Microsoft has updated its mitigation measures for the newly disclosed and actively exploited zero-day flaws in Exchange Server after it was found that they could be trivially bypassed. The two vulnerabilities, tracked as CVE-2022-41040 and CVE-2022-41082, have been codenamed ProxyNotShell due to similarities to another set of flaws called ProxyShell, which the tech giant resolved last year.
...moreSummary
Total Articles Found: 88
Top sources:
Top Keywords:
- cyber security: 1
- remote code execution: 1
- smb vulnerability: 1
- smb worm: 1
- windows security: 1
Top Authors
Top Articles:
- Your Amazon Devices to Automatically Share Your Wi-Fi With Neighbors
- Google Discloses Poorly-Patched, Now Unpatched, Windows 0-Day Bug
- Warning — Unpatched Critical 'Wormable' Windows SMBv3 Flaw Disclosed
- Google uncovers new iOS security feature Apple quietly added after zero-day attacks
- Secret Backdoor Account Found in Several Zyxel Firewall, VPN Products
- Major Instagram App Bug Could've Given Hackers Remote Access to Your Phone
- SolarWinds Blames Intern for 'solarwinds123' Password Lapse
- Apple will proxy Safe Browsing requests to hide iOS users' IP from Google
- Researchers Reveal New Security Flaw Affecting China's DJI Drones
- Intel CPUs Vulnerable to New 'SGAxe' and 'CrossTalk' Side-Channel Attacks
Mitigation for Exchange Zero-Days Bypassed! Microsoft Issues New Workarounds

Published: 2022-10-05 05:31:00
Popularity: 110
Author: noreply@blogger.com (Ravie Lakshmanan)
Uber Blames LAPSUS$ Hacking Group for Recent Security Breach

Published: 2022-09-20 09:21:00
Popularity: 153
Author: noreply@blogger.com (Ravie Lakshmanan)
🤖: ""Hackers at work""
Uber on Monday disclosed more details related to the security incident that happened last week, pinning the attack on a threat actor it believes is affiliated to the notorious LAPSUS$ hacking group. "This group typically uses similar techniques to target technology companies, and in 2022 alone has breached Microsoft, Cisco, Samsung, NVIDIA, and Okta, among others," the San Francisco-based
...moreGoogle Chrome Bug Lets Sites Silently Overwrite System Clipboard Content

Published: 2022-09-02 05:55:00
Popularity: 265
Author: noreply@blogger.com (Ravie Lakshmanan)
A "major" security issue in the Google Chrome web browser, as well as Chromium-based alternatives, could allow malicious web pages to automatically overwrite clipboard content without requiring any user consent or interaction by simply visiting them. The clipboard poisoning attack is said to have been accidentally introduced in Chrome version 104, according to developer Jeff Johnson. While the
...moreGoogle Launches New Open Source Bug Bounty to Tackle Supply Chain Attacks

Published: 2022-08-31 05:42:00
Popularity: 221
Author: noreply@blogger.com (Ravie Lakshmanan)
Google on Monday introduced a new bug bounty program for its open source projects, offering payouts anywhere from $100 to $31,337 (a reference to eleet or leet) to secure the ecosystem from supply chain attacks. Called the Open Source Software Vulnerability Rewards Program (OSS VRP), the offering is one of the first open source-specific vulnerability programs. With the tech giant the maintainer
...moreNew Google Chrome Zero-Day Vulnerability Being Exploited in the Wild

Published: 2022-08-17 05:02:28
Popularity: 280
Author: noreply@blogger.com (Ravie Lakshmanan)
Google on Tuesday rolled out patches for Chrome browser for desktops to contain an actively exploited high-severity zero-day flaw in the wild. Tracked as CVE-2022-2856, the issue has been described as a case of insufficient validation of untrusted input in Intents. Security researchers Ashley Shen and Christian Resell of Google Threat Analysis Group have been credited with reporting the flaw on
...moreResearchers Uncover UEFI Secure Boot Bypass in 3 Microsoft Signed Boot Loaders

Published: 2022-08-12 13:02:30
Popularity: 373
Author: noreply@blogger.com (Ravie Lakshmanan)
A security feature bypass vulnerability has been uncovered in three signed third-party Unified Extensible Firmware Interface (UEFI) boot loaders that allow bypass of the UEFI Secure Boot feature. "These vulnerabilities can be exploited by mounting the EFI System Partition and replacing the existing bootloader with the vulnerable one, or modifying a UEFI variable to load the vulnerable loader
...moreSonicWall Issues Patch for Critical Bug Affecting its Analytics and GMS Products

Published: 2022-07-22 11:39:32
Popularity: 232
Author: noreply@blogger.com (Ravie Lakshmanan)
Network security company SonicWall on Friday rolled out fixes to mitigate a critical SQL injection (SQLi) vulnerability affecting its Analytics On-Prem and Global Management System (GMS) products. The vulnerability, tracked as CVE-2022-22280, is rated 9.4 for severity on the CVSS scoring system and stems from what the company describes is an "improper neutralization of special elements" used in
...moreGoogle Adds Support for DNS-over-HTTP/3 in Android to Keep DNS Queries Private

Published: 2022-07-20 06:41:04
Popularity: 165
Author: noreply@blogger.com (Ravie Lakshmanan)
Google on Tuesday officially announced support for DNS-over-HTTP/3 (DoH3) for Android devices as part of a Google Play system update designed to keep DNS queries private. To that end, Android smartphones running Android 11 and higher are expected to use DoH3 instead of DNS-over-TLS (DoT), which was incorporated into the mobile operating system with Android 9.0. DoH3 is also an alternative to
...moreNew Cache Side Channel Attack Can De-Anonymize Targeted Online Users

Published: 2022-07-15 14:53:33
Popularity: 168
Author: noreply@blogger.com (Ravie Lakshmanan)
A group of academics from the New Jersey Institute of Technology (NJIT) has warned of a novel technique that could be used to defeat anonymity protections and identify a unique website visitor. "An attacker who has complete or partial control over a website can learn whether a specific target (i.e., a unique individual) is browsing the website," the researchers said. "The attacker knows this
...moreHackers Used Fake Job Offer to Hack and Steal $540 Million from Axie Infinity

Published: 2022-07-11 06:43:38
Popularity: 302
Author: noreply@blogger.com (Ravie Lakshmanan)
The $540 million hack of Axie Infinity's Ronin Bridge in late March 2022 was the consequence of one of its former employees getting tricked by a fraudulent job offer on LinkedIn, it has emerged. According to a report from The Block published last week citing two people familiar with the matter, a senior engineer at the company was duped into applying for a job at a non-existent company, causing
...morePyPI Repository Makes 2FA Security Mandatory for Critical Python Projects

Published: 2022-07-11 05:23:51
Popularity: 157
Author: noreply@blogger.com (Ravie Lakshmanan)
The maintainers of the official third-party software repository for Python have begun imposing a new two-factor authentication (2FA) condition for projects deemed "critical." "We've begun rolling out a 2FA requirement: soon, maintainers of critical projects must have 2FA enabled to publish, update, or modify them," Python Package Index (PyPI) said in a tweet last week. "Any maintainer of a
...moreApple's New "Lockdown Mode" Protects iPhone, iPad, and Mac Against Spyware

Published: 2022-07-07 03:23:14
Popularity: 301
Author: noreply@blogger.com (Ravie Lakshmanan)
Apple on Wednesday announced it plans to introduce an enhanced security setting called Lockdown Mode in iOS 16, iPadOS 16, and macOS Ventura to safeguard high-risk users against "highly targeted cyberattacks." The "extreme, optional protection" feature, now available for preview in beta versions of its upcoming software, is designed to counter a surge in threats posed by private companies
...moreUpdate Google Chrome Browser to Patch New Zero-Day Exploit Detected in the Wild

Published: 2022-07-05 02:55:41
Popularity: 427
Author: noreply@blogger.com (Ravie Lakshmanan)
Google on Monday shipped security updates to address a high-severity zero-day vulnerability in its Chrome web browser that it said is being exploited in the wild. The shortcoming, tracked as CVE-2022-2294, relates to a heap overflow flaw in the WebRTC component that provides real-time audio and video communication capabilities in browsers without the need to install plugins or download native
...moreNew Hertzbleed Side Channel Attack Affects All Modern AMD and Intel CPUs

Published: 2022-06-16 03:12:43
Popularity: 287
Author: noreply@blogger.com (Ravie Lakshmanan)
A newly discovered security vulnerability in modern Intel and AMD processors could let remote attackers steal encryption keys via a power side channel attack. Dubbed Hertzbleed by a group of researchers from the University of Texas, the University of Illinois Urbana-Champaign, and the University of Washington, the issue is rooted in dynamic voltage and frequency scaling (DVFS), a power and
...moreNew Syslogk Linux Rootkit Lets Attackers Remotely Command It Using "Magic Packets"
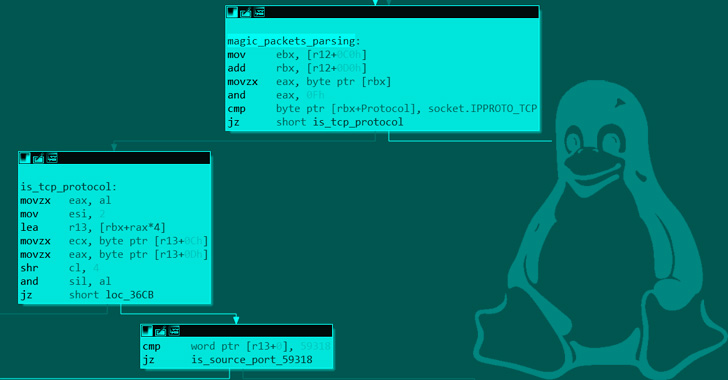
Published: 2022-06-14 08:54:54
Popularity: 270
Author: noreply@blogger.com (Ravie Lakshmanan)
A new covert Linux kernel rootkit named Syslogk has been spotted under development in the wild and cloaking a malicious payload that can be remotely commandeered by an adversary using a magic network traffic packet. "The Syslogk rootkit is heavily based on Adore-Ng but incorporates new functionalities making the user-mode application and the kernel rootkit hard to detect," Avast security
...moreMIT Researchers Discover New Flaw in Apple M1 CPUs That Can't Be Patched

Published: 2022-06-11 08:31:56
Popularity: 649
Author: noreply@blogger.com (Ravie Lakshmanan)
A novel hardware attack dubbed PACMAN has been demonstrated against Apple's M1 processor chipsets, potentially arming a malicious actor with the capability to gain arbitrary code execution on macOS systems. It leverages "speculative execution attacks to bypass an important memory protection mechanism, ARM Pointer Authentication, a security feature that is used to enforce pointer integrity," MIT
...moreSideWinder Hackers Launched Over a 1,000 Cyber Attacks Over the Past 2 Years

Published: 2022-05-31 08:30:39
Popularity: 162
Author: noreply@blogger.com (Ravie Lakshmanan)
An "aggressive" advanced persistent threat (APT) group known as SideWinder has been linked to over 1,000 new attacks since April 2020. "Some of the main characteristics of this threat actor that make it stand out among the others, are the sheer number, high frequency and persistence of their attacks and the large collection of encrypted and obfuscated malicious components used in their
...moreNew Zoom Flaws Could Let Attackers Hack Victims Just by Sending them a Message

Published: 2022-05-25 04:59:02
Popularity: 859
Author: noreply@blogger.com (Ravie Lakshmanan)
Popular video conferencing service Zoom has resolved as many as four security vulnerabilities, which could be exploited to compromise another user over chat by sending specially crafted Extensible Messaging and Presence Protocol (XMPP) messages and execute malicious code. Tracked from CVE-2022-22784 through CVE-2022-22787, the issues range between 5.9 and 8.1 in severity. Ivan Fratric of Google
...moreQNAP Advises to Mitigate Remote Hacking Flaws Until Patches are Available

Published: 2022-04-28 04:26:01
Popularity: 63
Author: noreply@blogger.com (Ravie Lakshmanan)
Network-attached storage (NAS) appliance maker QNAP on Wednesday said it's working on updating its QTS and QuTS operating systems after Netatalk last month released patches to contain seven security flaws in its software. Netatalk is an open-source implementation of the Apple Filing Protocol (AFP), allowing Unix-like operating systems to serve as file servers for Apple macOS computers. <!-
...moreGoogle Releases Android Update to Patch Actively Exploited Vulnerability

Published: 2022-05-06 05:13:54
Popularity: 200
Author: noreply@blogger.com (Ravie Lakshmanan)
Google has released monthly security patches for Android with fixes for 37 flaws across different components, one of which is a fix for an actively exploited Linux kernel vulnerability that came to light earlier this year. Tracked as CVE-2021-22600 (CVSS score: 7.8), the vulnerability is ranked "High" for severity and could be exploited by a local user to escalate privileges or deny service. The
...moreCritical TLStorm 2.0 Bugs Affect Widely-Used Aruba and Avaya Network Switches
Published: 2022-05-03 14:14:13
Popularity: 104
Author: noreply@blogger.com (Ravie Lakshmanan)
Cybersecurity researchers have detailed as many as five severe security flaws in the implementation of TLS protocol in several models of Aruba and Avaya network switches that could be abused to gain remote access to enterprise networks and steal valuable information. The findings follow the March disclosure of TLStorm, a set of three critical flaws in APC Smart-UPS devices that could permit an
...moreResearchers Detail Bug That Could Paralyze Snort Intrusion Detection System

Published: 2022-04-20 10:43:52
Popularity: 509
Author: noreply@blogger.com (Ravie Lakshmanan)
Details have emerged about a now-patched security vulnerability in the Snort intrusion detection and prevention system that could trigger a denial-of-service (DoS) condition and render it powerless against malicious traffic. Tracked as CVE-2022-20685, the vulnerability is rated 7.5 for severity and resides in the Modbus preprocessor of the Snort detection engine. It affects all open-source Snort
...moreBlock Admits Data Breach Involving Cash App Data Accessed by Former Employee

Published: 2022-04-06 09:01:34
Popularity: 105
Author: noreply@blogger.com (Ravie Lakshmanan)
Block, the company formerly known as Square, has disclosed a data breach that involved a former employee downloading unspecified reports pertaining to its Cash App Investing that contained information about its U.S. customers. "While this employee had regular access to these reports as part of their past job responsibilities, in this instance these reports were accessed without permission after
...moreNew Report on Okta Hack Reveals the Entire Episode LAPSUS$ Attack

Published: 2022-03-29 07:50:41
Popularity: 175
Author: noreply@blogger.com (Ravie Lakshmanan)
An independent security researcher has shared what's a detailed timeline of events that transpired as the notorious LAPSUS$ extortion gang broke into a third-party provider linked to the cyber incident at Okta in late January 2022. In a set of screenshots posted on Twitter, Bill Demirkapi published a two-page "intrusion timeline" allegedly prepared by Mandiant, the cybersecurity firm hired by
...moreNorth Korean Hackers Exploited Chrome Zero-Day to Target Fintech, IT, and Media Firms

Published: 2022-03-25 07:28:21
Popularity: 302
Author: noreply@blogger.com (Ravie Lakshmanan)
Google's Threat Analysis Group (TAG) on Thursday disclosed that it acted to mitigate threats from two distinct government-backed attacker groups based in North Korea that exploited a recently-uncovered remote code execution flaw in the Chrome web browser. The campaigns, once again "reflective of the regime's immediate concerns and priorities," are said to have targeted U.S. based organizations
...moreLAPSUS$ Hackers Claim to Have Breached Microsoft and Authentication Firm Okta

Published: 2022-03-22 15:33:10
Popularity: 400
Author: noreply@blogger.com (Ravie Lakshmanan)
Microsoft and authentication services provider Okta said they are investigating claims of a potential breach alleged by the LAPSUS$ extortionist gang. The development, which was first reported by Vice and Reuters, comes after the cyber criminal group posted screenshots and source code of what it said were the companies' internal projects and systems on its Telegram channel. The leaked 37GB
...moreMultiple Security Flaws Discovered in Popular Software Package Managers
Published: 2022-03-11 13:11:13
Popularity: 597
Author: noreply@blogger.com (Ravie Lakshmanan)
Multiple security vulnerabilities have been disclosed in popular package managers that, if potentially exploited, could be abused to run arbitrary code and access sensitive information, including source code and access tokens, from compromised machines. It's, however, worth noting that the flaws require the targeted developers to handle a malicious package in conjunction with one of the affected
...moreReport: Nearly 75% of Infusion Pumps Affected by Severe Vulnerabilities

Published: 2022-03-03 09:04:40
Popularity: 174
Author: noreply@blogger.com (Ravie Lakshmanan)
An analysis of data crowdsourced from more than 200,000 network-connected infusion pumps used in hospitals and healthcare entities has revealed that 75% of those medical devices contain security weaknesses that could put them at risk of potential exploitation. "These shortcomings included exposure to one or more of some 40 known cybersecurity vulnerabilities and/or alerts that they had one or
...moreCritical Flaw Uncovered in WordPress Backup Plugin Used by Over 3 Million Sites

Published: 2022-02-19 06:25:08
Popularity: 112
Author: noreply@blogger.com (Ravie Lakshmanan)
Patches have been issued to contain a "severe" security vulnerability in UpdraftPlus, a WordPress plugin with over three million installations, that can be weaponized to download the site's private data using an account on the vulnerable sites. "All versions of UpdraftPlus from March 2019 onwards have contained a vulnerability caused by a missing permissions-level check, allowing untrusted users
...moreThis New Tool Can Retrieve Pixelated Text from Redacted Documents
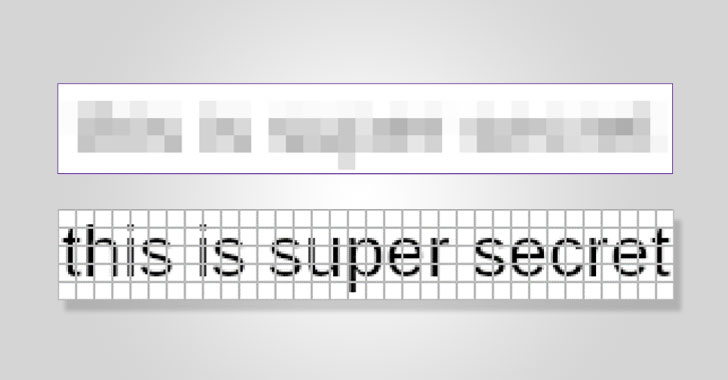
Published: 2022-02-17 09:22:21
Popularity: 982
Author: noreply@blogger.com (Ravie Lakshmanan)
The practice of blurring out text using a method called pixelation may not be as secure as previously thought. While the most foolproof way of concealing sensitive textual information is to use opaque black bars, other redaction methods like pixelation can achieve the opposite effect, enabling the reversal of pixelized text back into its original form. Dan Petro, a lead researcher at offensive
...moreVMware Patches Important Bug Affecting ESXi, Workstation and Fusion Products

Published: 2022-01-06 06:17:38
Popularity: 145
Author: noreply@blogger.com (Ravie Lakshmanan)
VMWare has shipped updates to Workstation, Fusion, and ESXi products to address an "important" security vulnerability that could be weaponized by a threat actor to take control of affected systems. The issue relates to a heap-overflow vulnerability — tracked as CVE-2021-22045 (CVSS score: 7.7) — that, if successfully exploited, results in the execution of arbitrary code. The company credited
...moreTwitter Bans Users From Posting ‘Private Media’ Without a Person's Consent

Published: 2021-12-01 05:20:46
Popularity: 83
Author: noreply@blogger.com (Ravie Lakshmanan)
Twitter on Tuesday announced an expansion to its private information policy to include private media, effectively prohibiting the sharing of photos and videos without express permission from the individuals depicted in them with an aim to curb doxxing and harassment. "Beginning today, we will not allow the sharing of private media, such as images or videos of private individuals without their
...moreCronRAT: A New Linux Malware That’s Scheduled to Run on February 31st

Published: 2021-11-26 08:08:34
Popularity: 518
Author: noreply@blogger.com (Ravie Lakshmanan)
Researchers have unearthed a new remote access trojan (RAT) for Linux that employs a never-before-seen stealth technique that involves masking its malicious actions by scheduling them for execution on February 31st, a non-existent calendar day. Dubbed CronRAT, the sneaky malware "enables server-side Magecart data theft which bypasses browser-based security solutions," Sansec Threat Research said
...more11 Malicious PyPI Python Libraries Caught Stealing Discord Tokens and Installing Shells

Published: 2021-11-19 13:14:08
Popularity: 548
Author: noreply@blogger.com (Ravie Lakshmanan)
Cybersecurity researchers have uncovered as many as 11 malicious Python packages that have been cumulatively downloaded more than 41,000 times from the Python Package Index (PyPI) repository, and could be exploited to steal Discord access tokens, passwords, and even stage dependency confusion attacks. The Python packages have since been removed from the repository following responsible
...moreResearchers Break Intel SGX With New 'SmashEx' CPU Attack Technique

Published: 2021-10-20 13:27:34
Popularity: 300
Author: noreply@blogger.com (Ravie Lakshmanan)
A newly disclosed vulnerability affecting Intel processors could be abused by an adversary to gain access to sensitive information stored within enclaves and even run arbitrary code on vulnerable systems. The vulnerability (CVE-2021-0186, CVSS score: 8.2) was discovered by a group of academics from ETH Zurich, the National University of Singapore, and the Chinese National University of Defense
...moreCode Execution Bug Affects Yamale Python Package — Used by Over 200 Projects

Published: 2021-10-07 11:50:04
Popularity: 112
Author: noreply@blogger.com (Ravie Lakshmanan)
A high-severity code injection vulnerability has been disclosed in 23andMe's Yamale, a schema and validator for YAML, that could be trivially exploited by adversaries to execute arbitrary Python code. The flaw, tracked as CVE-2021-38305 (CVSS score: 7.8), involves manipulating the schema file provided as input to the tool to circumvent protections and achieve code execution. Particularly, the
...moreTwitch Suffers Massive 125GB Data and Source Code Leak Due to Server Misconfiguration

Published: 2021-10-07 06:54:03
Popularity: 366
Author: noreply@blogger.com (Ravie Lakshmanan)
Interactive livestreaming platform Twitch acknowledged a "breach" after an anonymous poster on the 4chan messaging board leaked its source code, an unreleased Steam competitor from Amazon Game Studios, details of creator payouts, proprietary software development kits, and other internal tools. The Amazon-owned service said it's "working with urgency to understand the extent of this," adding the
...moreNew Capoae Malware Infiltrates WordPress Sites and Installs Backdoored Plugin

Published: 2021-09-21 10:08:05
Popularity: 600
Author: noreply@blogger.com (Ravie Lakshmanan)
🤖: "Malware alert"
A recently discovered wave of malware attacks has been spotted using a variety of tactics to enslave susceptible machines with easy-to-guess administrative credentials to co-opt them into a network with the goal of illegally mining cryptocurrency. "The malware's primary tactic is to spread by taking advantage of vulnerable systems and weak administrative credentials. Once they've been infected,
...moreCring Ransomware Gang Exploits 11-Year-Old ColdFusion Bug

Published: 2021-09-21 13:00:03
Popularity: 290
Author: noreply@blogger.com (Ravie Lakshmanan)
Unidentified threat actors breached a server running an unpatched, 11-year-old version of Adobe's ColdFusion 9 software in minutes to remotely take over control and deploy file-encrypting Cring ransomware on the target's network 79 hours after the hack. The server, which belonged to an unnamed services company, was used to collect timesheet and accounting data for payroll as well as to host a
...moreWhatsApp Photo Filter Bug Could Have Exposed Your Data to Remote Attackers

Published: 2021-09-02 10:07:25
Popularity: 384
Author: noreply@blogger.com (Ravie Lakshmanan)
A now-patched high-severity security vulnerability in WhatApp's image filter feature could have been abused to send a malicious image over the messaging app to read sensitive information from the app's memory. Tracked as CVE-2020-1910 (CVSS score: 7.8), the flaw concerns an out-of-bounds read/write and stems from applying specific image filters to a rogue image and sending the altered image to
...moreB. Braun Infusomat Pumps Could Let Attackers Remotely Alter Medication Dosages

Published: 2021-08-26 03:30:41
Popularity: 237
Author: noreply@blogger.com (Ravie Lakshmanan)
Cybersecurity researchers have disclosed five previously unreported security vulnerabilities affecting B. Braun's Infusomat Space Large Volume Pump and SpaceStation that could be abused by malicious parties to tamper with medication doses without any prior authentication. McAfee, which discovered and reported the flaws to the German medical and pharmaceutical device company on January 11, 2021,
...moreUnpatched Remote Hacking Flaw Disclosed in Fortinet's FortiWeb WAF

Published: 2021-08-19 06:50:20
Popularity: 620
Author: noreply@blogger.com (Ravie Lakshmanan)
Details have emerged about a new unpatched security vulnerability in Fortinet's web application firewall (WAF) appliances that could be abused by a remote, authenticated attacker to execute malicious commands on the system. "An OS command injection vulnerability in FortiWeb's management interface (version 6.3.11 and prior) can allow a remote, authenticated attacker to execute arbitrary commands
...moreA Critical Random Number Generator Flaw Affects Billions of IoT Devices
Published: 2021-08-09 14:06:43
Popularity: 850
Author: noreply@blogger.com (Ravie Lakshmanan)
A critical vulnerability has been disclosed in hardware random number generators used in billions of Internet of Things (IoT) devices whereby it fails to properly generate random numbers, thus undermining their security and putting them at risk of attacks. "It turns out that these 'randomly' chosen numbers aren't always as random as you'd like when it comes to IoT devices," Bishop Fox
...morePyPI Python Package Repository Patches Critical Supply Chain Flaw

Published: 2021-08-02 10:50:00
Popularity: 841
Author: noreply@blogger.com (Ravie Lakshmanan)
The maintainers of Python Package Index (PyPI) last week issued fixes for three vulnerabilities, one among which could be abused to achieve arbitrary code execution and take full control of the official third-party software repository. The security weaknesses were discovered and reported by Japanese security researcher RyotaK, who in the past has disclosed critical vulnerabilities in the
...moreNew Leak Reveals Abuse of Pegasus Spyware to Target Journalists Globally

Published: 2021-07-20 03:39:50
Popularity: 304
Author: noreply@blogger.com (Ravie Lakshmanan)
A sweeping probe into a data leak of more than 50,000 phone numbers has revealed an extensive misuse of Israeli company NSO Group's Pegasus "military-grade spyware" to facilitate human rights violations by surveilling heads of state, activists, journalists, and lawyers around the world. Dubbed the "Pegasus Project," the investigation is a collaboration by more than 80 journalists from a
...moreTurns Out That Low-Risk iOS Wi-Fi Naming Bug Can Hack iPhones Remotely
Published: 2021-07-22 03:40:57
Popularity: 436
Author: noreply@blogger.com (Ravie Lakshmanan)
The Wi-Fi network name bug that was found to completely disable an iPhone's networking functionality had remote code execution capabilities and was silently fixed by Apple earlier this year, according to new research. The denial-of-service vulnerability, which came to light last month, stemmed from the way iOS handled string formats associated with the SSID input, triggering a crash on any
...moreCritical Flaws Reported in Etherpad — a Popular Google Docs Alternative

Published: 2021-07-14 03:19:11
Popularity: 113
Author: noreply@blogger.com (Ravie Lakshmanan)
Cybersecurity researchers have disclosed new security vulnerabilities in the Etherpad text editor (version 1.8.13) that could potentially enable attackers to hijack administrator accounts, execute system commands, and even steal sensitive documents. The two flaws — tracked as CVE-2021-34816 and CVE-2021-34817 — were discovered and reported on June 4 by researchers from SonarSource, following
...moreKaseya Releases Patches for Flaws Exploited in Widespread Ransomware Attack

Published: 2021-07-12 10:46:11
Popularity: 147
Author: noreply@blogger.com (Ravie Lakshmanan)
Florida-based software vendor Kaseya on Sunday rolled out urgent updates to address critical security vulnerabilities in its Virtual System Administrator (VSA) solution that was used as a jumping off point to target as many as 1,500 businesses across the globe as part of a widespread supply-chain ransomware attack. Following the incident, the company had urged on-premises VSA customers to shut
...moreKaseya Supply-Chain Attack Hits Nearly 40 Service Providers With REvil Ransomware

Published: 2021-07-05 03:29:30
Popularity: 281
Author: noreply@blogger.com (Ravie Lakshmanan)
Threat actors behind the notorious REvil cybercrime operation appear to have pushed ransomware via an update for Kaseya's IT management software, hitting around 40 customers worldwide, in what's an instance of a widespread supply-chain ransomware attack. "Beginning around mid-day (EST/US) on Friday, July 2, 2021, Kaseya's Incident Response team learned of a potential security incident involving
...moreMicrosoft Urges Azure Users to Update PowerShell to Patch RCE Flaw
Published: 2021-07-05 06:42:47
Popularity: 500
Author: noreply@blogger.com (Ravie Lakshmanan)
Microsoft is urging Azure users to update the PowerShell command-line tool as soon as possible to protect against a critical remote code execution vulnerability impacting .NET Core. The issue, tracked as CVE-2021-26701 (CVSS score: 8.1), affects PowerShell versions 7.0 and 7.1 and have been remediated in versions 7.0.6 and 7.1.3, respectively. Windows PowerShell 5.1 isn't impacted by the flaw.
...moreMongolian Certificate Authority Hacked to Distribute Backdoored CA Software

Published: 2021-07-02 12:54:06
Popularity: 214
Author: noreply@blogger.com (Ravie Lakshmanan)
In yet another instance of software supply chain attack, unidentified hackers breached the website of MonPass, one of Mongolia's major certificate authorities, to backdoor its installer software with Cobalt Strike binaries. The trojanized client was available for download between February 8, 2021, and March 3, 2021, said Czech cybersecurity software company Avast in a report published Thursday.
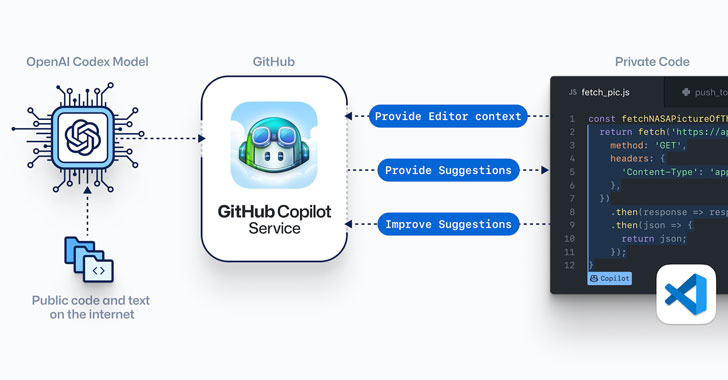
...moreGitHub Launches 'Copilot' — AI-Powered Code Completion Tool
Published: 2021-06-30 07:10:13
Popularity: 391
Author: noreply@blogger.com (Ravie Lakshmanan)
GitHub on Tuesday launched a technical preview of a new AI-powered pair programming tool that aims to help software developers write better code across a variety of programming languages, including Python, JavaScript, TypeScript, Ruby, and Go. Copilot, as the code synthesizer is called, has been developed in collaboration with OpenAI, and leverages Codex, a new AI system that's trained on
...moreGoogle now requires app developers to verify their address and use 2FA

Published: 2021-06-29 09:39:55
Popularity: 1422
Author: noreply@blogger.com (Ravie Lakshmanan)
Google on Monday announced new measures for the Play Store, including requiring developer accounts to turn on 2-Step Verification (2SV), provide an address, and verify their contact details later this year. The new identification and two-factor authentication requirements are a step towards strengthening account security and ensuring a safe and secure app marketplace, Google Play Trust and
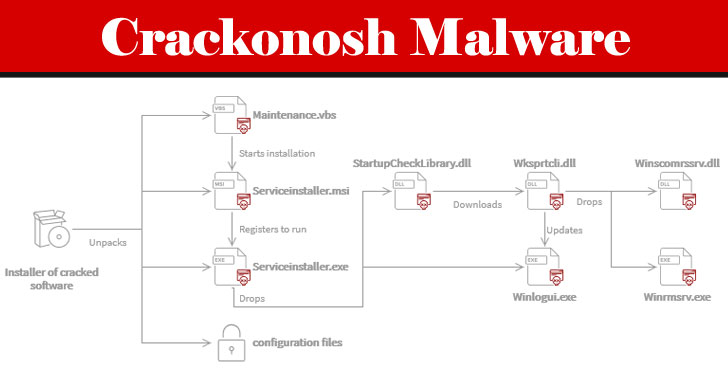
...moreCrackonosh virus mined $2 million of Monero from 222,000 hacked computers
Published: 2021-06-28 03:00:17
Popularity: 530
Author: noreply@blogger.com (Ravie Lakshmanan)
A previously undocumented Windows malware has infected over 222,000 systems worldwide since at least June 2018, yielding its developer no less than 9,000 Moneros ($2 million) in illegal profits. Dubbed "Crackonosh," the malware is distributed via illegal, cracked copies of popular software, only to disable antivirus programs installed in the machine and install a coin miner package called XMRig
...morePatch Tor Browser Bug to Prevent Tracking of Your Online Activities

Published: 2021-06-23 08:54:53
Popularity: 533
Author: noreply@blogger.com (Ravie Lakshmanan)
Open-source Tor browser has been updated to version 10.0.18 with fixes for multiple issues, including a privacy-defeating bug that could be used to uniquely fingerprint users across different browsers based on the apps installed on a computer. In addition to updating Tor to 0.4.5.9, the browser's Android version has been upgraded to Firefox to version 89.1.1, alongside incorporating patches
...moreNoxPlayer Supply-Chain Attack is Likely the Work of Gelsemium Hackers

Published: 2021-06-14 13:34:33
Popularity: 174
Author: noreply@blogger.com (Ravie Lakshmanan)
A new cyber espionage group named Gelsemium has been linked to a supply chain attack targeting the NoxPlayer Android emulator that was disclosed earlier this year. The findings come from a systematic analysis of multiple campaigns undertaken by the APT crew, with evidence of the earliest attack dating back all the way to 2014 under the codename Operation TooHash based on malware payloads
...more7-Year-Old Polkit Flaw Lets Unprivileged Linux Users Gain Root Access

Published: 2021-06-11 07:47:01
Popularity: 596
Author: noreply@blogger.com (Ravie Lakshmanan)
A seven-year-old privilege escalation vulnerability discovered in the polkit system service could be exploited by a malicious unprivileged local attacker to bypass authorization and escalate permissions to the root user. Tracked as CVE-2021-3560 (CVSS score: 7.8), the flaw affects polkit versions between 0.113 and 0.118 and was discovered by GitHub security researcher Kevin Backhouse, who said
...moreHackers Can Exploit Samsung Pre-Installed Apps to Spy On Users

Published: 2021-06-11 09:28:02
Popularity: 827
Author: noreply@blogger.com (Ravie Lakshmanan)
Multiple critical security flaws have been disclosed in Samsung's pre-installed Android apps, which, if successfully exploited, could have allowed adversaries access to personal data without users' consent and take control of the devices. "The impact of these bugs could have allowed an attacker to access and edit the victim's contacts, calls, SMS/MMS, install arbitrary apps with device
...moreCrypto-Mining Attacks Targeting Kubernetes Clusters via Kubeflow Instances

Published: 2021-06-09 10:43:36
Popularity: 127
Author: noreply@blogger.com (Ravie Lakshmanan)
Cybersecurity researchers on Tuesday disclosed a new large-scale campaign targeting Kubeflow deployments to run malicious cryptocurrency mining containers. The campaign involved deploying TensorFlow pods on Kubernetes clusters, with the pods running legitimate TensorFlow images from the official Docker Hub account. However, the container images were configured to execute rogue commands that mine
...moreCritical RCE Vulnerability Found in VMware vCenter Server — Patch Now!

Published: 2021-05-26 04:57:58
Popularity: 721
Author: noreply@blogger.com (Ravie Lakshmanan)
VMware has rolled out patches to address a critical security vulnerability in vCenter Server that could be leveraged by an adversary to execute arbitrary code on the server. Tracked as CVE-2021-21985 (CVSS score 9.8), the issue stems from a lack of input validation in the Virtual SAN (vSAN) Health Check plug-in, which is enabled by default in the vCenter Server. "A malicious actor with network
...moreYour Amazon Devices to Automatically Share Your Wi-Fi With Neighbors
Published: 2021-05-31 19:16:16
Popularity: 4676
Author: noreply@blogger.com (Ravie Lakshmanan)
Starting June 8, Amazon will automatically enable a feature on its family of hardware devices, including Echo speakers, Ring Video Doorbells, Ring Floodlight Cams, and Ring Spotlight Cams, that will share a small part of your Internet bandwidth with nearby neighbors — unless you choose to opt-out. To that effect, the company intends to register all compatible devices that are operational in the
...moreResearchers Demonstrate 2 New Hacks to Modify Certified PDF Documents

Published: 2021-05-29 08:34:47
Popularity: 133
Author: noreply@blogger.com (Ravie Lakshmanan)
Cybersecurity researchers have disclosed two new attack techniques on certified PDF documents that could potentially enable an attacker to alter a document's visible content by displaying malicious content over the certified content without invalidating its signature. "The attack idea exploits the flexibility of PDF certification, which allows signing or adding annotations to certified documents
...moreMozilla Begins Rolling Out 'Site Isolation' Security Feature to Firefox Browser
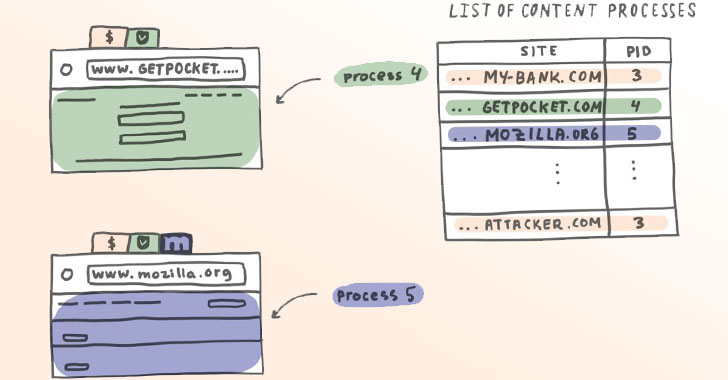
Published: 2021-05-19 12:51:06
Popularity: 595
Author: noreply@blogger.com (Ravie Lakshmanan)
Mozilla has begun rolling out a new security feature for its Firefox browser in nightly and beta channels that aims to protect users against a new class of side-channel attacks from malicious sites. Called "Site Isolation," the implementation loads each website separately in its own operating system process and, as a result, prevents untrusted code from a rogue website from accessing
...moreHackers Exploit VPN to Deploy SUPERNOVA malware on SolarWinds Orion
Published: 2021-04-23 05:52:36
Popularity: 817
Author: noreply@blogger.com (Ravie Lakshmanan)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has disclosed details of a new advanced persistent threat (APT) that's leveraging the Supernova backdoor to compromise SolarWinds Orion installations after gaining access to the network through a connection to a Pulse Secure VPN device. "The threat actor connected to the entity's network via a Pulse Secure virtual private network (
...morePasswordstate Password Manager Update Hijacked to Install Backdoor on Thousands of PCs

Published: 2021-04-24 19:04:55
Popularity: 883
Author: noreply@blogger.com (Ravie Lakshmanan)
Click Studios, the Australian software company behind the Passwordstate password management application, has notified customers to reset their passwords following a supply chain attack. The Adelaide-based firm said a bad actor used sophisticated techniques to compromise the software's update mechanism and used it to drop malware on user computers. The breach is said to have occurred between
...moreHackers Set Up a Fake Cybersecurity Firm to Target Security Experts
Published: 2021-04-03 06:05:54
Popularity: 1230
Author: noreply@blogger.com (Ravie Lakshmanan)
A North Korean government-backed campaign targeting cybersecurity researchers with malware has re-emerged with new tactics in their arsenal as part of a fresh social engineering attack. In an update shared on Wednesday, Google's Threat Analysis Group said the attackers behind the operation set up a fake security company called SecuriElite and a slew of social media accounts across Twitter and
...moreNew Zoom Screen-Sharing Bug Lets Other Users Access Restricted Apps
Published: 2021-03-19 10:48:14
Popularity: 588
Author: noreply@blogger.com (Ravie Lakshmanan)
A newly discovered glitch in Zoom's screen sharing feature can accidentally leak sensitive information to other attendees in a call, according to the latest findings. Tracked as CVE-2021-28133, the unpatched security vulnerability makes it possible to reveal contents of applications that are not shared, but only briefly, thereby making it harder to exploit it in the wild. It's worth pointing out
...moreAnother Google Chrome 0-Day Bug Found Actively Exploited In-the-Wild
Published: 2021-03-16 04:51:58
Popularity: 1885
Author: noreply@blogger.com (Ravie Lakshmanan)
Google has addressed yet another actively exploited zero-day in Chrome browser, marking the second such fix released by the company within a month. The browser maker on Friday shipped 89.0.4389.90 for Windows, Mac, and Linux, which is expected to be rolling out over the coming days/weeks to all users. While the update contains a total of five security fixes, the most important flaw rectified by
...moreSolarWinds Blames Intern for 'solarwinds123' Password Lapse
Published: 2021-03-02 01:45:46
Popularity: 3004
Author: noreply@blogger.com (Ravie Lakshmanan)
As cybersecurity researchers continue to piece together the sprawling SolarWinds supply chain attack, top executives of the Texas-based software services firm blamed an intern for a critical password lapse that went unnoticed for several years. The said password "solarwinds123" was originally believed to have been publicly accessible via a GitHub repository since June 17, 2018, before the
...moreFirst Malware Designed for Apple M1 Chip Discovered in the Wild
Published: 2021-02-19 06:56:15
Popularity: 1911
Author: noreply@blogger.com (Ravie Lakshmanan)
One of the first malware samples tailored to run natively on Apple's M1 chips has been discovered, suggesting a new development that indicates that bad actors have begun adapting malicious software to target the company's latest generation of Macs powered by its own processors. While the transition to Apple silicon has necessitated developers to build new versions of their apps to ensure better
...moreCritical Bugs Found in Popular Realtek Wi-Fi Module for Embedded Devices
Published: 2021-02-04 08:36:00
Popularity: 1787
Author: noreply@blogger.com (Ravie Lakshmanan)
Major vulnerabilities have been discovered in the Realtek RTL8195A Wi-Fi module that could have been exploited to gain root access and take complete control of a device's wireless communications. The six flaws were reported by researchers from Israeli IoT security firm Vdoo. The Realtek RTL8195A module is a standalone, low-power-consumption Wi-Fi hardware module targeted at embedded devices used
...moreApple will proxy Safe Browsing requests to hide iOS users' IP from Google
Published: 2021-02-16 03:55:24
Popularity: 2474
Author: noreply@blogger.com (Ravie Lakshmanan)
Apple's upcoming iOS 14.5 update will come with a new feature that will redirect all fraudulent website checks through its own proxy servers as a workaround to preserve user privacy and prevent leaking IP addresses to Google. A built-in security-focused feature in the Safari browser, "Fraudulent Website Warning," alerts users about dangerous websites that have been reported as deceptive,
...moreMalvertisers Exploited WebKit 0-Day to Redirect Browser Users to Scam Sites
Published: 2021-02-17 07:11:54
Popularity: 675
Author: noreply@blogger.com (Ravie Lakshmanan)
A malvertising group known as "ScamClub" exploited a zero-day vulnerability in WebKit-based browsers to inject malicious payloads that redirected users to fraudulent websites gift card scams. The attacks, first spotted by ad security firm Confiant in late June 2020, leveraged a bug (CVE-2021–1801) that allowed malicious parties to bypass the iframe sandboxing policy in the browser engine that
...moreDependency Confusion Supply-Chain Attack Hit Over 35 High-Profile Companies
Published: 2021-02-10 12:57:14
Popularity: 899
Author: noreply@blogger.com (Ravie Lakshmanan)
In what's a novel supply chain attack, a security researcher managed to breach over 35 major companies' internal systems, including that of Microsoft, Apple, PayPal, Shopify, Netflix, Yelp, Tesla, and Uber, and achieve remote code execution. The technique, called dependency confusion or a substitution attack, takes advantage of the fact that a piece of software may include components from a mix
...moreCybercriminals Now Using Plex Media Servers to Amplify DDoS Attacks
Published: 2021-02-06 07:28:24
Popularity: 824
Author: noreply@blogger.com (Ravie Lakshmanan)
A new distributed denial-of-service attack (DDoS) vector has ensnared Plex Media Server systems to amplify malicious traffic against targets to take them offline. "Plex's startup processes unintentionally expose a Plex UPnP-enabled service registration responder to the general Internet, where it can be abused to generate reflection/amplification DDoS attacks," Netscout researchers said in a
...moreWARNING — Hugely Popular 'The Great Suspender' Chrome Extension Contains Malware
Published: 2021-02-06 10:30:56
Popularity: 1105
Author: noreply@blogger.com (Ravie Lakshmanan)
Google on Thursday removed The Great Suspender, a popular Chrome extension used by millions of users, from its Chrome Web Store for containing malware. It also took the unusual step of deactivating it from users' computers. "This extension contains malware," read a terse notification from Google, but it has since emerged that the add-on stealthily added features that could be exploited to
...moreGoogle Discloses Severe Bug in Libgcrypt Encryption Library—Impacting Many Projects
Published: 2021-02-01 07:14:26
Popularity: 587
Author: noreply@blogger.com (Ravie Lakshmanan)
A "severe" vulnerability in GNU Privacy Guard (GnuPG)'s Libgcrypt encryption software could have allowed an attacker to write arbitrary data to the target machine, potentially leading to remote code execution. The flaw, which affects version 1.9.0 of libgcrypt, was discovered on January 28 by Tavis Ormandy of Project Zero, a security research unit within Google dedicated to finding zero-day bugs
...moreNew Docker Container Escape Bug Affects Microsoft Azure Functions
Published: 2021-01-27 15:59:14
Popularity: 992
Author: noreply@blogger.com (Ravie Lakshmanan)
Cybersecurity researcher Paul Litvak today disclosed an unpatched vulnerability in Microsoft Azure Functions that could be used by an attacker to escalate privileges and escape the Docker container used for hosting them. The findings come as part of Intezer Lab's investigations into the Azure compute infrastructure. Following disclosure to Microsoft, the Windows maker is said to have "determined
...moreGoogle uncovers new iOS security feature Apple quietly added after zero-day attacks

Published: 2021-02-01 05:06:31
Popularity: 3197
Author: noreply@blogger.com (Ravie Lakshmanan)
Google Project Zero on Thursday disclosed details of a new security mechanism that Apple quietly added to iOS 14 as a countermeasure to prevent attacks that were recently found to leverage zero-days in its messaging app. Dubbed "BlastDoor," the improved sandbox system for iMessage data was disclosed by Samuel Groß, a Google Project Zero researcher tasked with studying zero-day vulnerabilities in
...moreSharing eBook With Your Kindle Could Have Let Hackers Hijack Your Account
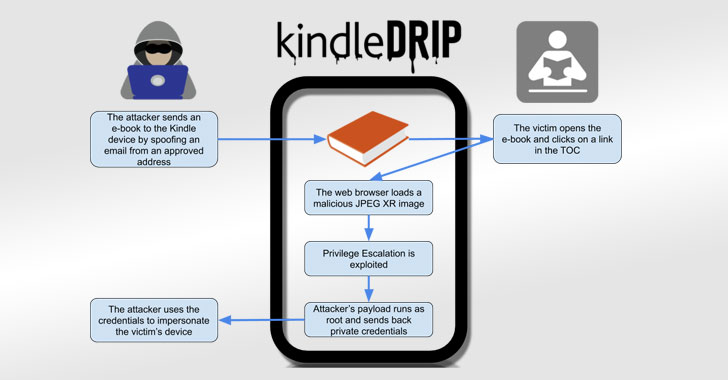
Published: 2021-01-22 10:40:32
Popularity: 640
Author: noreply@blogger.com (Ravie Lakshmanan)
Amazon has addressed a number of flaws in its Kindle e-reader platform that could have allowed an attacker to take control of victims' devices by simply sending them a malicious e-book. Dubbed "KindleDrip," the exploit chain takes advantage of a feature called "Send to Kindle" to send a malware-laced document to a Kindle device that, when opened, could be leveraged to remotely execute arbitrary
...moreSecret Backdoor Account Found in Several Zyxel Firewall, VPN Products

Published: 2021-01-04 17:12:05
Popularity: 3180
Author: noreply@blogger.com (Ravie Lakshmanan)
Zyxel has released a patch to address a critical vulnerability in its firmware concerning a hardcoded, undocumented secret account that could be abused by an attacker to login with administrative privileges and compromise its networking devices. The flaw, tracked as CVE-2020-29583 (CVSS score 7.8), affects version 4.60 present in a wide-range of Zyxel devices, including Unified Security Gateway
...moreGoogle Discloses Poorly-Patched, Now Unpatched, Windows 0-Day Bug
Published: 2020-12-28 06:17:30
Popularity: 3705
Author: noreply@blogger.com (Ravie Lakshmanan)
Google's Project Zero team has made public details of an improperly patched zero-day security vulnerability in Windows print spooler API that could be leveraged by a bad actor to execute arbitrary code. Details of the unpatched flaw were revealed publicly after Microsoft failed to rectify it within 90 days of responsible disclosure on September 24. Originally tracked as CVE-2020-0986, the flaw
...moreTwo New Chrome 0-Days Under Active Attacks – Update Your Browser
Published: 2020-11-12 03:36:28
Popularity: 1967
Author: noreply@blogger.com (Ravie Lakshmanan)
Google has patched two more zero-day flaws in the Chrome web browser for desktop, making it the fourth and fifth actively exploited vulnerabilities addressed by the search giant in recent weeks. The company released 86.0.4240.198 for Windows, Mac, and Linux, which it said will be rolling out over the coming days/weeks to all users. Tracked as CVE-2020-16013 and CVE-2020-16017, the flaws were
...moreMajor Instagram App Bug Could've Given Hackers Remote Access to Your Phone

Published: 2020-09-24 10:22:48
Popularity: 3054
Author: noreply@blogger.com (Ravie Lakshmanan)
Ever wonder how hackers can hack your smartphone remotely? In a report shared with The Hacker News today, Check Point researchers disclosed details about a critical vulnerability in Instagram's Android app that could have allowed remote attackers to take control over a targeted device just by sending victims a specially crafted image. What's more worrisome is that the flaw not only lets attackers
...moreEvasive Credit Card Skimmers Using Homograph Domains and Infected Favicon
Published: 2020-08-07 13:01:06
Popularity: 1485
Author: noreply@blogger.com (Ravie Lakshmanan)
Cybersecurity researchers today highlighted an evasive phishing technique that attackers are exploiting in the wild to target visitors of several sites with a quirk in domain names, and leverage modified favicons to inject e-skimmers and steal payment card information covertly. "The idea is simple and consists of using characters that look the same in order to dupe users," Malwarebytes
...moreResearchers Reveal New Security Flaw Affecting China's DJI Drones
Published: 2020-07-28 06:58:15
Popularity: 2028
Author: noreply@blogger.com (Ravie Lakshmanan)
Cybersecurity researchers on Thursday revealed security issues in the Android app developed by Chinese drone-maker Da Jiang Innovations (DJI) that comes with an auto-update mechanism that bypasses Google Play Store and could be used to install malicious applications and transmit sensitive personal information to DJI's servers. The twin reports, courtesy of cybersecurity firms Synacktiv and
...moreIntel CPUs Vulnerable to New 'SGAxe' and 'CrossTalk' Side-Channel Attacks
Published: 2020-06-10 12:59:04
Popularity: 1975
Author: noreply@blogger.com (Ravie Lakshmanan)
Cybersecurity researchers have discovered two distinct attacks that could be exploited against modern Intel processors to leak sensitive information from the CPU's trusted execution environments (TEE). Called SGAxe, the first of the flaws is an evolution of the previously uncovered CacheOut attack (CVE-2020-0549) earlier this year that allows an attacker to retrieve the contents from the CPU's
...moreWarning — Unpatched Critical 'Wormable' Windows SMBv3 Flaw Disclosed
Published: 2020-03-11 12:27:42
Popularity: 3303
Author: noreply@blogger.com (Ravie Lakshmanan)
Keywords:
Shortly after releasing its monthly batch of security updates, Microsoft late yesterday separately issued an advisory warning billions of its Windows users of a new critical, unpatched, and wormable vulnerability affecting Server Message Block 3.0 (SMBv3) network communication protocol. It appears Microsoft originally planned to fix the flaw as part of its March 2020 Patch Tuesday update only,
...more