Million Installations

Published: 2022-06-17 12:00:51
Popularity: 13
Author: Ionut Arghire
Keywords:
More than one million WordPress websites were potentially impacted by a critical Ninja Forms plugin vulnerability that appears to have been exploited in the wild. With over one million installations, the popular Ninja Forms plugin helps administrators add customizable forms to their WordPress sites. read more
...moreReport: L3 Emerges as Suitor for Embattled NSO Group

Published: 2022-06-14 16:18:52
Popularity: 9
Author: Ryan Naraine
Keywords:
🤖: "Spy game 😏"
L3 Technologies, a U.S. government contractor that sells aerospace and defense technology, has emerged as a suitor for Israeli exploit merchant NSO Group. read more
...moreMillions of Budget Smartphones With UNISOC Chips Vulnerable to Remote DoS Attacks

Published: 2022-06-02 15:00:17
Popularity: 10
Author: Eduard Kovacs
Keywords:
🤖: ""bugged phones""
Millions of budget smartphones that use UNISOC chipsets could have their communications remotely disrupted by hackers due to a critical vulnerability discovered recently by researchers at cybersecurity firm Check Point. read more
...moreResearchers Spot Supply Chain Attack Targeting GitLab CI Pipelines

Published: 2022-05-19 17:35:51
Popularity: 13
Author: Ryan Naraine
Keywords:
Security researchers at SentinelLabs are calling attention to a software chain supply attack targeting Rust developers with malware aimed directly at infecting GitLab Continuous Integration (CI) pipelines. read more
...moreGoogle Discloses Details of Zoom Zero-Click Remote Code Execution Exploit

Published: 2022-05-25 10:37:49
Popularity: 12
Author: Eduard Kovacs
Keywords:
Google’s Project Zero has disclosed the details of a zero-click remote code execution exploit targeting the Zoom video conferencing software. read more
...moreNVIDIA Patches Code Execution Vulnerabilities in Graphics Driver

Published: 2022-05-18 10:21:17
Popularity: 18
Author: Ionut Arghire
Keywords:
🤖: ""Crashing graphics""
NVIDIA has announced the roll-out of updates for its graphics drivers to address multiple vulnerabilities, including four CVEs rated “high severity.” read more
...moreLarge-Scale Attack Targeting Tatsu Builder WordPress Plugin

Published: 2022-05-18 08:38:10
Popularity: 29
Author: Ionut Arghire
Keywords:
🤖: "Security breach!"
Tens of thousands of WordPress websites are potentially at risk of compromise as part of an ongoing large-scale attack targeting a remote code execution vulnerability in the Tatsu Builder plugin. read more
...moreChrome 101 Update Patches High-Severity Vulnerabilities

Published: 2022-05-11 15:37:18
Popularity: 11
Author: Ionut Arghire
Keywords:
🤖: "Browser crisis!"
Google this week announced the release of a Chrome browser update that resolves a total of 13 vulnerabilities, including nine that were reported by external researchers. Of the externally reported security holes, seven are use-after-free bugs – these types of vulnerabilities could lead to arbitrary code execution. read more
...moreChrome 101 Patches 30 Vulnerabilities

Published: 2022-04-27 11:15:49
Popularity: 16
Author: Ionut Arghire
Keywords:
Google this week announced that Chrome 101 was released to the stable channel with 30 security fixes inside, including 25 for vulnerabilities identified by external security researchers. read more
...moreOracle Releases 520 New Security Patches With April 2022 CPU

Published: 2022-04-20 09:57:39
Popularity: 14
Author: Ionut Arghire
Keywords:
🤖: "Patching frenzy"
Oracle on Tuesday announced the release of 520 security fixes as part of its April 2022 Critical Patch Update (CPU), including nearly 300 for vulnerabilities that can be exploited remotely without authentication. read more
...moreFirmware Flaws Allow Disabling Secure Boot on Lenovo Laptops

Published: 2022-04-19 18:46:07
Popularity: 14
Author: Ionut Arghire
Keywords:
🤖: "Boot fail"
Computer maker Lenovo has started pushing security patches to address three vulnerabilities impacting the UEFI firmware of more than 110 laptop models. read more
...moreAdobe Patches Gaping Security Holes in Acrobat, Reader, Photoshop

Published: 2022-04-12 17:36:50
Popularity: 21
Author: Ryan Naraine
Keywords:
🤖: "security alert"
Adobe's security update engine revved into overdrive this month with the release of patches for at least 78 documented software vulnerabilities, some serious enough to expose corporate customers to remote code execution attacks. read more
...moreAcademics Devise Side-Channel Attack Targeting Multi-GPU Systems

Published: 2022-04-05 10:22:14
Popularity: 8
Author: Ionut Arghire
Keywords:
A group of academic researchers has devised a side-channel attack targeting architectures that rely on multiple graphics processing units (GPUs) for resource-intensive computational operations. read more
...moreResearchers Hack Remote Keyless System of Honda Vehicles

Published: 2022-03-28 19:28:47
Popularity: 15
Author: Ionut Arghire
Keywords:
🤖: "Car hacked!"
A researcher has published proof-of-concept (PoC) videos to demonstrate how an attacker can remotely unlock the doors of a Honda vehicle, or even start its engine. read more
...moreSonicWall Patches Critical Vulnerability in Firewall Appliances

Published: 2022-03-29 10:36:10
Popularity: 16
Author: Ionut Arghire
Keywords:
SonicWall has released patches for a critical-severity vulnerability in the web management interface of multiple firewall appliances. Tracked as CVE-2022-22274 (CVSS score of 9.4), the security flaw is described as a stack-based buffer overflow bug that impacts SonicOS. read more
...moreSoftware Supply Chain Weakness: Snyk Warns of 'Deliberate Sabotage' of NPM Ecosystem

Published: 2022-03-17 15:58:58
Popularity: 20
Author: Ryan Naraine
Keywords:
Software supply chain security fears escalated again this week with the discovery of what’s being described as "deliberate sabotage" of code in the open-source npm package manager ecosystem. read more
...moreGoogle Issues Emergency Fix for Chrome Zero-Day

Published: 2022-03-27 11:58:30
Popularity: 55
Author: Ionut Arghire
Keywords:
Google has issued an emergency security update for Chrome 99 to resolve a vulnerability for which a public exploit already exists. read more
...moreHigh-Severity UEFI Vulnerabilities Patched in Dell Enterprise Laptops

Published: 2022-03-22 11:51:19
Popularity: 7
Author: Ionut Arghire
Keywords:
🤖: "Firmware fail!"
Firmware security company Binarly this week disclosed the details of several vulnerabilities that impact the Unified Extensible Firmware Interface (UEFI) of multiple Dell enterprise laptop models. read more
...moreNew Variant of Spectre Attack Bypasses Intel and Arm Hardware Mitigations

Published: 2022-03-10 11:55:14
Popularity: 18
Author: Eduard Kovacs
Keywords:
🤖: ""Spectre strikes again""
A team of researchers from the Vrije Universiteit Amsterdam in the Netherlands has demonstrated a new Spectre attack variant that can bypass hardware mitigations implemented in recent years by Intel and Arm. read more
...moreAdobe Releases Emergency Patch for Exploited Commerce Zero-Day

Published: 2022-02-13 18:01:12
Popularity: 15
Author: Eduard Kovacs
Keywords:
Adobe released an emergency advisory on Sunday to inform Commerce and Magento users of a critical zero-day vulnerability that has been exploited in attacks. read more
...moreGoogle Patches 27 Vulnerabilities With Release of Chrome 98

Published: 2022-02-02 09:50:47
Popularity: 19
Author: Ionut Arghire
Keywords:
🤖: "Chrome patch party 🎉💻"
Google on Tuesday announced the release of Chrome 98 in the stable channel with a total of 27 security fixes inside, including 19 for vulnerabilities reported by external researchers. The most severe of these security defects could be exploited to execute arbitrary code with the same privileges as the Chrome browser has on the target system. read more
...moreXerox Quietly Patched Device-Bricking Flaw Affecting Some Printers

Published: 2022-01-28 11:41:48
Popularity: 20
Author: Ionut Arghire
Keywords:
Xerox patched a device-bricking vulnerability in certain printer models more than a year and a half ago, but said nothing until this week, when information on the bug became public. read more
...moreCritical SAP Vulnerability Allows Supply Chain Attacks

Published: 2022-01-17 13:13:42
Popularity: 15
Author: Ionut Arghire
Keywords:
🤖: ""sap hacked""
A critical vulnerability addressed recently in SAP NetWeaver AS ABAP and ABAP Platform could be abused to set up supply chain attacks, SAP security solutions provider SecurityBridge warns. read more
...moreNew Flaws Expose EVlink Electric Vehicle Charging Stations to Remote Hacking

Published: 2021-12-27 11:33:20
Popularity: 10
Author: Eduard Kovacs
Keywords:
🤖: ""Charging hacked""
Schneider Electric has patched several new vulnerabilities that expose its EVlink electric vehicle charging stations to remote hacker attacks. read more
...moreProject Zero Flags High-Risk Zoom Security Flaw

Published: 2021-11-29 19:03:13
Popularity: 23
Author: Ryan Naraine
Keywords:
Video conferencing software giant Zoom has shipped patches for a pair of security defects that expose Windows, macOS, Linux, iOS and Android users to malicious hacker attacks. read more
...moreGitHub Confirms Another Major NPM Security Defect

Published: 2021-11-16 16:39:16
Popularity: 15
Author: Ryan Naraine
Keywords:
Microsoft-owned GitHub is again flagging major security problems in the npm registry, warning that a pair of newly discovered vulnerabilities continue to expose the soft underbelly of the open-source software supply chain. read more
...moreBlacksmith: Rowhammer Fuzzer Bypasses Existing Protections

Published: 2021-11-16 20:07:55
Popularity: 4
Author: Ionut Arghire
Keywords:
🤖: "Hammer time crashes"
A group of security researchers devised a new attack that completely bypasses the existing mitigations against the Rowhammer vulnerability in dynamic random-access memory (DRAM) chips. read more
...moreShrootless: macOS Vulnerability Found by Microsoft Allows Rootkit Installation

Published: 2021-10-29 13:28:08
Popularity: 9
Author: Ionut Arghire
Keywords:
🤖: "Rootkit alert!"
Microsoft on Thursday published information on a vulnerability in Apple’s macOS platform that could allow an attacker to bypass System Integrity Protection (SIP) and modify operating system files. read more
...moreResearchers Disclose New Side-Channel Attacks Affecting All AMD CPUs
Published: 2021-10-15 11:07:26
Popularity: 18
Author: Eduard Kovacs
Keywords:
Researchers have disclosed the details of new timing and power-based side-channel attacks that affect all CPUs made by AMD, but the chipmaker says no new mitigations are necessary. read more
...moreYubico Enables Biometric Logins With New YubiKey Bio Series
Published: 2021-10-06 14:14:31
Popularity: 8
Author: Ionut Arghire
Keywords:
Yubico this week announced the general availability of YubiKey Bio Series, its first security key to support biometric authentication on desktop computers. read more
...moreEncrypted Messaging App Signal Hit by Brief Outage
Published: 2021-09-27 10:39:58
Popularity: 7
Author: AFP
Keywords:
Encrypted instant messaging app Signal was hit by a brief outage late Sunday that interrupted services on the platform at the same time as localised interruptions on other social media services. read more
...moreAkamai to Acquire Guardicore in $600M Zero Trust Tech Deal
Published: 2021-09-29 17:03:38
Popularity: 5
Author: Ryan Naraine
Keywords:
Edge security and content delivery giant Akamai Technologies on Wednesday announced plans to spend $600 million to acquire Guardicore, an Israeli micro-segmentation technology startup. Akamai said the deal would add new capabilities to help customers thwart ransomware attacks by blocking the spread of malware within an already-compromised enterprise. read more
...moreApple Confirms New Zero-Day Attacks on Older iPhones
Published: 2021-09-23 20:39:09
Popularity: 8
Author: Ryan Naraine
Keywords:
Apple on Thursday confirmed a new zero-day exploit hitting older iPhones and warned that the security vulnerability also affects the macOS Catalina platform. read more
...moreAttacks Targeting OMIGOD Vulnerability Ramping Up
Published: 2021-09-21 03:45:05
Popularity: 13
Author: Ionut Arghire
Keywords:
Attackers are increasingly targeting a remote code execution vulnerability in the Open Management Infrastructure (OMI) framework that Microsoft released patches for earlier this month. read more
...moreGoogle Warns of Exploited Zero-Days in Chrome Browser

Published: 2021-09-13 21:51:32
Popularity: 29
Author: Ryan Naraine
Keywords:
🤖: "Zero Day Alert"
Google has joined the list of major software providers scrambling to respond to zero-day exploits in the wild. read more
...moreRecently Patched Confluence Vulnerability Exploited in the Wild
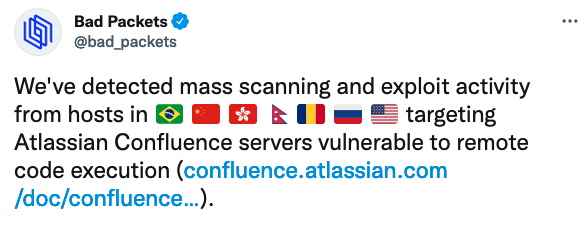
Published: 2021-09-02 10:47:16
Popularity: 7
Author: Eduard Kovacs
Keywords:
Hackers started exploiting a vulnerability in Atlassian’s Confluence enterprise collaboration product just one week after the availability of a patch was announced. read more
...moreAdobe Plugs Critical Photoshop Security Flaws

Published: 2021-08-17 23:14:52
Popularity: 12
Author: Ryan Naraine
Keywords:
🤖: "Photoshop fail"
Adobe has issued a warning for a pair of major security vulnerabilities affecting its popular Photoshop image manipulation software. The flaws, rated critical, expose both Windows and MacOS users to code execution attacks, Adobe said in an advisory released Tuesday. read more
...moreNew DNS Attack Enables 'Nation-State Level Spying' via Domain Registration
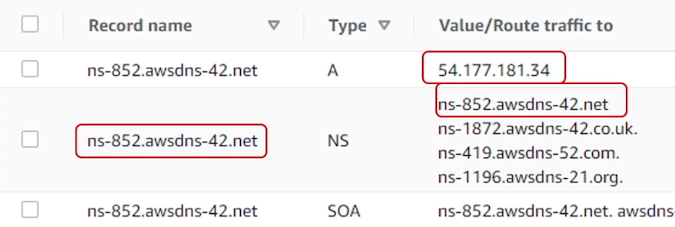
Published: 2021-08-06 15:08:13
Popularity: 14
Author: Eduard Kovacs
Keywords:
A new domain name system (DNS) attack method that involves registering a domain with a specific name can be leveraged for what researchers described as “nation-state level spying.” read more
...moreAdobe Patches 21 Vulnerabilities Across Seven Products

Published: 2021-07-21 10:03:49
Popularity: 13
Author: Eduard Kovacs
Keywords:
🤖: ""Patch party""
Security updates released by Adobe on Tuesday for seven of its products patch a total of 21 vulnerabilities, including 15 flaws that have been assigned a critical severity rating. read more
...moreAdobe: Critical Flaws in Reader, Acrobat, Illustrator

Published: 2021-07-13 15:08:49
Popularity: 40
Author: Ryan Naraine
Keywords:
🤖: "Crashing software"
Adobe has issued multiple security advisories with patches for critical vulnerabilities in a wide range of software products, including the ever-present Adobe Acrobat and Reader application. read more
...moreBiden Tells Putin Russia Must Crack Down on Cybercriminals

Published: 2021-07-10 16:22:11
Popularity: 13
Author: Associated Press
Keywords:
🤖: "Russian hackers busted"
President Joe Biden told Russian President Vladimir Putin in a Friday phone call that he must “take action” against cybercriminals acting in his country and that the U.S. reserves the right to “defend its people and its critical infrastructure” from future attacks, the White House said. read more
...moreAttacks Against Container Infrastructures Increasing, Including Supply Chain Attacks

Published: 2021-06-21 20:05:07
Popularity: 19
Author: Kevin Townsend
Keywords:
🤖: ""Container Chaos""
Research finds that adversaries could detect a new misconfigured container within an average of five hours read more
...moreGoogle Releases Open Source Tools and Libraries for Fully Homomorphic Encryption

Published: 2021-06-16 13:37:47
Popularity: 12
Author: Eduard Kovacs
Keywords:
🤖: "crypto secrets"
Google this week announced that it has released open source tools and libraries that can be used by developers to implement fully homomorphic encryption (FHE). read more
...moreGitHub Discloses Details of Easy-to-Exploit Linux Vulnerability

Published: 2021-06-11 13:09:45
Popularity: 12
Author: Eduard Kovacs
Keywords:
🤖: ""Linux pwned""
GitHub this week disclosed the details of an easy-to-exploit Linux vulnerability that can be leveraged to escalate privileges to root on the targeted system. The flaw, classified as high severity and tracked as CVE-2021-3560, impacts polkit, an authorization service that is present by default in many Linux distributions. read more
...moreVMware Urges Customers to Immediately Patch Critical vSphere Vulnerability

Published: 2021-05-26 14:29:30
Popularity: 9
Author: Eduard Kovacs
Keywords:
🤖: "patch party fail"
VMware has urged customers to immediately patch a critical vulnerability affecting vCenter Server, the management interface for vSphere environments. The vulnerability, tracked as CVE-2021-21985, was reported to VMware by Ricter Z of 360 Noah Lab and it has been patched in versions 6.5, 6.7 and 7.0 of vCenter Server. read more
...moreVulnerabilities in Visual Studio Code Extensions Expose Developers to Attacks

Published: 2021-05-27 14:09:48
Popularity: 10
Author: Ionut Arghire
Keywords:
🤖: ""Extension exploited""
Vulnerabilities in Visual Studio Code extensions could be exploited by malicious attackers to steal valuable information from developers and even compromise organizations, researchers with open-source software security firm Snyk say. read more
...moreResearchers Find Exploitable Bugs in Mercedes-Benz Cars

Published: 2021-05-18 20:24:37
Popularity: 93
Author: Ionut Arghire
Keywords:
🤖: "car hack"
Following an eight-month audit of the code in the latest infotainment system in Mercedes-Benz cars, security researchers with Tencent Security Keen Lab identified five vulnerabilities, four of which could be exploited for remote code execution. read more
...more$200,000 Awarded for Zero-Click Zoom Exploit at Pwn2Own

Published: 2021-04-08 11:13:54
Popularity: 47
Author: Eduard Kovacs
Keywords:
Two researchers earned $200,000 on the second day of the Pwn2Own 2021 hacking competition for a Zoom exploit allowing remote code execution without user interaction. read more
...moreNorth Korean .Gov Hackers Back With Fake Pen-Test Company

Published: 2021-03-31 20:57:11
Popularity: 78
Author: Ryan Naraine
Keywords:
A North Korean government-backed APT group has been caught using a fake pen-testing company and a range of sock puppet social media accounts in an escalation of a hacking campaign targeting security research professionals. read more
...morePolish State Websites Hacked and Used to Spread False Info

Published: 2021-03-18 09:46:58
Popularity: 49
Author: Associated Press
Keywords:
🤖: ""Hacked again""
Two Polish government websites were hacked Wednesday and used briefly to spread false information about a non-existent radioactive threat, in what a Polish government official said had the hallmarks of a Russian cyberattack. read more
...moreResearch Shows How Solar Energy Installations Can Be Abused by Hackers

Published: 2021-02-17 15:24:26
Popularity: 28
Author: Eduard Kovacs
Keywords:
Researchers at cybersecurity firm FireEye have analyzed a gateway device used for solar energy installations, and discovered vulnerabilities that could be useful to malicious hackers. read more
...moreAdobe Patches Reader Vulnerability Exploited in the Wild

Published: 2021-02-09 18:29:39
Popularity: 24
Author: Eduard Kovacs
Keywords:
Adobe on Tuesday announced the availability of patches for 50 vulnerabilities across six of its products, including a zero-day vulnerability in Reader that has been exploited in the wild. read more
...moreThree New Vulnerabilities Patched in OpenSSL

Published: 2021-02-17 09:31:00
Popularity: 36
Author: Eduard Kovacs
Keywords:
read more
...moreVulnerabilities in Realtek Wi-Fi Module Expose Many Devices to Remote Attacks

Published: 2021-02-04 13:21:18
Popularity: 24
Author: Ionut Arghire
Keywords:
Major vulnerabilities in the Realtek RTL8195A Wi-Fi module expose embedded devices used in a myriad of industries to remote attacks, researchers with automated device security platform provider Vdoo reveal. read more
...moreGoogle Patches Over a Dozen High-Severity Privilege Escalation Flaws in Android

Published: 2021-02-03 04:38:32
Popularity: 36
Author: Ionut Arghire
Keywords:
Google this week published its Android security bulletin for February 2021, which includes information on more than 40 vulnerabilities, most of which could lead to elevation of privilege. read more
...moreWeak ACLs in Adobe ColdFusion Allow Privilege Escalation

Published: 2021-02-03 12:59:51
Popularity: 36
Author: Ionut Arghire
Keywords:
A newly disclosed vulnerability in Adobe ColdFusion could be exploited by unprivileged users for the execution of arbitrary code with SYSTEM privileges. The popular commercial web-application development platform uses the CFML scripting language and is mainly used for the creation of data-driven websites. read more
...moreApple Issues Patches for NAT Slipstreaming 2.0 Attack

Published: 2021-02-02 11:26:42
Popularity: 42
Author: Ionut Arghire
Keywords:
Apple this week released security updates to address multiple vulnerabilities in macOS and Safari, including a flaw that can be exploited for the recently disclosed NAT Slipstreaming 2.0 attack. read more
...moreApple Adds 'BlastDoor' to Secure iPhones From Zero-Click Attacks

Published: 2021-01-28 20:31:16
Popularity: 70
Author: Ryan Naraine
Keywords:
Apple has quietly added several anti-exploit mitigations into its flagship mobile operating system in what appears to be a specific response to zero-click iMessage attacks observed in the wild. read more
...morePwn2Own 2021: Hackers Offered $200,000 for Zoom, Microsoft Teams Exploits

Published: 2021-01-27 09:49:45
Popularity: 54
Author: Eduard Kovacs
Keywords:
Trend Micro’s Zero Day Initiative (ZDI) on Tuesday announced the targets, prizes and rules for the Pwn2Own Vancouver 2021 hacking competition, a hybrid event scheduled to take place on April 6-8. read more
...moreReport: TikTok Harvested MAC Addresses By Exploiting Android Loophole

Published: 2021-01-14 16:21:03
Popularity: 287
Author: SecurityWeek News
Keywords:
The ongoing controversies surrounding TikTok hit a new gear on Thursday with a bombshell report accusing the Chinese company of spying on millions of Android users using a technique banned by Google. read more
...moreHardcoded Credentials Expose Zyxel Firewalls and WLAN Controllers to Remote Attacks

Published: 2021-01-04 15:12:42
Popularity: 24
Author: Ionut Arghire
Keywords:
🤖: "passwords out"
Several Zyxel firewall and WLAN controller products contain hardcoded credentials for an undocumented user account that has admin privileges. Identified by EYE security researcher Niels Teusink, the vulnerability exists because the password for the “zyfwp” user account was stored in plaintext and was visible in one of the binaries on the system. read more
...moreApple Loses Copyright Suit Against Security Startup
A federal judge Tuesday dismissed Apple's copyright infringement lawsuit against cybersecurity startup Corellium in a case which could have implications for researchers who find software bugs and vulnerabilities. read more
...moreGlobal Espionage Campaign Used Software Supply Chain Hack To Compromise Targets, Including US Gov
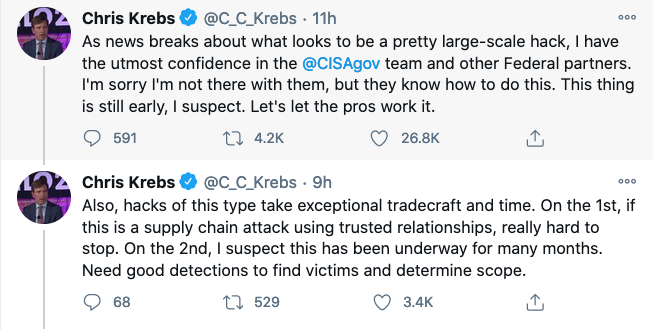
Published: 2020-12-14 12:02:05
Popularity: 64
Author: Mike Lennon
Keywords:
Tampered Versions of SolarWinds Orion IT Monitoring Software Used to Compromise Global Organizations read more
...moreVulnerabilities Expose Thousands of MobileIron Servers to Remote Attacks

Published: 2020-09-14 12:18:11
Popularity: 44
Author: Eduard Kovacs
Keywords:
Researchers have disclosed the details of several potentially serious vulnerabilities affecting MobileIron’s mobile device management (MDM) solutions, including a flaw that can be exploited by an unauthenticated attacker for remote code execution on affected servers. read more
...moreAdobe Patches Critical Code Execution Flaws in AEM, FrameMaker, InDesign

Published: 2020-09-08 18:07:19
Popularity: 24
Author: Eduard Kovacs
Keywords:
Adobe on Tuesday informed customers that it has patched a total of 18 vulnerabilities across its Experience Manager (AEM), FrameMaker and InDesign products. read more
...moreChinese Researchers Show How They Remotely Hacked a Mercedes-Benz

Published: 2020-08-07 19:11:40
Popularity: 100
Author: Eduard Kovacs
Keywords:
read more
...moreAMD Preparing Patches for UEFI SMM Vulnerability

Published: 2020-06-22 10:11:26
Popularity: 40
Author: Ionut Arghire
Keywords:
🤖: ""Firmware fix""
AMD last week said it was preparing patches for a vulnerability affecting the System Management Mode (SMM) of the Unified Extensible Firmware Interface (UEFI) shipped with systems that use certain notebook and embedded processors. read more
...moreMicrosoft Patches Critical Code Execution Vulnerabilities in Windows, Browsers

Published: 2020-06-10 03:32:35
Popularity: 29
Author: Eduard Kovacs
Keywords:
Microsoft’s security updates for June 2020 patch 129 vulnerabilities, including 11 critical remote code execution flaws affecting Windows, the Edge and Internet Explorer browsers, and SharePoint. read more
...more'SMBleed' Vulnerability Impacts Windows SMB Protocol

Published: 2020-06-10 17:46:48
Popularity: 36
Author: Ionut Arghire
Keywords:
One of the vulnerabilities that Microsoft addressed on June 2020 Patch Tuesday is a Server Message Block (SMB) protocol bug that could allow an attacker to leak kernel memory remotely, without authentication. read more
...moreCritical Flaw in SEO Plugin Exposed Many WordPress Sites to Attacks

Published: 2020-04-01 12:05:32
Popularity: 33
Author: Ionut Arghire
Keywords:
A critical vulnerability in the Rank Math SEO plugin for WordPress could allow attackers to lock administrators out of their own websites, WordPress security company Defiant reports. read more
...moreNo Patch for VPN Bypass Flaw Discovered in iOS

Published: 2020-03-26 19:55:19
Popularity: 49
Author: Eduard Kovacs
Keywords:
🤖: ""VPN fail""
Proton Technologies, the company behind the privacy-focused ProtonMail and ProtonVPN services, this week disclosed the existence of a vulnerability in Apple’s iOS mobile operating system that prevents VPN applications from encrypting all traffic. read more
...moreGoogle Releases Tool to Block USB Keystroke Injection Attacks

Published: 2020-03-12 18:25:13
Popularity: 59
Author: Ionut Arghire
Keywords:
Google has released a new software tool designed to identify potential USB keystroke injection attacks and block devices they originate from. read more
...moreCritical Flaw in VMware Workstation, Fusion Allows Code Execution on Host From Guest

Published: 2020-03-13 15:21:36
Popularity: 72
Author: Eduard Kovacs
Keywords:
🤖: ""Vulnerable VMs""
VMware has patched three serious vulnerabilities in its products, including a critical flaw in Workstation and Fusion that can be exploited to execute arbitrary code on the host from the guest operating system. The critical flaw, tracked as CVE-2020-3947, is caused by a use-after-free bug in the vmnetdhcp component. read more
...moreCisco Patches Remote Code Execution Flaws in Webex Player

Published: 2020-03-04 21:06:42
Popularity: 24
Author: Ionut Arghire
Keywords:
🤖: ""Code execution failure""
Cisco has released patches to address more than a dozen vulnerabilities across various products, including two code execution bugs in Webex Player that could be exploited remotely. read more
...moreFlaw in WordPress Themes Plugin Allowed Hackers to Become Site Admin

Published: 2020-02-17 15:44:34
Popularity: 41
Author: Eduard Kovacs
Keywords:
🤖: ""Security breach""
A serious vulnerability found in a WordPress themes plugin with over 200,000 active installations can be exploited to wipe a website’s database and gain administrator access to the site. read more
...moreGoogle Axes 500 Chrome Extensions Exfiltrating User Data

Published: 2020-02-17 19:38:51
Popularity: 41
Author: Ionut Arghire
Keywords:
🤖: "Chrome crashes"
Google has removed more than 500 extensions from the Chrome Web Store after they were found performing covert data exfiltration activities. read more
...moreFireEye Acquires Cloud Governance Firm Cloudvisory

Published: 2020-01-21 18:23:55
Popularity: 20
Author: Mike Lennon
Keywords:
🤖: "cloud takeover"
FireEye (NASDAQ: FEYE) on Tuesday announced that it has acquired Cloudvisory, a Dallas, Texas-based provider of tools for cloud visibility, security, and policy management. Terms of the acquisition were not disclosed. read more
...moreThai Officials Say Prison Cameras Were Hacked, Broadcast

Published: 2019-12-26 15:07:05
Popularity: 40
Author: Associated Press
Keywords:
Authorities in Thailand say they are investigating an apparent online break-in by a computer hacker that allowed him to broadcast surveillance video from inside a prison in the country's south. read more
...moreVulnerability Allows Hackers to Unlock Smart Home Door Locks

Published: 2019-12-11 14:16:45
Popularity: 21
Author: Kevin Townsend
Keywords:
Vulnerability in KeyWe Smart Locks Could be Exploited by Attackers to Intercept Communications to Steal Key and Unlock Doors read more
...moreHackers Plead Guilty in Data Breach that Uber Covered Up

Published: 2019-10-31 00:39:57
Popularity: 37
Author: Associated Press
Keywords:
read more
...moreResearchers Disclose Another SIM Card Attack Possibly Impacting Millions
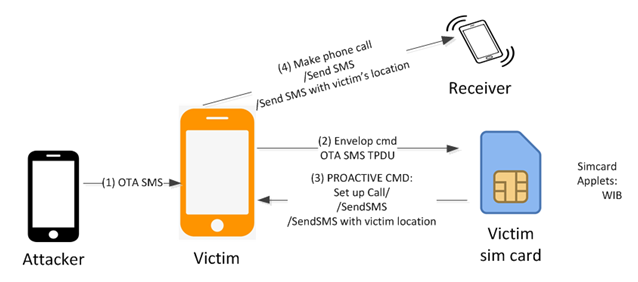
Published: 2019-09-27 11:33:27
Popularity: 76
Author: Eduard Kovacs
Keywords:
A new variant of a recently disclosed SIM card attack method could expose millions of mobile phones to remote hacking, researchers have warned. read more
...moreLinux Crypto-Miner Uses Kernel-Mode Rootkits for Evasion

Published: 2019-09-17 15:13:17
Popularity: 20
Author: Ionut Arghire
Keywords:
A recently discovered cryptocurrency mining malware targeting Linux machines is employing kernel-mode rootkits in an attempt to make detection more difficult, Trend Micro reveals. read more
...moreVulnerability Patched in Firefox Password Manager

Published: 2019-08-15 18:04:13
Popularity: 38
Author: Eduard Kovacs
Keywords:
🤖: "Browser blues"
The latest update released by Mozilla for Firefox patches a vulnerability that can be exploited to bypass the master password of the built-in password manager and obtain stored passwords. read more
...moreThreat Actor Poisons OpenPGP Certificates

Published: 2019-07-01 15:30:03
Popularity: 29
Author: Ionut Arghire
Keywords:
🤖: "Crypto chaos"
Poisoned certificates are in the OpenPGP SKS keyserver network after an unknown threat actor targeted the OpenPGP certificates of two high-profile community contributors. read more
...moreVulnerabilities Expose BD Infusion Therapy Devices to Attacks

Published: 2019-06-14 14:16:23
Popularity: 51
Author: Eduard Kovacs
Keywords:
🤖: ""Infusion hack""
CyberMDX, a research and analysis company specializing in medical device security, on Thursday revealed that its employees identified two serious vulnerabilities in infusion therapy products from medical technology firm BD. read more
...moreFacebook to Cut off Huawei to Comply With U.S. Sanctions
🤖: ""Cutting ties""
Facebook said Friday it would cut off Huawei from its popular social networking apps to comply with US sanctions, further isolating the Chinese tech giant considered a national security threat by Washington. read more
...moreIntel MDS Vulnerabilities: What You Need to Know

Published: 2019-05-15 14:29:55
Popularity: 64
Author: Eduard Kovacs
Keywords:
read more
...moreCisco Finds Serious Flaws in Sierra Wireless AirLink Devices

Published: 2019-04-26 13:55:06
Popularity: 153
Author: Eduard Kovacs
Keywords:
Cisco’s Talos research and intelligence group on Thursday disclosed the details of nearly a dozen vulnerabilities uncovered in Sierra Wireless AirLink devices, including serious flaws that can be exploited to change system settings, execute arbitrary code, and modify passwords. read more
...moreGoogle Discloses Windows Lockdown Policy Zero-Day | SecurityWeek.Com
Published: 2019-03-07 22:25:04
Popularity: None
Author: None
Google Discloses Unpatched Windows Lockdown Policy Bypass
A Windows 10 vulnerability that could bypass Windows Lockdown Policy and result in arbitrary code execution remains unpatched 90 days after Microsoft has been informed on the bug’s existence.
On systems with User Mode Code Integrity (UMCI) enabled, a .NET bug can be exploited to bypass the Windows Lockdown Policy check for COM Class instantiation, security researcher James Forshaw of Google's Project Zero team.
The issue was reproduced on Windows 10S, but is said to impact all Windows 10 versions with UMCI enabled.
The vulnerability, the security researcher explains, resides in the manner in which the WLDP COM Class lockdown policy behaves when a .NET COM object is instantiated.
The policy contains a hardcoded list of 8 to 50 COM objects which enlightened scripting engines can instantiate. Thus, even if one would be able to register an existing DLL under one of the allowed COM CLSIDs, a good implementation should check the CLSID passed to DllGetObject against said internal list, and prevent attacks.
What the security researcher discovered was that, when a .NET COM object is instantiated, the CLSID passed to DllGetClassObject is only used to look up the registration information in HKCR, the CLSID is thrown away, and the .NET object created.
Because of that, an attacker can add registry keys, including to HKCU, to load an arbitrary COM visible class under one of the allowed CLSIDs.
“This has a direct impact on the class policy as it allows an attacker to add registry keys (including to HKCU) that would load an arbitrary COM visible class under one of the allowed CLSIDs. As .NET then doesn’t care about whether the .NET Type has that specific GUID you can use this to bootstrap arbitrary code execution,” the researcher notes.
For a successful exploitation, an attacker could use tools such as Forshaw’s DotNetToJScript, a free tool that allows users to generate a JScript which bootstraps an arbitrary .NET Assembly and class.
Forshaw also published a Proof-of-Concept as two files: an .INF to set-up the registry and a .SCT. The latter is an example built using DotNetToJScript to load an untrusted .NET assembly into memory to display a message box, but it could be used for more than that.
The flaw was reported to Microsoft on January 19, when the company acknowledged the flaw. As per Project Zero’s policy, vendors are given 90 days to patch flaws before they are made public, and Microsoft didn’t meet the deadline for this issue.
The bug, however, isn’t critical, this being one of the main reasons details on it were publicly released.
“This issue was not fixed in April patch Tuesday therefore it's going over deadline. This issue only affects systems with Device Guard enabled (such as Windows 10S) and only serves as a way of getting persistent code execution on such a machine. It's not an issue which can be exploited remotely, nor is it a privilege escalation,” the security researcher explains.
To abuse the flaw, an attacker would require foothold on the impacted machine to install the needed registry entries. A remote code execution flaw in the operating system could be abused for that.
Considering that there are known Device Guard bypasses in the .NET framework that haven’t been fixed and continue to be usable, the security vulnerability is less serious than it would have been if all known avenues for bypass were fixed, Forshaw concludes.
Related: Google Discloses Unpatched Vulnerability in Edge Web Browser
Related: Google Discloses Unpatched Windows GDI Vulnerability
Ionut Arghire is an international correspondent for SecurityWeek.
EPA Issues Alert After Finding Critical Vulnerabilities in Drinking Water Systems

Published: 2024-05-21 10:25:29
Popularity: 29
Author: Eduard Kovacs
Keywords:
The EPA has issued an enforcement alert, outlining the steps needed to comply with the Safe Drinking Water Act. The post EPA Issues Alert After Finding Critical Vulnerabilities in Drinking Water Systems appeared first on SecurityWeek.
...moreCompany Paid Record-Breaking $75 Million to Ransomware Group: Report

Published: 2024-07-31 08:51:48
Popularity: 22
Author: Eduard Kovacs
Keywords:
🤖: "Ransomware alert"
Zscaler is aware of a company that paid a record-breaking $75 million ransom to the Dark Angels ransomware group. The post Company Paid Record-Breaking $75 Million to Ransomware Group: Report appeared first on SecurityWeek.
...moreOil Giant Halliburton Confirms Cyber Incident, Details Scarce

Published: 2024-08-22 17:31:41
Popularity: 7
Author: SecurityWeek News
Keywords:
🤖: ""System Down""
US oil giant Halliburton confirmed its computer systems were hit by a cyberattack that affected operations at its Houston offices. The post Oil Giant Halliburton Confirms Cyber Incident, Details Scarce appeared first on SecurityWeek.
...moreRussian GRU Unit Tied to Assassinations Linked to Global Cyber Sabotage and Espionage

Published: 2024-09-05 18:41:02
Popularity: 21
Author: Ryan Naraine
Keywords:
🤖: ""Spy Game""
A secretive Russian military unit, previously linked to assassinations and destabilization in Europe, is blamed for destructive wiper malware attacks in Ukraine. The post Russian GRU Unit Tied to Assassinations Linked to Global Cyber Sabotage and Espionage appeared first on SecurityWeek.
...moreControversial Firms Cellebrite and Corellium Announce $200 Million Acquisition Deal

Published: 2025-06-05 12:35:44
Popularity: 6
Author: Eduard Kovacs
Keywords:
🤖: "Spyware boom 💸🔒"
Cellebrite and Corellium, whose names have been mentioned in spyware stories, are joining forces to provide advanced investigative solutions. The post Controversial Firms Cellebrite and Corellium Announce $200 Million Acquisition Deal appeared first on SecurityWeek.
...more
