It's one of the many new connected bathroom fixtures the company is debuting at CES 2024.
...moreSummary
Total Articles Found: 42
Top sources:
- Gizmodo 42
Top Keywords:
Top Authors
- Dell Cameron: 7
- Tom McKay: 6
- Rhett Jones: 4
- Kate Conger: 3
- Sam Rutherford: 3
Top Articles:
- Kohler's Newest Bidet Finally Brings Alexa and Google to Your Butt
- Meta Security Exec Hacked and Tracked for a Year by 'Predator' Spyware
- It's Time to Nervously Mock the 50 Worst Passwords of the Year
- Stop Using Avast and AVG Plugins Right Now
- Cisco to Pay $8.6 Million in Settlement Over Vulnerabilities in Video Surveillance Software It Sold to Feds, States
- One of the Largest Dark Net Markets ‘of All Time’ Falls to Police
- Deep Web Search Engine Memex Fights Crime a Bit Like Minority Report
- LA's New Streetlamps Will Keep Cell Service Running After an Earthquake
- A Single Text Can Disable iOS Messages Forever
- AT&T Launches Fake 5G Network in Desperate Attempt to Seem Innovative
Kohler's Newest Bidet Finally Brings Alexa and Google to Your Butt

Published: 2024-01-07 17:22:03
Popularity: None
Author: None
Meta Security Exec Hacked and Tracked for a Year by 'Predator' Spyware

Published: 2023-03-21 11:12:15
Popularity: None
Author: None
A Meta executive spent a year under surveillance by the Greek government, in what appears to be the first targeting of a U.S. citizen by "Predator" spyware.
...moreIt's Time to Nervously Mock the 50 Worst Passwords of the Year

Published: 2019-12-20 03:40:28
Popularity: None
Author: None
In spite of everything—the leaks, the breaches, the myriad privacy risks—a large majority of people are still using “password” and “123456” as their password. Folks, it’s long past time to stop taking security shortcuts.
...moreStop Using Avast and AVG Plugins Right Now

Published: 2019-12-05 12:57:38
Popularity: None
Author: None
🤖: ""Plugin Pandemonium""
Two browsers have yanked Avast and AVG online security extensions from their web stores after a report revealed that they were unnecessarily sucking up a ton of data about users’ browsing history.
...moreCisco to Pay $8.6 Million in Settlement Over Vulnerabilities in Video Surveillance Software It Sold to Feds, States

Published: 2019-08-01 10:24:04
Popularity: None
Author: Tom McKay
🤖: "Bug bounty 🐞💸"
Cisco Systems has agreed to an $8.6 million settlement with the federal government stemming from allegations it “improperly sold video surveillance software with known vulnerabilities to U.S. federal and state governments,” Reuters reported on Wednesday.
...moreOne of the Largest Dark Net Markets ‘of All Time’ Falls to Police

Published: 2019-05-05 02:55:43
Popularity: None
Author: Patrick Howell O'Neill
🤖: "Dark web takedown"
Police from around the world shut down the biggest active black market on the dark web this month, according to announcements from law enforcement agencies in the United States, Germany, and the Netherlands released on Friday.
...moreDeep Web Search Engine Memex Fights Crime a Bit Like Minority Report

Published: 2019-03-08 00:26:12
Popularity: None
Author: Adam Clark Estes
🤖: ""Future crime solver""
Exactly one year ago, DARPA announced a characteristically scifi-inspired mission: to create a search engine that could find things on the deep web that Google's crawlers would miss. The so-called Memex project is now well underway, and for the first time we're getting a look at the crime-fighting search engine in action.
...moreLA's New Streetlamps Will Keep Cell Service Running After an Earthquake

Published: 2019-03-08 00:05:05
Popularity: None
Author: Alissa Walker
🤖: "Wireless rescue"
Cities beefing up their smart infrastructure have tapped the ubiquitous streetlamp to track traffic data and measure pollution. Now, in Los Angeles, some streetlights will help keep the communications network intact after an emergency.
...moreA Single Text Can Disable iOS Messages Forever

Published: 2019-03-07 23:24:41
Popularity: None
Author: Alex Cranz
One of the beauties of iOS versus other phone operating systems is its relative security and stability versus other phone operating systems. There just aren’t a lot of hacks that can harm an iPhone unless it has been jailbroken or hacked by Israeli cyber weapons dealers. But a new exploit will permanently disable the Messages app. So prepare to be wary of any text your asshole friends and colleagues send your way.
...moreAT&T Launches Fake 5G Network in Desperate Attempt to Seem Innovative

Published: 2019-03-07 23:06:43
Popularity: None
Author: Adam Clark Estes
Have you heard? AT&T is going to “pave the way for the next generation of faster speeds” with something called 5G Evolution. No, it’s not actually a new 5G network, the much hyped successor to 4G that’s supposed to change the way we connect to the internet. It’s just a re-branded 4G offering, and AT&T’s sad attempt at seeming innovative.
...moreIn Worrisome Move, Kaspersky Agrees to Turn Over Source Code to US Government

Published: 2019-03-07 22:59:17
Popularity: None
Author: Rhett Jones
Over the last couple of weeks, there’s been a disturbing trend of governments demanding that private tech companies share their source code if they want to do business. Now, the US government is giving the same ultimatum and it’s getting what it wants.
...moreMost Guns Sold on the Dark Web Originate From the United States, Study Finds, Surprising No One

Published: 2019-03-07 22:58:09
Popularity: None
Author: Dell Cameron
Roughly three-fifths of the weapons sold on a selection of dark web marketplaces originate from the United States, according to a new study examining the scope of the internet’s black market arms trade.
...moreHackers Breach Cybersecurity Company In Apparent Revenge On Employee

Published: 2019-03-07 22:56:37
Popularity: None
Author: Kate Conger
A threat analyst at the cybersecurity firm Mandiant has been hacked and the attackers are claiming to have lurked on his computer for a year, collecting his login credentials for various sites and tracking his location.
...moreTop Security Firm May Be Leaking 'Terabytes' of Confidential Data From Fortune 100 Companies [Updated]

Published: 2019-03-07 22:55:22
Popularity: None
Author: Dell Cameron
A leading American security company and purveyor of anti-malware detection services is waking up to a damning report about a massive vulnerability in its flagship product. The report describes an unimaginable leak, the scope of which covers a wide range of confidential data, including customer credentials and financial records, among other sensitive files.
...moreReports of Cuba's Deafening 'Covert Sonic Device' Are Only Getting Stranger

Published: 2019-03-07 22:53:57
Popularity: None
Author: Rhett Jones
The State Department has remained tight-lipped about the strange circumstances in which US diplomats to Cuba reportedly suffered permanent hearing damage from an “inaudible covert sonic device.” But new details reveal that “a deafeningly loud sound similar to the buzzing created by insects or metal scraping” was also used to harass the American envoys. What’s more, the number of people who were harmed is reportedly even greater than was previously known.
...moreEquifax Has Been Sending Consumers to a Fake Phishing Site for Almost Two Weeks

Published: 2019-03-07 22:50:48
Popularity: None
Author: Dell Cameron
Equifax’s response to its data breach has been a total shitshow, something the company seems determined to remind us of each and every day.
...moreWelp, Looks Like Imgur Has Also Been Hacked
Published: 2019-03-07 22:41:24
Popularity: None
Author: Tom McKay
2017's unending parade of major companies and web destinations suffering through major breaches of user information has not slowed down. Image-sharing site Imgur revealed it had been hacked several years ago this week, with the details of approximately 1.7 million accounts lost in 2014 to hackers who have not been identified.
...moreStudy: Hackers Could Disrupt or Crash HDDs Using Only Sound Waves

Published: 2019-03-07 22:36:27
Popularity: None
Author: Tom McKay
Want to destroy video evidence of a break-in, prevent ATMs from logging malware attacks, or simply shut down a critical computer system? One possible way to do that might be disrupting hard disk drives with sound waves, either with a specialized device or just by hijacking a nearby speaker.
...moreYet Another Password Vulnerability Has Been Found in macOS High Sierra
Published: 2019-03-07 22:35:34
Popularity: None
Author: Bryan Menegus
For the third time in recent months, big problems have been discovered with macOS High Sierra.
...moreCryptocurrency Scam Site Disappears, Leaving Only the Word ‘Penis’ Behind

Published: 2019-03-07 22:33:05
Popularity: None
Author: Bryan Menegus
A short-lived and relatively unknown cryptocurrency project built on Ethereum called Prodeum disappeared this weekend—along with the money a small number of hapless investors sunk into it. All that remained of its website was a white page with the word “penis” written on it.
...moreUpdate Your Firefox Now: Mozilla Just Patched a ‘Critical’ Security Flaw

Published: 2019-03-07 22:32:29
Popularity: None
Author: Sam Rutherford
Firefox version 57, otherwise known as Firefox Quantum, has done wonderful things to help get Mozilla’s open-source web browser back in shape, but along the way, the company has made a few mistakes. One of the biggest of Mozilla’s recent flubs was an exploit hidden in Firefox’s user interface code that made it possible to for an attacker to run unsanitized HTML on a user’s computer.
...moreFacebook Admits Spam Texts to Two-Factor Authentication Users Were a Bug

Published: 2019-03-07 22:31:18
Popularity: None
Author: Kate Conger
Two-factor authentication, a security measure that requires a verification code as well as a password upon login, can help prevent phishing and account takeover.
...moreDo Not, I Repeat, Do Not Download Onavo, Facebook’s Vampiric VPN Service

Published: 2019-03-07 22:30:38
Popularity: None
Author: Dell Cameron
Facebook is not a privacy company; it’s Big Brother on PCP. It does not want to anonymize and protect you; it wants to drain you of your privacy, sucking up every bit of personal data. You should resist the urge to let it, at every turn.
...morePyeongchang Olympics Hit By Cyber Attack, With Widespread Rumors Russia to Blame

Published: 2019-03-07 22:30:35
Popularity: None
Author: Tom McKay
Officials at the 2018 Pyeonchang Winter Olympics have occurred that a cyber attack hit the games, taking its website as well as TV and internet access at its main press center offline, the Guardian reported.
...moreGo Update Your Apple Devices to Fix the Telugu 'Text Bomb' Bug Now
Published: 2019-03-07 22:30:29
Popularity: None
Author: Sam Rutherford
What started out as a seemingly simple bug turned into a real hassle when people figured out it was possible to crash iMessage, Twitter or even the Wi-Fi app on Apple products by inserting a single character from the Indian language of Telugu. And once an app had crashed, it would keep crashing forever until you took somewhat extreme measures like deleting and reinstalling the app, erasing entire conversation threads, or upgrading to a beta version of your device’s OS.
...moreHouse Democrats Join Everyone Else in Letting Equifax Off Easy for Catastrophic Hack

Published: 2019-03-07 22:30:23
Popularity: None
Author: Matt Novak
After Equifax’s negligence allowed hackers to steal the personal information of 145.5 million Americans, the company promised to give everyone free credit monitoring for a year. But House Democrats have formally requested that Equifax extend the monitoring from one year to three years. Even that, however, feels pretty damn inadequate.
...moreThe FBI Busts Phantom Secure CEO for Allegedly Selling Encrypted Phones to Gangs, Drug Cartels

Published: 2019-03-07 22:29:03
Popularity: None
Author: Tom McKay
The FBI has arrested the owner of Phantom Secure, one of a number of phone companies that it claims sells customized BlackBerry and Android devices for use in international criminal organizations.
...moreUS Power Company Fined $2.7 Million Over Security Flaws Impacting 'Critical Assets'

Published: 2019-03-07 22:28:53
Popularity: None
Author: Dell Cameron
An American power company has reached a settlement to pay an unprecedented $2.7 million penalty over significant security oversights that could have allowed hackers to gain remote access to the power provider’s systems.
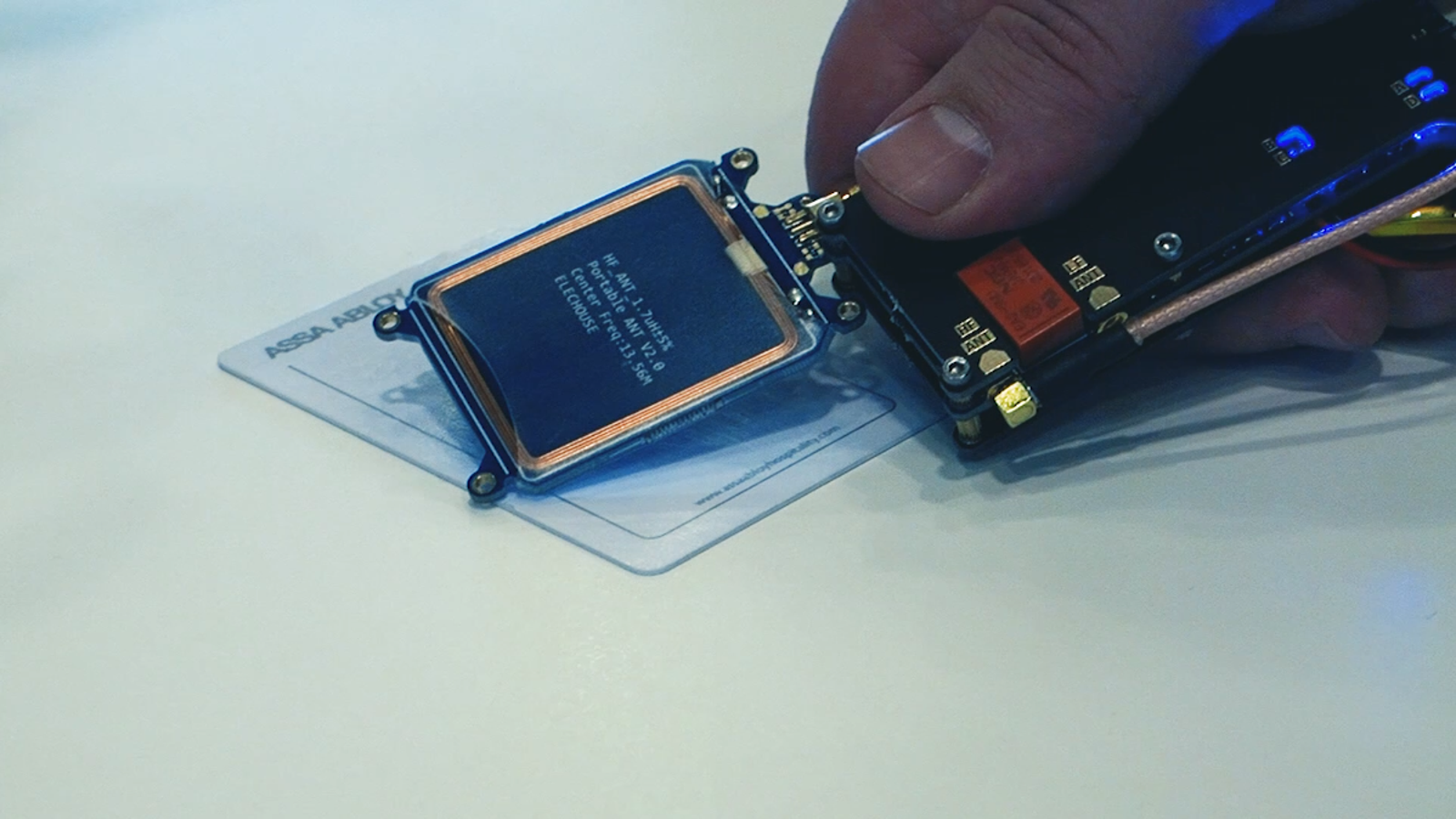
...moreHackers Designed a 'Master Key' to Unlock Millions of Hotel Room Doors
Published: 2019-03-07 22:24:03
Popularity: None
Author: Dell Cameron
A critical flaw in electronic locks left millions of hotel rooms worldwide vulnerable to hackers. Now, the security researchers who developed the attack are helping hotels patch the problem, literally door to door.
...moreCambridge Analytica Is Shutting Down [Updated]

Published: 2019-03-07 22:23:24
Popularity: None
Author: Melanie Ehrenkranz
On Wednesday, Cambridge Analytica employees learned that its parent company, the SCL Group, was shuttering the business, with American-based workers directed to return their keycards immediately, according to documentation reviewed by Gizmodo.
...moreShhlack Lets You Encrypt Slack Messages So Your Boss Can't See Private Conversations
Published: 2019-03-07 22:23:10
Popularity: None
Author: AJ Dellinger
Slack, the messaging service of choice for tens of thousands of organizations, has given employers a considerable amount of access to the data and communications of employees. A new tool called Shhlack finally gives employees the power to shield their private conversations with end-to-end encryption.
...moreNew PGP Encryption Exploits Are Being Discovered Almost Every Other Day

Published: 2019-03-07 22:21:08
Popularity: None
Author: Dell Cameron
For more than a week, PGP developers have been rapidly working to patch critical flaws in the legacy encryption protocol used for sending and receiving secure emails; a tool that’s widely relied upon by lawyers, journalists, dissidents, and human rights advocates, many of whom operate at the highest levels of risk in shadows cast by repressive and unforgiving regimes.
...moreGoogle Plans Not to Renew Its Contract for Project Maven, a Controversial Pentagon Drone AI Imaging Program
Published: 2019-03-07 22:19:51
Popularity: None
Author: Kate Conger
Google will not seek another contract for its controversial work providing artificial intelligence to the U.S. Department of Defense for analyzing drone footage after its current contract expires.
...morePaul Manafort Learns That Encrypting Messages Doesn't Matter If the Feds Have a Warrant to Search Your iCloud Account

Published: 2019-03-07 22:19:20
Popularity: None
Author: Matt Novak
Federal prosecutors have accused Paul Manafort of witness tampering, alleging that he used WhatsApp and Telegram in an attempt to coordinate his testimony with old business associates. Manafort, Donald Trump’s former campaign manager, may have thought that he was being sneaky by using encrypted chat apps, but Manafort just learned the hard way that strong encryption doesn’t really matter if you’re backing up your messages to the cloud—especially when the federal government gets a warrant to access your iCloud account.
...moreVerizon's New Phone Plan Proves It Has No Idea What 'Unlimited' Actually Means

Published: 2019-03-07 22:18:35
Popularity: None
Author: Sam Rutherford
Wireless carriers have already demonstrated an inability to understand what “unlimited” actually means, offering phone plans that habitually throttle customers who use more than 26GB or so of data every month. However, with the release of its new Above Unlimited plan, Verizon is pushing the mental gymnastics carriers employ to define unlimited to a whole new level.
...moreRobbing an Apple Store Looks Exactly as Easy as You'd Expect

Published: 2019-03-07 22:16:36
Popularity: None
Author: Melanie Ehrenkranz
Stealing tens of thousands of dollars worth of Apple products didn’t call for an Oceans Eleven-style elaborate heist. No, it simply required less than thirty seconds and moving with a sense of purpose.
...moreWi-Fi 6 Is Coming: Here's Why You Should Care

Published: 2019-03-07 22:09:26
Popularity: None
Author: David Nield
Get ready for the next generation of wifi technology: Wi-fi 6 (for so it is named) is going to be appearing on devices from next year. But will you have to throw out your old router and get a new one? And is this going to make your Netflix run faster? Here’s everything you need to know about the new standard.
...moreSIM Cards That Force Your Mobile Data Through Tor Are Coming

Published: 2019-03-07 22:07:24
Popularity: None
Author: Rhett Jones
It’s increasingly difficult to expect privacy when you’re browsing online, so a non-profit in the UK is working to build the power of Tor’s anonymity network right into the heart of your smartphone.
...moreApple Reportedly Blocked Police iPhone Hacking Tool and Nobody Knows How

Published: 2019-03-07 22:07:20
Popularity: None
Author: Rhett Jones
Apple’s latest iteration of iOS has reportedly turned the GrayKey hacking device into an expensive doorstop. Law enforcement around the world has taken to using GrayKey to break into locked iPhones but it appears Apple has finally gotten ahead of the device’s crafty manufacturers. For now.
...moreHackers Take Over Chromecast Device to Warn Users, Plug YouTuber PewDiePie

Published: 2019-03-07 22:01:21
Popularity: None
Author: Tom McKay
Hackers who reportedly commandeered thousands of Chromecast streaming devices on Monday used them to alert owners to a hole in their security, while also plugging their favorite YouTube star—perennial edgelord PewDiePie, a.k.a. Felix Kjellberg
...moreHuawei Punishes Employees Who Sent New Year's Tweet From an iPhone

Published: 2019-03-07 22:01:16
Popularity: None
Author: Matt Novak
Chinese technology company Huawei sent out a tweet over the New Year’s holiday wishing everyone a happy 2019. But many social media users noticed that the tweet had been sent from an iPhone. Why does that matter? The iPhone is made by Huawei’s American competitor Apple, and now there are reports that the employees who were responsible for the Huawei tweet have been punished.
...moreIt’s Time to Audit All the Extensions You've Installed on Your Browser
Published: 2019-03-07 21:59:19
Popularity: None
Author: David Nield
A lot of what we do on our computers goes through the browser, and that means any extensions you choose to add on top of that browser have a very privileged position: They can see where you’re going online, they can see the data you’re passing to and from the web, and they can send and receive data themselves.
...more