This write up is about a pentest we did in which we managed to compromise a hybrid GCP hosted infrastructure using native GCP tools for…
...moreSummary
Total Articles Found: 20
Top sources:
- Medium 20
Top Keywords:
Top Authors
- Security Shenanigans: 1
- Andy Robbins: 1
- Dmitrii Eliuseev: 1
- Guardio: 1
- Sourav Kalal: 1
Top Articles:
- Enumeration and lateral movement in GCP environments
- Managed Identity Attack Paths, Part 1: Automation Accounts
- Nude Pictures on early Retro PCs — Was it Possible?
- Message Security Layer
- Announcing Scumblr and Sketchy
- Detecting VPN (and its configuration!) and proxy users on the server side
- Another “critical” “VPN” “vulnerability” and why Port Fail is bullshit
- Introducing BOLOS: Blockchain Open Ledger Operating System
- Vue 2.0 is Here!
- Message#5 — Trick or Treat?
Enumeration and lateral movement in GCP environments

Published: 2022-06-12 19:07:00
Popularity: None
Author: Security Shenanigans
🤖: "pentest mode on"
Managed Identity Attack Paths, Part 1: Automation Accounts

Published: 2022-06-12 19:06:06
Popularity: None
Author: Andy Robbins
🤖: ""backdoor found""
In this three part blog series we will explore attack paths that emerge out of Managed Identity assignments in three Azure services.
...moreNude Pictures on early Retro PCs — Was it Possible?

Published: 2022-01-06 17:25:40
Popularity: None
Author: Dmitrii Eliuseev
🤖: "Old computer shame"
The JPEG image format was introduced in 1993 and GIF was released in 1987. Was it possible to watch nude photos on this lovely portable…
...moreMessage Security Layer

Published: 2019-03-08 00:47:08
Popularity: None
Author: None
🤖: "Secure fail"
A Modern Take on Securing Communication
...moreAnnouncing Scumblr and Sketchy

Published: 2019-03-08 00:42:15
Popularity: None
Author: None
🤖: "New sketchy features"
Search, Screenshot, and Reclaim the Internet
...moreDetecting VPN (and its configuration!) and proxy users on the server side

Published: 2019-03-08 00:15:44
Popularity: None
Author: None
🤖: ""Sneaky users""
A lot of people use VPN every day. Somebody use it in always-on mode to circumvent government or corporative internet censorship, while…
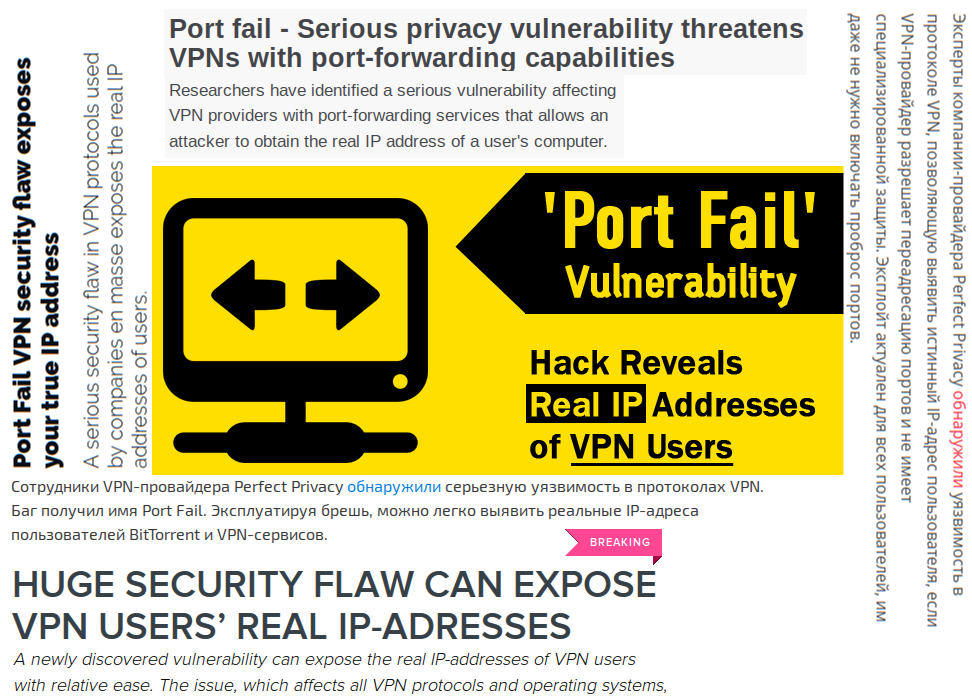
...moreAnother “critical” “VPN” “vulnerability” and why Port Fail is bullshit
Published: 2019-03-08 00:01:32
Popularity: None
Author: None
The morning of November 26 brought me interesting news: guys from Perfect Privacy disclosed the Port Fail vulnerability, which can lead to…
...moreIntroducing BOLOS: Blockchain Open Ledger Operating System

Published: 2019-03-07 23:57:01
Popularity: None
Author: None
We’re pleased to introduce our new Operating System, designed by our firmware team and leveraging on the expertise of powering millions of…
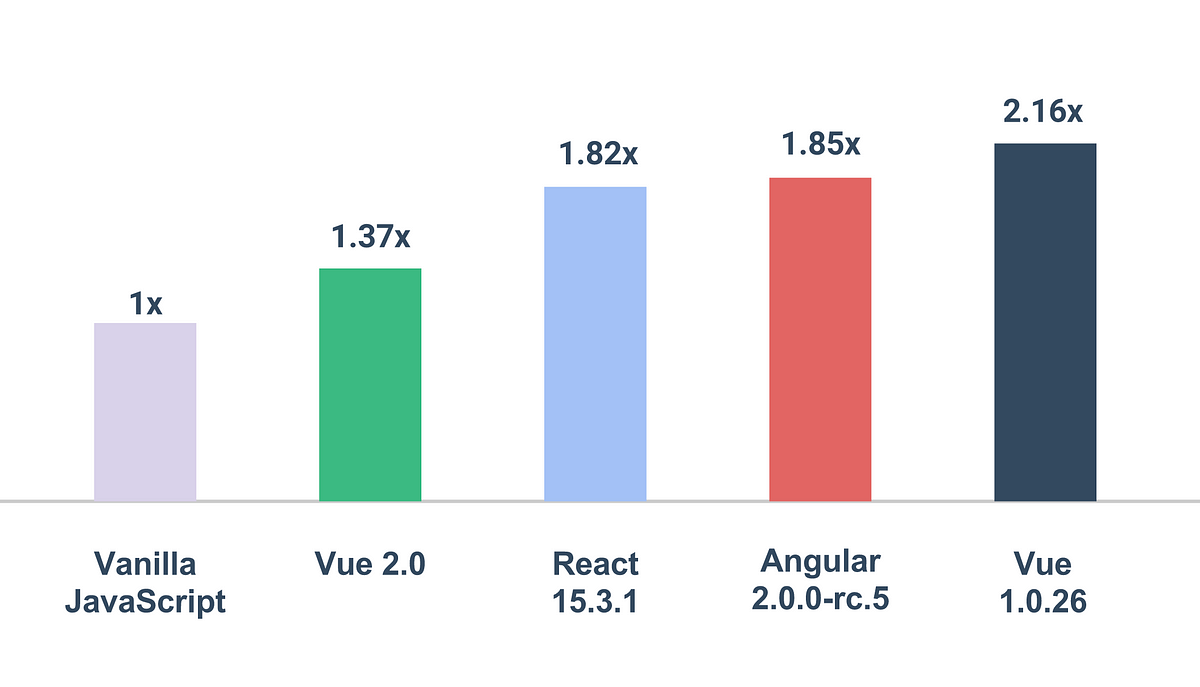
...moreVue 2.0 is Here!
Published: 2019-03-07 23:33:18
Popularity: None
Author: None
Today I am thrilled to announce the official release of Vue.js 2.0: Ghost in the Shell. After 8 alphas, 8 betas and 8 rcs (a total…
...moreMessage#5 — Trick or Treat?
Published: 2019-03-07 23:30:30
Popularity: None
Author: None
— — -BEGIN PGP SIGNED MESSAGE — — - Hash: SHA256
...moreHistory tells us what may happen next with Brexit & Trump

Published: 2019-03-07 23:17:25
Popularity: None
Author: None
It seems we’re entering another of those stupid seasons humans impose on themselves at fairly regular intervals. I am sketching out here…
...moreIntroducing “gnirehtet”, a reverse tethering tool for Android

Published: 2019-03-07 23:07:48
Popularity: None
Author: None
A cross-platform tool providing internet access to Android devices through USB
...moreCryptographic vulnerabilities in IOTA
Published: 2019-03-07 22:52:20
Popularity: None
Author: None
Last month, Ethan Heilman, Tadge Dryja, Madars Virza, and I took a look at IOTA, currently the 8th largest cryptocurrency with a $1.9B…
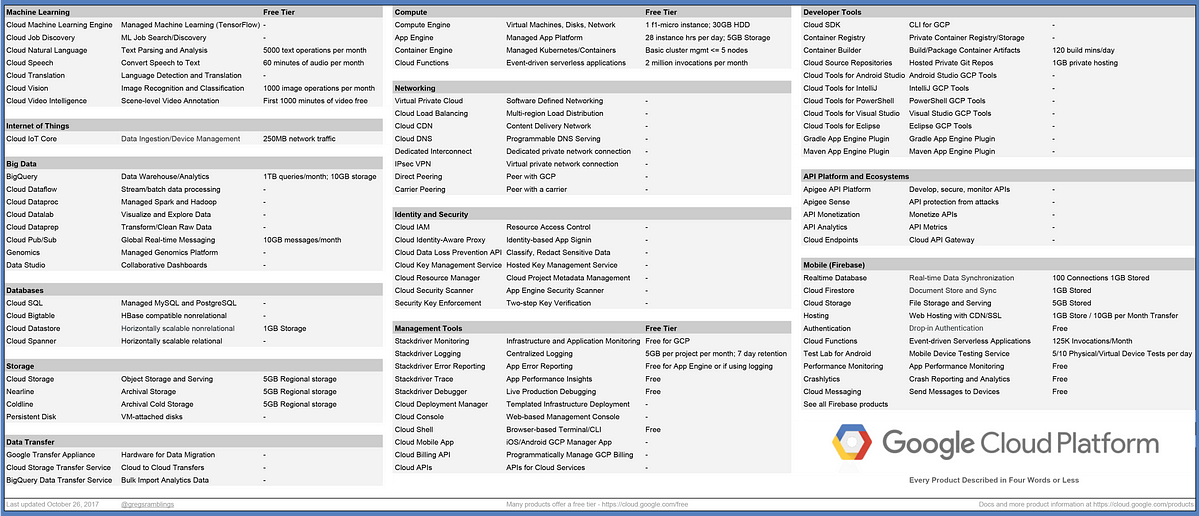
...moreGCP products described in 4 words or less
Published: 2019-03-07 22:45:31
Popularity: None
Author: None
Google Cloud Platform products described in 4 words or less and free tier information.
...more“Huge Dirty COW” (CVE-2017–1000405)
Published: 2019-03-07 22:40:48
Popularity: None
Author: None
The incomplete Dirty COW patch
...moreOh-my-zsh Plugins for Metasploit Framework and Python SimpleHTTPServer

Published: 2019-03-07 22:40:43
Popularity: None
Author: None
Oh-My-Zsh is an open source, community-driven framework for managing your ZSH configuration. It comes bundled with a ton of helpful…
...moreLicense received: Edgeless becomes first legal blockchain casino!

Published: 2019-03-07 22:37:32
Popularity: None
Author: None
The Edgeless team is extremely excited to announce a successfully received casino license. That’s a huge step for the entire gambling and…
...moreExploiting a 0-Day Opera Vulnerability with a Cross-Browser Extension Store Attack

Published: 2024-10-31 12:30:03
Popularity: None
Author: Guardio
🤖: ""Opera hack fail""
By Nati Tal (Head of Guardio Labs)
...moreElectron JS ASAR Integrity Bypass

Published: 2024-07-22 16:01:38
Popularity: None
Author: Sourav Kalal
🤖: ""Exploit detected""
I recently created an Electron JS-based Windows and MacOS application. The newer version of Electron has Integrity detection which…
...moreMarketplace Takeover: How We Could’ve Taken Over Every Developer Using a VSCode Fork; Putting Millions at Risk

Published: 2025-07-01 02:50:24
Popularity: None
Author: Oren Yomtov
🤖: "VSCode takeover"
TL;DR: We discovered a critical vulnerability in open-vsx.org — the open-source VS Code extension marketplace used by over 8,000,000…
...more