Comments
...moreSummary
Total Articles Found: 11
Top sources:
Top Keywords:
- hardware: 11
- security: 8
- vulnerabilities: 2
- privacy: 1
- networking: 1
Top Authors
Top Articles:
- Unpatchable vulnerability in Apple chip leaks secret encryption keys
- Smart male chastity lock cock-up
- DARPA Is Developing an Open-Source Voting System
- Wi-Fi Chip Vulnerability
- A mysterious bug in the firmware of Google's Titan M chip (CVE-2019-9465)
- Thangrycat: A Serious Cisco Vulnerability
- How I built a fully offline smart home, and why you should too
- Intel Microcode Decryptor
- SATAn: Air-Gap Exfiltration Attack via Radio Signals From SATA Cables
- Telenot Complex: Insecure AES Key Generation
Unpatchable vulnerability in Apple chip leaks secret encryption keys
Published: 2024-03-21 17:15:26
Popularity: 1630
Author: arstechnica.com via asymmetric
Keywords:
How I built a fully offline smart home, and why you should too
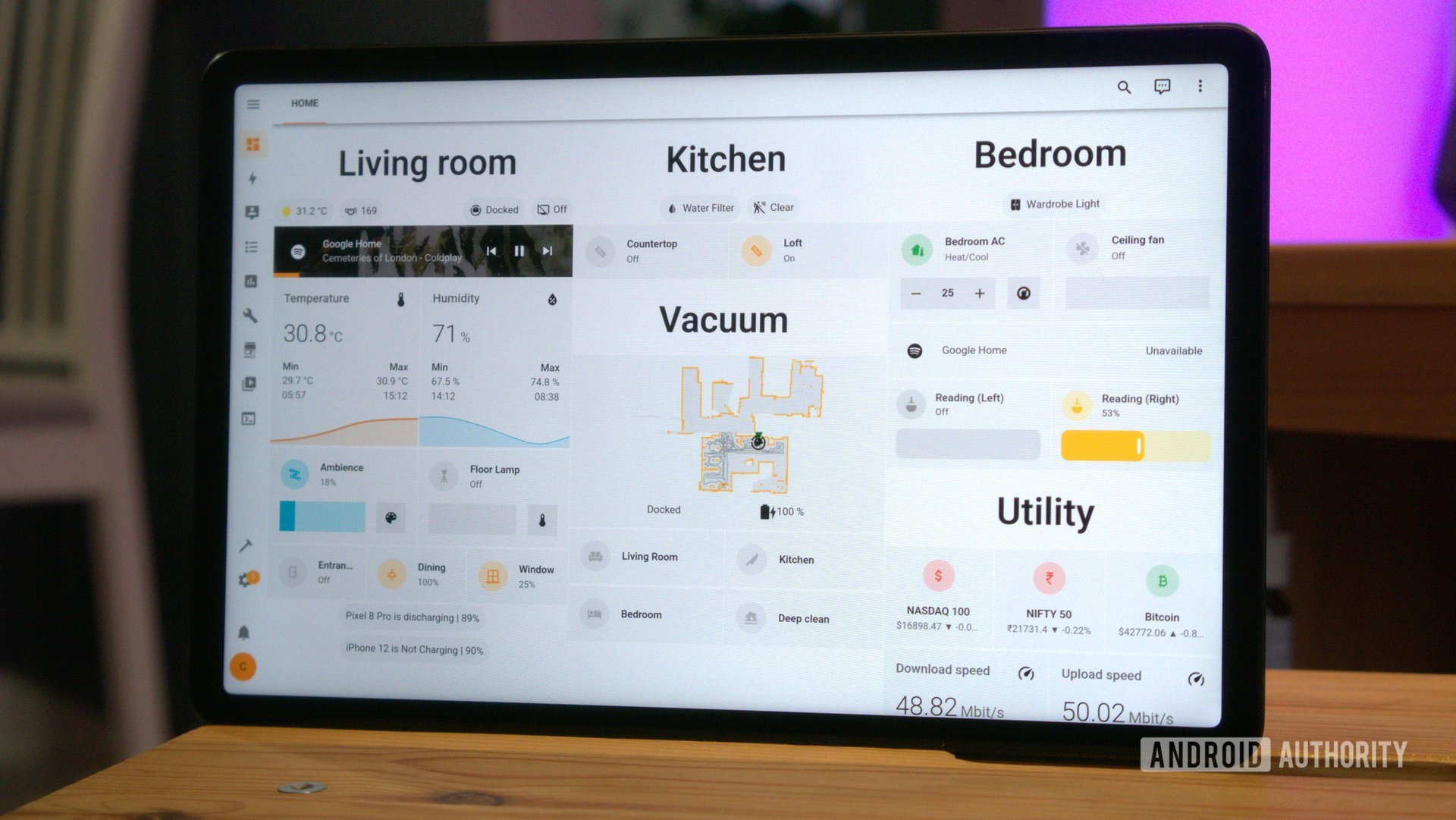
Published: 2024-01-07 14:11:26
Popularity: 96
Author: andrewfromx@users.lobste.rs (andrewfromx)
Keywords:
Comments
...moreIntel Microcode Decryptor
Published: 2022-07-19 12:38:57
Popularity: 68
Author: wizardishungry@users.lobste.rs (wizardishungry)
Keywords:
Comments
...moreSATAn: Air-Gap Exfiltration Attack via Radio Signals From SATA Cables

Published: 2022-07-18 19:22:00
Popularity: 54
Author: rjzak@users.lobste.rs (rjzak)
Keywords:
🤖: "SATA hack 📊💻"
Comments
...moreTelenot Complex: Insecure AES Key Generation
Published: 2022-01-18 12:06:54
Popularity: None
Author: freddyb@users.lobste.rs (freddyb)
Keywords:
Comments
...moreStop! Hammer Time: Rethinking Our Approach to Rowhammer Mitigations

Published: 2021-06-03 17:07:50
Popularity: None
Author: kuijsten@users.lobste.rs (kuijsten)
Keywords:
🤖: "Hammer time smash"
Rowhammer attacks exploit electromagnetic interference among nearby DRAM cells to flip bits, corrupting data and altering system behavior. Unfortunately, DRAM vendors have opted for a blackbox approach to preventing these bit flips, exposing little information about in-DRAM mitigations. Despite vendor claims that their mitigations prevent Rowhammer, recent work bypasses these defenses to corrupt data. Further work shows that the Rowhammer problem is actually worsening in emerging DRAM and posits that system-level support is needed to produce adaptable and scalable defenses. Accordingly, we argue that the systems community can and must drive a fundamental change in Rowhammer mitigation techniques. In the short term, cloud providers and CPU vendors must work together to supplement limited in-DRAM mitigations—ill-equipped to handle rising susceptibility— with their own mitigations. We propose novel hardware primitives in the CPU’s integrated memory controller that would enable a variety of efficient software defenses, offering flexible safeguards against future attacks. In the long term, we assert that major consumers of DRAM must persuade DRAM vendors to provide precise information on their defenses, limitations, and necessary supplemental solutions. Comments
...moreSmart male chastity lock cock-up
Published: 2020-10-08 02:50:25
Popularity: 1398
Author: calvin@users.lobste.rs (calvin)
Keywords:
Comments
...moreA mysterious bug in the firmware of Google's Titan M chip (CVE-2019-9465)

Published: 2020-02-29 18:51:54
Popularity: 147
Author: calvin@users.lobste.rs (calvin)
Keywords:
🤖: "BuggedTitan"
Comments
...moreWi-Fi Chip Vulnerability

Published: 2020-03-03 12:43:15
Popularity: 194
Author: Bruce Schneier
Keywords:
🤖: ""Hack alert""
There's a vulnerability in Wi-Fi hardware that breaks the encryption: The vulnerability exists in Wi-Fi chips made by Cypress Semiconductor and Broadcom, the latter a chipmaker Cypress acquired in 2016. The affected devices include iPhones, iPads, Macs, Amazon Echos and Kindles, Android devices, and Wi-Fi routers from Asus and Huawei, as well as the Raspberry Pi 3. Eset, the security...
...moreThangrycat: A Serious Cisco Vulnerability

Published: 2019-05-23 16:52:31
Popularity: 147
Author: Bruce Schneier
Keywords:
🤖: "pwned 💻"
Summary: Thangrycat is caused by a series of hardware design flaws within Cisco's Trust Anchor module. First commercially introduced in 2013, Cisco Trust Anchor module (TAm) is a proprietary hardware security module used in a wide range of Cisco products, including enterprise routers, switches and firewalls. TAm is the root of trust that underpins all other Cisco security and trustworthy...
...moreDARPA Is Developing an Open-Source Voting System

Published: 2019-03-14 18:20:34
Popularity: 248
Author: Bruce Schneier
Keywords:
🤖: "Election hack proof?"
This sounds like a good development: ...a new $10 million contract the Defense Department's Defense Advanced Research Projects Agency (DARPA) has launched to design and build a secure voting system that it hopes will be impervious to hacking. The first-of-its-kind system will be designed by an Oregon-based firm called Galois, a longtime government contractor with experience in designing secure and...
...more